This document discusses cryptographic protocols and their analysis. It begins by covering the origins of cryptographic protocols and some key concepts like primitives, definitions, and modeling adversaries. It then addresses information policies protocols aim to achieve, like maintaining privacy or authenticating parties. The document outlines principles for analyzing protocols like Simmons's heuristics and separation of concerns. It also notes challenges like proving correctness and dealing with protocol composition. Finally, it introduces tools like Scyther for automated security analysis of protocols. In summary, the document provides an overview of cryptographic protocols, issues in their design and analysis, and techniques for evaluating their security.











![Separation of concerns
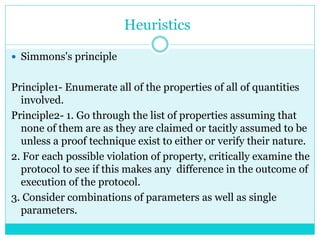
Divide and conquer is a useful principle in
algorithmic design.
A direct and natural problem partitioning attempt
for cryptographic protocol is to separate the concern
of crypto-primitives and cryptographic protocols.
An encryption of message m under secret key k
becomes abstracted and an ideal with [m]k, though a
detailed definition of what this notation means in
terms of security must be made too.](https://image.slidesharecdn.com/cryptographicprotocols-180403140345/85/Cryptographic-protocols-14-320.jpg)
![ A simple approach to cryptographic protocol
specification between an initiator I and responder R,
based on initialization of crypto-primitives c an go
like this:
1. I --> R: [NI, I] pk(R)
2. R--> I: [NI, NR] pk(I)
3. I --> R: [NR] pk(R)
This describes Needham -Schroeder public based
mutual authentication protocol.](https://image.slidesharecdn.com/cryptographicprotocols-180403140345/85/Cryptographic-protocols-15-320.jpg)
![ResponderInitiator
Nonce NI
[NI, I] pk(R)
[NI, NR] pk(I) Nonce NR
R authenticated
NI , NR Secret [NR] pk(R) I authenticated
NI , NR Secret
Fig. Needham –Schroder public key based authentication protocol](https://image.slidesharecdn.com/cryptographicprotocols-180403140345/85/Cryptographic-protocols-16-320.jpg)
![More prudent engineering advice
Basic principle1: Explicit communication
Every message should say what it means : its
interpretation depends on its content.
Basic principle2: Appropriate Conditions for Actions
The conditions for [received] message to be acted upon
should be clearly set out so that someone receiving a
design may see whether they are acceptable or not.](https://image.slidesharecdn.com/cryptographicprotocols-180403140345/85/Cryptographic-protocols-17-320.jpg)