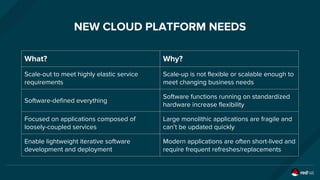
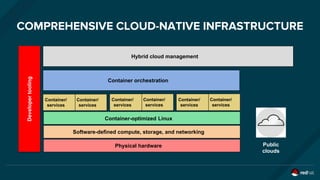
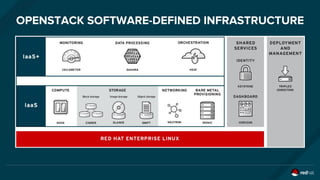
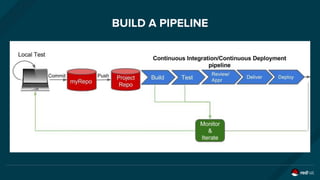
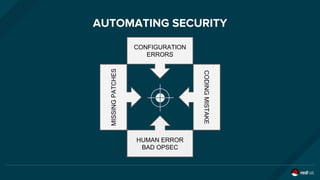
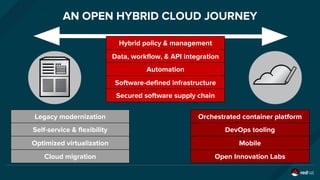
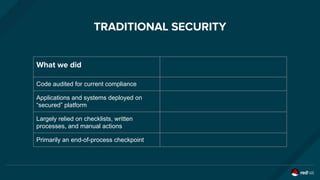
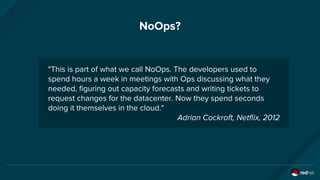
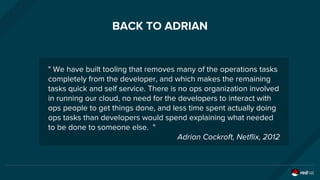
The document discusses the evolution and optimization of DevOps practices, emphasizing the integration of cloud-native applications and automated workflows to enhance collaboration and efficiency among developers. It highlights the importance of security in the development process through a DevSecOps approach, advocating for automated security practices that do not impede agility. Additionally, it addresses challenges related to operational management in hybrid infrastructures and the need for effective resource optimization and lifecycle management.