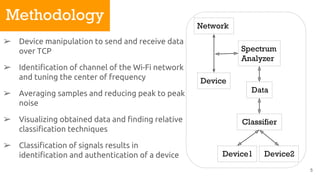
The document discusses device fingerprinting as a method for identifying and authenticating devices using internal and external characteristics, particularly through transmission control protocol in mobile devices. It details a methodology involving network device spectrum analysis and data classification, highlighting promising results for identifying mobile devices, especially between the iPhone 7 and Xiaomi Mi A1. Future work aims for more advanced classification techniques and the necessity for testing a broader range of devices to enhance security.










![11
Reference
➢ G. Baldini and G. Steri, “Survey of techniques for the identification of mobile using the physical fingerprints of the
built-in components,” IEEE Communications Surveys & Tutorials, vol. 19, no. 3, pp. 1761–1789, 2017.
➢ B. D. Fulcher and N. S. Jones, “Highly comparative feature-based time-series classification,” IEEE Transactions on
Knowledge and Data Engineering, vol. 26, no. 12, pp. 3026–3037, 2014.
➢ J. E. V. Ferreira, C. H. S. da Costa, R. M. de Miranda, and A. F. de Figueiredo, “The use of the k nearest neighbor method
to classify the representative elements,” Educación Química, vol. 26, no. 3, pp. 195 – 201, 2015. [Online]. Available:
http://www.sciencedirect.com/science/article/pii/S0187893X15000312
➢ P. Mulak and N. Talhar, “Analysis of distance measures using k-nearest neighbor algorithm on kdd dataset,”
International Journal of Science and Research, vol. 4, no. 7, pp. 2101–2104, 2015.
➢ T. Kohno, A. Broido, and K. C. Claffy, “Remote physical device fingerprinting,” IEEE Transactions on Dependable and
Secure Computing, vol. 2, no. 2, pp. 93–108, 2005.
➢ M. Cristea and B. Groza, “Fingerprinting smartphones remotely via ICMP timestamps,” IEEE Communications Letters,
vol. 17, no. 6, pp. 1081–1083, 2013.](https://image.slidesharecdn.com/presentation-eleko2-181202154016/85/Device-Fingerprinting-for-Authentication-12-320.jpg)
