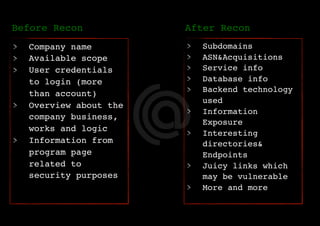
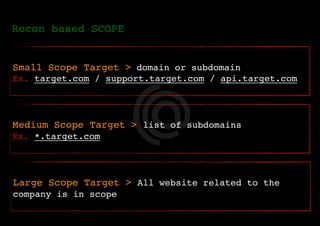
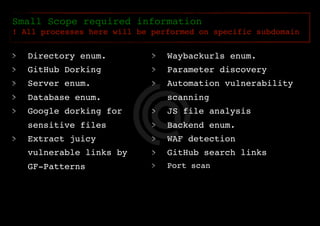
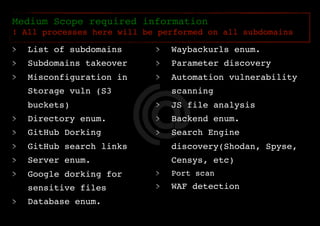
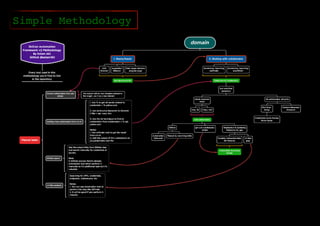
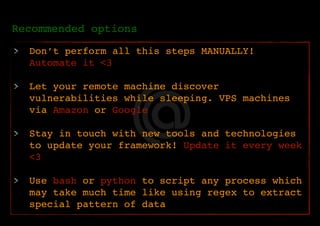
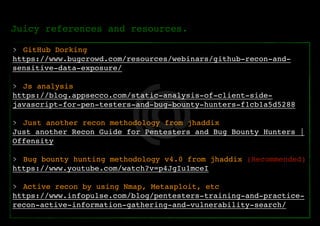
The document outlines a methodology for reconnaissance in penetration testing, including different types of recon (passive and active) and the information required based on the scope of the target. It emphasizes automating the recon process and provides resources and tools to enhance vulnerability discovery. Recommendations for practices and links to additional resources are also included.