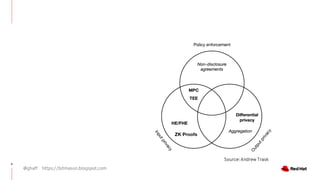
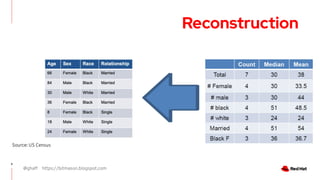
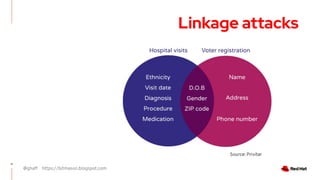
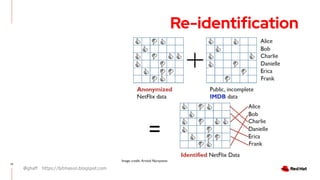
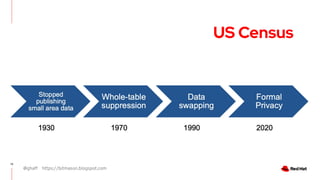
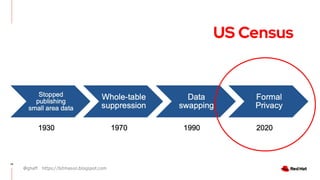
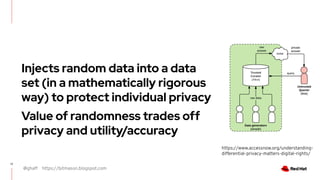
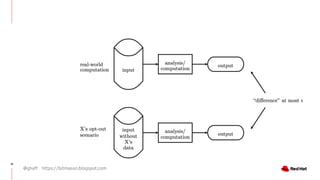
The document discusses the importance of preserving privacy while sharing data across various sectors such as energy and healthcare. It highlights techniques like anonymization, differential privacy, and multi-party computation to safeguard individual privacy while allowing data utilization. The article also addresses the challenges and limitations of these methods and emphasizes the need for ongoing research in the field.