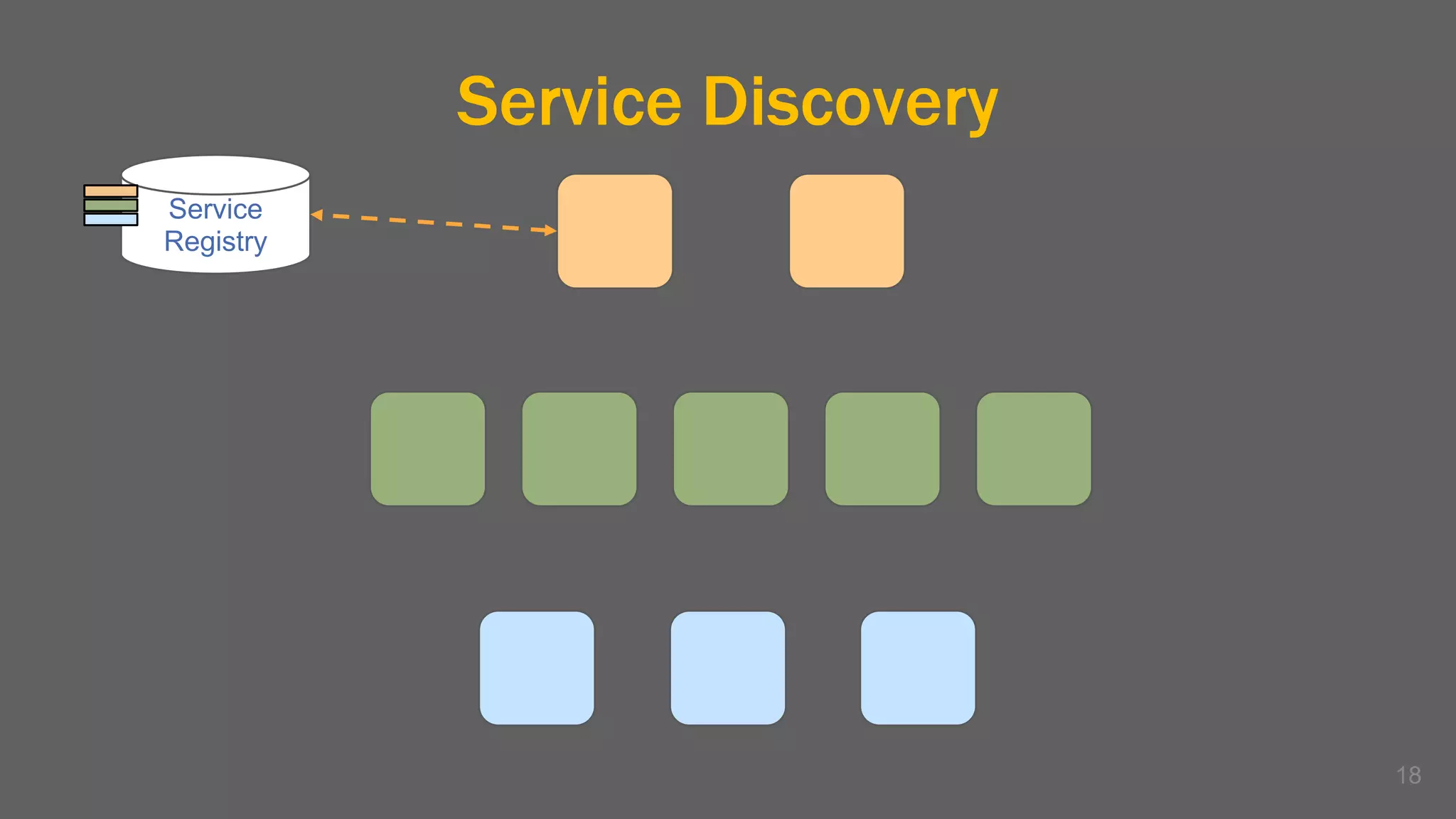
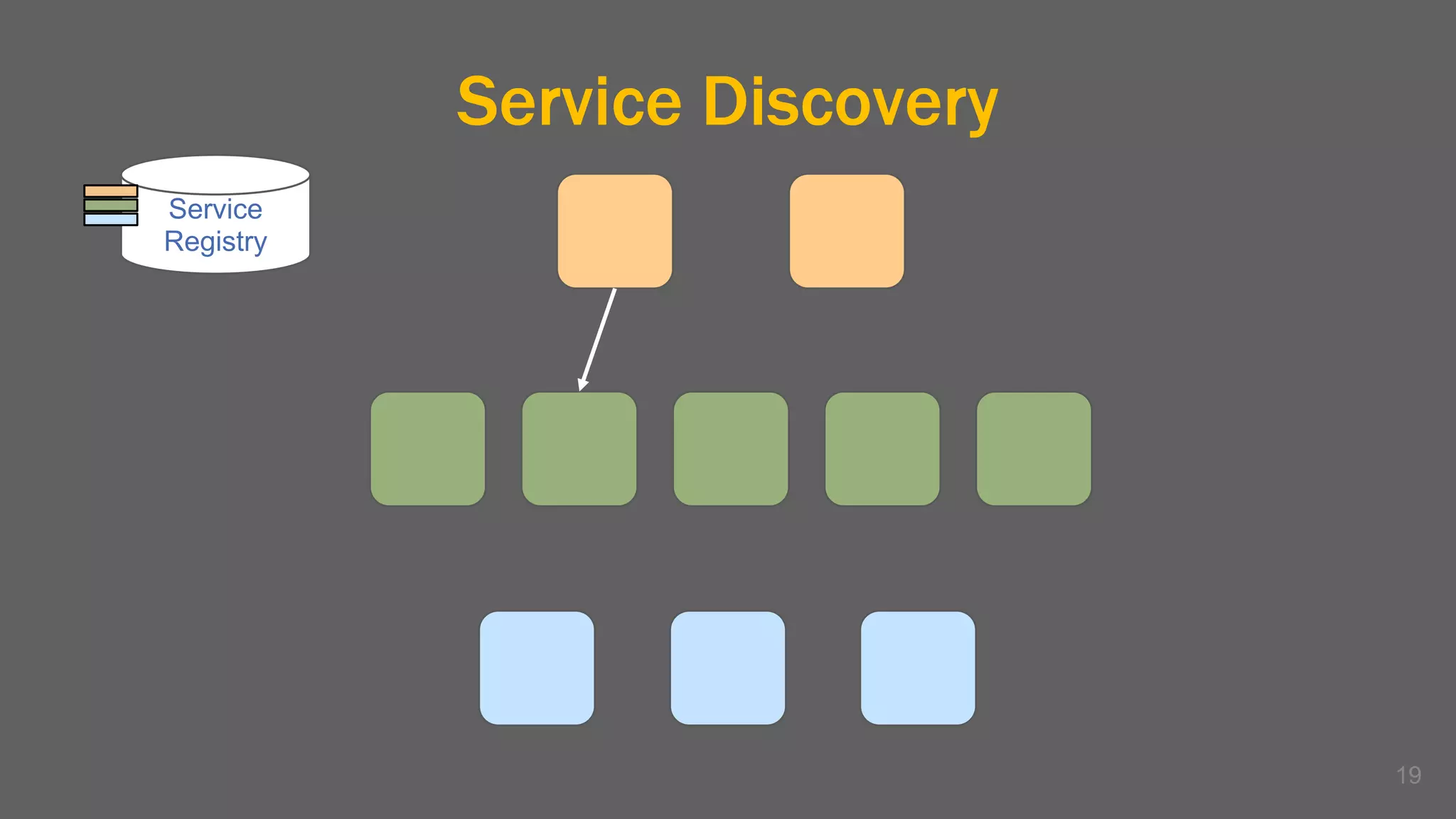
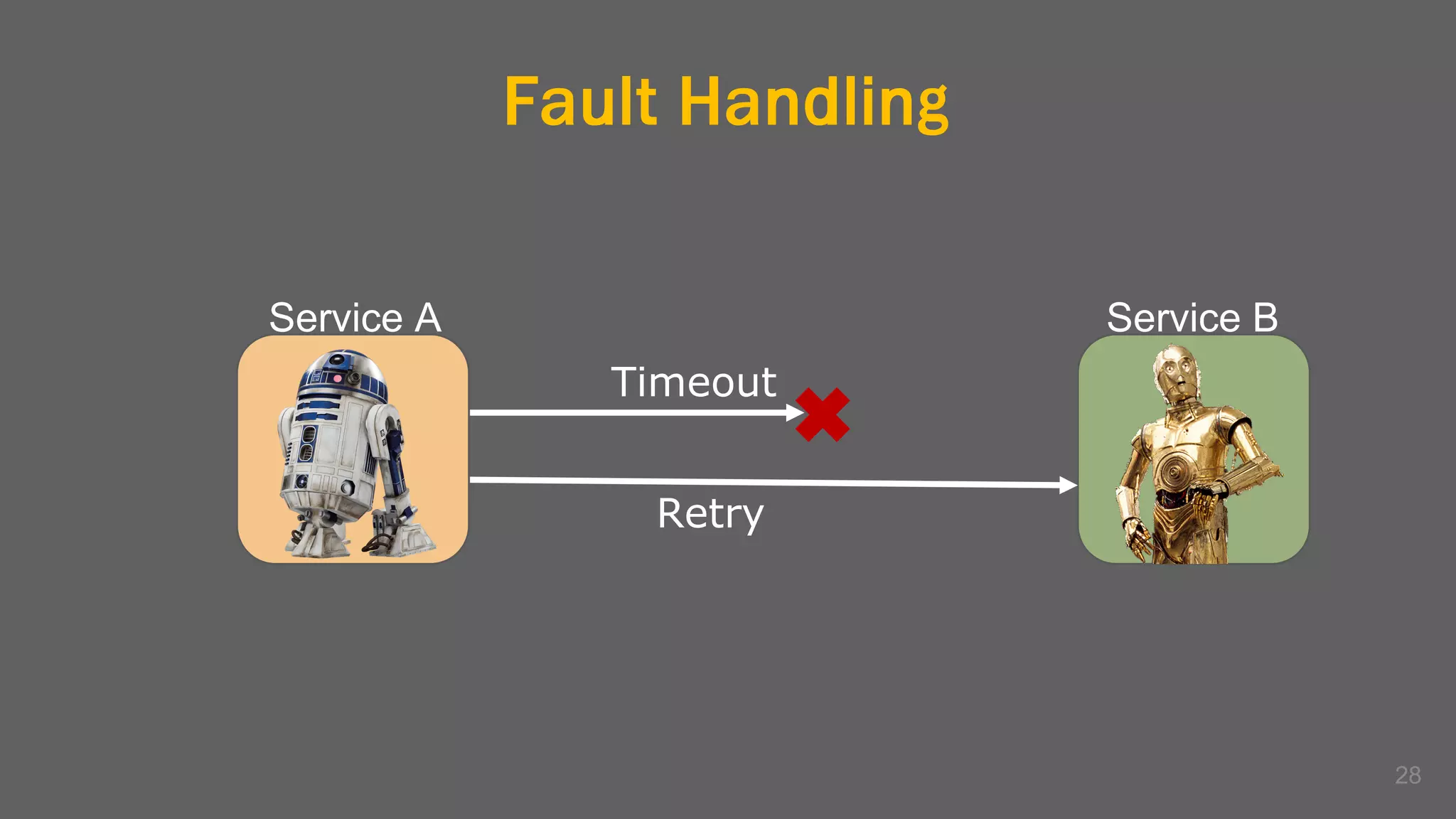
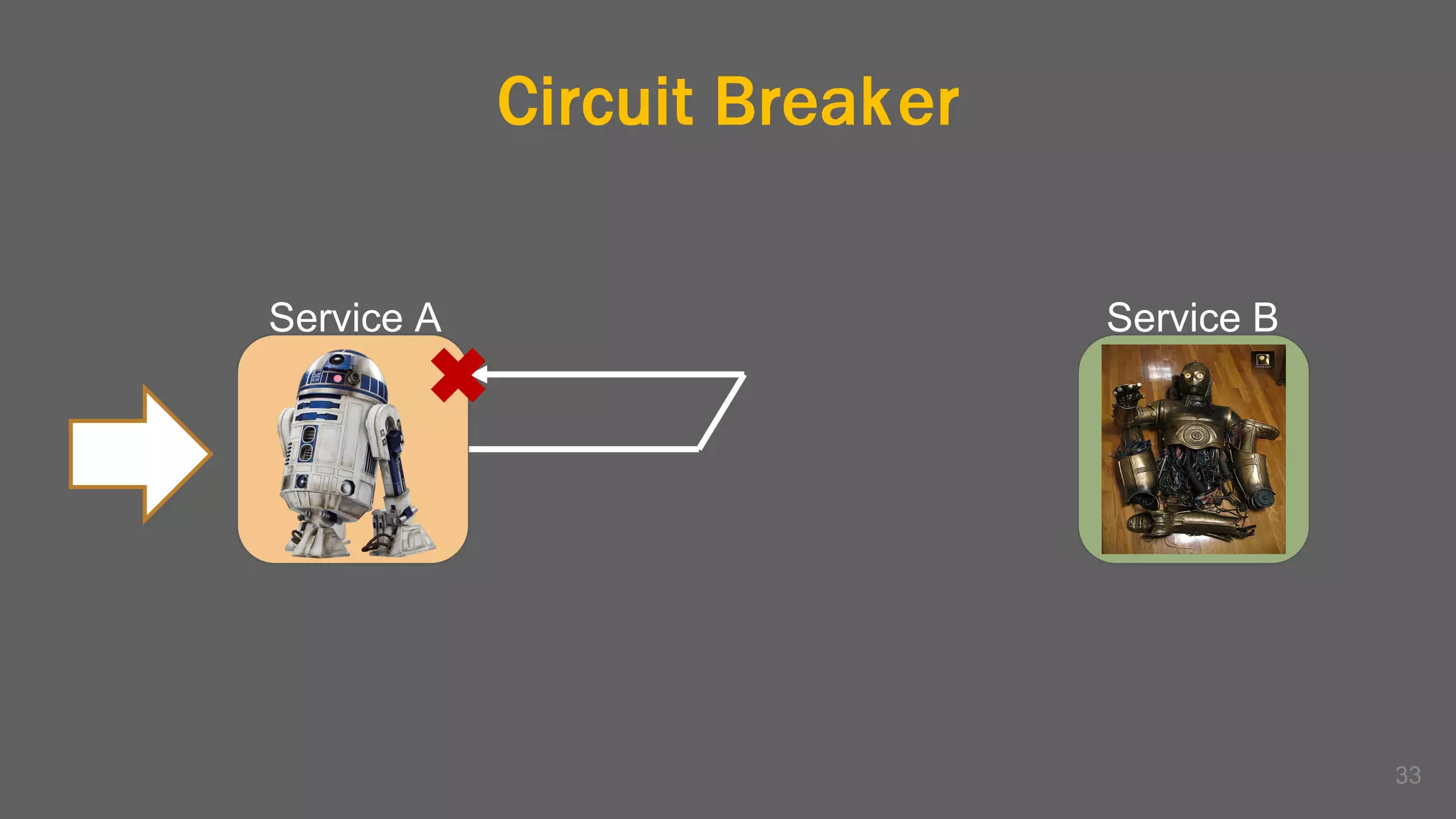
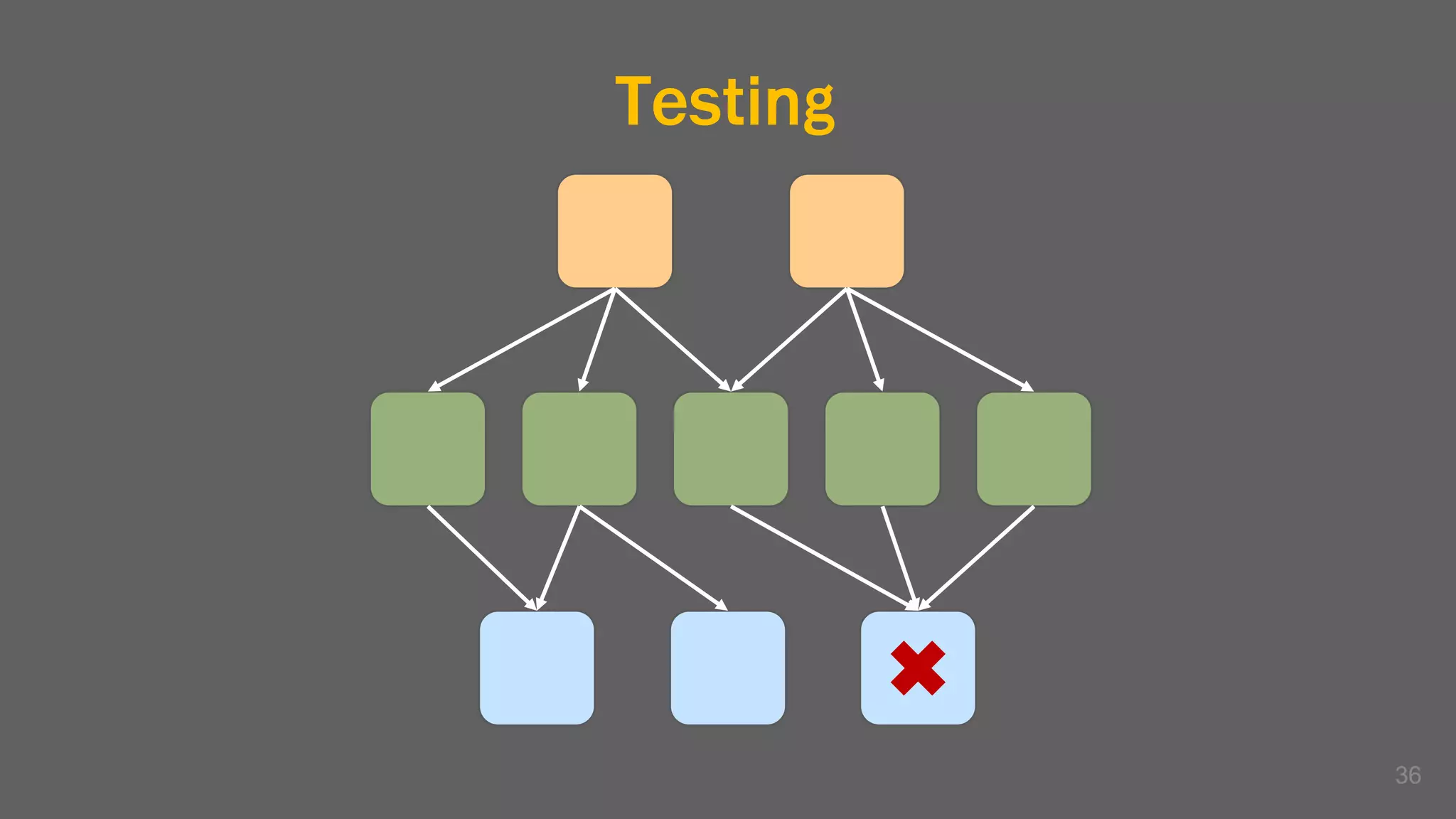
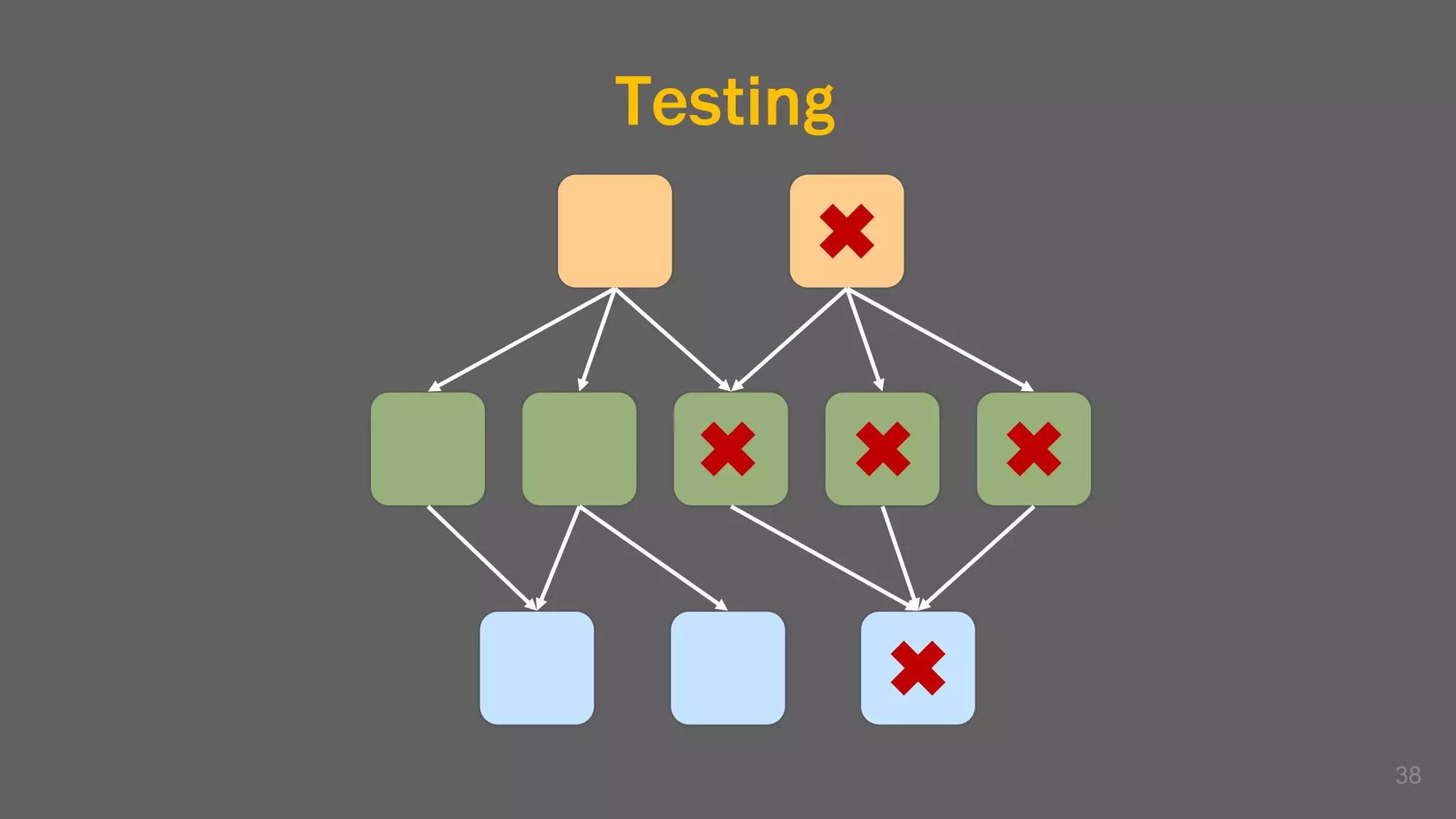
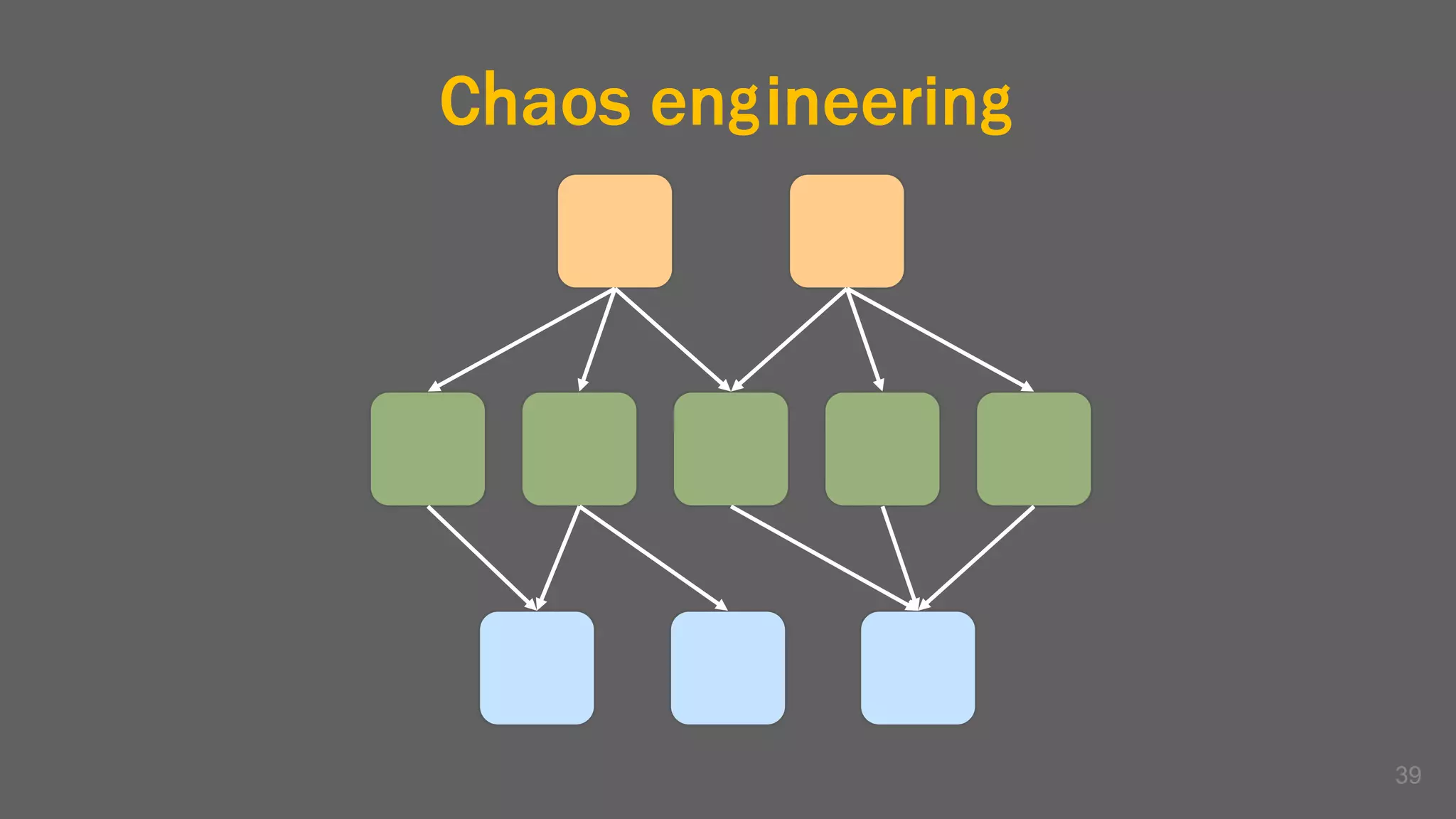
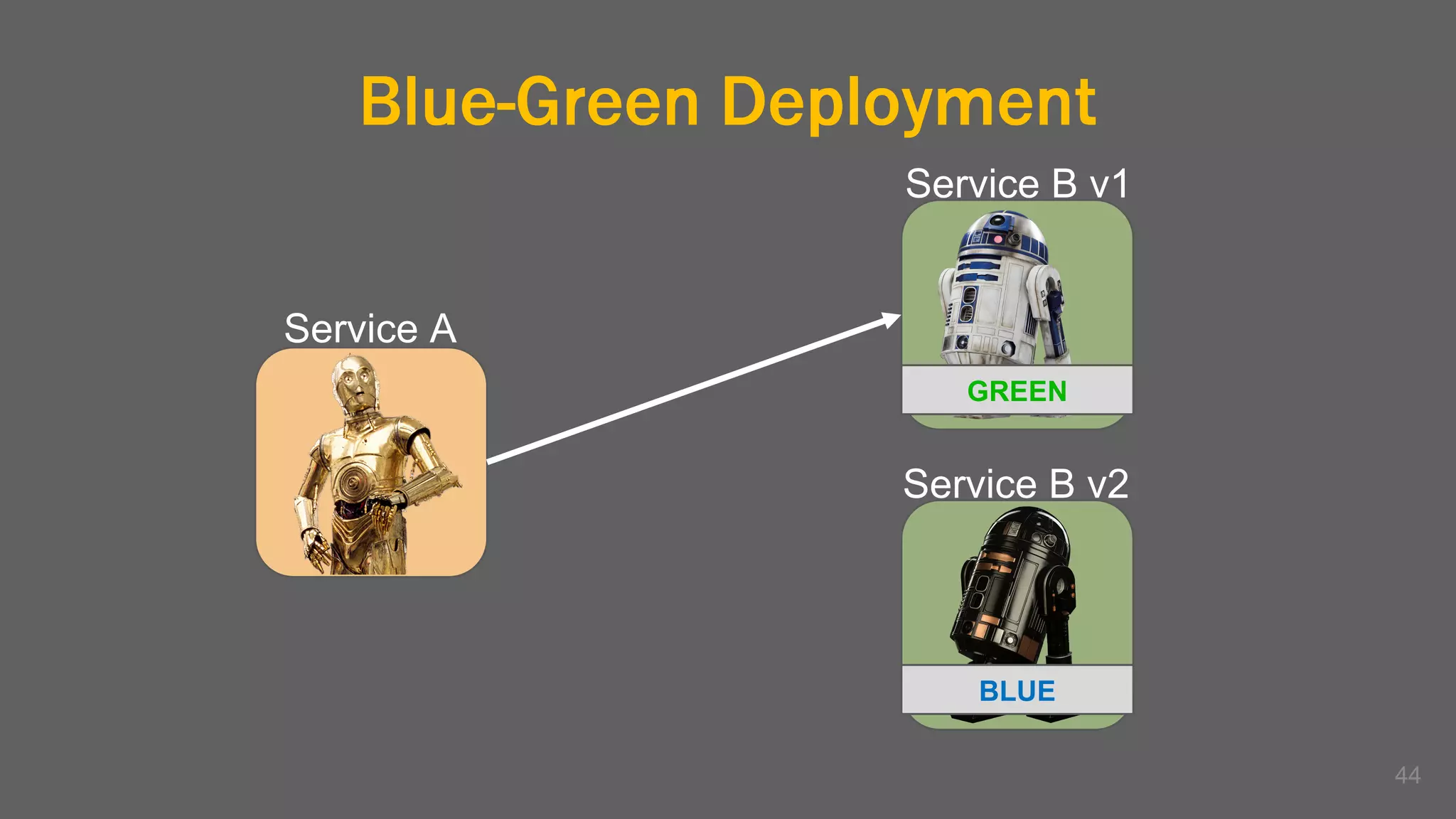
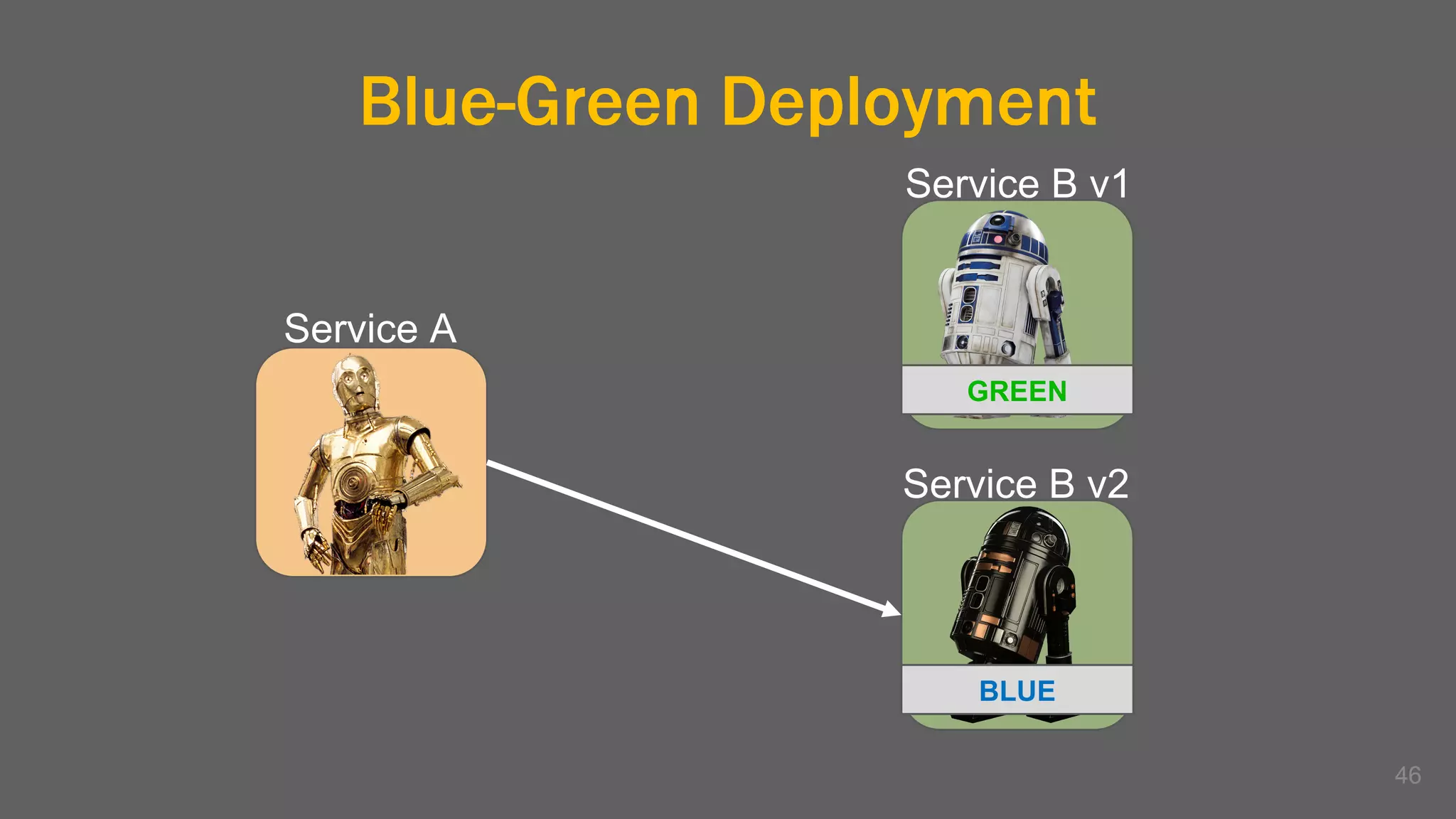
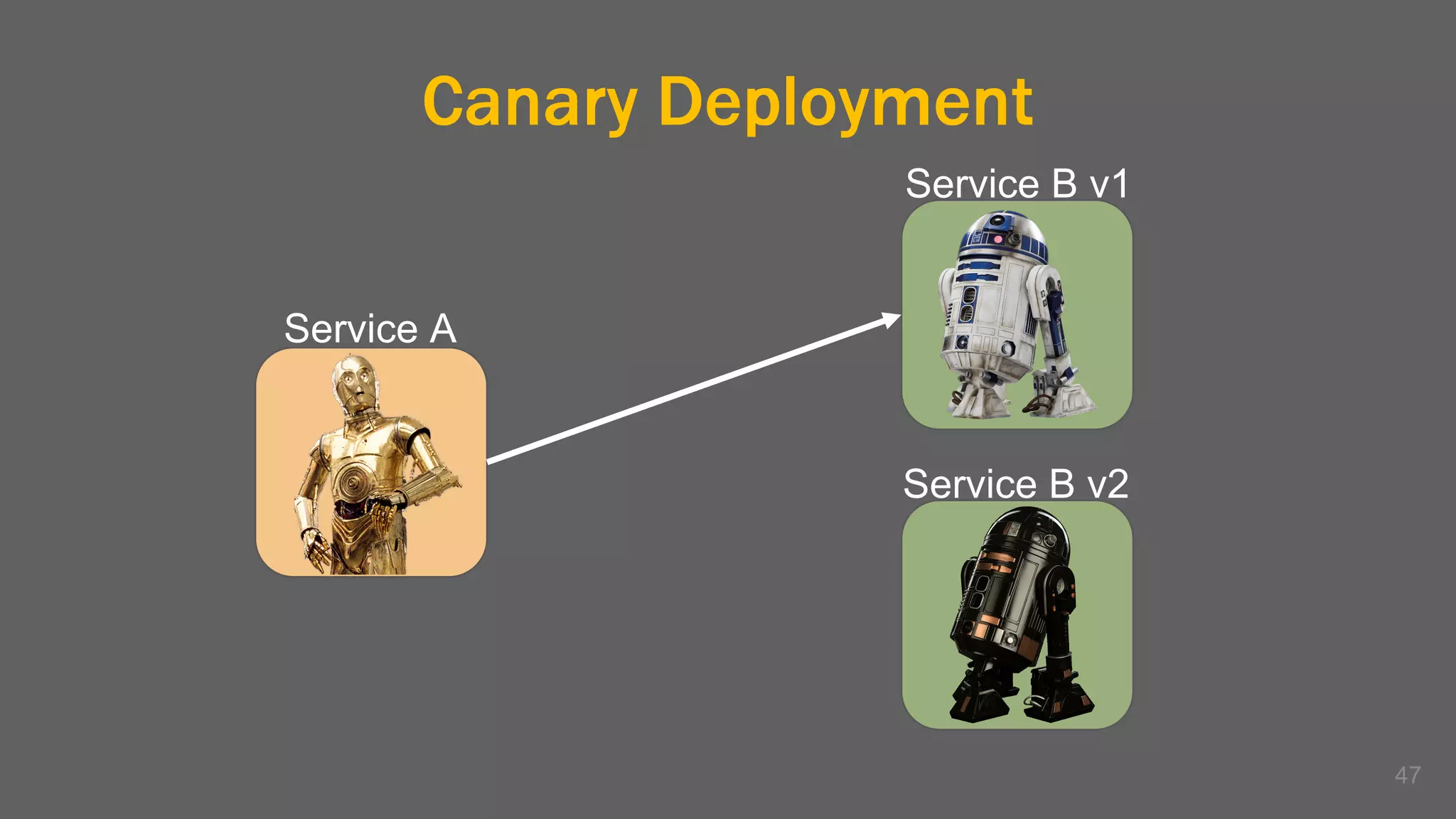
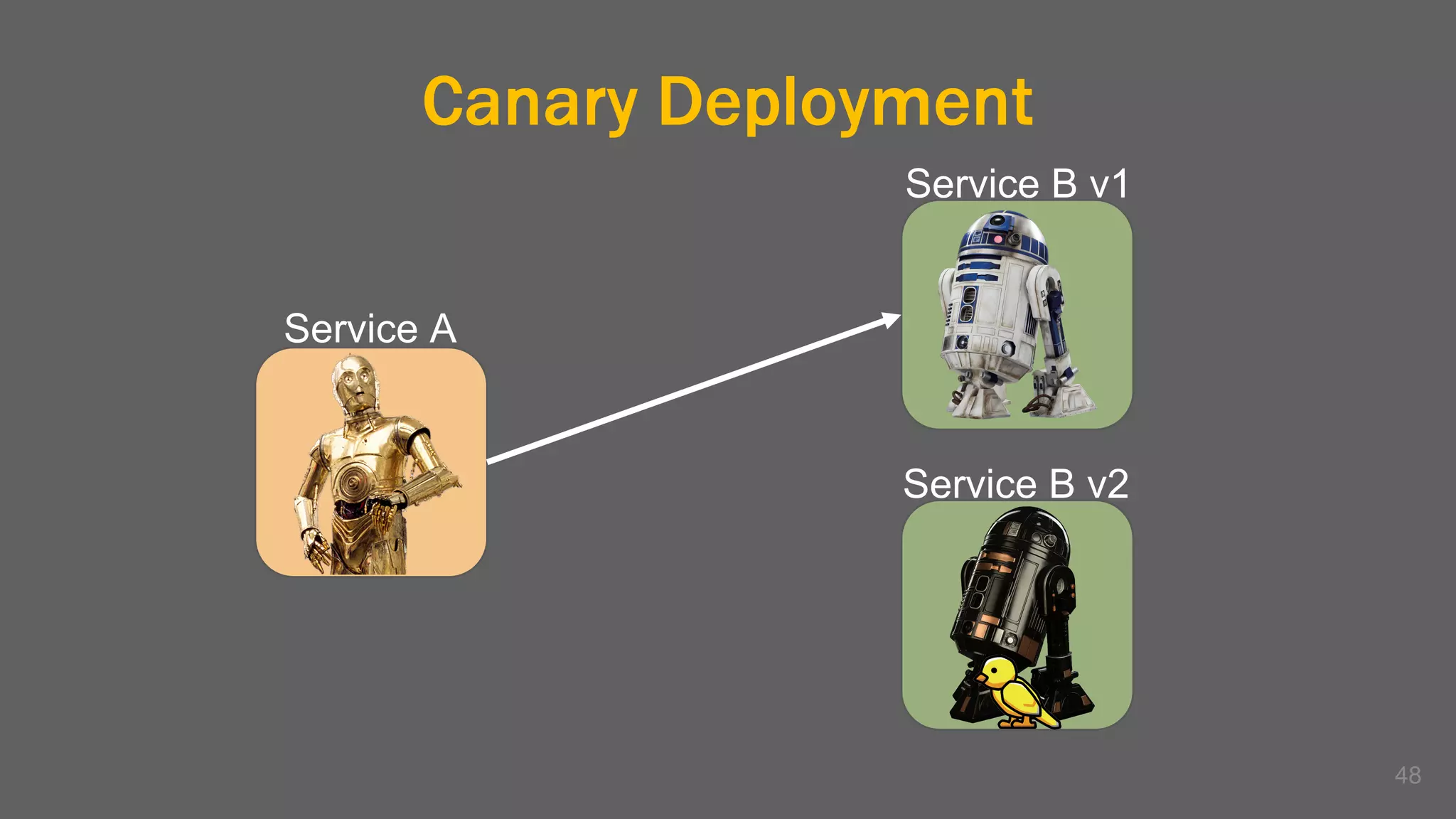
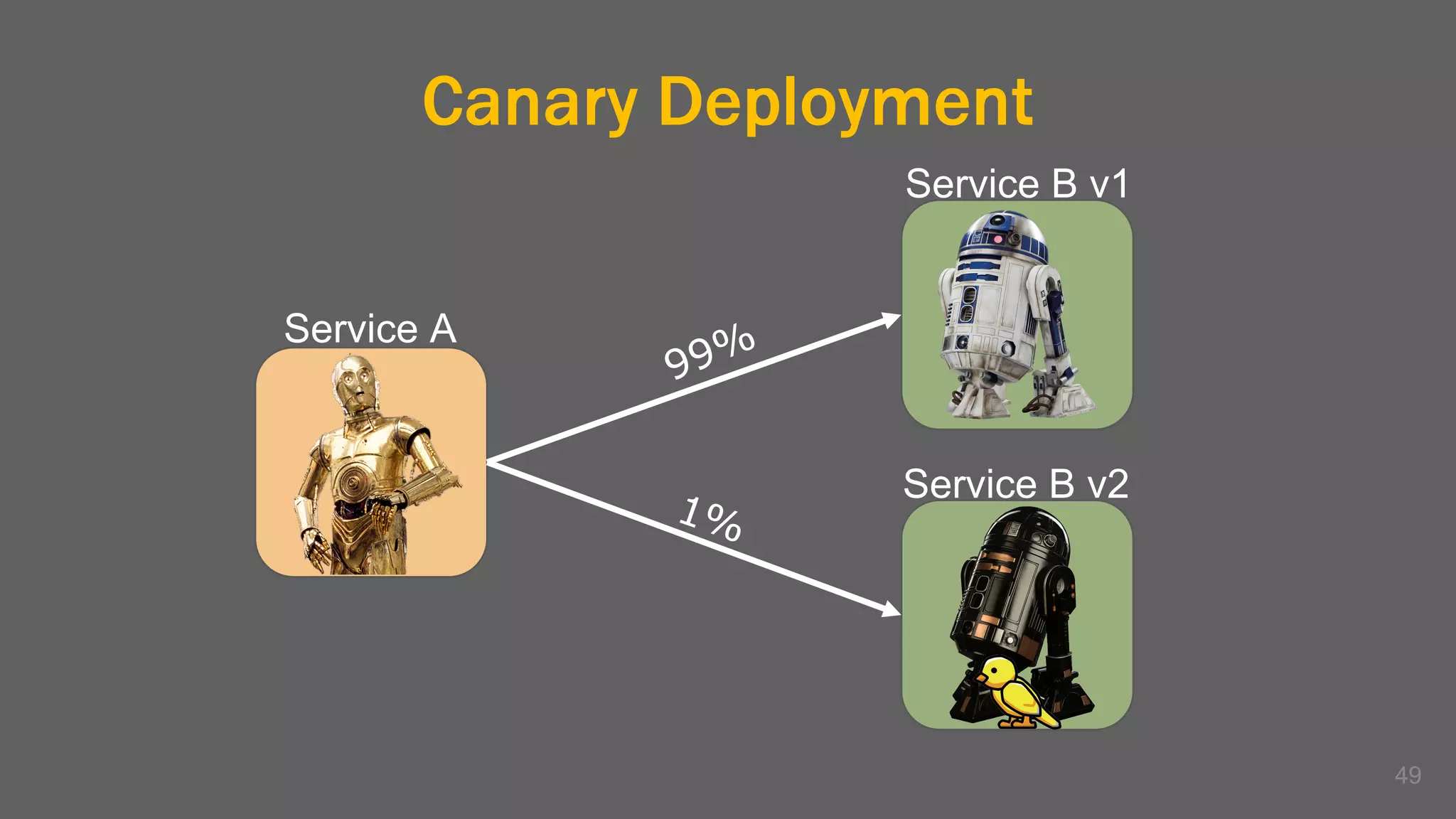
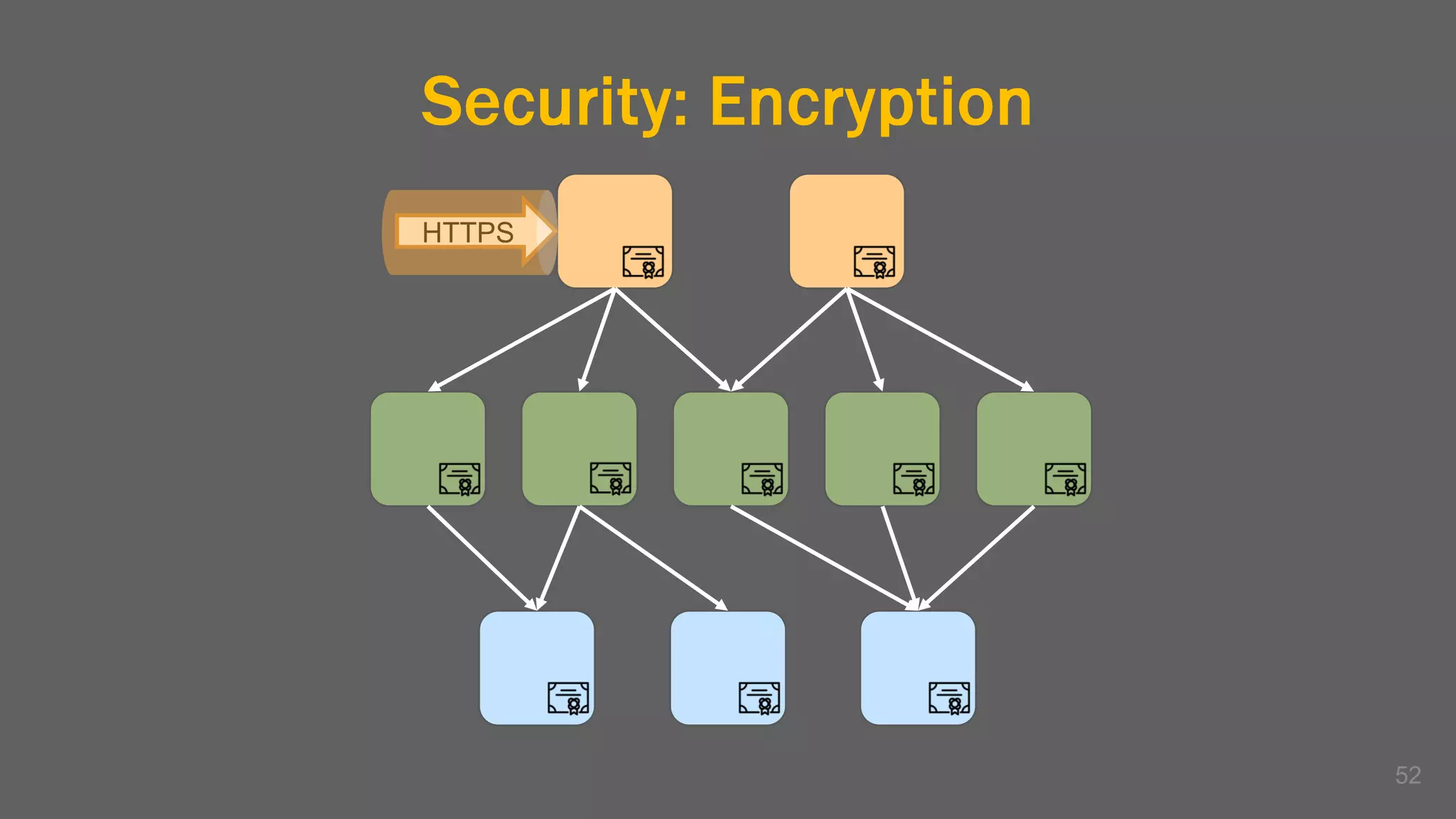
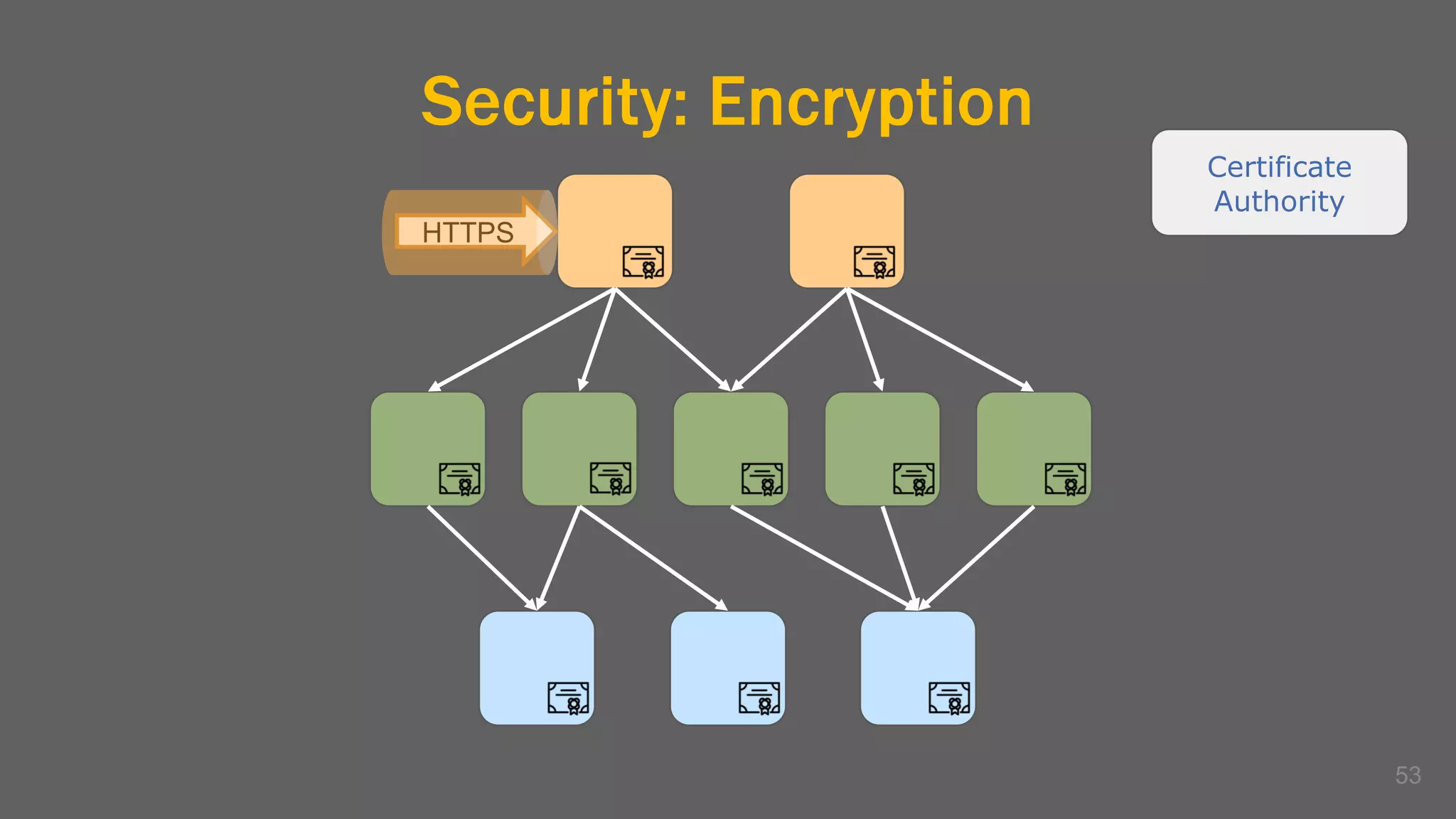
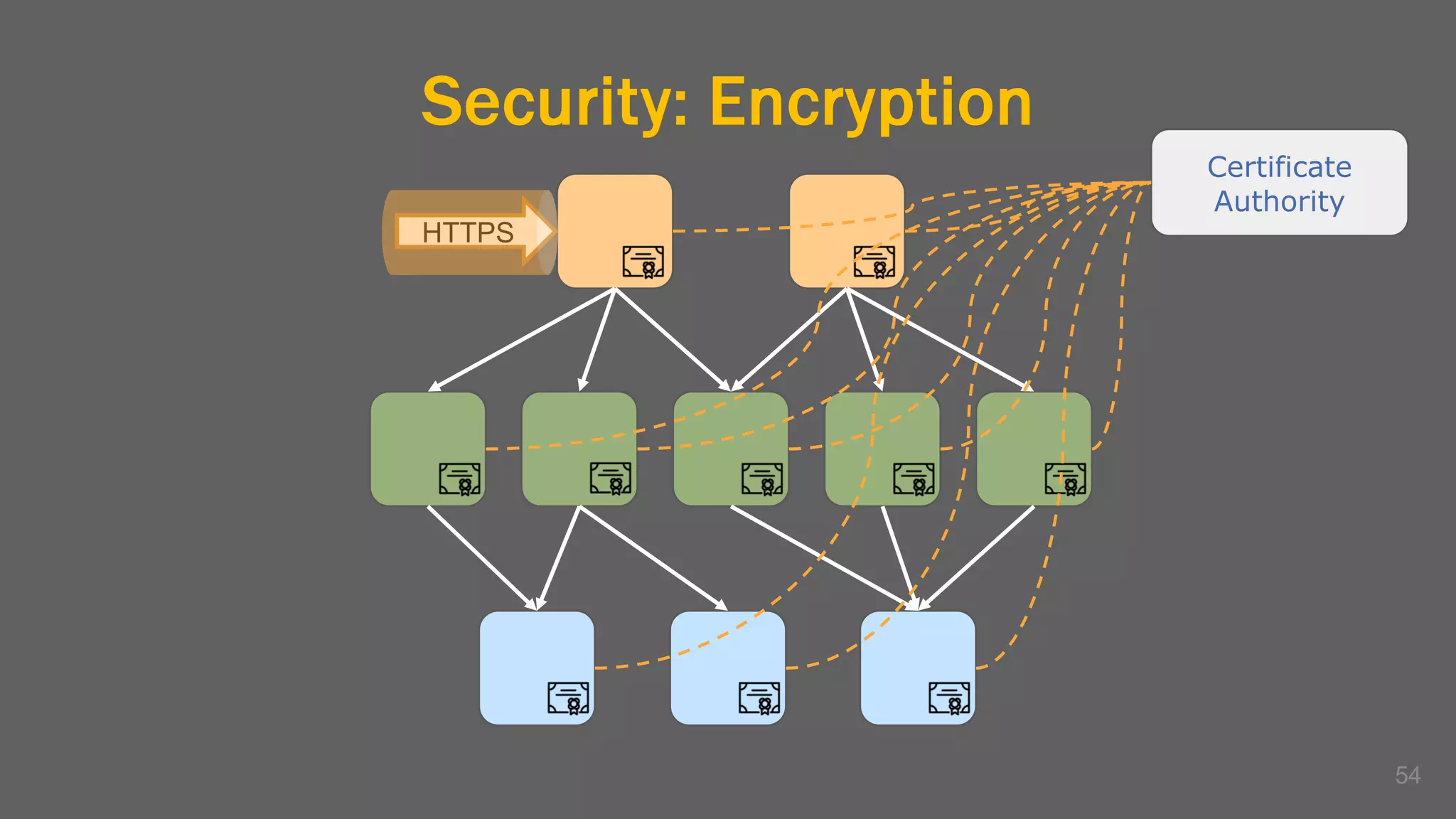
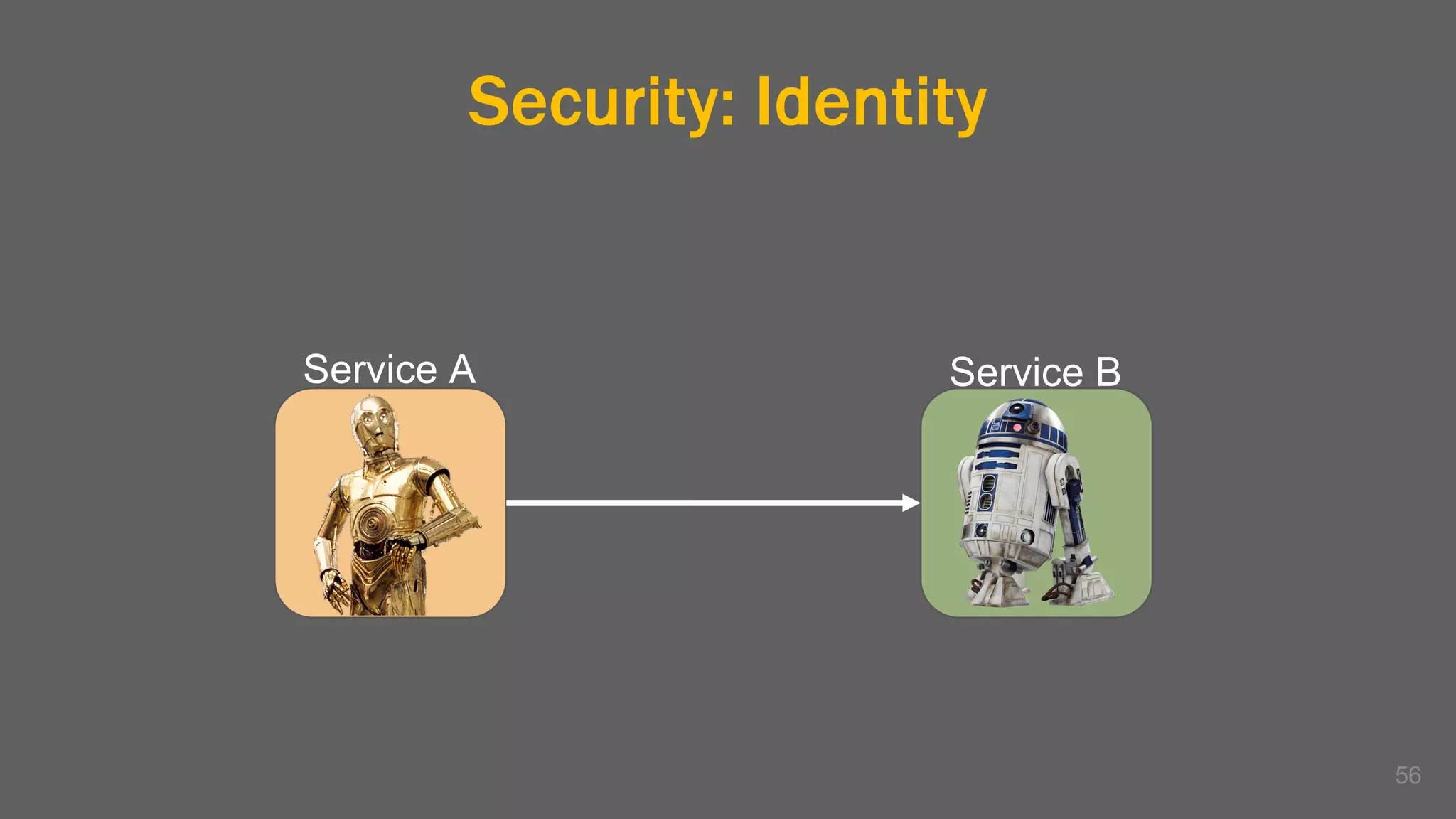
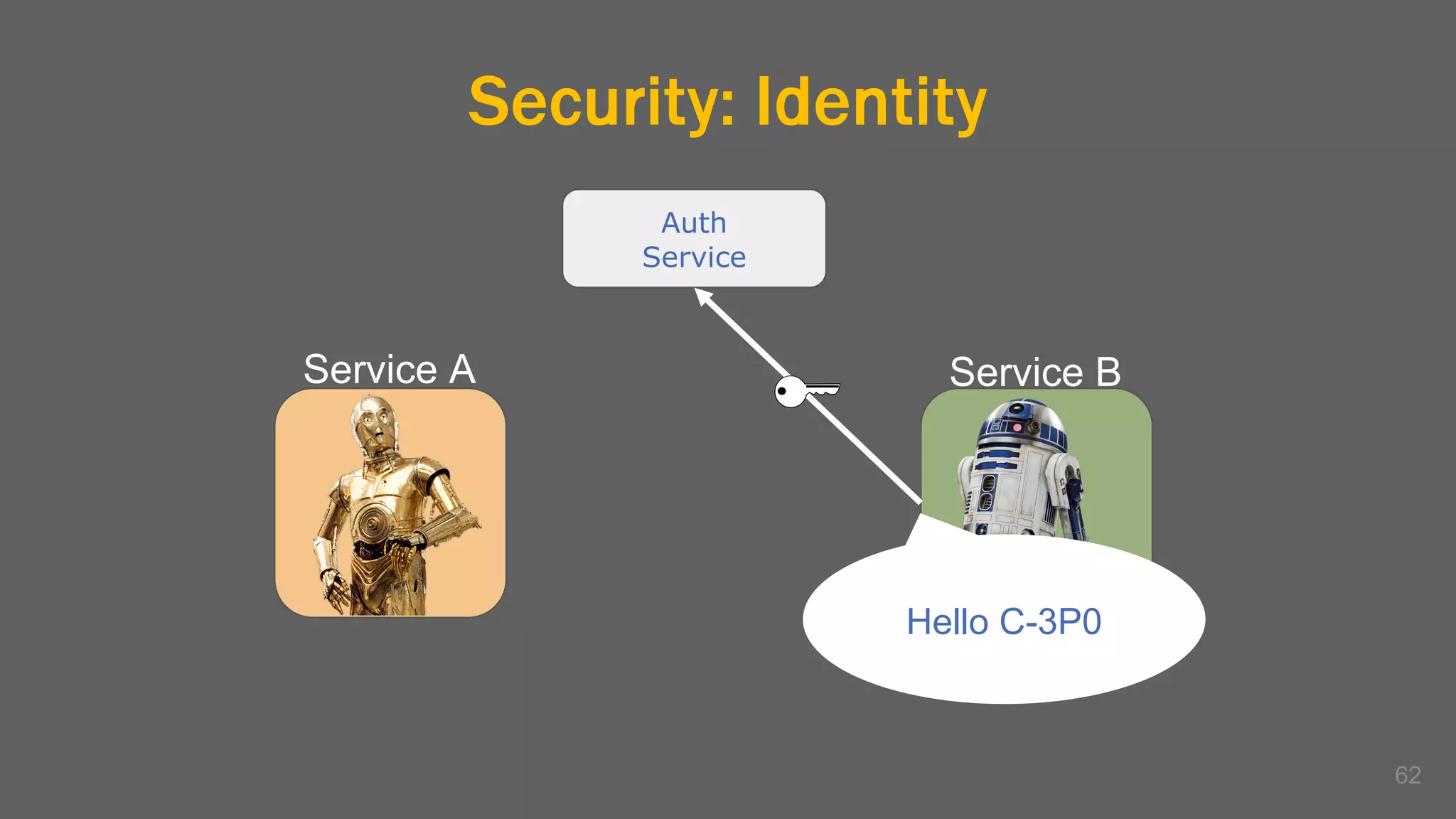
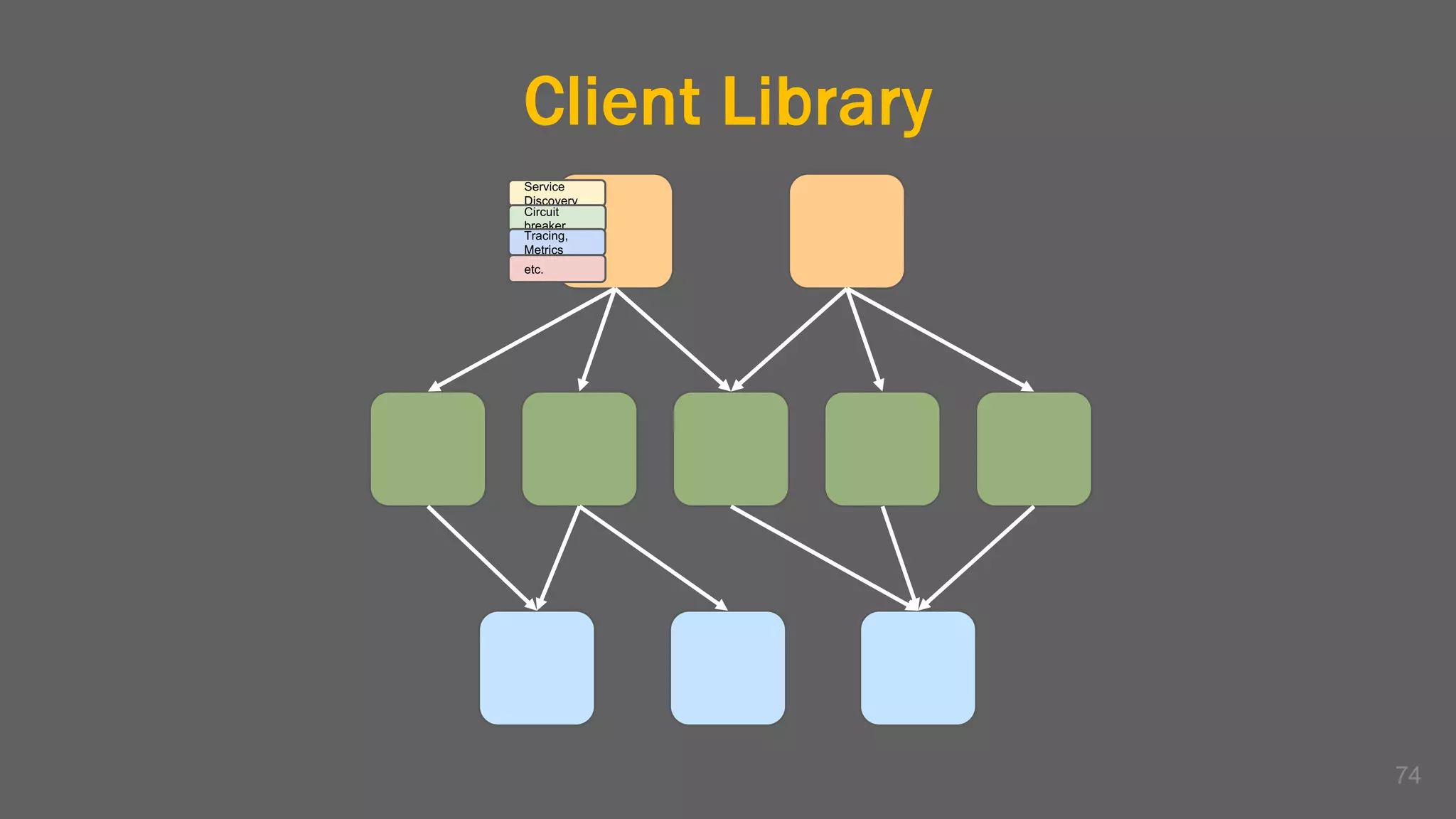
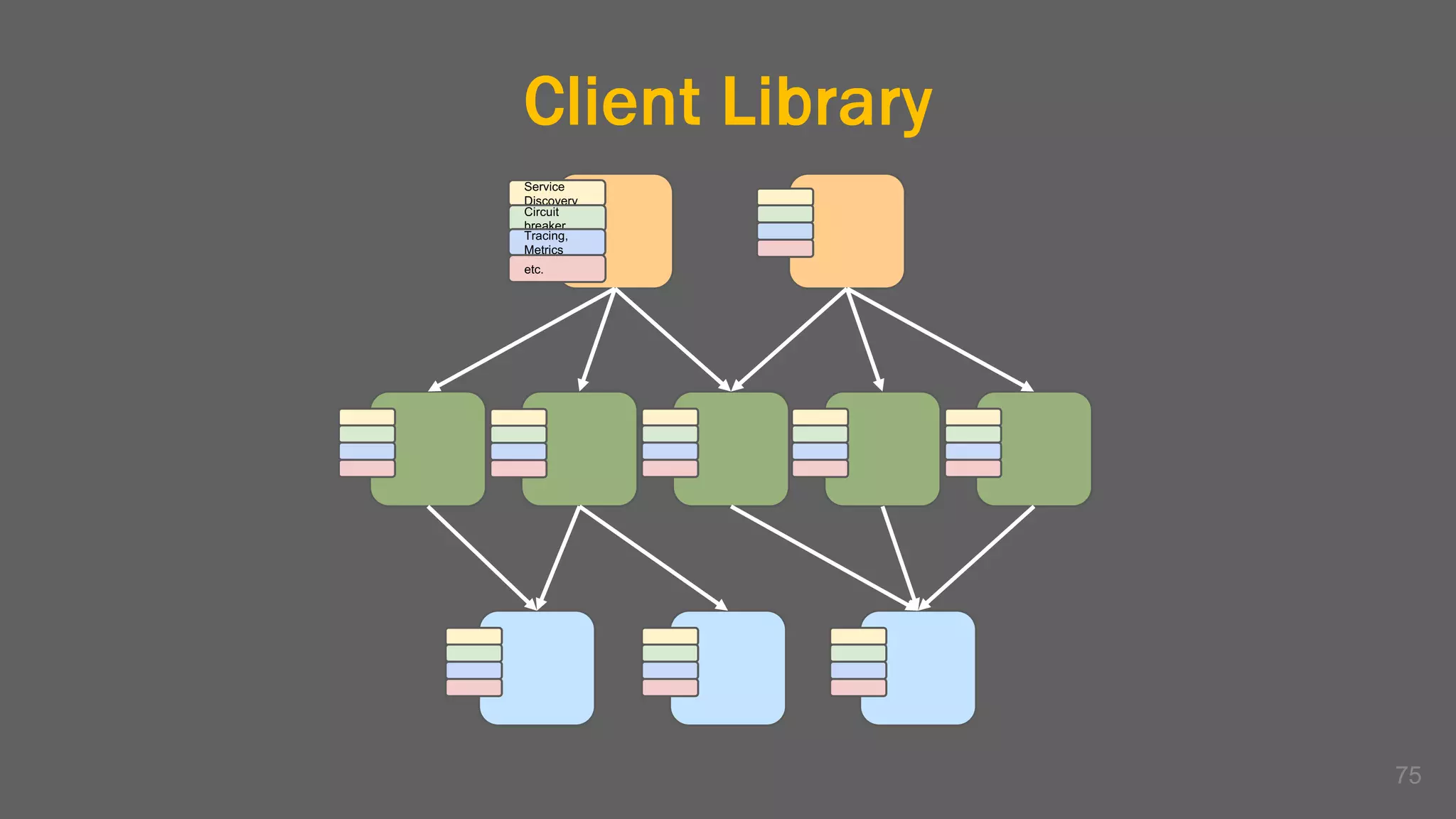
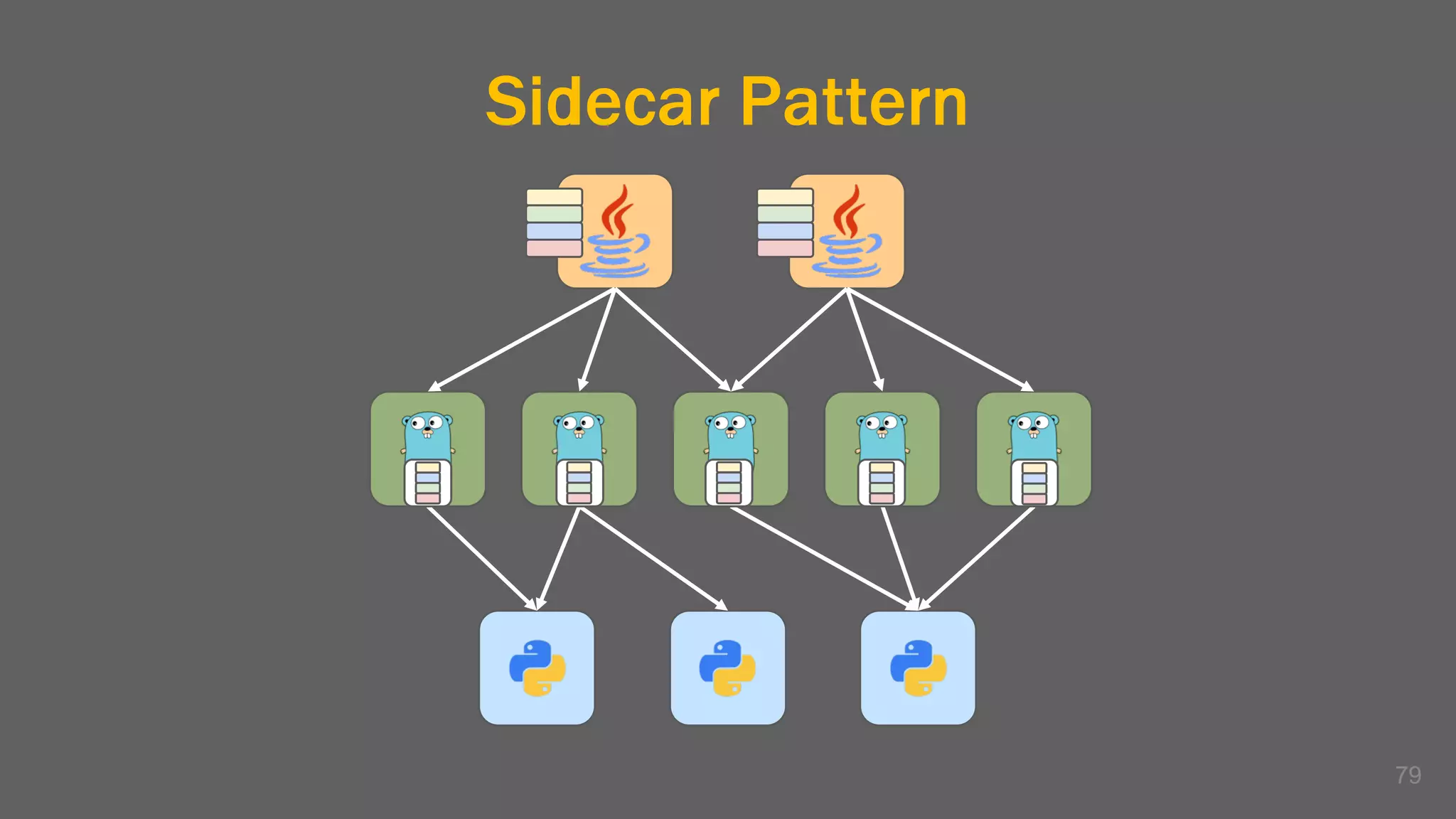
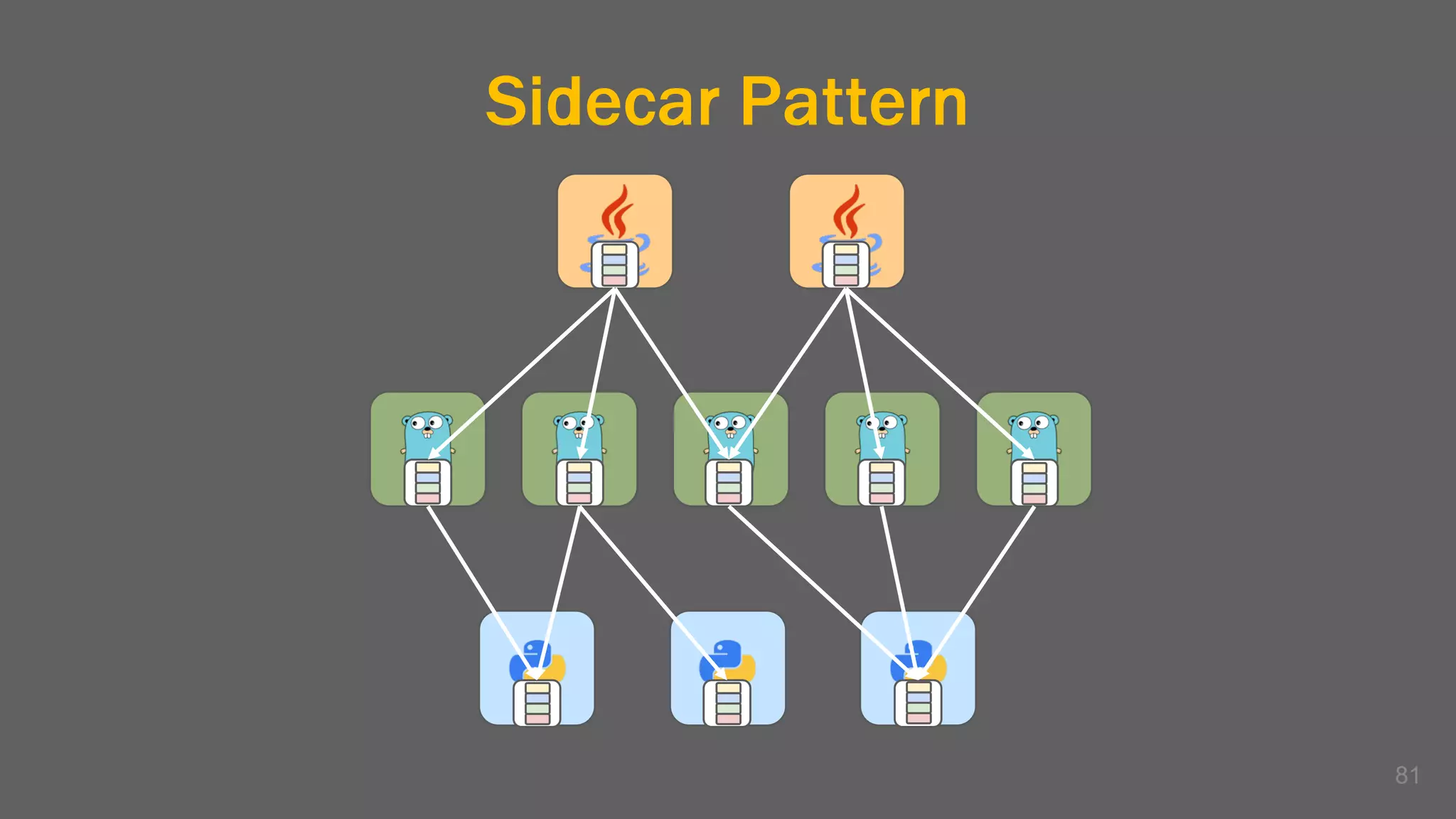
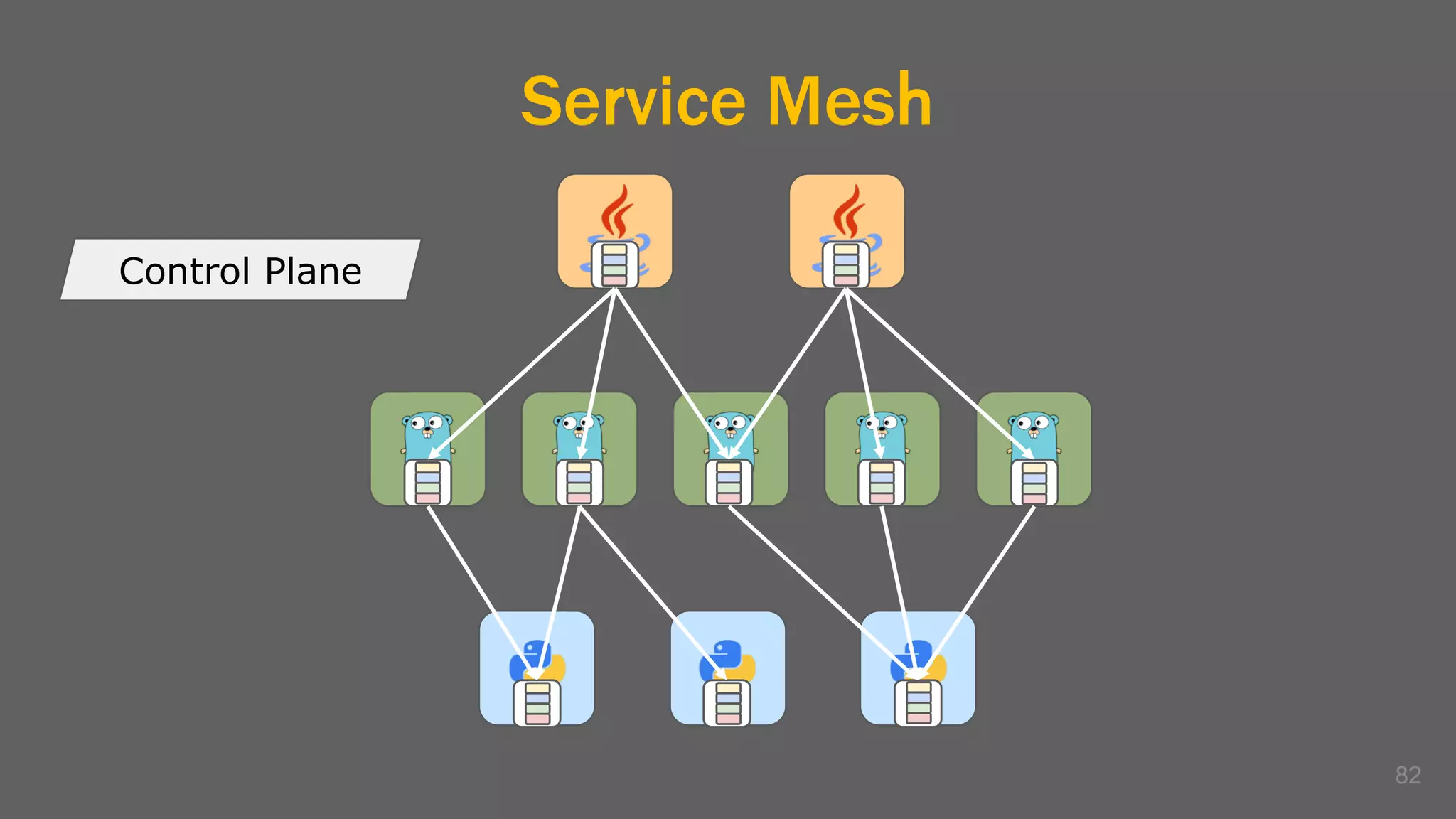
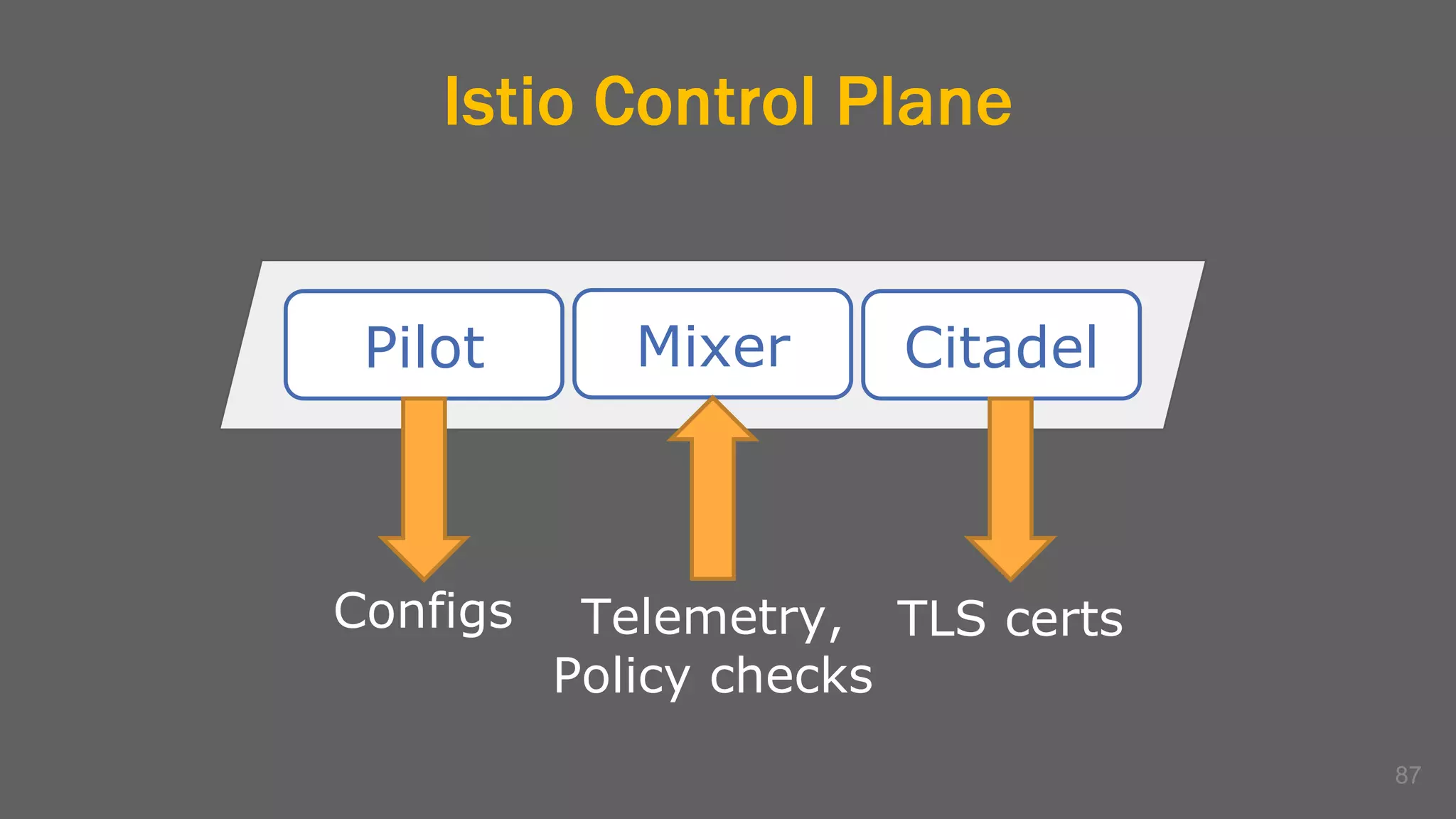
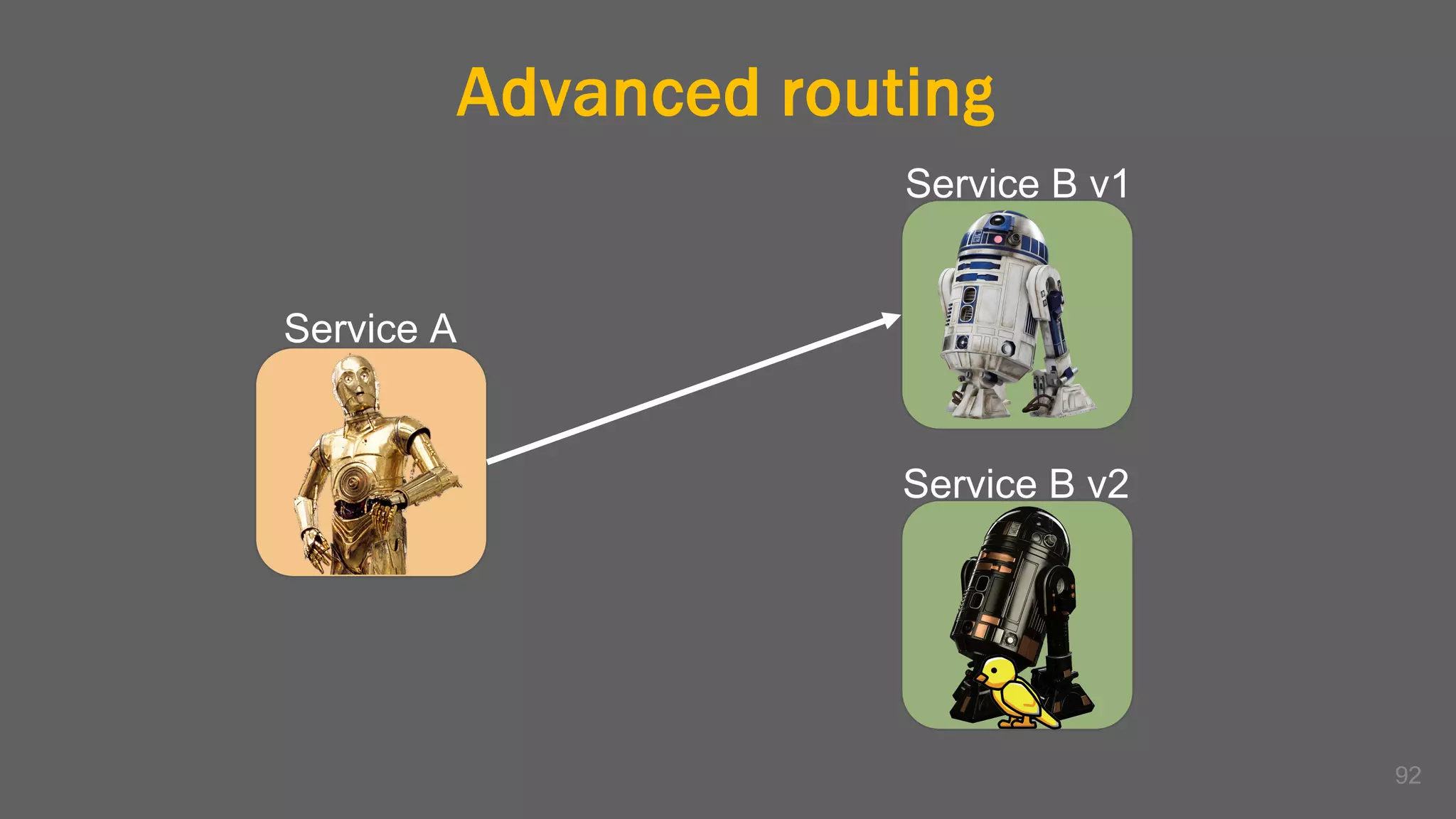
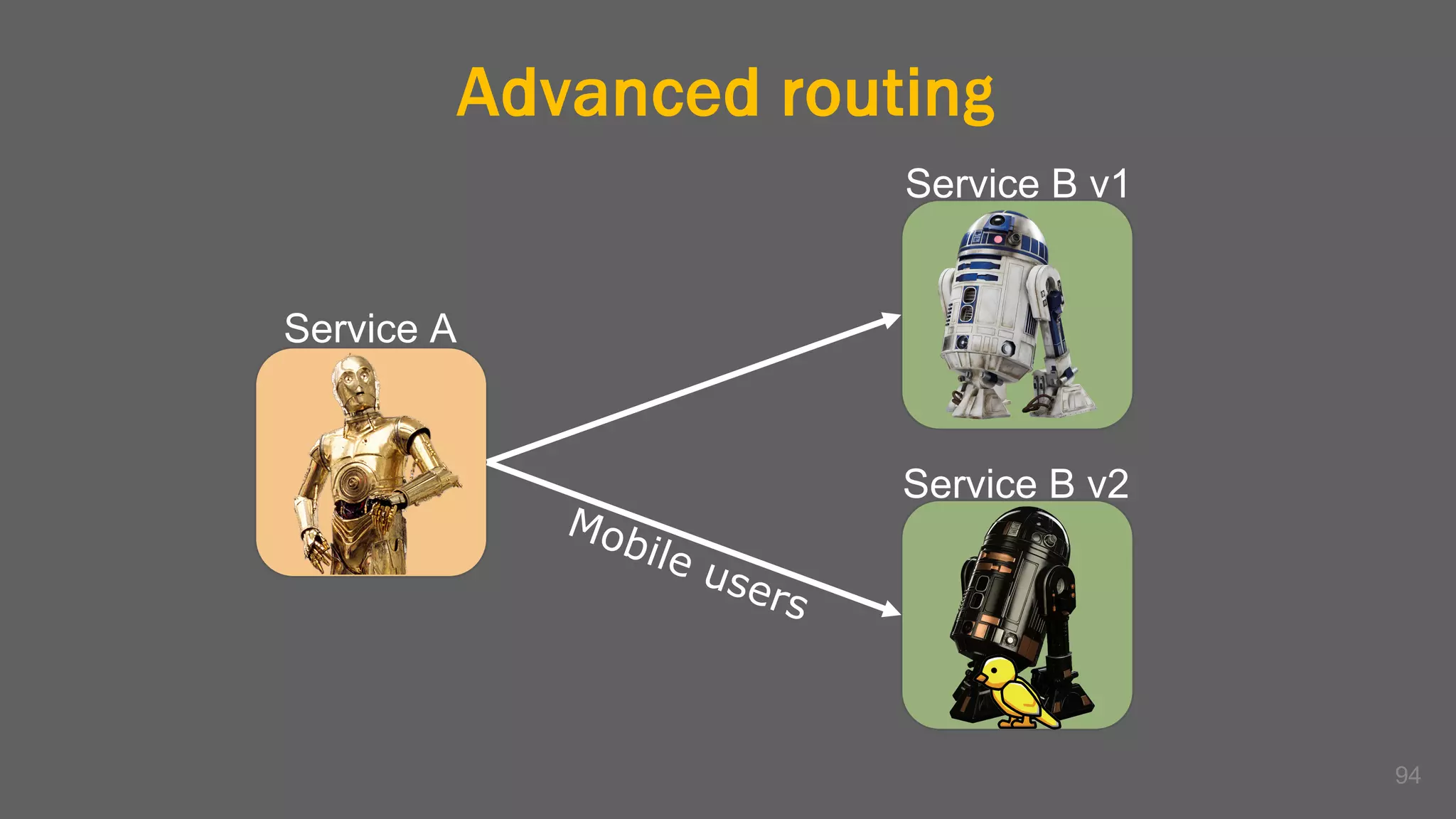
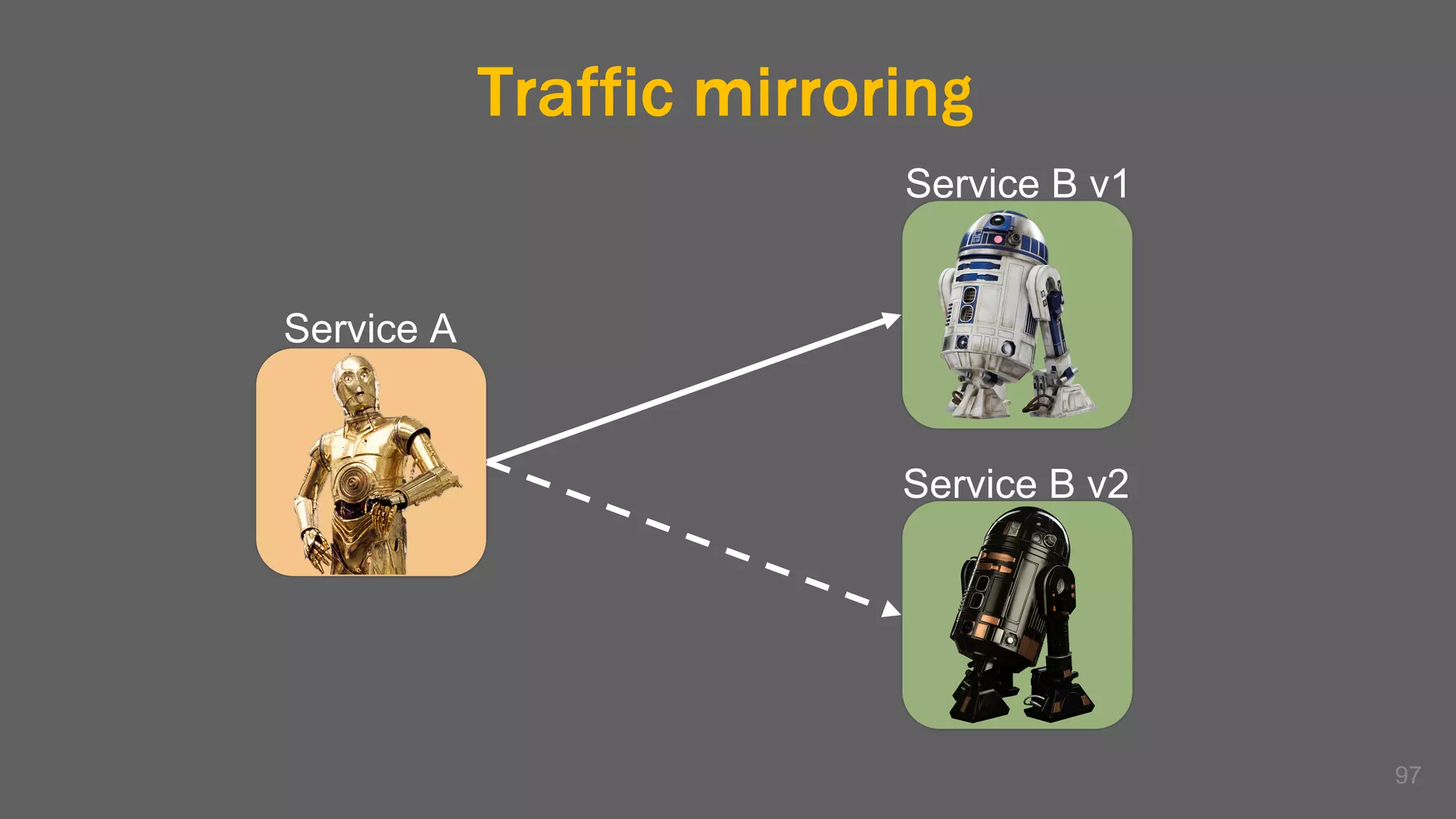
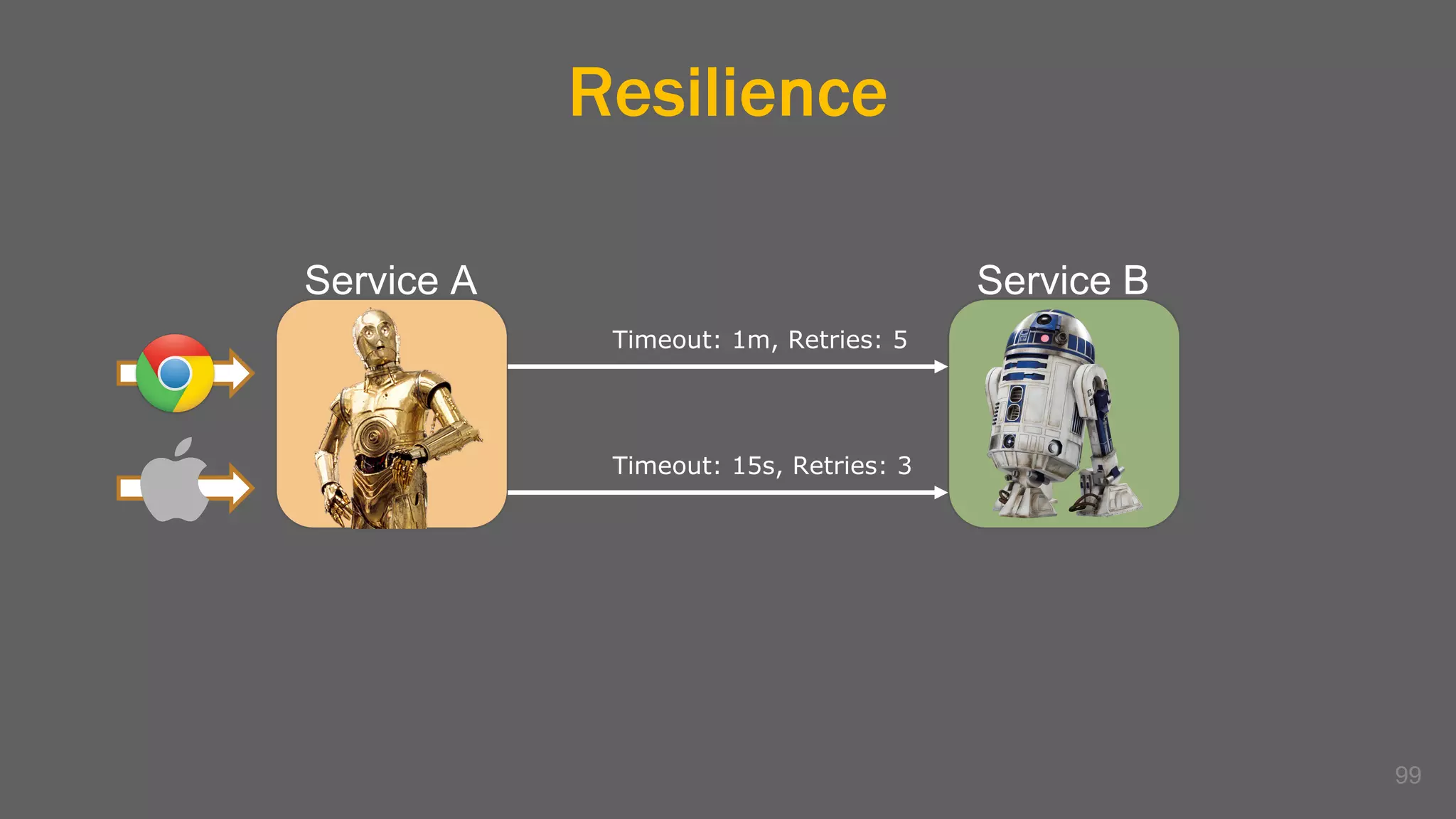
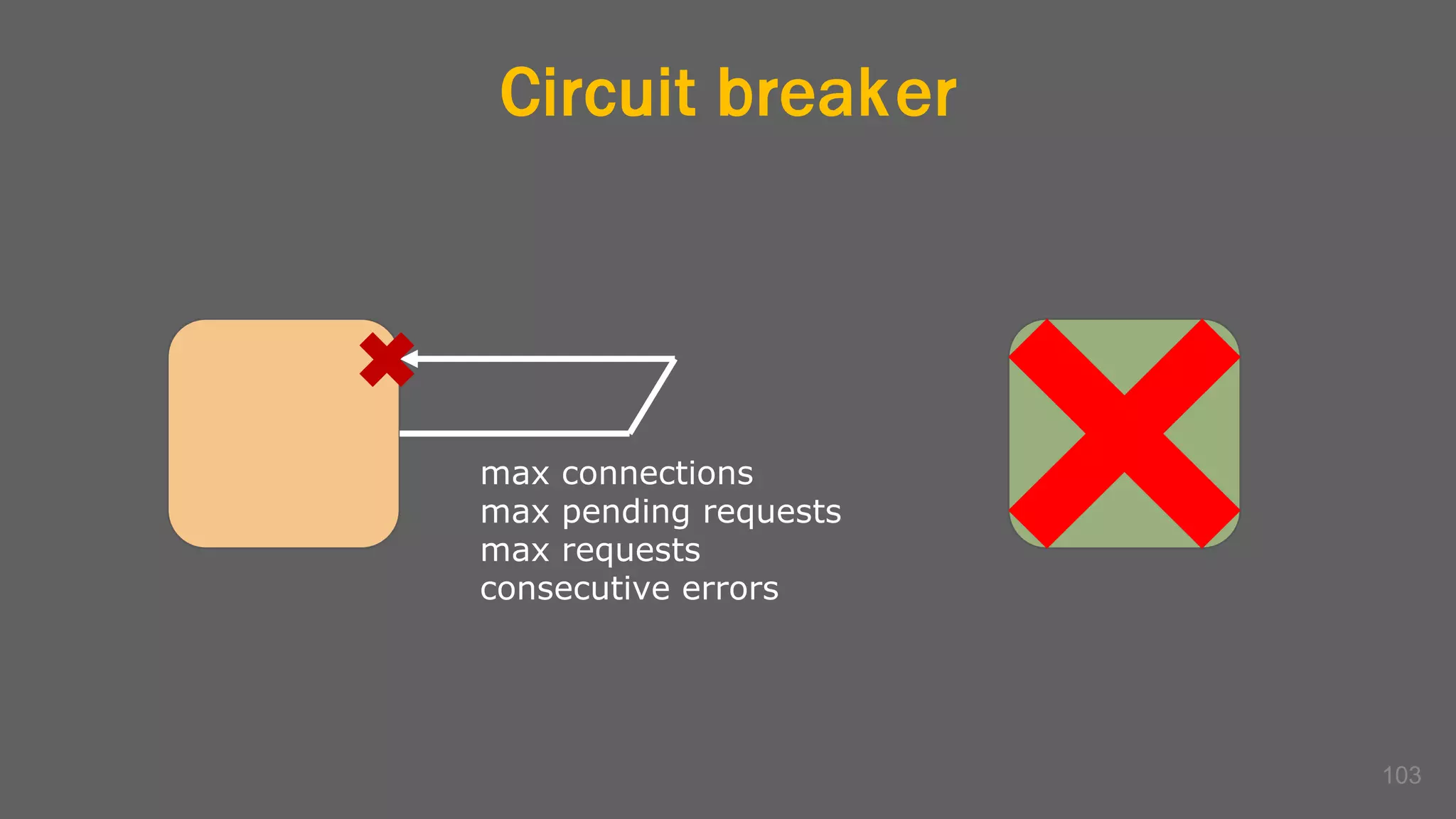
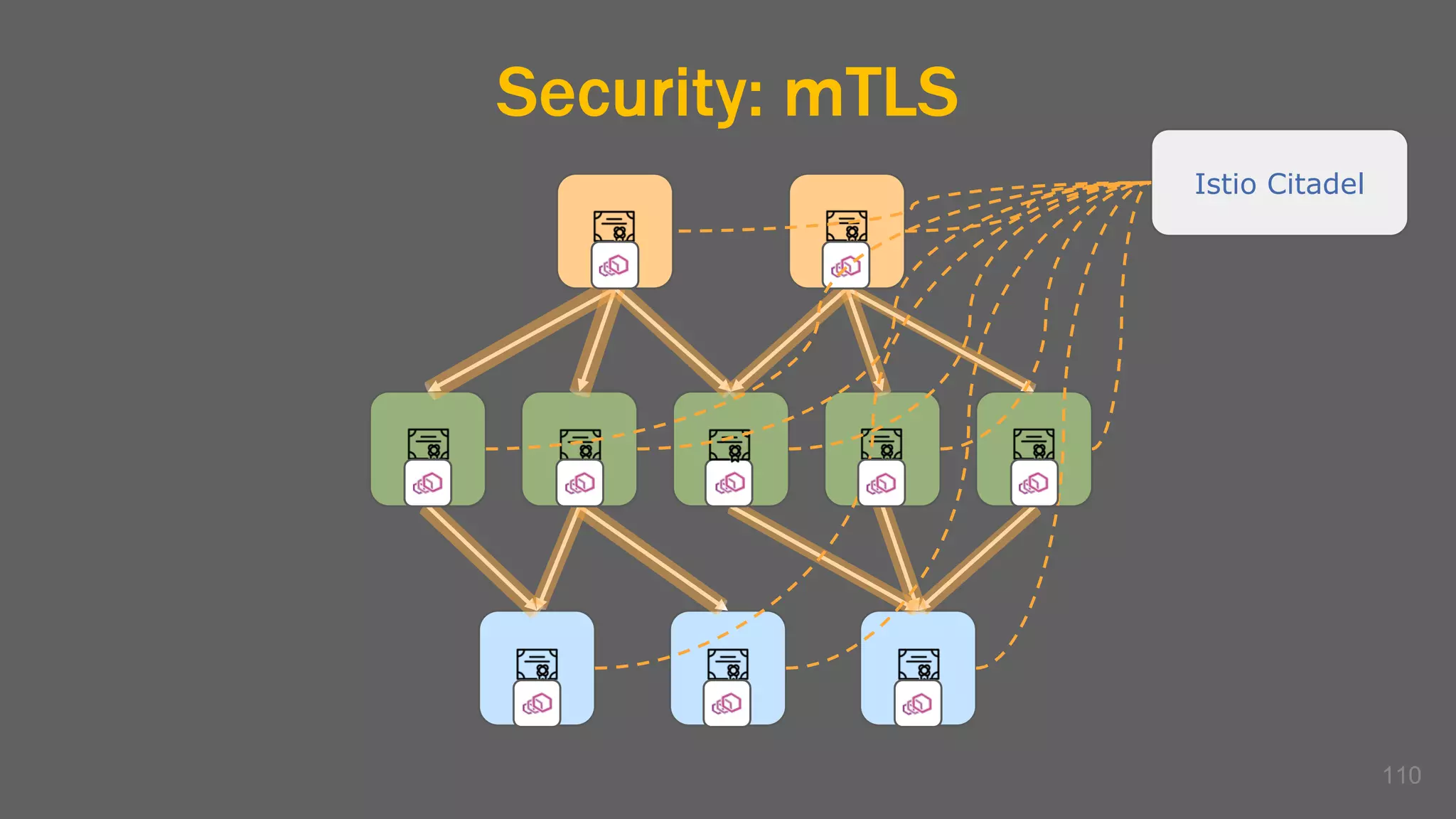
The document discusses the challenges, benefits, and complexities of microservices architecture, focusing on service mesh and Istio as a solution. It outlines key concepts such as service discovery, fault handling, security, and deployment strategies like blue-green and canary deployments. The presentation concludes with resources for further reading and emphasizes the importance of observability and technology choice in microservices deployment.