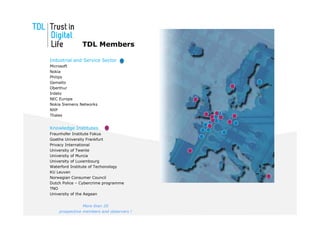
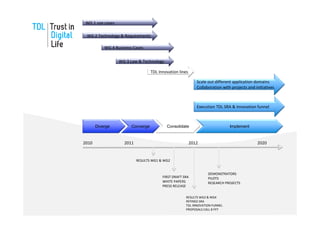
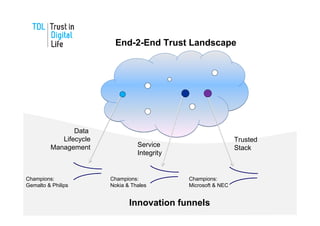
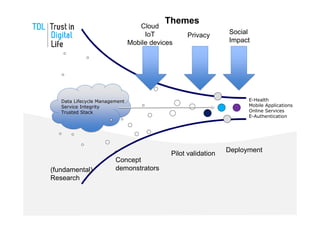
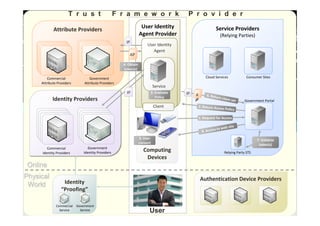
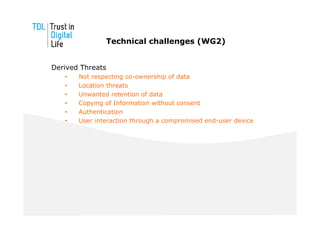
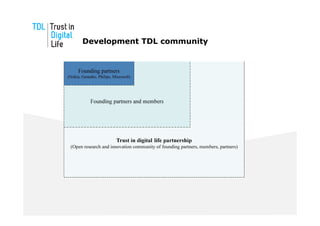
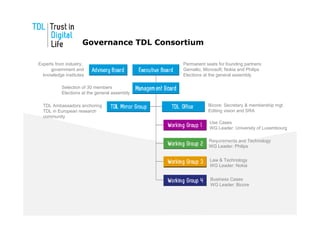
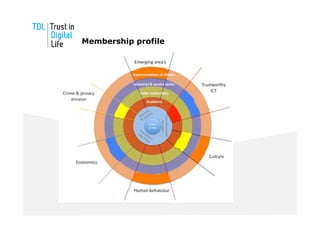
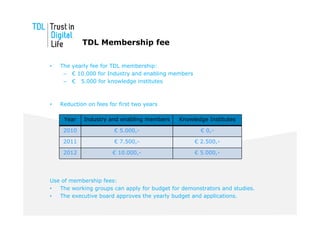
The document discusses the Trust in Digital Life (TDL) consortium, which aims to stimulate research and development of trustworthy information and communication technology (ICT) solutions. TDL has over 20 members from industry, academia, and government working to set a research agenda. The consortium's goals are to establish an inspiring and self-sustaining community to advance knowledge and collaborative projects, develop an innovative research agenda, enable public funding for related projects, and increase awareness through demonstrations. TDL will measure progress using key performance indicators like adoption rates of e-services and survey scores on consumer trust.