DFS.pdf
•
0 likes•7 views
This document discusses depth-first search (DFS), a graph traversal algorithm that visits vertices in an order where all neighbors of a vertex are explored before moving to the next vertex. It describes the basic DFS algorithm, properties of DFS like producing a spanning tree, and applications of DFS like solving maze problems and finding paths/cycles in graphs.
Report
Share
Report
Share
Download to read offline
Recommended
Ppt 1

This document discusses several graph algorithms:
1) Topological sort is an ordering of the vertices of a directed acyclic graph (DAG) such that for every edge from vertex u to v, u comes before v in the ordering. It can be used to find a valid schedule respecting dependencies.
2) Strongly connected components are maximal subsets of vertices in a directed graph such that there is a path between every pair of vertices. An algorithm uses depth-first search to find SCCs in linear time.
3) Minimum spanning trees find a subset of edges that connects all vertices at minimum total cost. Prim's and Kruskal's algorithms find minimum spanning trees using greedy strategies in O(E
Topological Sort

This document discusses several graph algorithms:
1) Topological sort is an ordering of the vertices of a directed acyclic graph (DAG) such that for every edge from vertex u to v, u comes before v in the ordering. It can be used to find a valid schedule respecting dependencies.
2) Strongly connected components are maximal subsets of vertices in a directed graph such that there is a path between every pair of vertices. An algorithm uses depth-first search to find SCCs in linear time.
3) Minimum spanning trees find a subset of edges that connects all vertices at minimum total cost. Prim's and Kruskal's algorithms find minimum spanning trees using greedy strategies in O(E
topological_sort_strongly Connected Components

The document describes algorithms for depth-first search (DFS) and how it can be used to find strongly connected components (SCCs) in a directed graph. DFS assigns discovery and finish times to vertices and classifies graph edges. It can determine if a graph is acyclic by checking for back edges. To find SCCs, DFS is run on the original graph and its transpose to group vertices reachable from each other into components. The result is a directed acyclic graph of components. Lemmas are presented about paths between components based on discovery/finish times.
Unit ii-ppt

The document discusses optimization problems and various graph search algorithms. It covers:
- Formulating optimization problems as finding the best solution from all feasible solutions.
- Graph search algorithms like breadth-first search and depth-first search that can be used to find optimal solutions by traversing graphs.
- Dijkstra's algorithm, a graph search algorithm that finds the shortest paths between nodes in a graph.
Prim's Algorithm on minimum spanning tree

Prim's algorithm is used to find the minimum spanning tree of a connected, undirected graph. It works by continuously adding edges to a growing tree that connects vertices. The algorithm maintains two lists - a closed list of vertices already included in the minimum spanning tree, and a priority queue of open vertices. It starts with a single vertex in the closed list. Then it selects the lowest cost edge that connects an open vertex to a closed one, adds it to the tree and updates the lists. This process repeats until all vertices are in the closed list and connected by edges in the minimum spanning tree. The algorithm runs in O(E log V) time when using a binary heap priority queue.
graphin-c1.pnggraphin-c1.txt1 22 3 83 44 5.docx

graphin-c1.png
graphin-c1.txt
1: 2
2: 3 8
3: 4
4: 5
5: 3
6: 7
7: 3 6 8
8: 1 9
9: 1
graphin-c2.jpg
graphin-c2.txt
1: 2 9
2: 3 8
3: 4
4: 5 9
5: 3
6: 7
7: 3 6 8
8: 1
9:
graphin-DAG.png
graphin-DAG.txt
1: 2
2: 3 8
3: 4
4: 5
5: 9
6: 4 7
7: 3 8
8: 9
9:
CS 340 Programming Assignment III:
Topological Sort
Description: You are to implement the Depth-First Search (DFS) based algorithm for (i)
testing whether or not the input directed graph G is acyclic (a DAG), and (ii) if G is a DAG,
topologically sorting the vertices of G and outputting the topologically sorted order.
I/O Specifications: You will prompt the user from the console to select an input graph
filename, including the sample file graphin.txt as an option. The graph input files must be of
the following adjacency list representation where each xij is the j'th neighbor of vertex i (vertex
labels are 1 through n):
1: x11 x12 x13 ...
2: x21 x22 x23 ...
.
.
n: xn1 xn2 xn3 ...
Your output will be to the console. You will first output whether or not the graph is acyclic. If
the graph is NOT acyclic, then you will output the set of back edges you have detected during
DFS. Otherwise, if the graph is acyclic, then you will output the vertices in topologically
sorted order.
Algorithmic specifications:
Your algorithm must use DFS appropriately and run in O(E + V) time on any input graph. You will
need to keep track of edge types and finish times so that you can use DFS for detecting
cyclicity/acyclicity and topologically sorting if the graph is a DAG. You may implement your graph
class as you wish so long as your overall algorithm runs correctly and efficiently.
What to Turn in: You must turn in a single zipped file containing your source code, a Makefile
if your language must be compiled, appropriate input and output files, and a README file
indicating how to execute your program (especially if not written in C++ or Java). Refer to
proglag.pdf for further specifications.
This assignment is due by MIDNIGHT of Monday, February 19. Late submissions
carry a minus 40% per-day late penalty.
Sheet1Name:Possible:Score:Comments:10Graph structure with adjacency list representationDFS16Correct and O(V+E) time10Detecting cycles, is graph DAG?Topological Sort16Correctness of Topo-Sort algorithm and output18No problems in compilation and execution? Non-compiling projects receive max total 10 points, and code that compiles but crashes during execution receives max total 18 points.700Total
&"Helvetica,Regular"&12&K000000&P
Sheet2
&"Helvetica,Regular"&12&K000000&P
Sheet3
&"Helvetica,Regular"&12&K000000&P
DFS and topological sort
CS340
Depth first search
breadth
depth
Search "deeper" whenever possible
*example shows discovery times
Depth first search
Input: G = (V,E), directed or undirected.
No source vertex is given!
Output: 2 timestamps on each vertex:
v.d discovery time
v.f finishing time
These will be useful ...
ICAMS033-G.NITHYA.pptx

This document provides definitions and theorems related to domination and strong domination of graphs. It begins with introductions to graph theory concepts like vertex degree. It then defines different types of domination like dominating sets, connected dominating sets, and k-dominating sets. Further definitions include total domination, strong domination, and dominating cycles. Theorems are provided that relate strong domination number to independence number and domination number. The document concludes by discussing applications of domination in fields like communication networks and distributing computer resources.
Recommended
Ppt 1

This document discusses several graph algorithms:
1) Topological sort is an ordering of the vertices of a directed acyclic graph (DAG) such that for every edge from vertex u to v, u comes before v in the ordering. It can be used to find a valid schedule respecting dependencies.
2) Strongly connected components are maximal subsets of vertices in a directed graph such that there is a path between every pair of vertices. An algorithm uses depth-first search to find SCCs in linear time.
3) Minimum spanning trees find a subset of edges that connects all vertices at minimum total cost. Prim's and Kruskal's algorithms find minimum spanning trees using greedy strategies in O(E
Topological Sort

This document discusses several graph algorithms:
1) Topological sort is an ordering of the vertices of a directed acyclic graph (DAG) such that for every edge from vertex u to v, u comes before v in the ordering. It can be used to find a valid schedule respecting dependencies.
2) Strongly connected components are maximal subsets of vertices in a directed graph such that there is a path between every pair of vertices. An algorithm uses depth-first search to find SCCs in linear time.
3) Minimum spanning trees find a subset of edges that connects all vertices at minimum total cost. Prim's and Kruskal's algorithms find minimum spanning trees using greedy strategies in O(E
topological_sort_strongly Connected Components

The document describes algorithms for depth-first search (DFS) and how it can be used to find strongly connected components (SCCs) in a directed graph. DFS assigns discovery and finish times to vertices and classifies graph edges. It can determine if a graph is acyclic by checking for back edges. To find SCCs, DFS is run on the original graph and its transpose to group vertices reachable from each other into components. The result is a directed acyclic graph of components. Lemmas are presented about paths between components based on discovery/finish times.
Unit ii-ppt

The document discusses optimization problems and various graph search algorithms. It covers:
- Formulating optimization problems as finding the best solution from all feasible solutions.
- Graph search algorithms like breadth-first search and depth-first search that can be used to find optimal solutions by traversing graphs.
- Dijkstra's algorithm, a graph search algorithm that finds the shortest paths between nodes in a graph.
Prim's Algorithm on minimum spanning tree

Prim's algorithm is used to find the minimum spanning tree of a connected, undirected graph. It works by continuously adding edges to a growing tree that connects vertices. The algorithm maintains two lists - a closed list of vertices already included in the minimum spanning tree, and a priority queue of open vertices. It starts with a single vertex in the closed list. Then it selects the lowest cost edge that connects an open vertex to a closed one, adds it to the tree and updates the lists. This process repeats until all vertices are in the closed list and connected by edges in the minimum spanning tree. The algorithm runs in O(E log V) time when using a binary heap priority queue.
graphin-c1.pnggraphin-c1.txt1 22 3 83 44 5.docx

graphin-c1.png
graphin-c1.txt
1: 2
2: 3 8
3: 4
4: 5
5: 3
6: 7
7: 3 6 8
8: 1 9
9: 1
graphin-c2.jpg
graphin-c2.txt
1: 2 9
2: 3 8
3: 4
4: 5 9
5: 3
6: 7
7: 3 6 8
8: 1
9:
graphin-DAG.png
graphin-DAG.txt
1: 2
2: 3 8
3: 4
4: 5
5: 9
6: 4 7
7: 3 8
8: 9
9:
CS 340 Programming Assignment III:
Topological Sort
Description: You are to implement the Depth-First Search (DFS) based algorithm for (i)
testing whether or not the input directed graph G is acyclic (a DAG), and (ii) if G is a DAG,
topologically sorting the vertices of G and outputting the topologically sorted order.
I/O Specifications: You will prompt the user from the console to select an input graph
filename, including the sample file graphin.txt as an option. The graph input files must be of
the following adjacency list representation where each xij is the j'th neighbor of vertex i (vertex
labels are 1 through n):
1: x11 x12 x13 ...
2: x21 x22 x23 ...
.
.
n: xn1 xn2 xn3 ...
Your output will be to the console. You will first output whether or not the graph is acyclic. If
the graph is NOT acyclic, then you will output the set of back edges you have detected during
DFS. Otherwise, if the graph is acyclic, then you will output the vertices in topologically
sorted order.
Algorithmic specifications:
Your algorithm must use DFS appropriately and run in O(E + V) time on any input graph. You will
need to keep track of edge types and finish times so that you can use DFS for detecting
cyclicity/acyclicity and topologically sorting if the graph is a DAG. You may implement your graph
class as you wish so long as your overall algorithm runs correctly and efficiently.
What to Turn in: You must turn in a single zipped file containing your source code, a Makefile
if your language must be compiled, appropriate input and output files, and a README file
indicating how to execute your program (especially if not written in C++ or Java). Refer to
proglag.pdf for further specifications.
This assignment is due by MIDNIGHT of Monday, February 19. Late submissions
carry a minus 40% per-day late penalty.
Sheet1Name:Possible:Score:Comments:10Graph structure with adjacency list representationDFS16Correct and O(V+E) time10Detecting cycles, is graph DAG?Topological Sort16Correctness of Topo-Sort algorithm and output18No problems in compilation and execution? Non-compiling projects receive max total 10 points, and code that compiles but crashes during execution receives max total 18 points.700Total
&"Helvetica,Regular"&12&K000000&P
Sheet2
&"Helvetica,Regular"&12&K000000&P
Sheet3
&"Helvetica,Regular"&12&K000000&P
DFS and topological sort
CS340
Depth first search
breadth
depth
Search "deeper" whenever possible
*example shows discovery times
Depth first search
Input: G = (V,E), directed or undirected.
No source vertex is given!
Output: 2 timestamps on each vertex:
v.d discovery time
v.f finishing time
These will be useful ...
ICAMS033-G.NITHYA.pptx

This document provides definitions and theorems related to domination and strong domination of graphs. It begins with introductions to graph theory concepts like vertex degree. It then defines different types of domination like dominating sets, connected dominating sets, and k-dominating sets. Further definitions include total domination, strong domination, and dominating cycles. Theorems are provided that relate strong domination number to independence number and domination number. The document concludes by discussing applications of domination in fields like communication networks and distributing computer resources.
Graph Traversal Algorithms - Depth First Search Traversal

This document discusses graph traversal techniques, specifically depth-first search (DFS) and breadth-first search (BFS). It provides pseudocode for DFS and explains key properties like edge classification, time complexity of O(V+E), and applications such as finding connected components and articulation points.
breadth first search

Breadth-first search (BFS) and depth-first search (DFS) are two standard graph traversal algorithms. BFS explores nodes level-by-level starting from the root node, using a queue data structure. In contrast, DFS prioritizes exploring nodes to the deepest levels first, using a stack data structure. Both algorithms are useful for problems like finding the shortest path in a graph and determining connected components. BFS and DFS can be used to generate spanning trees and forests that connect all nodes within each component of the graph.
Strong (Weak) Triple Connected Domination Number of a Fuzzy Graph

International Journal of Computational Engineering Research(IJCER) is an intentional online Journal in English monthly publishing journal. This Journal publish original research work that contributes significantly to further the scientific knowledge in engineering and Technology.
Chapter 1

This document provides an overview of key concepts in graph theory, including:
- A graph consists of a set of vertices and edges connecting pairs of vertices.
- Paths and cycles are walks through a graph without repeating edges or vertices. A tree is an acyclic connected graph.
- The degree of a vertex is the number of edges connected to it. Regular graphs have all vertices of the same degree.
- Graphs can be represented using adjacency matrices and incidence matrices to show connections between vertices and edges.
- Directed graphs have edges oriented from a starting to ending vertex. Connectedness in directed graphs depends on the underlying graph or directionality of paths.
Algorithm Design and Complexity - Course 8

The document discusses algorithms for finding strongly connected components (SCCs) in directed graphs. It describes Kosaraju's algorithm, which uses two depth-first searches (DFS) to find the SCCs. The first DFS computes a finishing time ordering, while the second DFS uses the transpose graph and the finishing time ordering to find the SCCs, outputting each SCC as a separate DFS tree. The algorithm runs in O(V+E) time and uses the property that the first DFS provides a topological sorting of the SCCs graph.
Spanningtreesppt

This document discusses graphs and spanning trees. A graph is a data structure containing vertices and edges connecting the vertices. A spanning tree of a graph is a subgraph that connects all vertices without cycles. Spanning trees can be found using graph search algorithms like breadth-first search or depth-first search. Spanning trees have properties like containing no cycles, having the minimum number of edges to connect all vertices, and being uniquely defined up to the choice of starting vertex for the search algorithm.
THE RESULT FOR THE GRUNDY NUMBER ON P4- CLASSES

This document summarizes research on calculating the Grundy number of fat-extended P4-laden graphs. It begins by introducing the Grundy number and discussing that it is NP-complete to calculate for general graphs. It then presents previous work that has found polynomial time algorithms to calculate the Grundy number for certain graph classes. The main results are that the document proves that the Grundy number can be calculated in polynomial time, specifically O(n3) time, for fat-extended P4-laden graphs by traversing their modular decomposition tree. This implies the Grundy number can also be calculated efficiently for several related graph classes that are contained within fat-extended P4-laden graphs.
Hamilton Path & Dijkstra's Algorithm

This document summarizes topics related to discrete structures, including Hamiltonian paths and circuits, matching theory, and the shortest path problem solved using Dijkstra's algorithm. It defines Hamiltonian paths and circuits, discusses maximal and perfect matchings in graphs, and outlines Dijkstra's algorithm for finding the shortest path between nodes in a weighted graph by iteratively updating distances and marking visited nodes.
358 33 powerpoint-slides_13-graphs_chapter-13

This document discusses different data structures and algorithms for representing graphs. It begins with definitions of basic graph terminology like vertices, edges, degrees of vertices, paths, cycles, etc. It then covers representations of graphs using adjacency matrices and adjacency lists. Adjacency matrices store whether each pair of vertices is connected in a 2D array while adjacency lists store the neighbors of each vertex using linked lists. The document also discusses algorithms for finding the transitive closure of a directed graph and representing bi-connected graphs.
Graph terminology and algorithm and tree.pptx

This document provides an overview of key concepts in graph theory including graph terminology, representations, traversals, spanning trees, minimum spanning trees, and shortest path algorithms. It defines graphs, directed vs undirected graphs, connectedness, degrees, adjacency, paths, cycles, trees, and graph representations using adjacency matrices and lists. It also describes breadth-first and depth-first traversals, spanning trees, minimum spanning trees, and algorithms for finding minimum spanning trees and shortest paths like Kruskal's, Prim's, Dijkstra's, Bellman-Ford and A* algorithms.
Shortest path (Dijkistra's Algorithm) & Spanning Tree (Prim's Algorithm)

Shortest path (Dijkistra's Algorithm) & Spanning Tree (Prim's Algorithm)Mohanlal Sukhadia University (MLSU)
The document discusses shortest path problems and algorithms for finding shortest paths in graphs. It describes Dijkstra's algorithm for finding the shortest path between two nodes in a graph with non-negative edge weights. Prim's algorithm is presented for finding a minimum spanning tree, which is a subgraph connecting all nodes with minimum total edge weight. An example graph is given and steps are outlined for applying Prim's algorithm to find its minimum spanning tree.Link Analysis in Networks - or - Finding the Terrorists

A rapid fire introduction to network theory and how link analysis can be used by law enforcement agencies
Unit 9 graph

This document provides information about graphs and graph algorithms. It discusses different graph representations including adjacency matrices and adjacency lists. It also describes common graph traversal algorithms like depth-first search and breadth-first search. Finally, it covers minimum spanning trees and algorithms to find them, specifically mentioning Kruskal's algorithm.
NON-LINEAR DATA STRUCTURE-Graphs.pptx

The document defines graphs and discusses their properties and applications. It covers topics like directed vs undirected graphs, representations using adjacency matrices and lists, graph traversals using depth-first and breadth-first search, minimum spanning trees, and applications of graphs in areas like social networks and the world wide web.
Unit ix graph 

This document provides an overview of graphs and graph algorithms. It begins with an introduction to graphs, including definitions of vertices, edges, directed/undirected graphs, and graph representations using adjacency matrices and lists. It then covers graph traversal algorithms like depth-first search and breadth-first search. Minimum spanning trees and algorithms for finding them like Kruskal's algorithm are also discussed. The document provides examples and pseudocode for the algorithms. It analyzes the time complexity of the graph algorithms. Overall, the document provides a comprehensive introduction to fundamental graph concepts and algorithms.
Slides Chapter10.1 10.2

This section provides an introduction to graphs and graph theory. Key points include:
- Graphs consist of vertices and edges that connect the vertices. They can be directed or undirected.
- Common terminology is introduced, such as adjacent vertices, neighborhoods, degrees of vertices, and handshaking theorem.
- Different types of graphs are discussed, including multigraphs, pseudographs, and directed graphs.
- Examples of graph models are given for computer networks, social networks, information networks, transportation networks, and software design. Graphs can be used to model many real-world systems and applications.
Clique Relaxation Models in Networks: Theory, Algorithms, and Applications

This document discusses clique relaxation models in networks. It provides an introduction to graph theory basics and defines common clique relaxation concepts like k-cliques, k-clubs, and k-plexes. The document outlines topics on the theory, algorithms, and applications of clique relaxations and discusses finding cohesive subgroups in social networks and other applications.
Graph theory

The document introduces the concepts of graphs and different types of graphs. It defines what a graph is - a set of vertices and edges, and how they can be represented. It discusses weighted and non-weighted graphs, directed and undirected graphs, self-loops, multigraphs, and provides examples of how graphs are used in real world applications like social networks, maps, computer networks and more.
Unit 3 graph chapter6

This document provides an overview of graphs and graph algorithms. It defines graphs, directed and undirected graphs, and graph terminology like vertices, edges, paths, cycles, connected components, and degrees. It describes different graph representations like adjacency matrices and adjacency lists. It also explains graph traversal algorithms like depth-first search and breadth-first search. Finally, it covers graph algorithms for finding minimum spanning trees, shortest paths, and transitive closure.
Computer Science Assignment Help 

I am Travis W. I am a Computer Science Assignment Expert at programminghomeworkhelp.com. I hold a Master's in Computer Science, Leeds University. I have been helping students with their homework for the past 9 years. I solve assignments related to Computer Science.
Visit programminghomeworkhelp.com or email support@programminghomeworkhelp.com.You can also call on +1 678 648 4277 for any assistance with Computer Science assignments.
databasemanagementsystempptforbeginners.ppt

This document discusses key concepts in database systems, including:
- Database management systems (DBMS) store and manage collections of related data through a set of programs.
- DBMS provide multiple levels of abstraction over the data including physical, logical, and view levels to simplify user interaction.
- Common data models include the relational model and entity-relationship model for structuring data.
- Data definition languages are used to define the database schema and structure, while data manipulation languages allow users to interact with the data.
- DBMS provide features like data independence, security, integrity, and concurrency control that address limitations of early file-based data storage systems.
authentication.ppt

Authentication is the process of verifying a principal's identity, while authorization determines what actions a principal can perform. Common authentication methods include password authentication using hashes and salts to secure passwords, and public-key authentication using challenge-response protocols like SSH. SSH authentication works by having the client prove possession of the private key without revealing it, through an agent that stores private keys in memory to avoid repeatedly entering passphrases.
More Related Content
Similar to DFS.pdf
Graph Traversal Algorithms - Depth First Search Traversal

This document discusses graph traversal techniques, specifically depth-first search (DFS) and breadth-first search (BFS). It provides pseudocode for DFS and explains key properties like edge classification, time complexity of O(V+E), and applications such as finding connected components and articulation points.
breadth first search

Breadth-first search (BFS) and depth-first search (DFS) are two standard graph traversal algorithms. BFS explores nodes level-by-level starting from the root node, using a queue data structure. In contrast, DFS prioritizes exploring nodes to the deepest levels first, using a stack data structure. Both algorithms are useful for problems like finding the shortest path in a graph and determining connected components. BFS and DFS can be used to generate spanning trees and forests that connect all nodes within each component of the graph.
Strong (Weak) Triple Connected Domination Number of a Fuzzy Graph

International Journal of Computational Engineering Research(IJCER) is an intentional online Journal in English monthly publishing journal. This Journal publish original research work that contributes significantly to further the scientific knowledge in engineering and Technology.
Chapter 1

This document provides an overview of key concepts in graph theory, including:
- A graph consists of a set of vertices and edges connecting pairs of vertices.
- Paths and cycles are walks through a graph without repeating edges or vertices. A tree is an acyclic connected graph.
- The degree of a vertex is the number of edges connected to it. Regular graphs have all vertices of the same degree.
- Graphs can be represented using adjacency matrices and incidence matrices to show connections between vertices and edges.
- Directed graphs have edges oriented from a starting to ending vertex. Connectedness in directed graphs depends on the underlying graph or directionality of paths.
Algorithm Design and Complexity - Course 8

The document discusses algorithms for finding strongly connected components (SCCs) in directed graphs. It describes Kosaraju's algorithm, which uses two depth-first searches (DFS) to find the SCCs. The first DFS computes a finishing time ordering, while the second DFS uses the transpose graph and the finishing time ordering to find the SCCs, outputting each SCC as a separate DFS tree. The algorithm runs in O(V+E) time and uses the property that the first DFS provides a topological sorting of the SCCs graph.
Spanningtreesppt

This document discusses graphs and spanning trees. A graph is a data structure containing vertices and edges connecting the vertices. A spanning tree of a graph is a subgraph that connects all vertices without cycles. Spanning trees can be found using graph search algorithms like breadth-first search or depth-first search. Spanning trees have properties like containing no cycles, having the minimum number of edges to connect all vertices, and being uniquely defined up to the choice of starting vertex for the search algorithm.
THE RESULT FOR THE GRUNDY NUMBER ON P4- CLASSES

This document summarizes research on calculating the Grundy number of fat-extended P4-laden graphs. It begins by introducing the Grundy number and discussing that it is NP-complete to calculate for general graphs. It then presents previous work that has found polynomial time algorithms to calculate the Grundy number for certain graph classes. The main results are that the document proves that the Grundy number can be calculated in polynomial time, specifically O(n3) time, for fat-extended P4-laden graphs by traversing their modular decomposition tree. This implies the Grundy number can also be calculated efficiently for several related graph classes that are contained within fat-extended P4-laden graphs.
Hamilton Path & Dijkstra's Algorithm

This document summarizes topics related to discrete structures, including Hamiltonian paths and circuits, matching theory, and the shortest path problem solved using Dijkstra's algorithm. It defines Hamiltonian paths and circuits, discusses maximal and perfect matchings in graphs, and outlines Dijkstra's algorithm for finding the shortest path between nodes in a weighted graph by iteratively updating distances and marking visited nodes.
358 33 powerpoint-slides_13-graphs_chapter-13

This document discusses different data structures and algorithms for representing graphs. It begins with definitions of basic graph terminology like vertices, edges, degrees of vertices, paths, cycles, etc. It then covers representations of graphs using adjacency matrices and adjacency lists. Adjacency matrices store whether each pair of vertices is connected in a 2D array while adjacency lists store the neighbors of each vertex using linked lists. The document also discusses algorithms for finding the transitive closure of a directed graph and representing bi-connected graphs.
Graph terminology and algorithm and tree.pptx

This document provides an overview of key concepts in graph theory including graph terminology, representations, traversals, spanning trees, minimum spanning trees, and shortest path algorithms. It defines graphs, directed vs undirected graphs, connectedness, degrees, adjacency, paths, cycles, trees, and graph representations using adjacency matrices and lists. It also describes breadth-first and depth-first traversals, spanning trees, minimum spanning trees, and algorithms for finding minimum spanning trees and shortest paths like Kruskal's, Prim's, Dijkstra's, Bellman-Ford and A* algorithms.
Shortest path (Dijkistra's Algorithm) & Spanning Tree (Prim's Algorithm)

Shortest path (Dijkistra's Algorithm) & Spanning Tree (Prim's Algorithm)Mohanlal Sukhadia University (MLSU)
The document discusses shortest path problems and algorithms for finding shortest paths in graphs. It describes Dijkstra's algorithm for finding the shortest path between two nodes in a graph with non-negative edge weights. Prim's algorithm is presented for finding a minimum spanning tree, which is a subgraph connecting all nodes with minimum total edge weight. An example graph is given and steps are outlined for applying Prim's algorithm to find its minimum spanning tree.Link Analysis in Networks - or - Finding the Terrorists

A rapid fire introduction to network theory and how link analysis can be used by law enforcement agencies
Unit 9 graph

This document provides information about graphs and graph algorithms. It discusses different graph representations including adjacency matrices and adjacency lists. It also describes common graph traversal algorithms like depth-first search and breadth-first search. Finally, it covers minimum spanning trees and algorithms to find them, specifically mentioning Kruskal's algorithm.
NON-LINEAR DATA STRUCTURE-Graphs.pptx

The document defines graphs and discusses their properties and applications. It covers topics like directed vs undirected graphs, representations using adjacency matrices and lists, graph traversals using depth-first and breadth-first search, minimum spanning trees, and applications of graphs in areas like social networks and the world wide web.
Unit ix graph 

This document provides an overview of graphs and graph algorithms. It begins with an introduction to graphs, including definitions of vertices, edges, directed/undirected graphs, and graph representations using adjacency matrices and lists. It then covers graph traversal algorithms like depth-first search and breadth-first search. Minimum spanning trees and algorithms for finding them like Kruskal's algorithm are also discussed. The document provides examples and pseudocode for the algorithms. It analyzes the time complexity of the graph algorithms. Overall, the document provides a comprehensive introduction to fundamental graph concepts and algorithms.
Slides Chapter10.1 10.2

This section provides an introduction to graphs and graph theory. Key points include:
- Graphs consist of vertices and edges that connect the vertices. They can be directed or undirected.
- Common terminology is introduced, such as adjacent vertices, neighborhoods, degrees of vertices, and handshaking theorem.
- Different types of graphs are discussed, including multigraphs, pseudographs, and directed graphs.
- Examples of graph models are given for computer networks, social networks, information networks, transportation networks, and software design. Graphs can be used to model many real-world systems and applications.
Clique Relaxation Models in Networks: Theory, Algorithms, and Applications

This document discusses clique relaxation models in networks. It provides an introduction to graph theory basics and defines common clique relaxation concepts like k-cliques, k-clubs, and k-plexes. The document outlines topics on the theory, algorithms, and applications of clique relaxations and discusses finding cohesive subgroups in social networks and other applications.
Graph theory

The document introduces the concepts of graphs and different types of graphs. It defines what a graph is - a set of vertices and edges, and how they can be represented. It discusses weighted and non-weighted graphs, directed and undirected graphs, self-loops, multigraphs, and provides examples of how graphs are used in real world applications like social networks, maps, computer networks and more.
Unit 3 graph chapter6

This document provides an overview of graphs and graph algorithms. It defines graphs, directed and undirected graphs, and graph terminology like vertices, edges, paths, cycles, connected components, and degrees. It describes different graph representations like adjacency matrices and adjacency lists. It also explains graph traversal algorithms like depth-first search and breadth-first search. Finally, it covers graph algorithms for finding minimum spanning trees, shortest paths, and transitive closure.
Computer Science Assignment Help 

I am Travis W. I am a Computer Science Assignment Expert at programminghomeworkhelp.com. I hold a Master's in Computer Science, Leeds University. I have been helping students with their homework for the past 9 years. I solve assignments related to Computer Science.
Visit programminghomeworkhelp.com or email support@programminghomeworkhelp.com.You can also call on +1 678 648 4277 for any assistance with Computer Science assignments.
Similar to DFS.pdf (20)
Graph Traversal Algorithms - Depth First Search Traversal

Graph Traversal Algorithms - Depth First Search Traversal
Strong (Weak) Triple Connected Domination Number of a Fuzzy Graph

Strong (Weak) Triple Connected Domination Number of a Fuzzy Graph
Shortest path (Dijkistra's Algorithm) & Spanning Tree (Prim's Algorithm)

Shortest path (Dijkistra's Algorithm) & Spanning Tree (Prim's Algorithm)
Link Analysis in Networks - or - Finding the Terrorists

Link Analysis in Networks - or - Finding the Terrorists
Clique Relaxation Models in Networks: Theory, Algorithms, and Applications

Clique Relaxation Models in Networks: Theory, Algorithms, and Applications
More from jayarao21
databasemanagementsystempptforbeginners.ppt

This document discusses key concepts in database systems, including:
- Database management systems (DBMS) store and manage collections of related data through a set of programs.
- DBMS provide multiple levels of abstraction over the data including physical, logical, and view levels to simplify user interaction.
- Common data models include the relational model and entity-relationship model for structuring data.
- Data definition languages are used to define the database schema and structure, while data manipulation languages allow users to interact with the data.
- DBMS provide features like data independence, security, integrity, and concurrency control that address limitations of early file-based data storage systems.
authentication.ppt

Authentication is the process of verifying a principal's identity, while authorization determines what actions a principal can perform. Common authentication methods include password authentication using hashes and salts to secure passwords, and public-key authentication using challenge-response protocols like SSH. SSH authentication works by having the client prove possession of the private key without revealing it, through an agent that stores private keys in memory to avoid repeatedly entering passphrases.
6.Lab Syllabus.docx

This document outlines the syllabus for a Cloud Computing Lab course. The course objectives are to prepare students to set up a cloud environment, expose them to virtual environments for managing resources, and expertise them in managing resources and applications in cloud environments. The course outcomes are for students to configure virtualization tools, manage virtual machine resources, design and deploy applications in PaaS environments, use Unix and Hadoop commands in VMs, and explore Hadoop features by installing a single node Hadoop cluster and running simple applications. The course involves experiments in virtual machine creation, adding virtual blocks, running programs in VMs, VM migration, Hadoop installation, creating a one node Hadoop cluster, using Unix commands in VMs, HDFS
unit5_part2.pptx

JSON (JavaScript Object Notation) is a lightweight data-interchange format that is easy for humans to read and write and for machines to parse and generate. It is built on two structures: a collection of name/value pairs and an ordered list of values. JSON is primarily used to transmit data between a web application and a server. It is the primary data format used by APIs, allowing JavaScript code to communicate with servers.
CCCDjango2010.pdf

This document provides an overview and introduction to web programming using the Python Django web framework. It discusses what Django is and its key features like pluggable apps, an object-relational mapper for databases, an automatic admin interface, templates, and URL structure. The core components of models, views, templates, and URLs are explained. Models are used to store and retrieve data from databases. Views are functions that generate web pages by utilizing models and templates. Templates contain tags to dynamically output content. URLs are mapped to views using a configuration file. The document also covers forms, the admin interface, and provides examples throughout.
ch2_jayarao.ppt

This document discusses key concepts in relational database modeling including:
- A relational database consists of a collection of tables, each with a unique name.
- Relations, tuples, attributes, relation schemas, and relation instances are defined.
- Superkeys, candidate keys, and primary keys are discussed as ways to uniquely identify tuples in a relation. A foreign key is defined as an attribute that refers to a primary key in another table to link the tables.
digital_sign_interview.ppt

This document discusses digital signatures and their use for message authentication and integrity. It describes how digital signatures work using asymmetric cryptography like RSA, providing non-repudiation by tying a message to the private key of the signer. MAC techniques are also discussed but are limited by not providing non-repudiation. The RSA digital signature scheme is then outlined, including key generation, signing messages, and verification. Applications of digital signatures are mentioned for email, data storage, payments, and software distribution.
introdution-to-html_jayarao27_11_22.pptx

The document provides an introduction to HTML and describes several important HTML elements and tags. It explains that HTML is used to create documents on the World Wide Web and is platform independent. It also describes common HTML tags such as <HTML>, <HEAD>, <BODY>, <TITLE>, character formatting tags (<B>, <I>, etc.), paragraph tags (<P>, <BR>, <PRE>), and other tags like <HR> and header tags (<H1>-<H6>).
MFCS PPT.pdf

This document discusses mathematical foundations of computer science. It covers topics such as statements (propositions), logic operators (NOT, AND, OR), compound statements, logical equivalence, conditional statements, and arguments. Specifically, it defines statements as sentences that are either true or false. It introduces logic operators and how they can be used to construct new statements from old ones. It also discusses logical forms such as truth tables and De Morgan's laws. Finally, it discusses conditional statements, logical equivalence, and valid arguments.
More from jayarao21 (9)
Recently uploaded
SCALING OF MOS CIRCUITS m .pptx

this ppt explains about scaling parameters of the mosfet it is basically vlsi subject
Electric vehicle and photovoltaic advanced roles in enhancing the financial p...

Climate change's impact on the planet forced the United Nations and governments to promote green energies and electric transportation. The deployments of photovoltaic (PV) and electric vehicle (EV) systems gained stronger momentum due to their numerous advantages over fossil fuel types. The advantages go beyond sustainability to reach financial support and stability. The work in this paper introduces the hybrid system between PV and EV to support industrial and commercial plants. This paper covers the theoretical framework of the proposed hybrid system including the required equation to complete the cost analysis when PV and EV are present. In addition, the proposed design diagram which sets the priorities and requirements of the system is presented. The proposed approach allows setup to advance their power stability, especially during power outages. The presented information supports researchers and plant owners to complete the necessary analysis while promoting the deployment of clean energy. The result of a case study that represents a dairy milk farmer supports the theoretical works and highlights its advanced benefits to existing plants. The short return on investment of the proposed approach supports the paper's novelty approach for the sustainable electrical system. In addition, the proposed system allows for an isolated power setup without the need for a transmission line which enhances the safety of the electrical network
Object Oriented Analysis and Design - OOAD

This ppt gives detailed description of Object Oriented Analysis and design.
AI + Data Community Tour - Build the Next Generation of Apps with the Einstei...

AI + Data Community Tour - Build the Next Generation of Apps with the Einstei...Paris Salesforce Developer Group
Build the Next Generation of Apps with the Einstein 1 Platform.
Rejoignez Philippe Ozil pour une session de workshops qui vous guidera à travers les détails de la plateforme Einstein 1, l'importance des données pour la création d'applications d'intelligence artificielle et les différents outils et technologies que Salesforce propose pour vous apporter tous les bénéfices de l'IA.Comparative analysis between traditional aquaponics and reconstructed aquapon...

The aquaponic system of planting is a method that does not require soil usage. It is a method that only needs water, fish, lava rocks (a substitute for soil), and plants. Aquaponic systems are sustainable and environmentally friendly. Its use not only helps to plant in small spaces but also helps reduce artificial chemical use and minimizes excess water use, as aquaponics consumes 90% less water than soil-based gardening. The study applied a descriptive and experimental design to assess and compare conventional and reconstructed aquaponic methods for reproducing tomatoes. The researchers created an observation checklist to determine the significant factors of the study. The study aims to determine the significant difference between traditional aquaponics and reconstructed aquaponics systems propagating tomatoes in terms of height, weight, girth, and number of fruits. The reconstructed aquaponics system’s higher growth yield results in a much more nourished crop than the traditional aquaponics system. It is superior in its number of fruits, height, weight, and girth measurement. Moreover, the reconstructed aquaponics system is proven to eliminate all the hindrances present in the traditional aquaponics system, which are overcrowding of fish, algae growth, pest problems, contaminated water, and dead fish.
DEEP LEARNING FOR SMART GRID INTRUSION DETECTION: A HYBRID CNN-LSTM-BASED MODEL

As digital technology becomes more deeply embedded in power systems, protecting the communication
networks of Smart Grids (SG) has emerged as a critical concern. Distributed Network Protocol 3 (DNP3)
represents a multi-tiered application layer protocol extensively utilized in Supervisory Control and Data
Acquisition (SCADA)-based smart grids to facilitate real-time data gathering and control functionalities.
Robust Intrusion Detection Systems (IDS) are necessary for early threat detection and mitigation because
of the interconnection of these networks, which makes them vulnerable to a variety of cyberattacks. To
solve this issue, this paper develops a hybrid Deep Learning (DL) model specifically designed for intrusion
detection in smart grids. The proposed approach is a combination of the Convolutional Neural Network
(CNN) and the Long-Short-Term Memory algorithms (LSTM). We employed a recent intrusion detection
dataset (DNP3), which focuses on unauthorized commands and Denial of Service (DoS) cyberattacks, to
train and test our model. The results of our experiments show that our CNN-LSTM method is much better
at finding smart grid intrusions than other deep learning algorithms used for classification. In addition,
our proposed approach improves accuracy, precision, recall, and F1 score, achieving a high detection
accuracy rate of 99.50%.
22CYT12-Unit-V-E Waste and its Management.ppt

Introduction- e - waste – definition - sources of e-waste– hazardous substances in e-waste - effects of e-waste on environment and human health- need for e-waste management– e-waste handling rules - waste minimization techniques for managing e-waste – recycling of e-waste - disposal treatment methods of e- waste – mechanism of extraction of precious metal from leaching solution-global Scenario of E-waste – E-waste in India- case studies.
Data Driven Maintenance | UReason Webinar

Discover the latest insights on Data Driven Maintenance with our comprehensive webinar presentation. Learn about traditional maintenance challenges, the right approach to utilizing data, and the benefits of adopting a Data Driven Maintenance strategy. Explore real-world examples, industry best practices, and innovative solutions like FMECA and the D3M model. This presentation, led by expert Jules Oudmans, is essential for asset owners looking to optimize their maintenance processes and leverage digital technologies for improved efficiency and performance. Download now to stay ahead in the evolving maintenance landscape.
一比一原版(CalArts毕业证)加利福尼亚艺术学院毕业证如何办理

CalArts毕业证学历书【微信95270640】CalArts毕业证’圣力嘉学院毕业证《Q微信95270640》办理CalArts毕业证√文凭学历制作{CalArts文凭}购买学历学位证书本科硕士,CalArts毕业证学历学位证【实体公司】办毕业证、成绩单、学历认证、学位证、文凭认证、办留信网认证、(网上可查,实体公司,专业可靠)
(诚招代理)办理国外高校毕业证成绩单文凭学位证,真实使馆公证(留学回国人员证明)真实留信网认证国外学历学位认证雅思代考国外学校代申请名校保录开请假条改GPA改成绩ID卡
1.高仿业务:【本科硕士】毕业证,成绩单(GPA修改),学历认证(教育部认证),大学Offer,,ID,留信认证,使馆认证,雅思,语言证书等高仿类证书;
2.认证服务: 学历认证(教育部认证),大使馆认证(回国人员证明),留信认证(可查有编号证书),大学保录取,雅思保分成绩单。
3.技术服务:钢印水印烫金激光防伪凹凸版设计印刷激凸温感光标底纹镭射速度快。
办理加利福尼亚艺术学院加利福尼亚艺术学院毕业证文凭证书流程:
1客户提供办理信息:姓名生日专业学位毕业时间等(如信息不确定可以咨询顾问:我们有专业老师帮你查询);
2开始安排制作毕业证成绩单电子图;
3毕业证成绩单电子版做好以后发送给您确认;
4毕业证成绩单电子版您确认信息无误之后安排制作成品;
5成品做好拍照或者视频给您确认;
6快递给客户(国内顺丰国外DHLUPS等快读邮寄)
-办理真实使馆公证(即留学回国人员证明)
-办理各国各大学文凭(世界名校一对一专业服务,可全程监控跟踪进度)
-全套服务:毕业证成绩单真实使馆公证真实教育部认证。让您回国发展信心十足!
(详情请加一下 文凭顾问+微信:95270640)欢迎咨询!子小伍玩小伍比山娃小一岁虎头虎脑的很霸气父亲让山娃跟小伍去夏令营听课山娃很高兴夏令营就设在附近一所小学山娃发现那所小学比自己的学校更大更美操场上还铺有塑胶跑道呢里面很多小朋友一班一班的快快乐乐原来城里娃都藏这儿来了怪不得平时见不到他们山娃恍然大悟起来吹拉弹唱琴棋书画山娃都不懂却什么都想学山娃怨自己太笨什么都不会斟酌再三山娃终于选定了学美术当听说每月要交元时父亲犹豫了山娃也说爸算了吧咱学校一学期才转
Advanced control scheme of doubly fed induction generator for wind turbine us...

This paper describes a speed control device for generating electrical energy on an electricity network based on the doubly fed induction generator (DFIG) used for wind power conversion systems. At first, a double-fed induction generator model was constructed. A control law is formulated to govern the flow of energy between the stator of a DFIG and the energy network using three types of controllers: proportional integral (PI), sliding mode controller (SMC) and second order sliding mode controller (SOSMC). Their different results in terms of power reference tracking, reaction to unexpected speed fluctuations, sensitivity to perturbations, and resilience against machine parameter alterations are compared. MATLAB/Simulink was used to conduct the simulations for the preceding study. Multiple simulations have shown very satisfying results, and the investigations demonstrate the efficacy and power-enhancing capabilities of the suggested control system.
Use PyCharm for remote debugging of WSL on a Windo cf5c162d672e4e58b4dde5d797...

This document serves as a comprehensive step-by-step guide on how to effectively use PyCharm for remote debugging of the Windows Subsystem for Linux (WSL) on a local Windows machine. It meticulously outlines several critical steps in the process, starting with the crucial task of enabling permissions, followed by the installation and configuration of WSL.
The guide then proceeds to explain how to set up the SSH service within the WSL environment, an integral part of the process. Alongside this, it also provides detailed instructions on how to modify the inbound rules of the Windows firewall to facilitate the process, ensuring that there are no connectivity issues that could potentially hinder the debugging process.
The document further emphasizes on the importance of checking the connection between the Windows and WSL environments, providing instructions on how to ensure that the connection is optimal and ready for remote debugging.
It also offers an in-depth guide on how to configure the WSL interpreter and files within the PyCharm environment. This is essential for ensuring that the debugging process is set up correctly and that the program can be run effectively within the WSL terminal.
Additionally, the document provides guidance on how to set up breakpoints for debugging, a fundamental aspect of the debugging process which allows the developer to stop the execution of their code at certain points and inspect their program at those stages.
Finally, the document concludes by providing a link to a reference blog. This blog offers additional information and guidance on configuring the remote Python interpreter in PyCharm, providing the reader with a well-rounded understanding of the process.
Embedded machine learning-based road conditions and driving behavior monitoring

Car accident rates have increased in recent years, resulting in losses in human lives, properties, and other financial costs. An embedded machine learning-based system is developed to address this critical issue. The system can monitor road conditions, detect driving patterns, and identify aggressive driving behaviors. The system is based on neural networks trained on a comprehensive dataset of driving events, driving styles, and road conditions. The system effectively detects potential risks and helps mitigate the frequency and impact of accidents. The primary goal is to ensure the safety of drivers and vehicles. Collecting data involved gathering information on three key road events: normal street and normal drive, speed bumps, circular yellow speed bumps, and three aggressive driving actions: sudden start, sudden stop, and sudden entry. The gathered data is processed and analyzed using a machine learning system designed for limited power and memory devices. The developed system resulted in 91.9% accuracy, 93.6% precision, and 92% recall. The achieved inference time on an Arduino Nano 33 BLE Sense with a 32-bit CPU running at 64 MHz is 34 ms and requires 2.6 kB peak RAM and 139.9 kB program flash memory, making it suitable for resource-constrained embedded systems.
LLM Fine Tuning with QLoRA Cassandra Lunch 4, presented by Anant

Slides for the 4th Presentation on LLM Fine-Tuning with QLoRA Presented by Anant, featuring DataStax Astra
Recently uploaded (20)
4. Mosca vol I -Fisica-Tipler-5ta-Edicion-Vol-1.pdf

4. Mosca vol I -Fisica-Tipler-5ta-Edicion-Vol-1.pdf
Electric vehicle and photovoltaic advanced roles in enhancing the financial p...

Electric vehicle and photovoltaic advanced roles in enhancing the financial p...
AI + Data Community Tour - Build the Next Generation of Apps with the Einstei...

AI + Data Community Tour - Build the Next Generation of Apps with the Einstei...
Comparative analysis between traditional aquaponics and reconstructed aquapon...

Comparative analysis between traditional aquaponics and reconstructed aquapon...
DEEP LEARNING FOR SMART GRID INTRUSION DETECTION: A HYBRID CNN-LSTM-BASED MODEL

DEEP LEARNING FOR SMART GRID INTRUSION DETECTION: A HYBRID CNN-LSTM-BASED MODEL
Advanced control scheme of doubly fed induction generator for wind turbine us...

Advanced control scheme of doubly fed induction generator for wind turbine us...
Use PyCharm for remote debugging of WSL on a Windo cf5c162d672e4e58b4dde5d797...

Use PyCharm for remote debugging of WSL on a Windo cf5c162d672e4e58b4dde5d797...
Embedded machine learning-based road conditions and driving behavior monitoring

Embedded machine learning-based road conditions and driving behavior monitoring
LLM Fine Tuning with QLoRA Cassandra Lunch 4, presented by Anant

LLM Fine Tuning with QLoRA Cassandra Lunch 4, presented by Anant
DFS.pdf
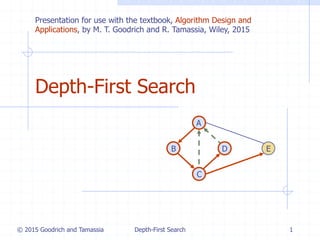
- 1. © 2015 Goodrich and Tamassia Depth-First Search 1 Depth-First Search D B A C E Presentation for use with the textbook, Algorithm Design and Applications, by M. T. Goodrich and R. Tamassia, Wiley, 2015
- 2. © 2015 Goodrich and Tamassia Depth-First Search 2 Subgraphs q A subgraph S of a graph G is a graph such that n The vertices of S are a subset of the vertices of G n The edges of S are a subset of the edges of G q A spanning subgraph of G is a subgraph that contains all the vertices of G Subgraph Spanning subgraph
- 3. © 2015 Goodrich and Tamassia Application: Web Crawlers q A fundamental kind of algorithmic operation that we might wish to perform on a graph is traversing the edges and the vertices of that graph. q A traversal is a systematic procedure for exploring a graph by examining all of its vertices and edges. q For example, a web crawler, which is the data collecting part of a search engine, must explore a graph of hypertext documents by examining its vertices, which are the documents, and its edges, which are the hyperlinks between documents. q A traversal is efficient if it visits all the vertices and edges in linear time. Depth-First Search 3
- 4. © 2015 Goodrich and Tamassia Depth-First Search 4 Connectivity q A graph is connected if there is a path between every pair of vertices q A connected component of a graph G is a maximal connected subgraph of G Connected graph Non connected graph with two connected components
- 5. © 2015 Goodrich and Tamassia Depth-First Search 5 Trees and Forests q A (free) tree is an undirected graph T such that n T is connected n T has no cycles This definition of tree is different from the one of a rooted tree q A forest is an undirected graph without cycles q The connected components of a forest are trees Tree Forest
- 6. © 2015 Goodrich and Tamassia Depth-First Search 6 Spanning Trees and Forests q A spanning tree of a connected graph is a spanning subgraph that is a tree q A spanning tree is not unique unless the graph is a tree q Spanning trees have applications to the design of communication networks q A spanning forest of a graph is a spanning subgraph that is a forest Graph Spanning tree
- 7. © 2015 Goodrich and Tamassia Depth-First Search 7 Depth-First Search q Depth-first search (DFS) is a general technique for traversing a graph q A DFS traversal of a graph G n Visits all the vertices and edges of G n Determines whether G is connected n Computes the connected components of G n Computes a spanning forest of G q DFS on a graph with n vertices and m edges takes O(n + m ) time q DFS can be further extended to solve other graph problems n Find and report a path between two given vertices n Find a cycle in the graph q Depth-first search is to graphs what Euler tour is to binary trees
- 8. © 2015 Goodrich and Tamassia Depth-First Search 8 DFS Algorithm from a Vertex
- 9. © 2015 Goodrich and Tamassia Depth-First Search 9 Example D B A C E D B A C E D B A C E discovery edge back edge A visited vertex A unexplored vertex unexplored edge
- 10. © 2015 Goodrich and Tamassia Depth-First Search 10 Example (cont.) D B A C E D B A C E D B A C E D B A C E
- 11. © 2015 Goodrich and Tamassia Depth-First Search 11 DFS and Maze Traversal q The DFS algorithm is similar to a classic strategy for exploring a maze n We mark each intersection, corner and dead end (vertex) visited n We mark each corridor (edge ) traversed n We keep track of the path back to the entrance (start vertex) by means of a rope (recursion stack)
- 12. © 2015 Goodrich and Tamassia Depth-First Search 12 Properties of DFS Property 1 DFS(G, v) visits all the vertices and edges in the connected component of v Property 2 The discovery edges labeled by DFS(G, v) form a spanning tree of the connected component of v D B A C E
- 13. © 2015 Goodrich and Tamassia The General DFS Algorithm q Perform a DFS from each unexplored vertex: Depth-First Search 13
- 14. © 2015 Goodrich and Tamassia Depth-First Search 14 Analysis of DFS q Setting/getting a vertex/edge label takes O(1) time q Each vertex is labeled twice n once as UNEXPLORED n once as VISITED q Each edge is labeled twice n once as UNEXPLORED n once as DISCOVERY or BACK q Method incidentEdges is called once for each vertex q DFS runs in O(n + m) time provided the graph is represented by the adjacency list structure n Recall that Σv deg(v) = 2m
- 15. © 2015 Goodrich and Tamassia Depth-First Search 15 Path Finding (not in book) q We can specialize the DFS algorithm to find a path between two given vertices u and z using the template method pattern q We call DFS(G, u) with u as the start vertex q We use a stack S to keep track of the path between the start vertex and the current vertex q As soon as destination vertex z is encountered, we return the path as the contents of the stack Algorithm pathDFS(G, v, z) setLabel(v, VISITED) S.push(v) if v = z return S.elements() for all e ∈ G.incidentEdges(v) if getLabel(e) = UNEXPLORED w ← opposite(v,e) if getLabel(w) = UNEXPLORED setLabel(e, DISCOVERY) S.push(e) pathDFS(G, w, z) S.pop(e) else setLabel(e, BACK) S.pop(v)
- 16. © 2015 Goodrich and Tamassia Depth-First Search 16 Cycle Finding (not in book) q We can specialize the DFS algorithm to find a simple cycle using the template method pattern q We use a stack S to keep track of the path between the start vertex and the current vertex q As soon as a back edge (v, w) is encountered, we return the cycle as the portion of the stack from the top to vertex w Algorithm cycleDFS(G, v, z) setLabel(v, VISITED) S.push(v) for all e ∈ G.incidentEdges(v) if getLabel(e) = UNEXPLORED w ← opposite(v,e) S.push(e) if getLabel(w) = UNEXPLORED setLabel(e, DISCOVERY) pathDFS(G, w, z) S.pop(e) else T ← new empty stack repeat o ← S.pop() T.push(o) until o = w return T.elements() S.pop(v)