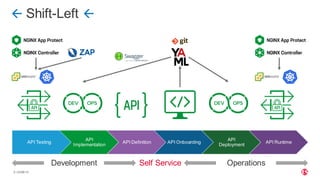
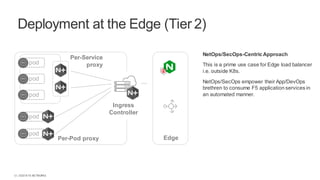
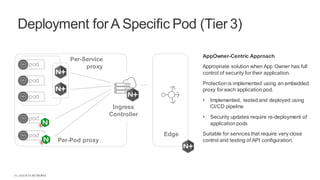
The document discusses the integration of DevOps practices into operational security, addressing challenges like speed, complexity, and inconsistent security across cloud environments while advocating for a proactive approach to security in the development process. It outlines various deployment options, such as edge deployment and specific service or pod deployment, catering to different operational structures and security management preferences within organizations. Recommendations include the adoption of declarative templates and a collaborative approach between DevOps and SecOps teams to enhance security without hindering development efficiency.






![| ©2018 F5 NETWORKS7
Declarative
Support Base Templates
predefined or externalreference
Adaptation layer: Base Template Adaption
Option to customize the initial policy
{"policy": {
"name":"AppPolicy01",
"description":"AppV1.1 - DEMO FOR DECLARATIVE AND WEBHOOKS CAPABILITIES",
"template":{ "name":"POLICY_TEMPLATE_RAPID_DEPLOYMENT" },
"enforcementMode":"blocking",
"server-technologies":[
{
"serverTechnologyName":"MySQL"
} ],
"signature-settings":{
"signatureStaging": false
},
"modifications": [{
"entityChanges": {
"type": "explicit"
},
"entity": {
"name": "log"
},
"entityKind": "tm:asm:policies:filetypes:filetypestate",
"action": "delete",
"description": "Delete Disallowed File Type"
} ] }
Modification layer: Policy builder suggestions
Part of the modification layer and can be shared between
policies](https://image.slidesharecdn.com/mysecuredapimdeckv6-200817155731/85/Secured-APIM-as-a-Service-7-320.jpg)