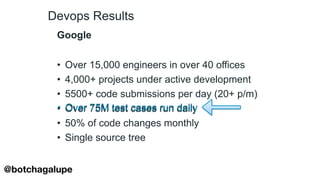
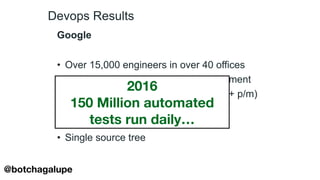
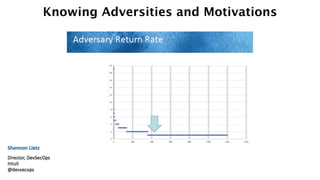
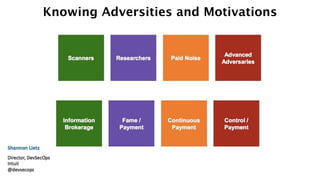
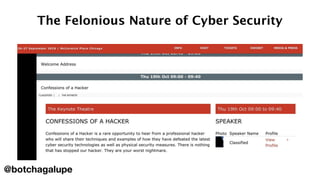
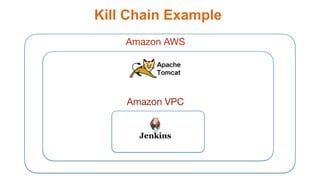
1) The document discusses the divine and felonious nature of cyber security and introduces DevSecOps.
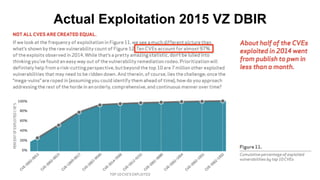
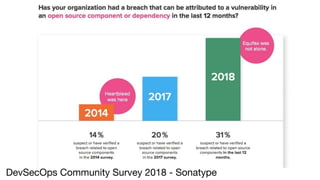
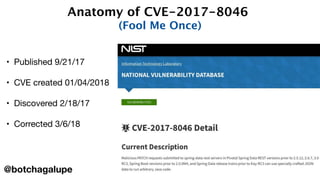
2) It provides examples of vulnerabilities like CVE-2017-5638 and how many organizations downloaded vulnerable software versions.
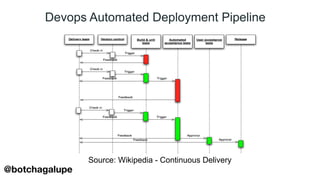
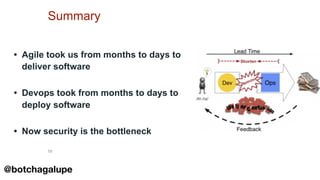
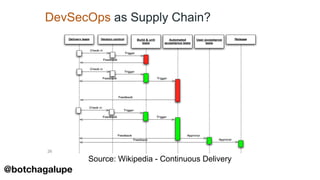
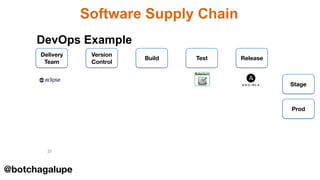
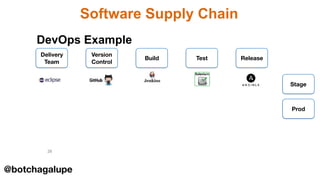
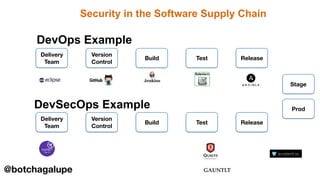
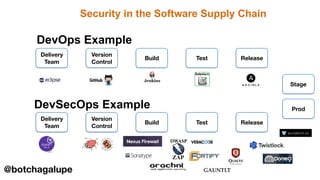
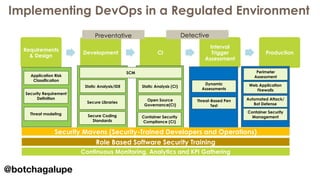
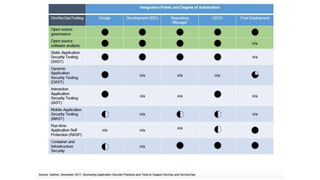
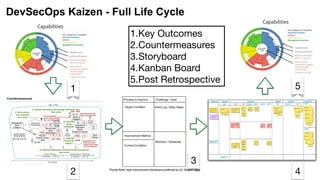
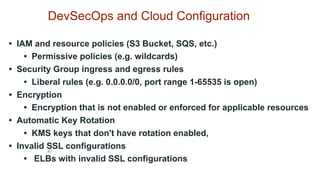
3) DevSecOps is presented as integrating security practices and automation into the entire software development lifecycle to help address cyber security issues.