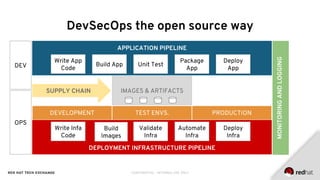
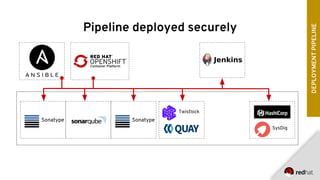
The document discusses the growing interest in integrating security into DevOps, highlighting the importance of training and designing systems that account for human behavior. It outlines the evolution of security risks from 2007 to 2017 as identified by OWASP and introduces the concept of DevSecOps with a focus on automation, supply chain security, and effective logging and monitoring. Key recommendations include securing deployment pipelines, implementing robust secrets management, and promoting quality assurance measures throughout the software development lifecycle.