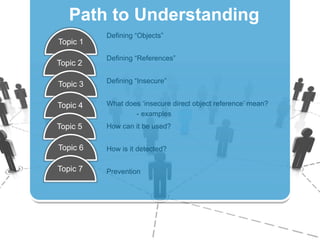
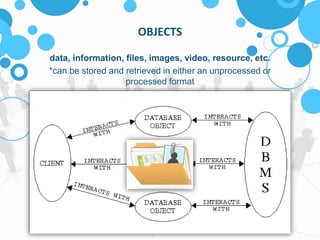
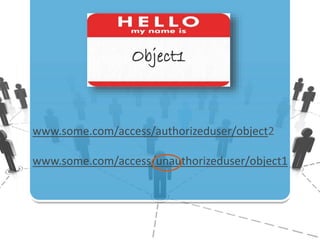
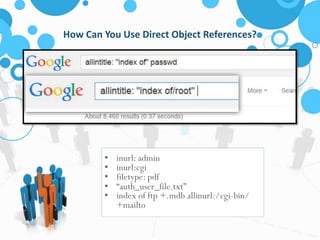
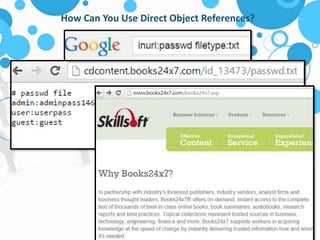
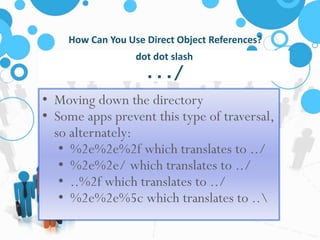
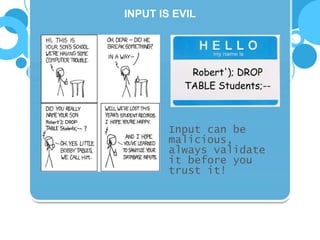
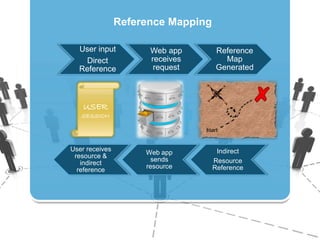
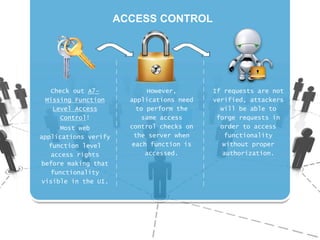
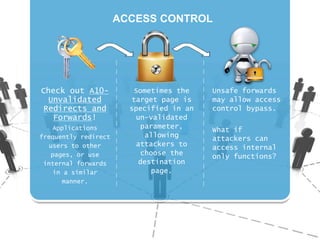
The document discusses insecure direct object references (IDOR) and their implications in information security, highlighting how developers can unintentionally expose access to internal objects without proper checks. It emphasizes the need for access control validations in web applications to prevent unauthorized access and provides examples and prevention techniques for developers. Additionally, it references OWASP guidelines and various sources for further information about IDOR vulnerabilities.