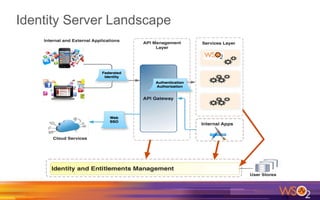
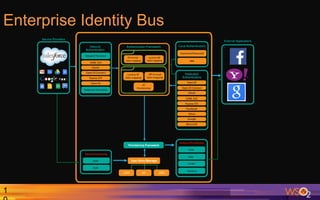
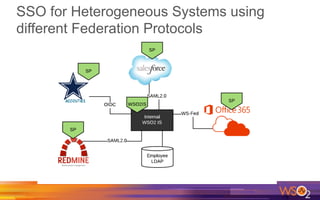
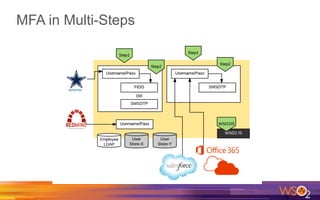
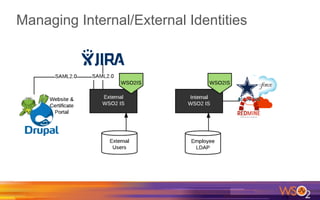
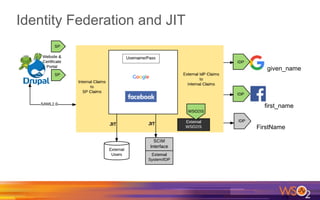
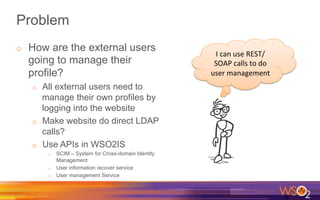
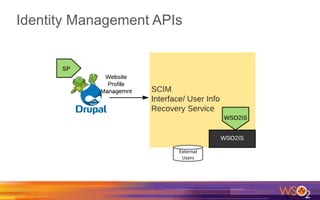
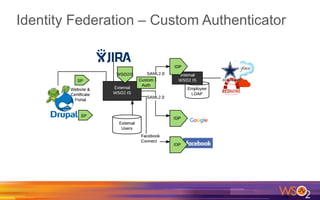
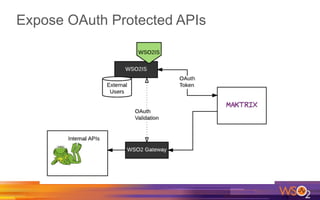
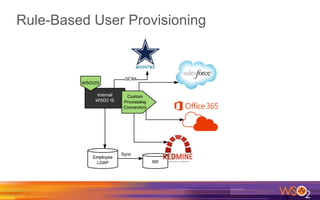
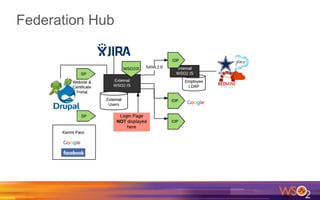
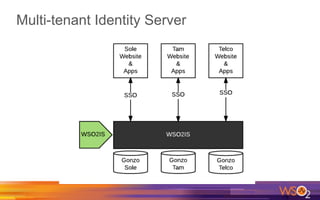
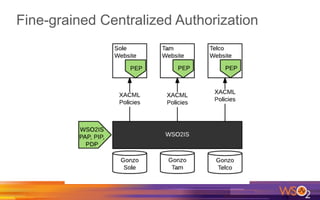
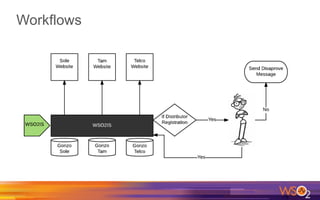
Kermit Co. is upgrading its identity management system to address several problems: 1) employees need single sign-on across internal and cloud applications using different protocols; 2) strengthening security by adding multi-factor authentication; 3) managing external identities at scale including social logins and just-in-time provisioning; 4) exposing APIs securely and automating provisioning using rules. The WSO2 Identity Server provides an enterprise identity bus to federate identities across systems using various protocols while allowing management of internal and external identities at different assurance levels through APIs.