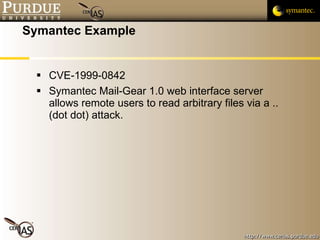
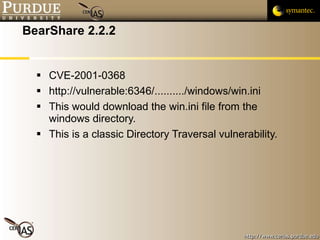
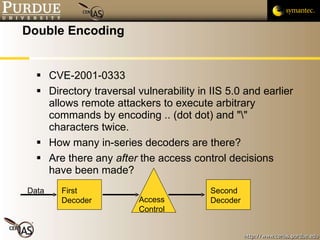
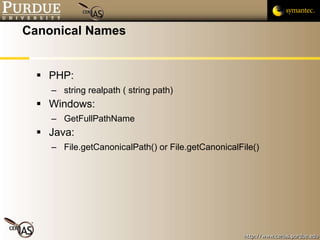
The document discusses canonicalization and directory traversal vulnerabilities. It explains that canonicalization ensures files have a standard name without symlinks or duplicate characters. Directory traversal occurs when a request contains ".." to access files outside the intended directory. The document recommends canonicalizing file paths using OS functions and using chroot jails to limit processes to a subdirectory.























![Chroot Chroot changes the filesystem "root". The applications in a chroot jail can't use files outside the visible root of the filesystem They are "jailed" down in a subdirectory Example chdir("/foo/bar"); chroot("/foo/bar"); chroot [-u -user] [-g -group] [-G -group,group,...] newroot [command]](https://image.slidesharecdn.com/7-canondt-091013224335-phpapp02/85/7-Canon-Dt-31-320.jpg)



![Pascal Meunier [email_address] Contributors: Jared Robinson, Alan Krassowski, Craig Ozancin, Tim Brown, Wes Higaki, Melissa Dark, Chris Clifton, Gustavo Rodriguez-Rivera](https://image.slidesharecdn.com/7-canondt-091013224335-phpapp02/85/7-Canon-Dt-37-320.jpg)