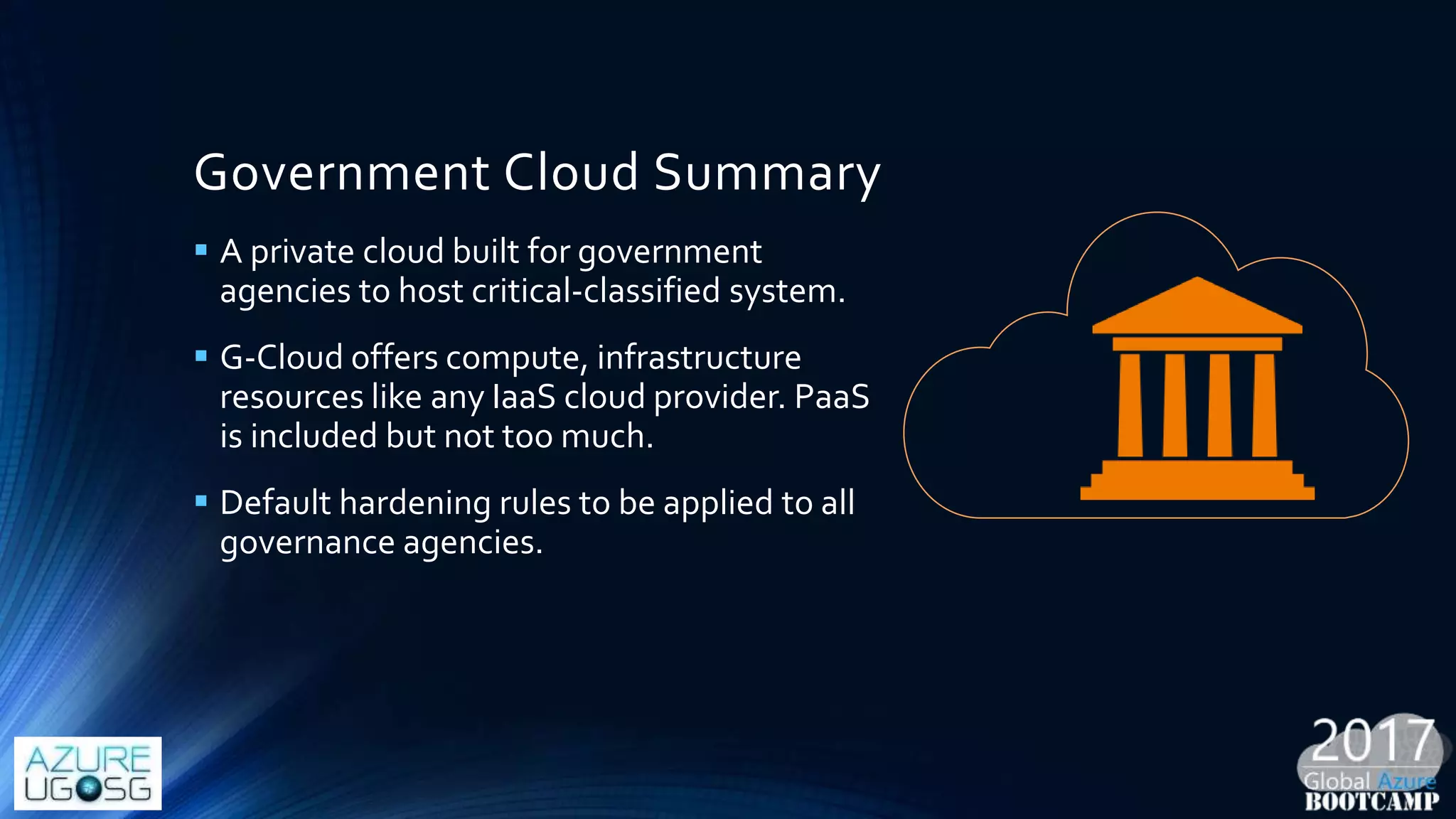
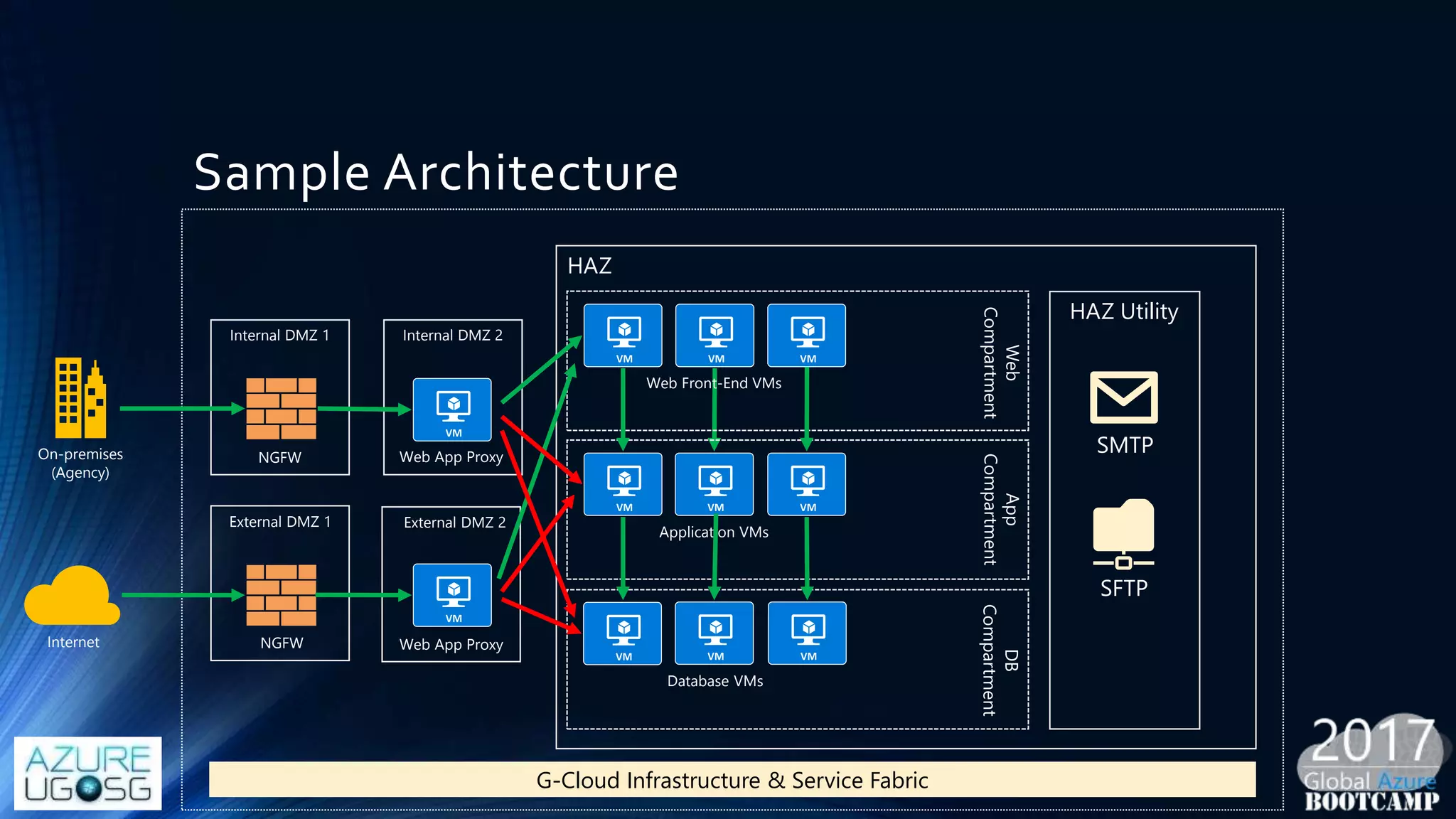
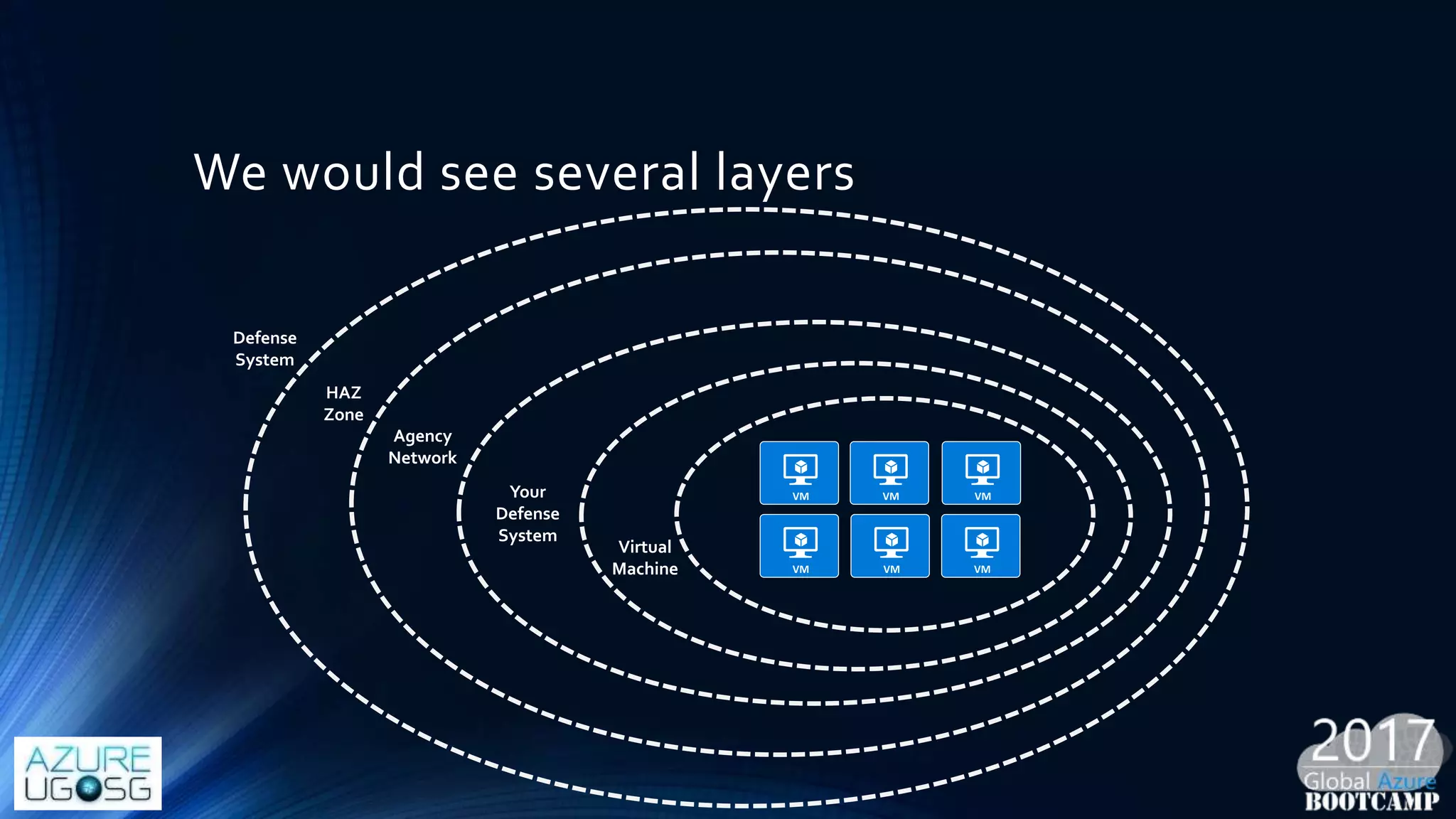
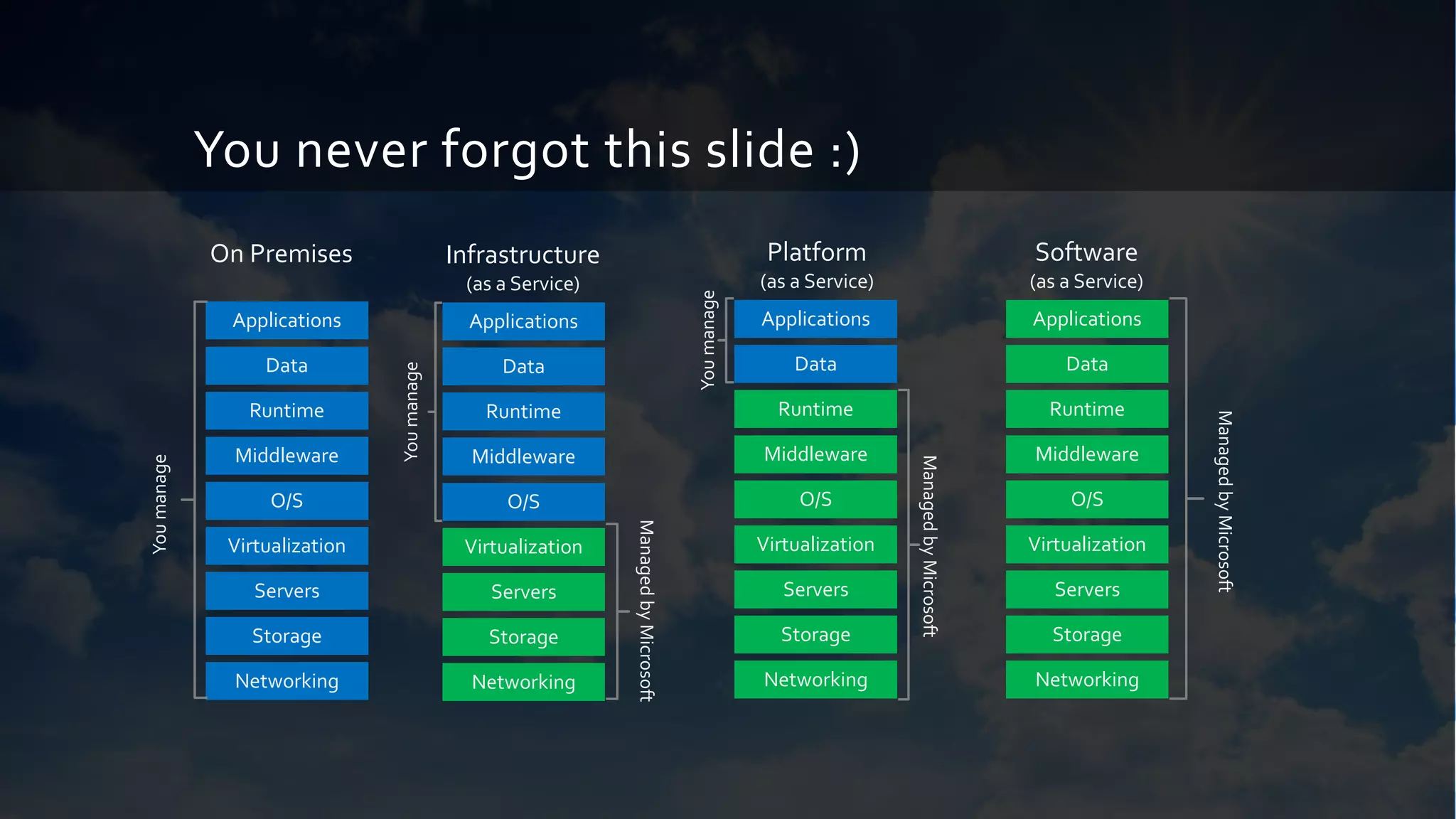
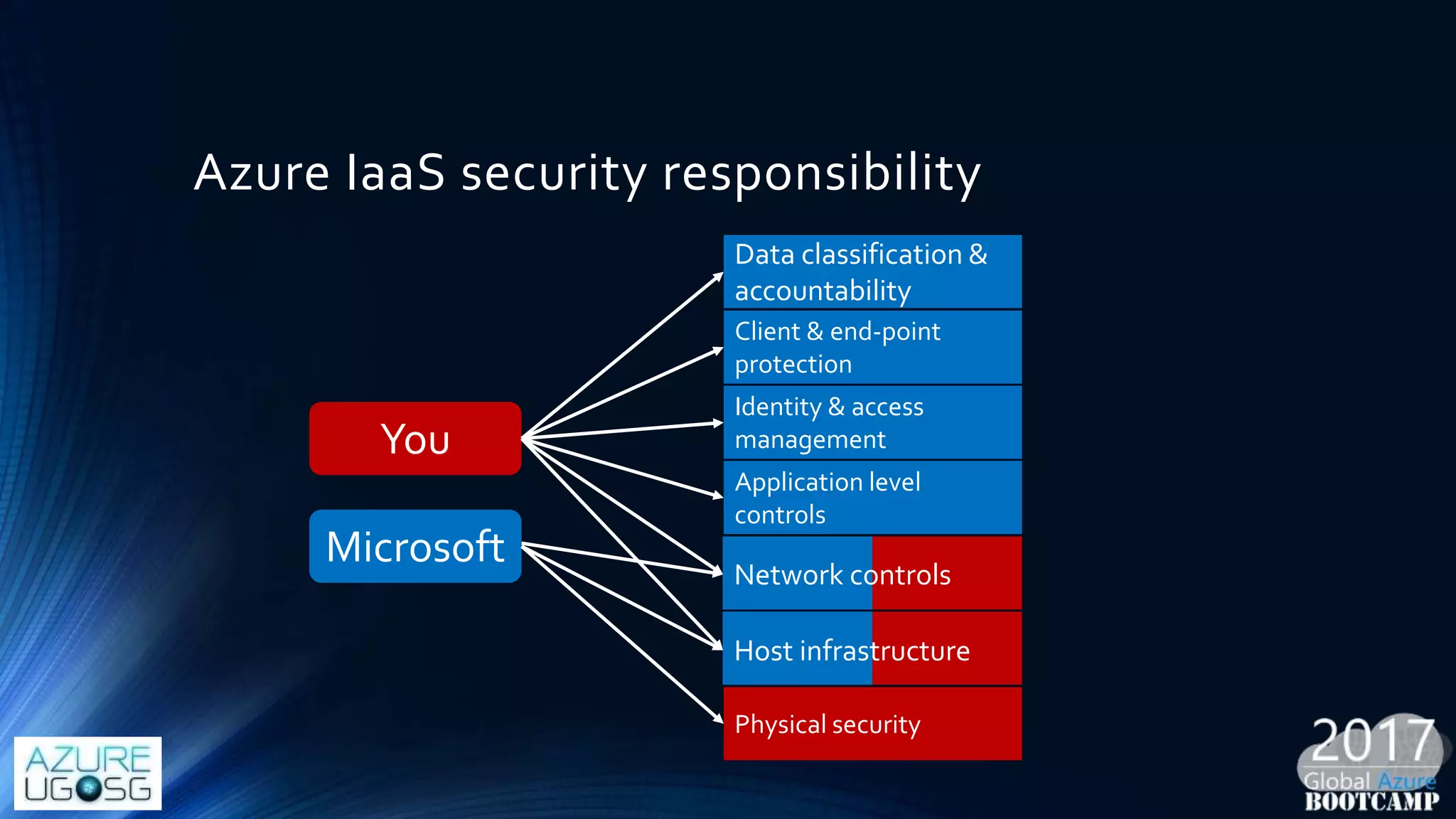
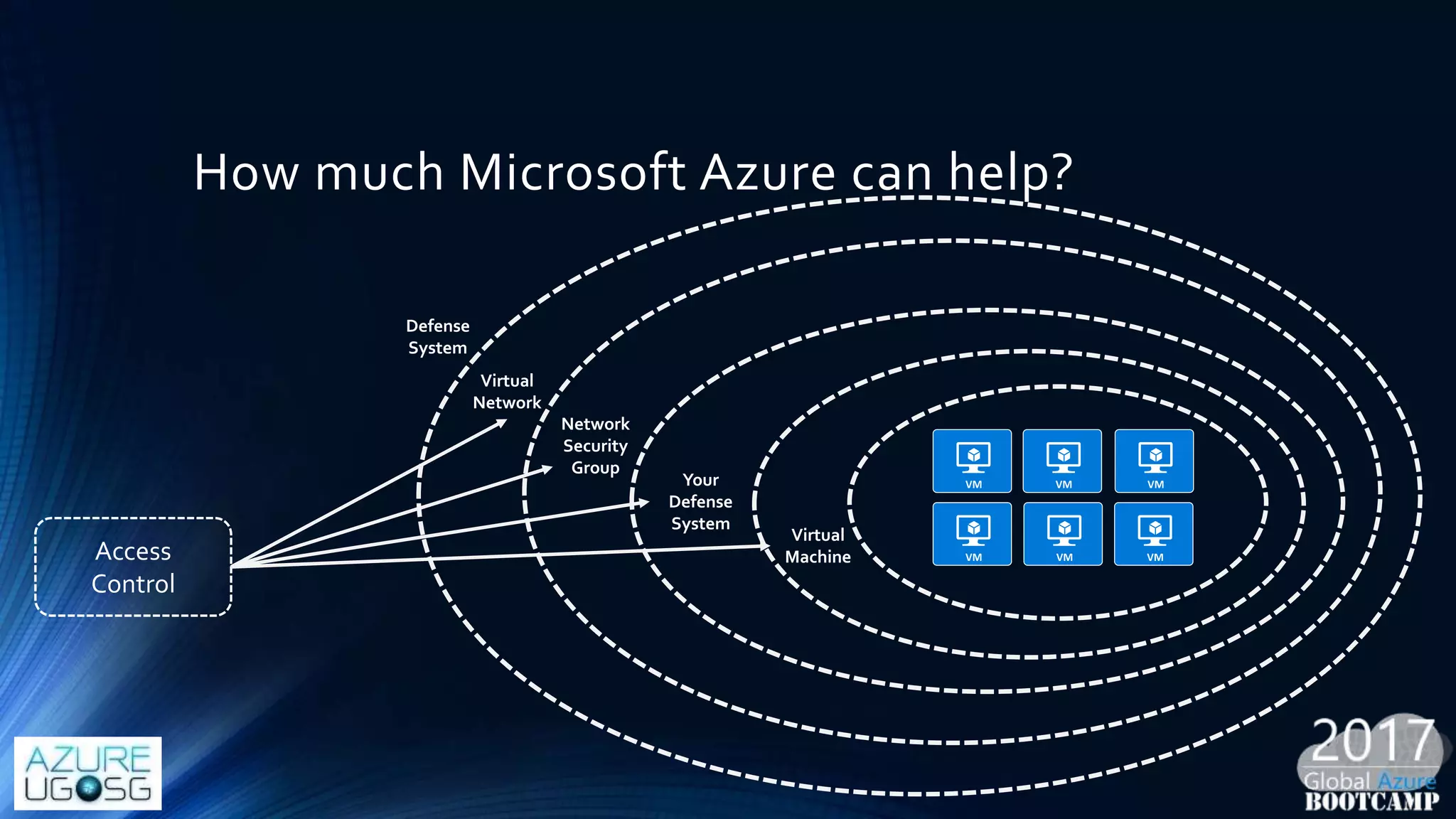
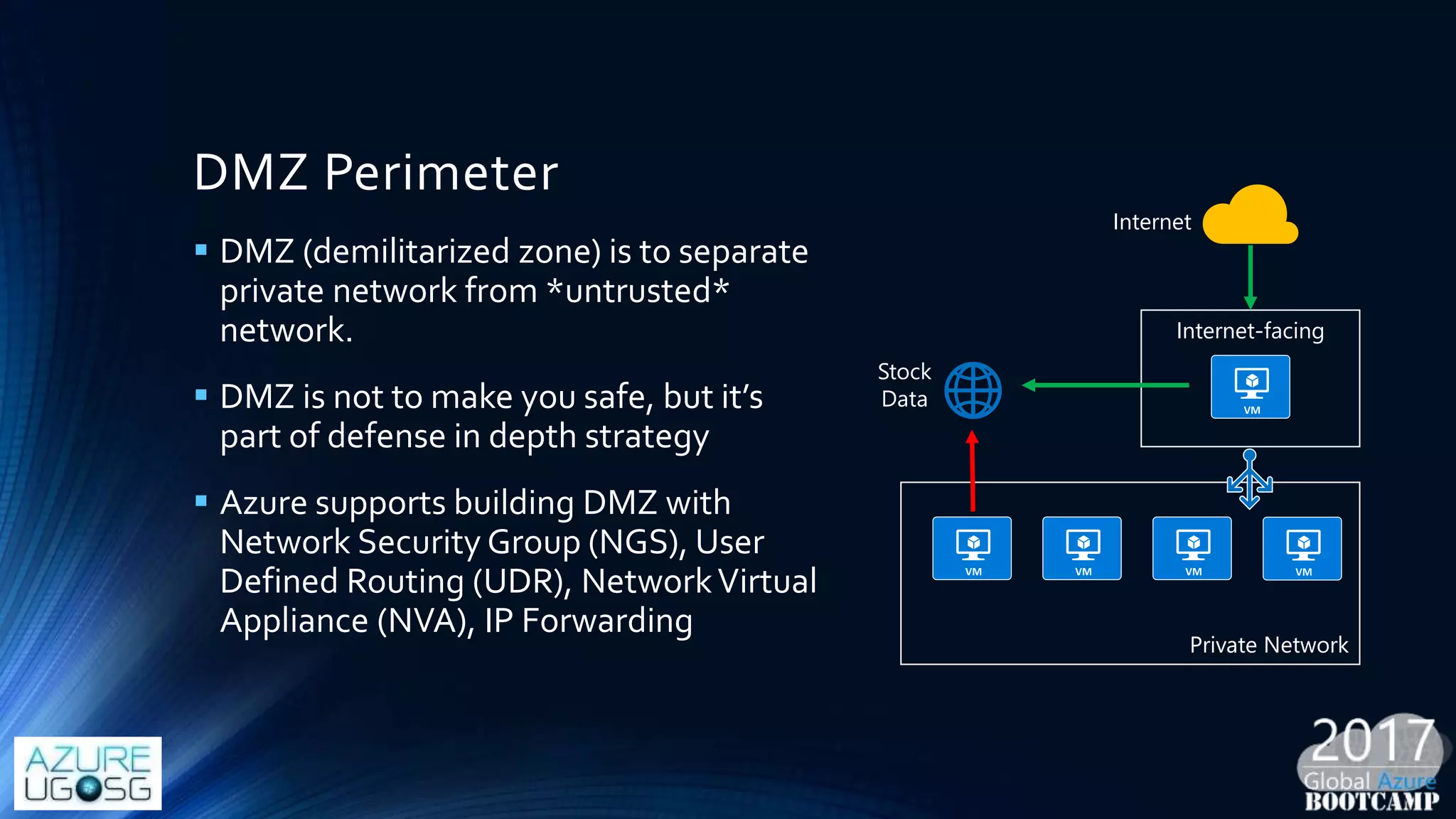
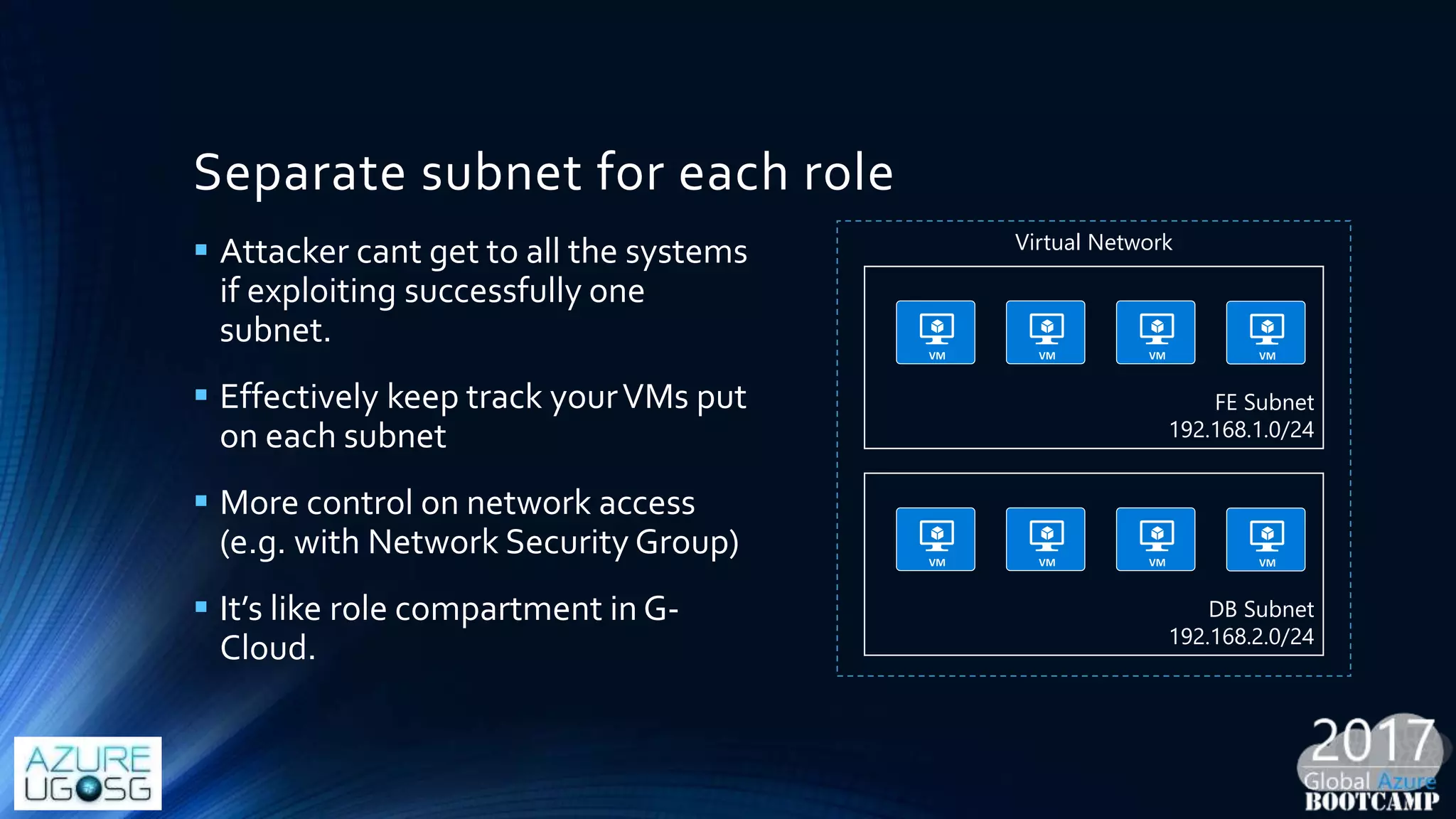
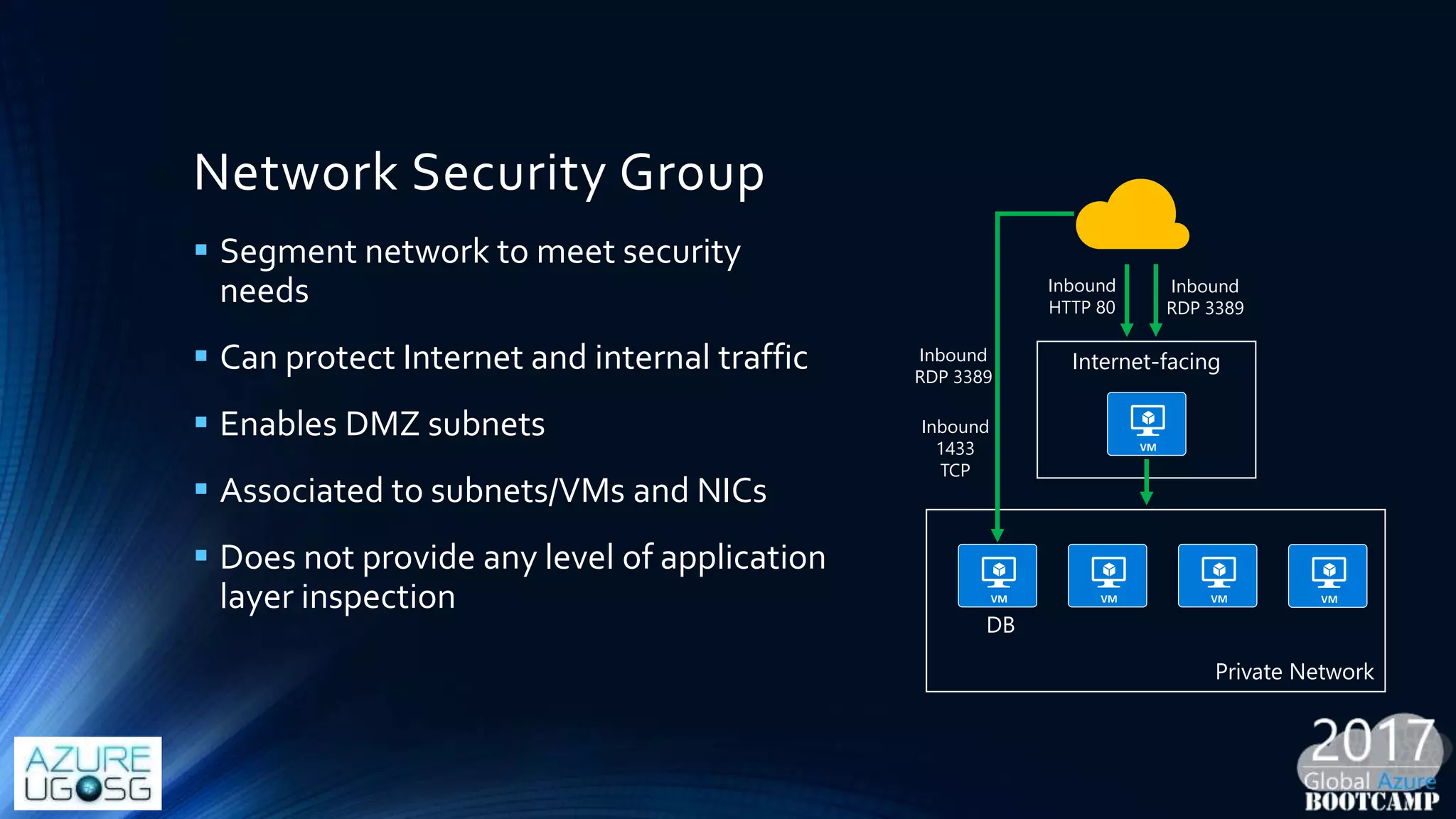
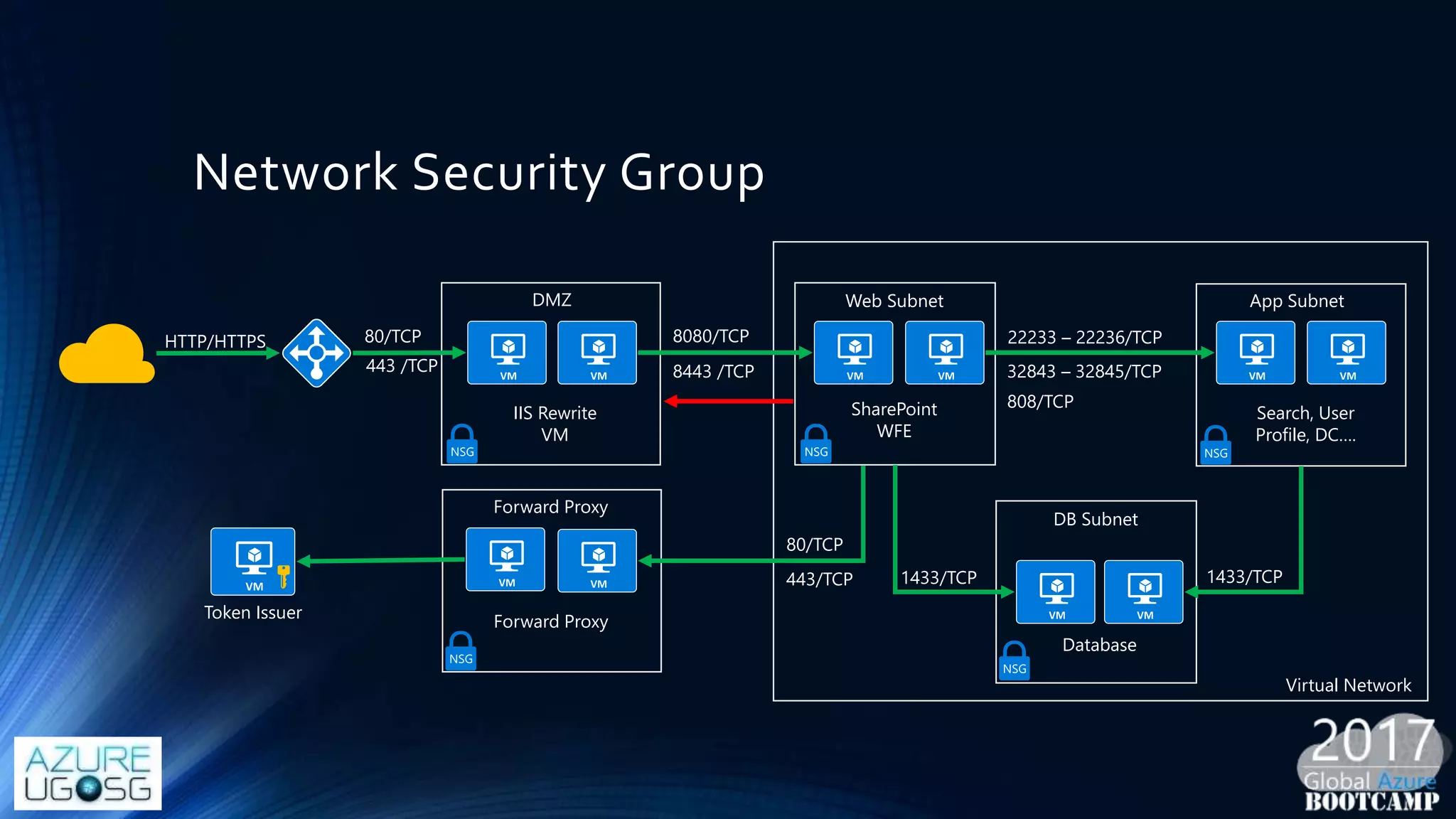
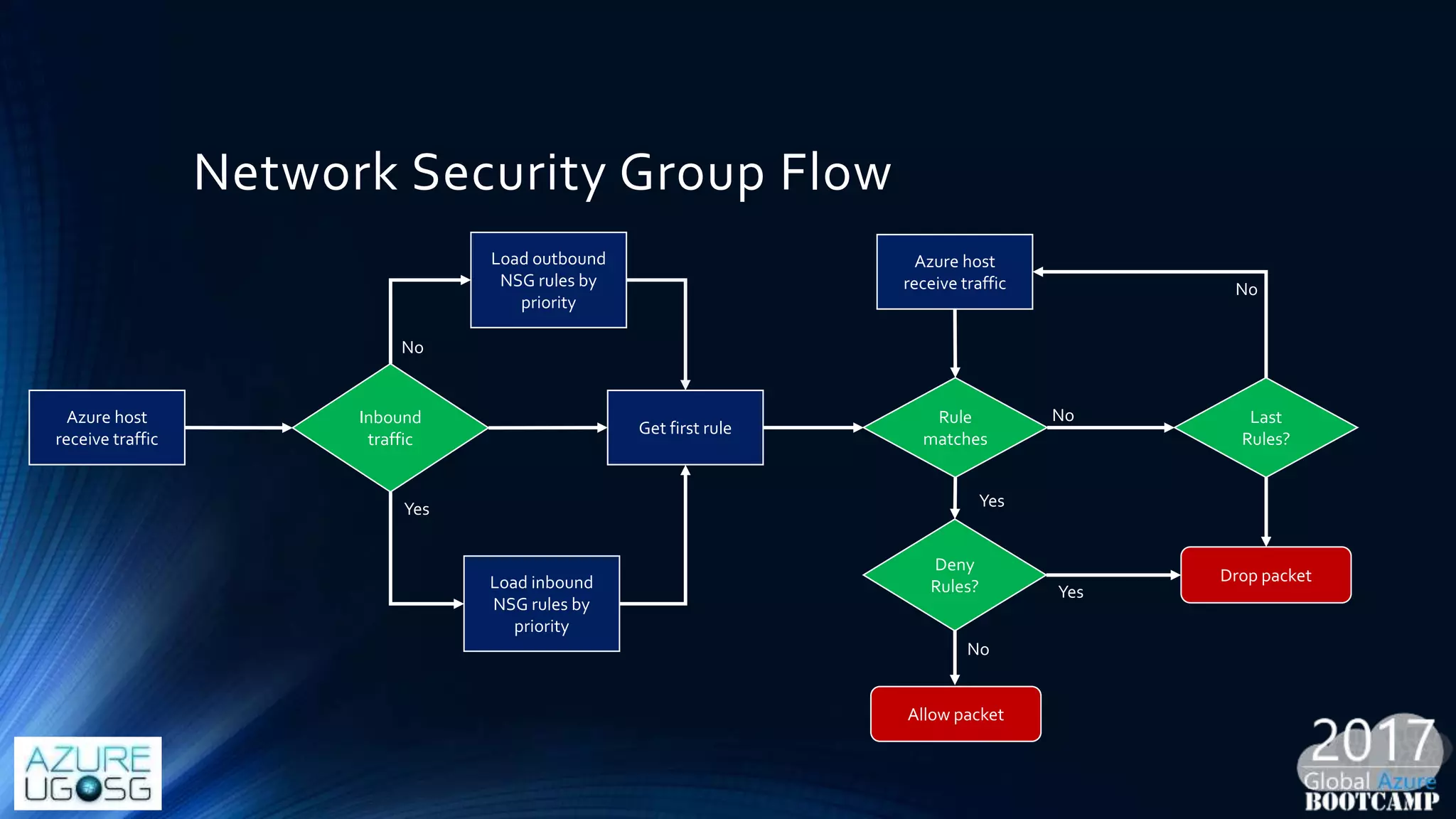
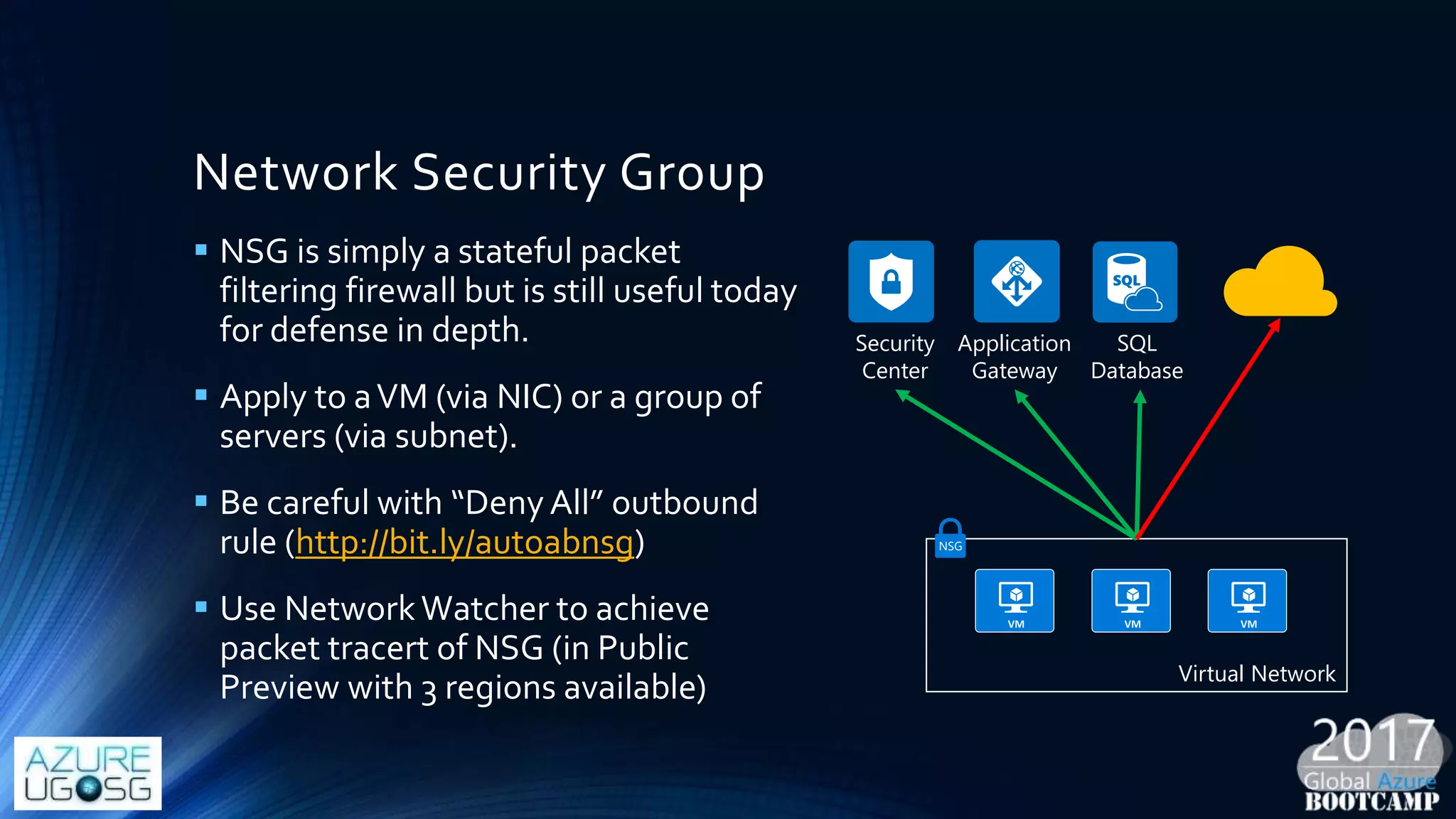
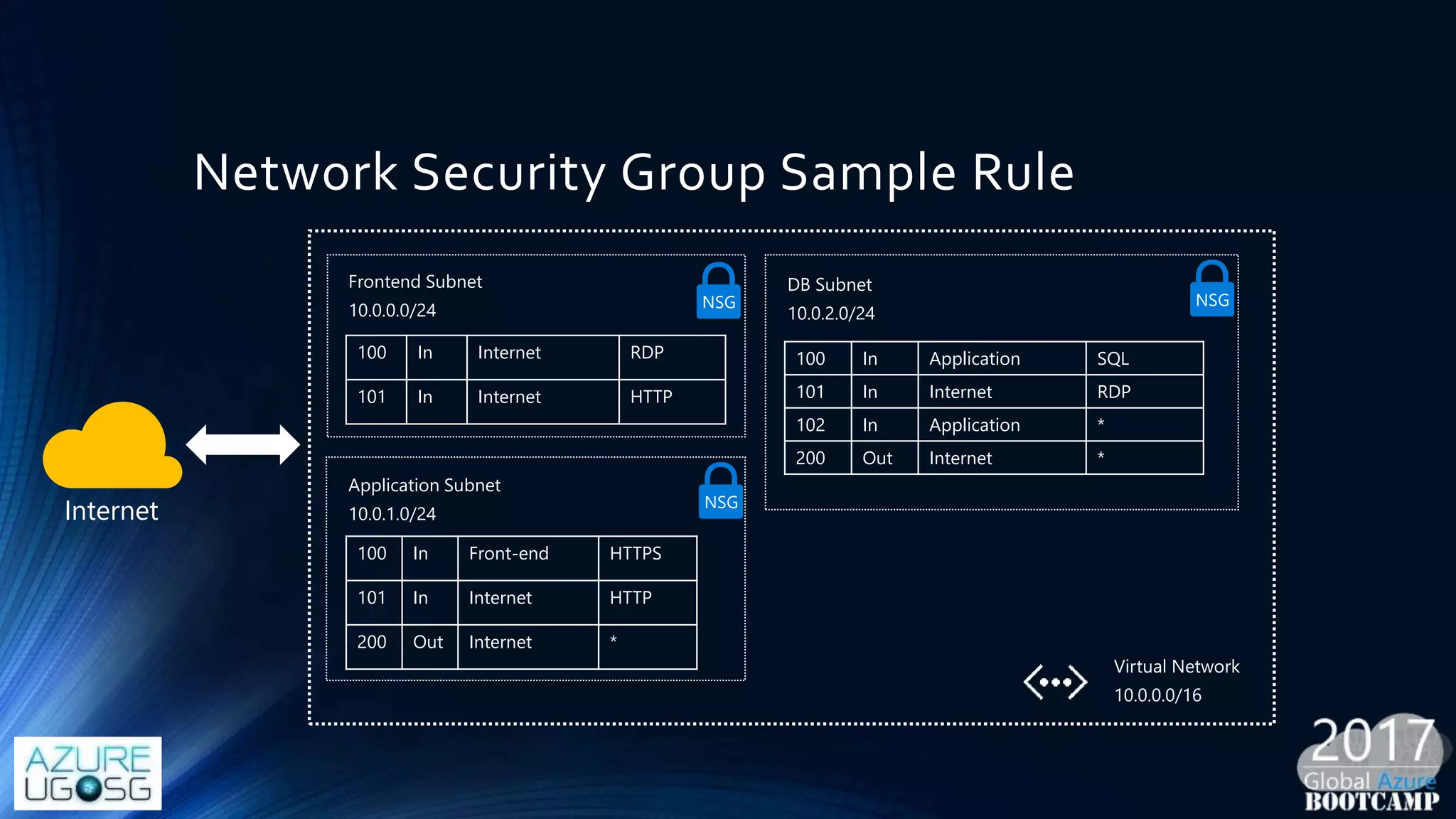
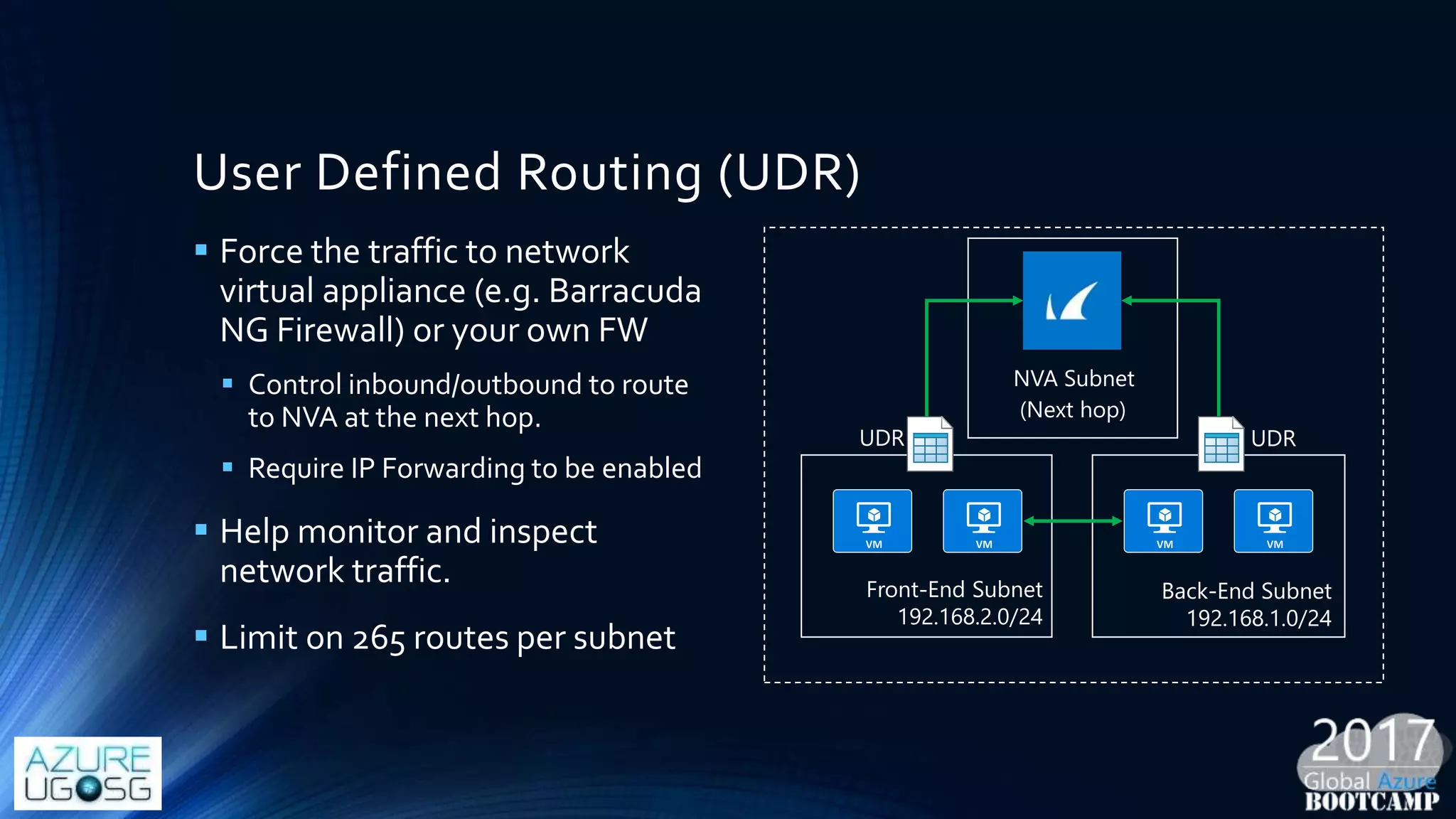
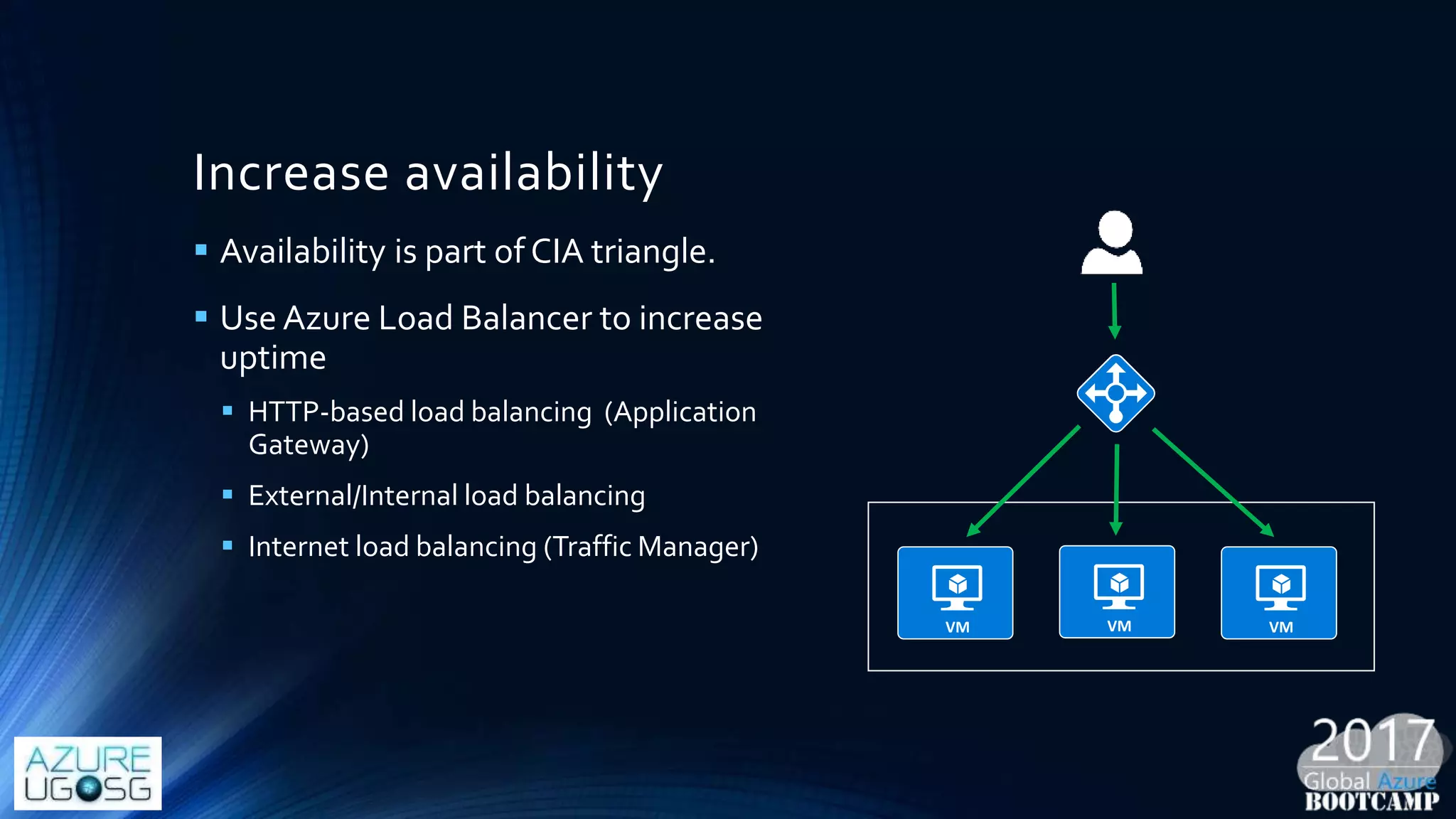
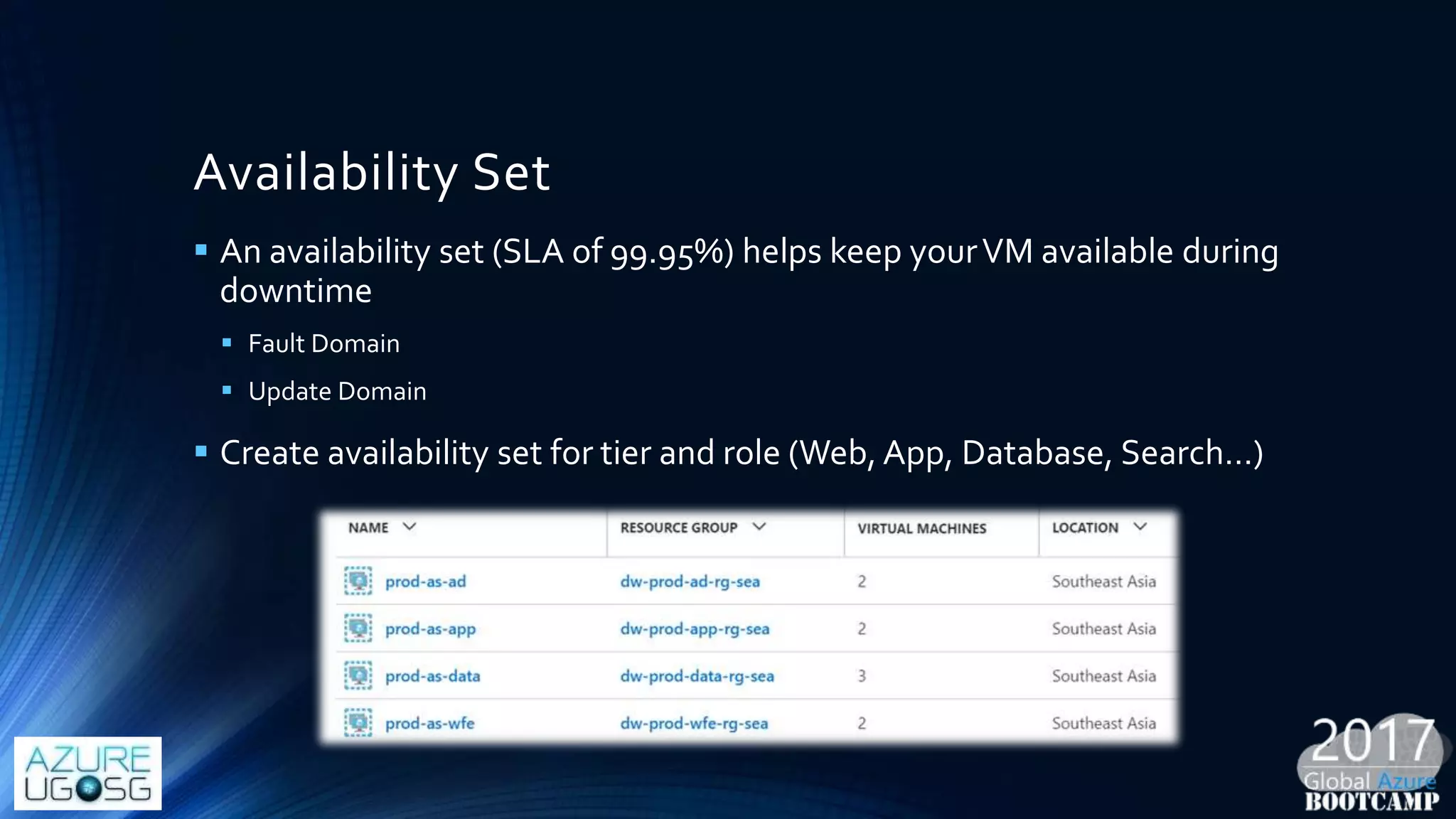
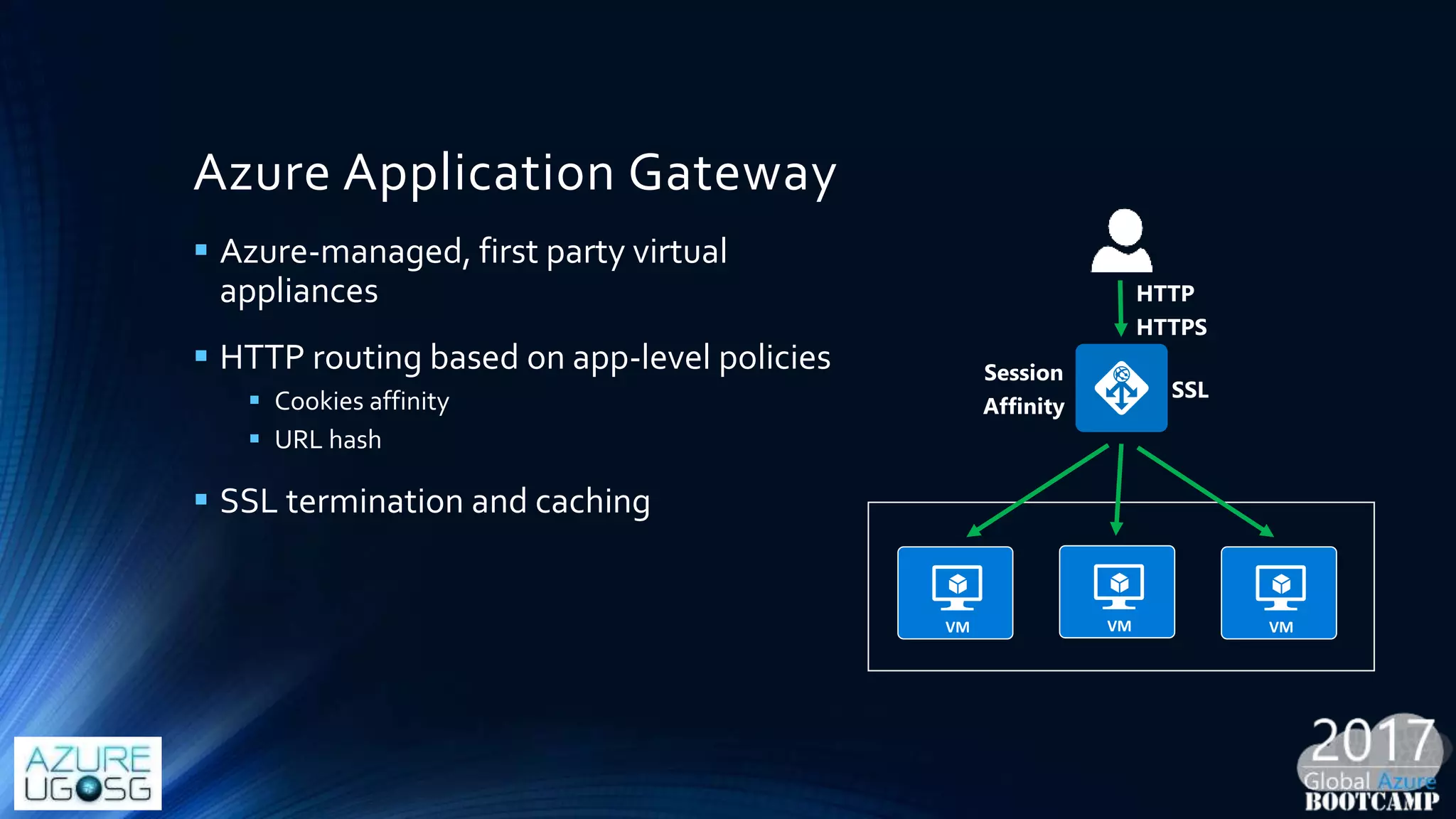
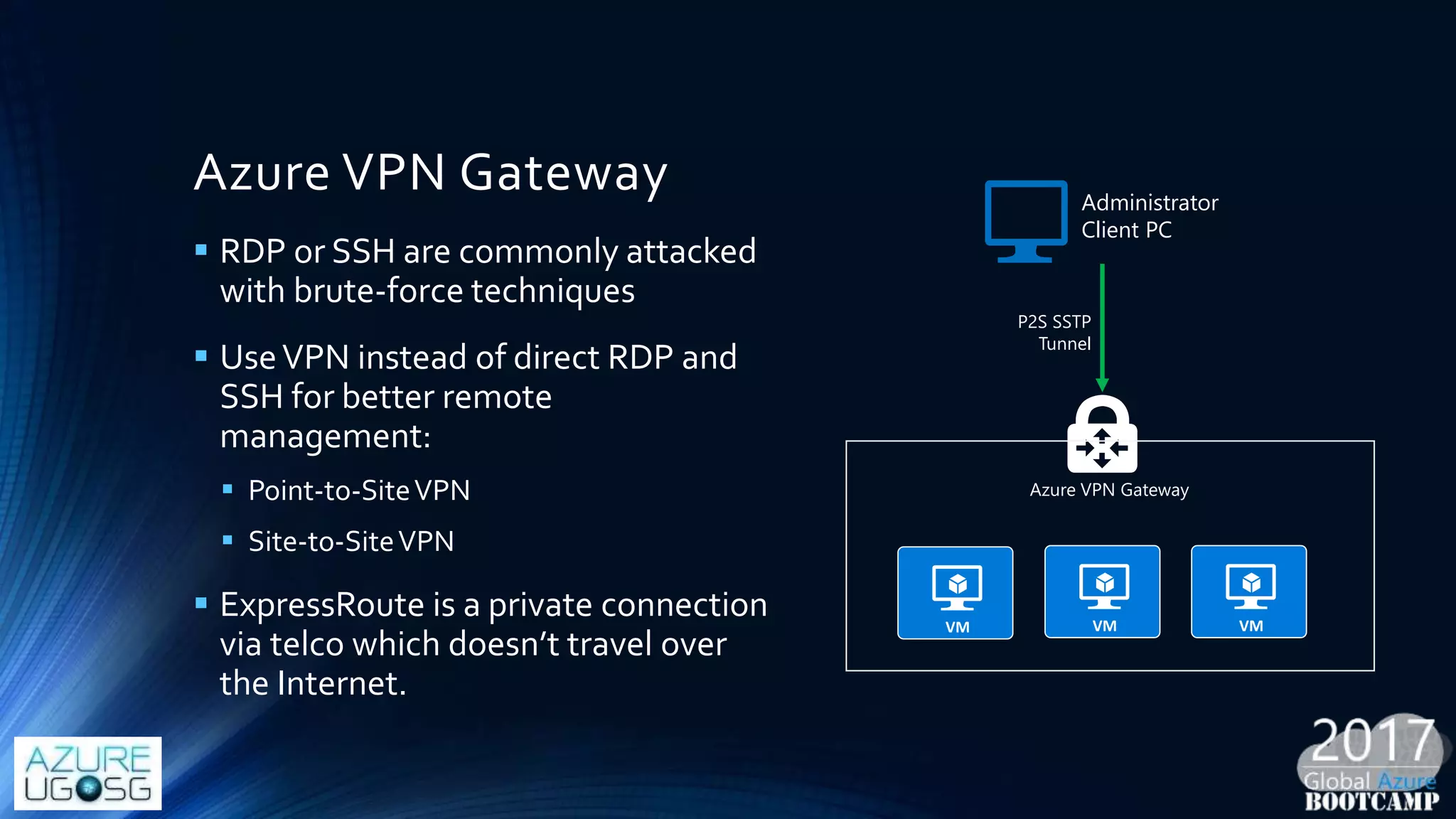
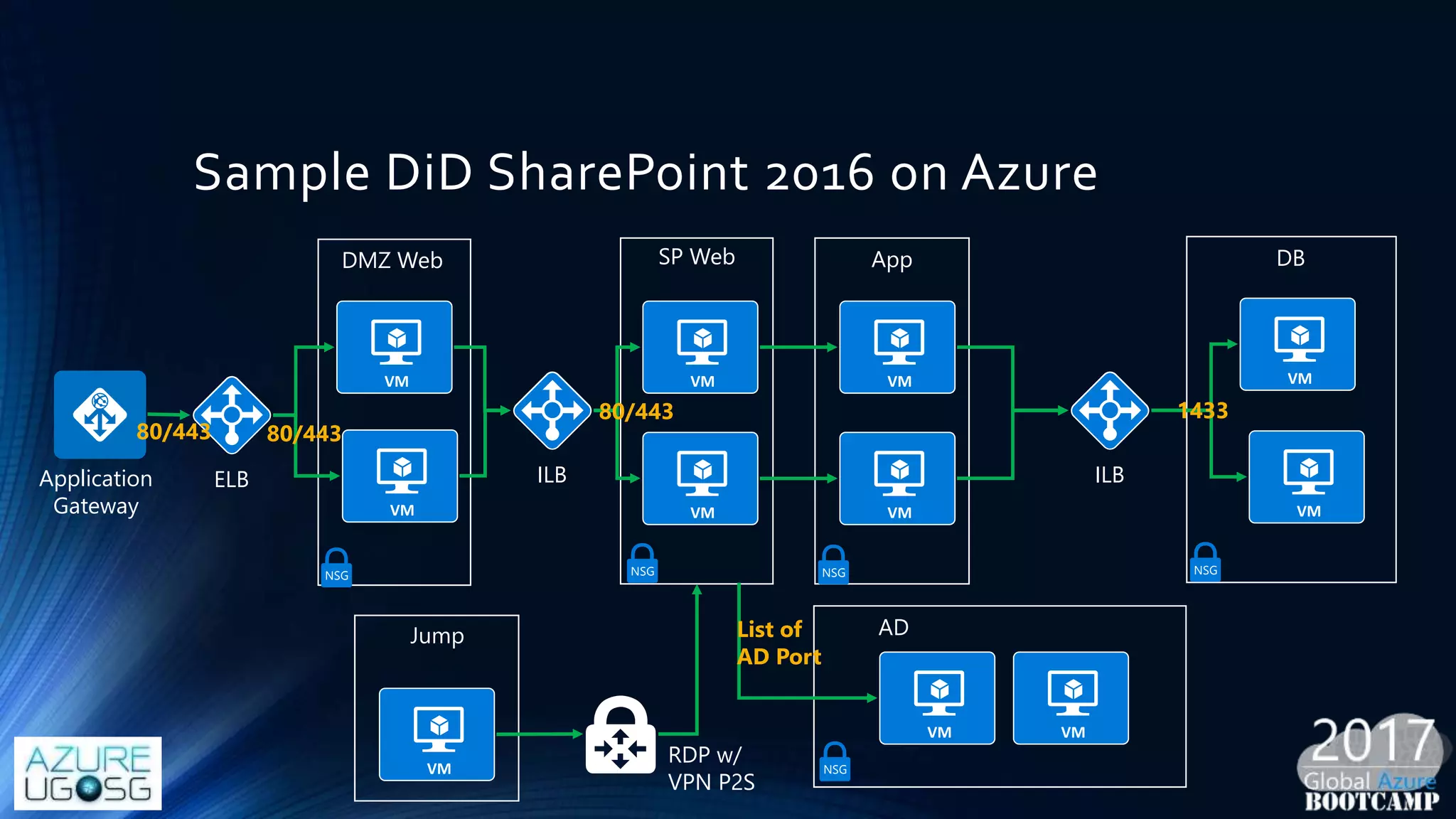
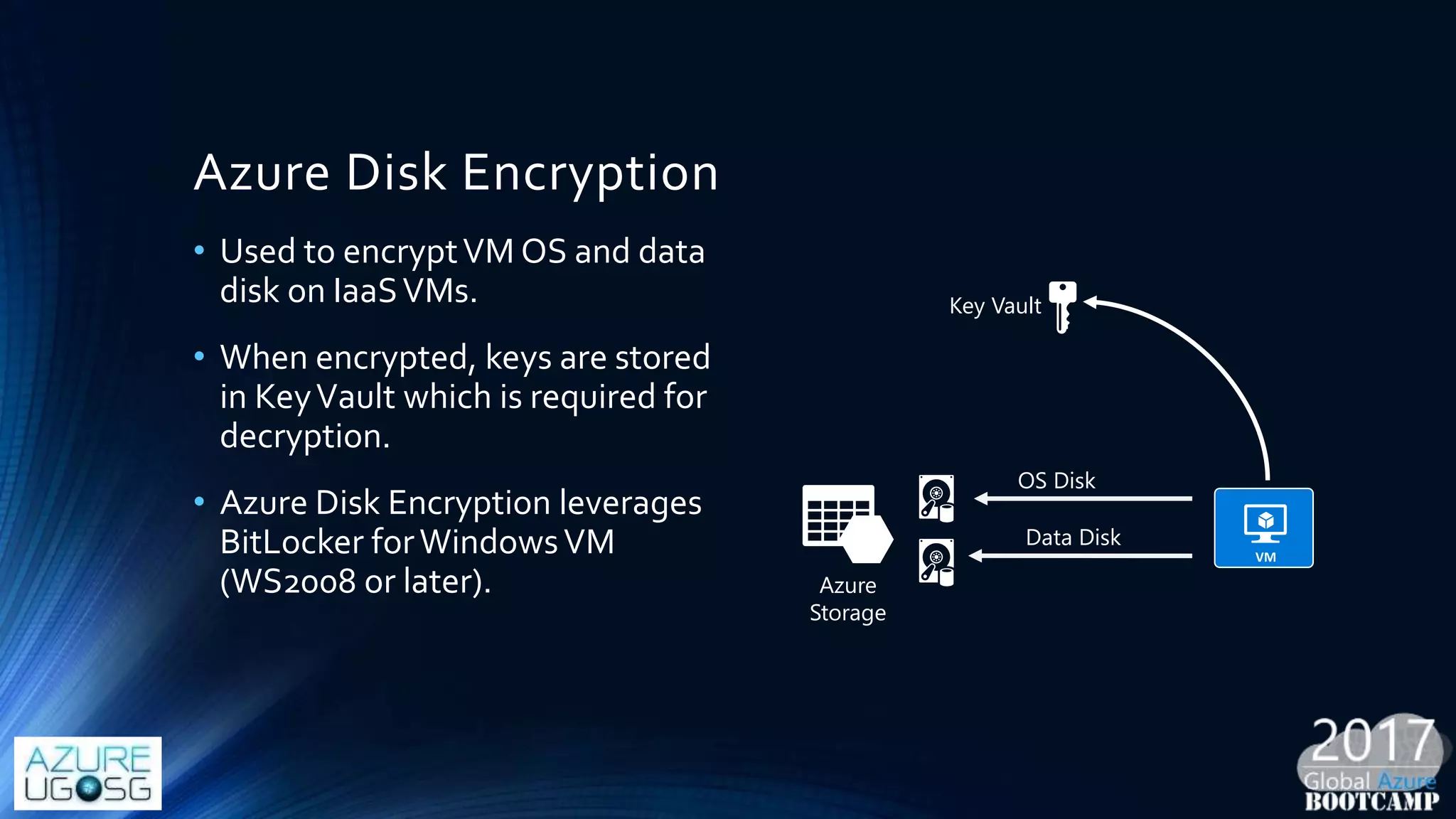
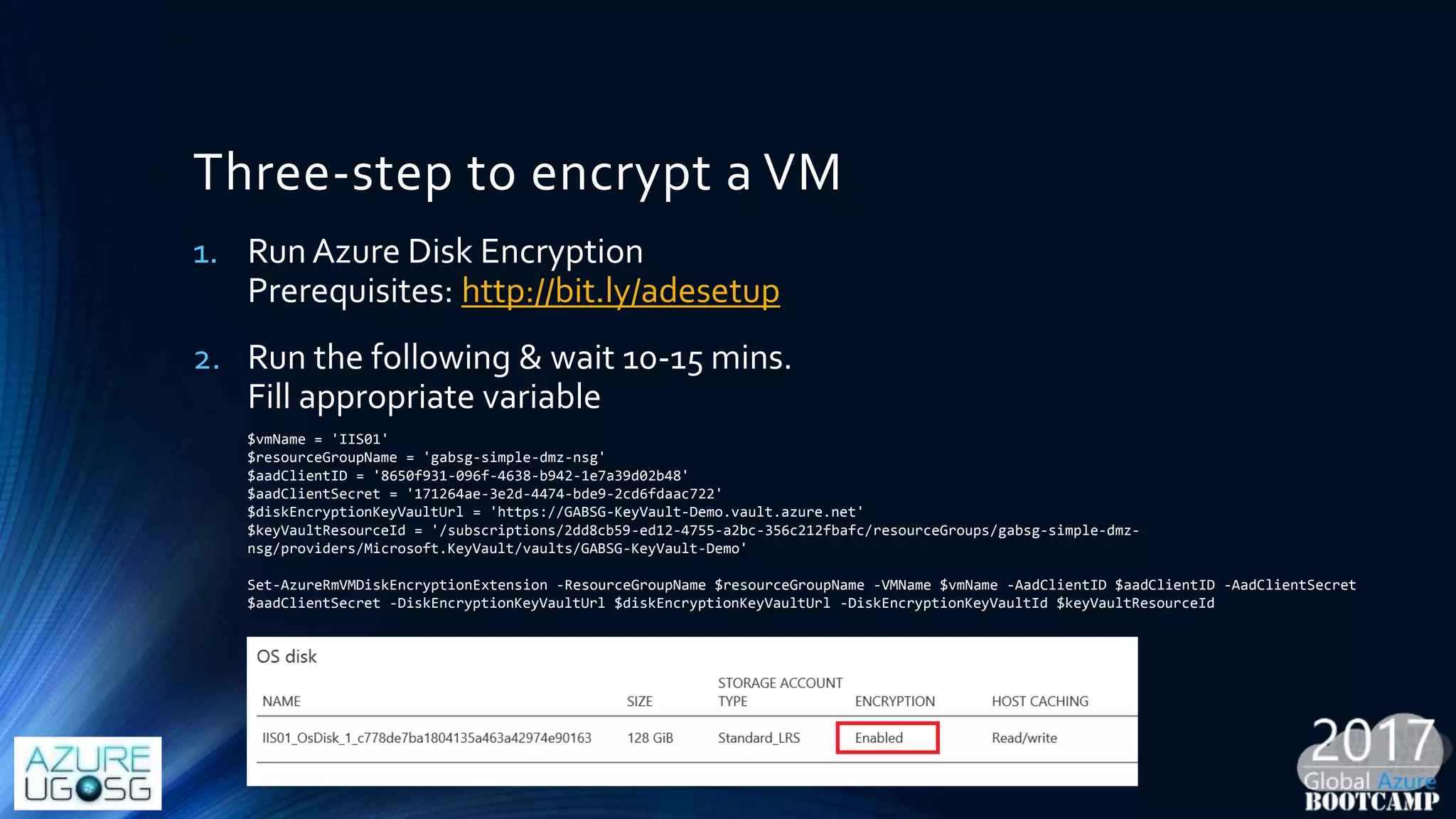
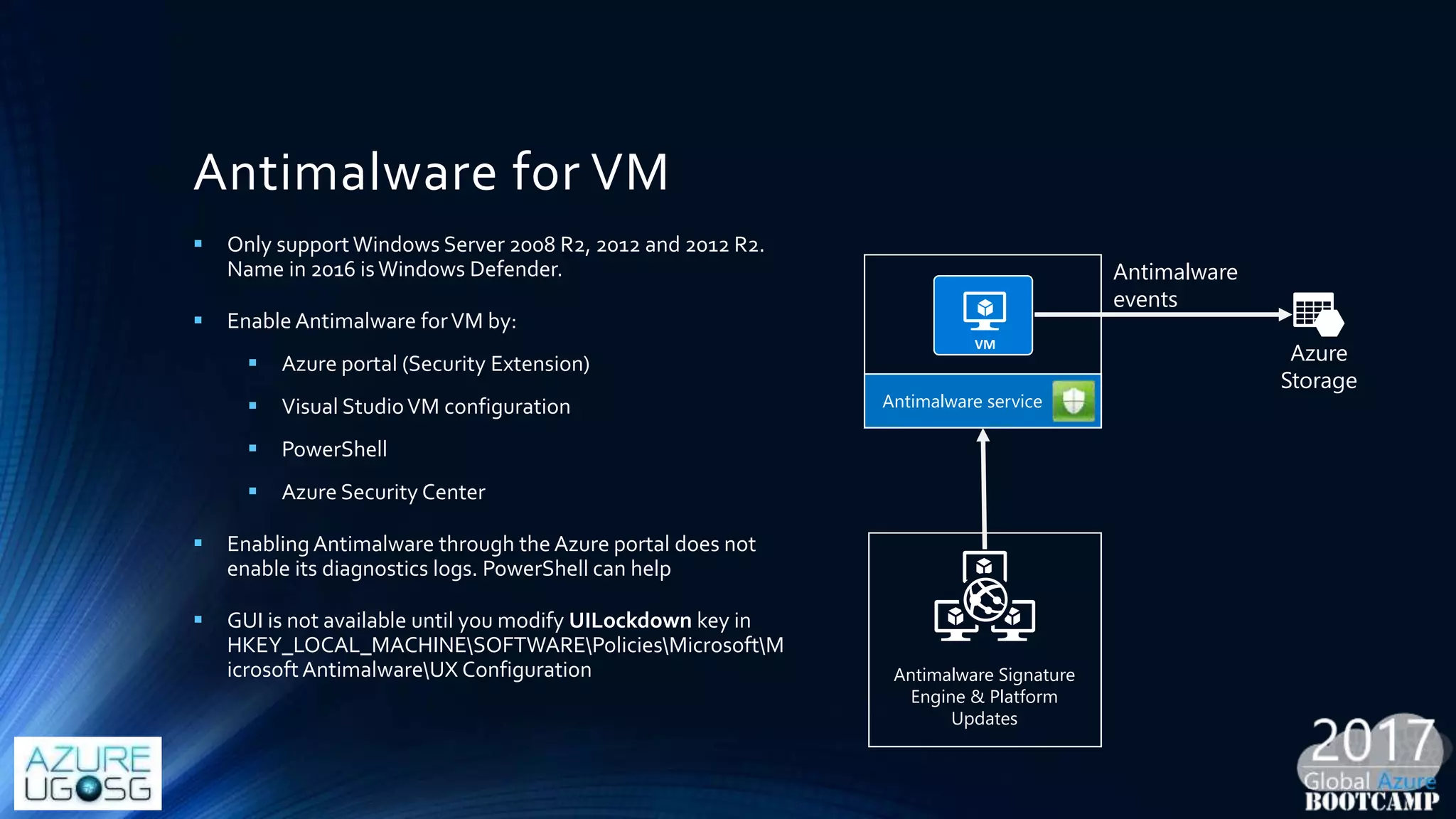
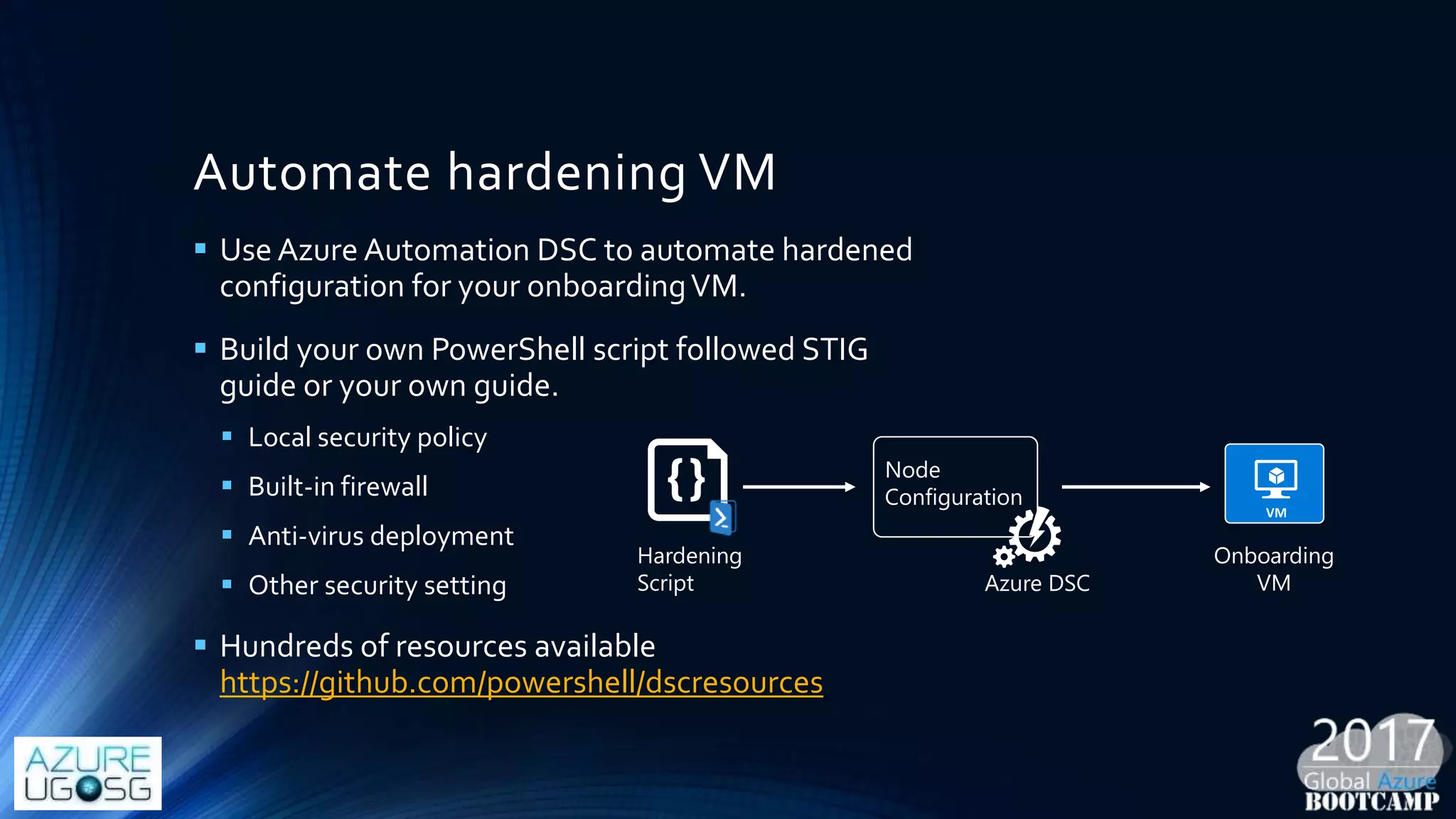
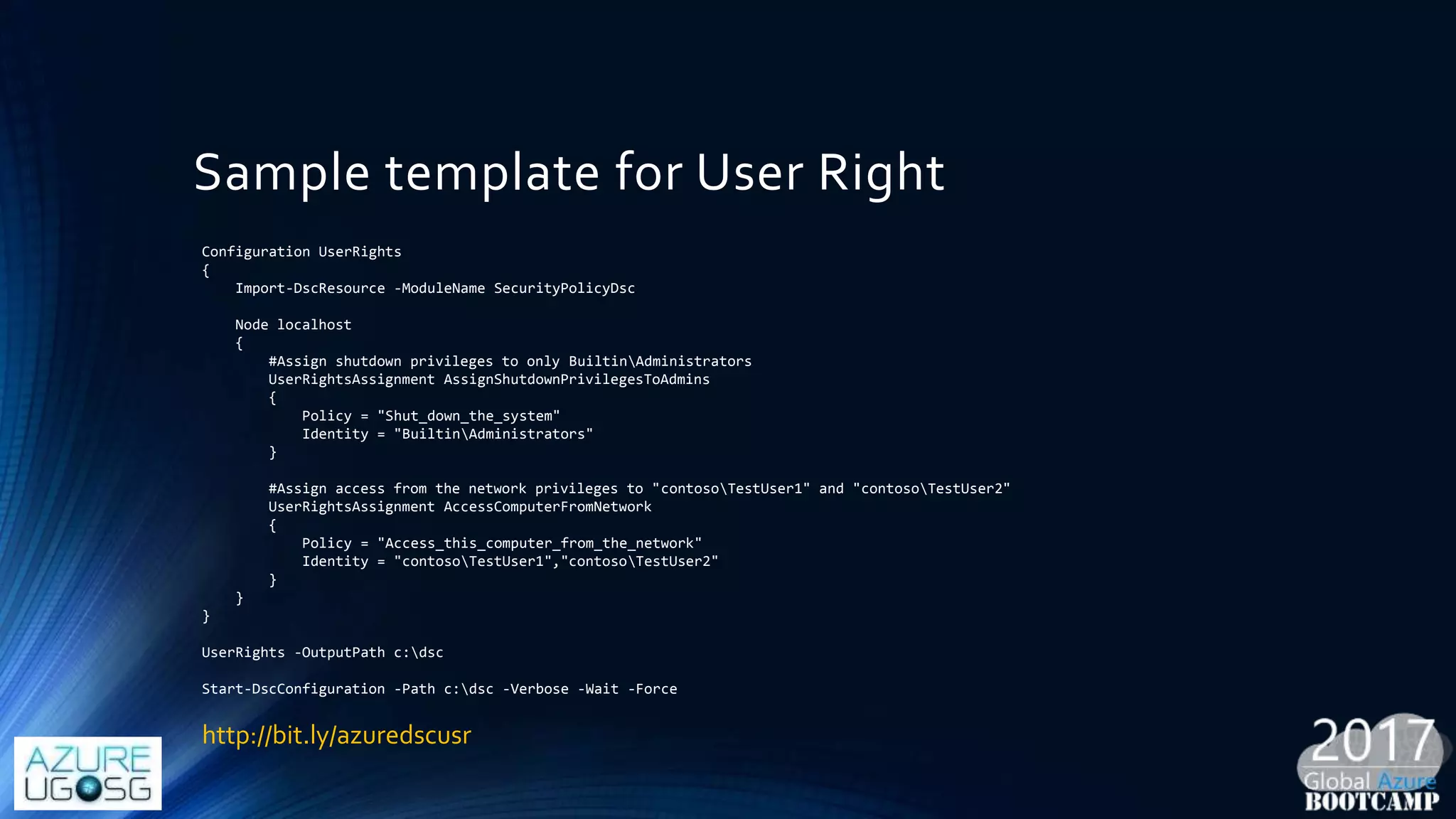
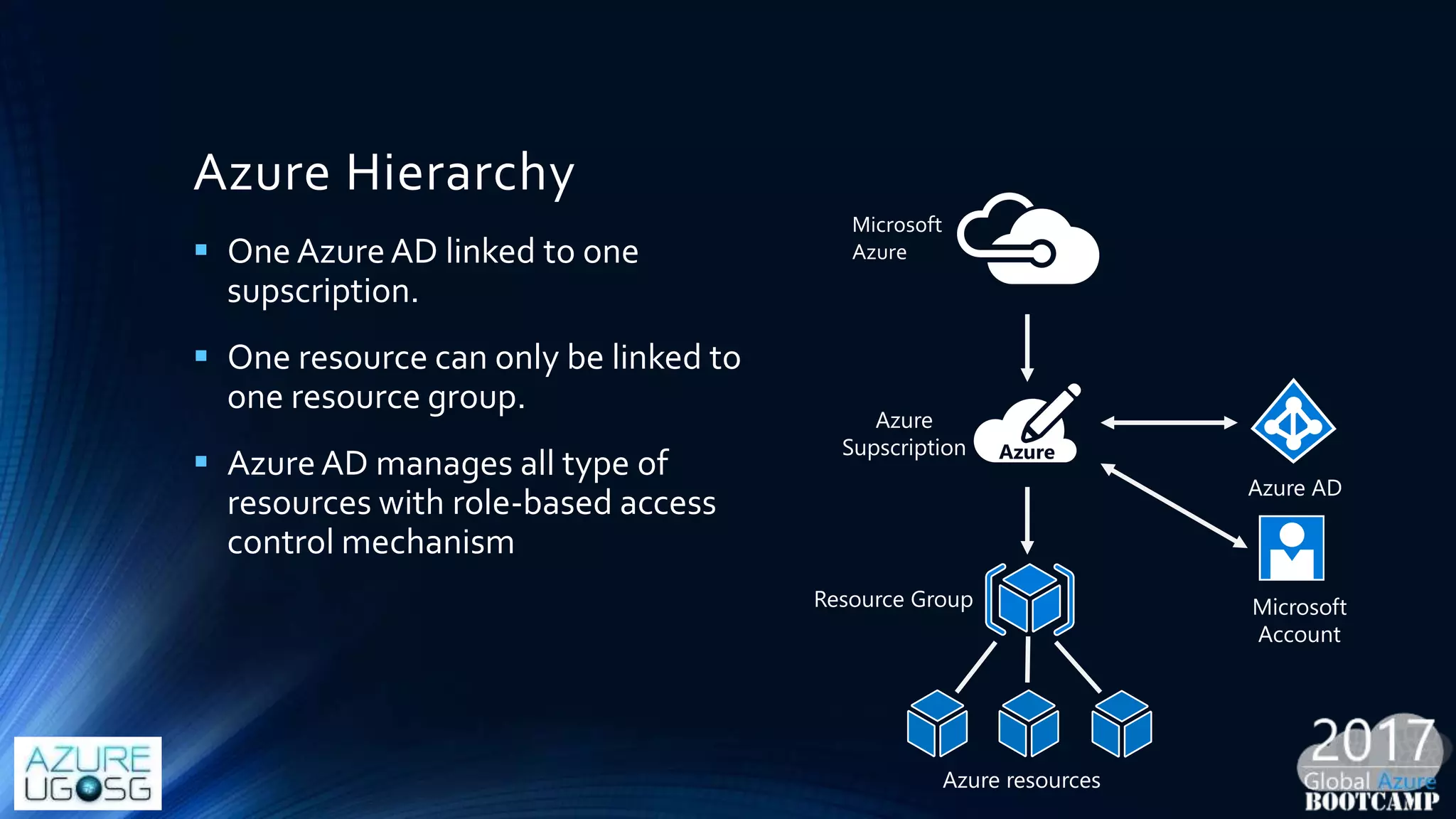
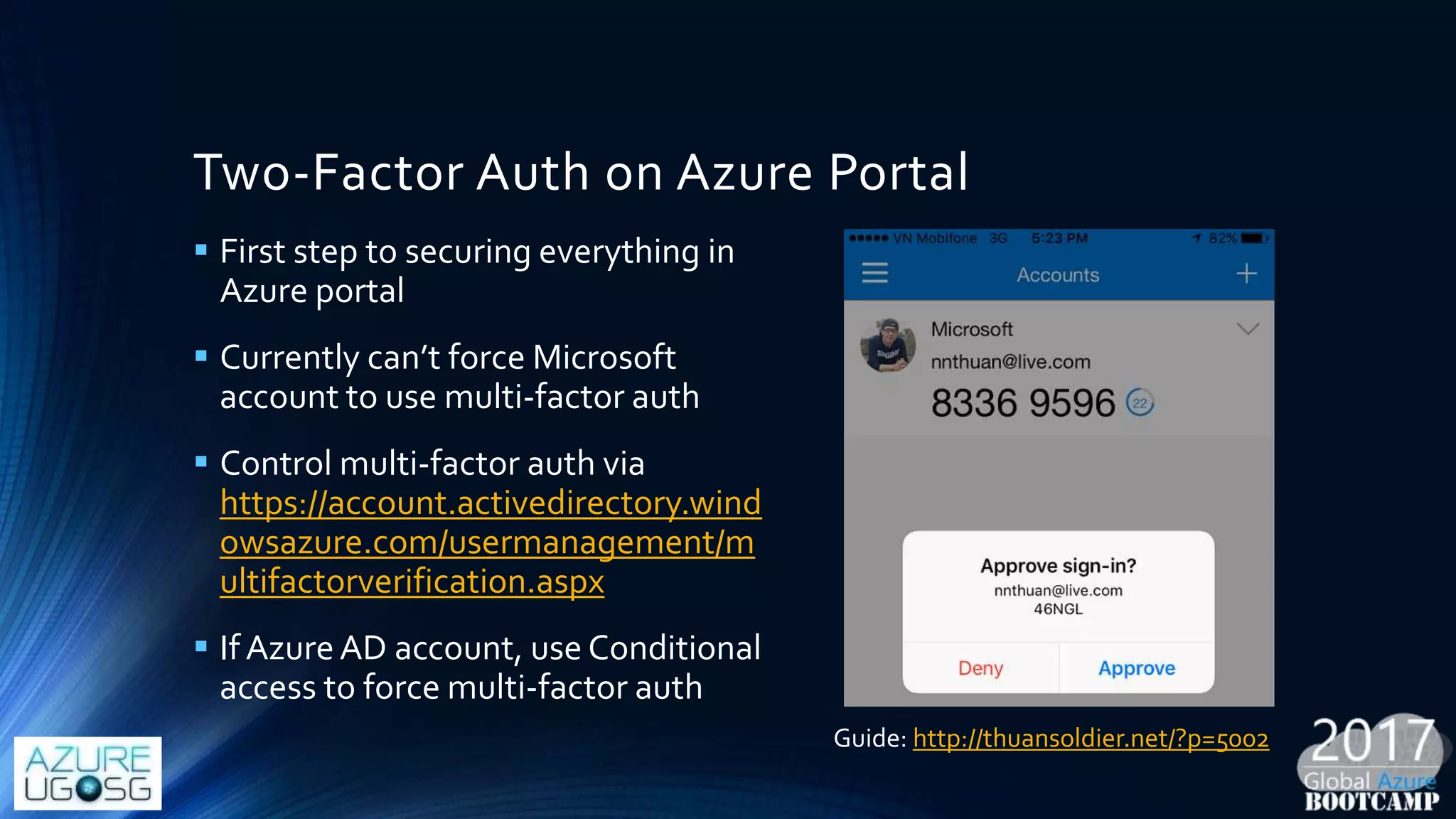
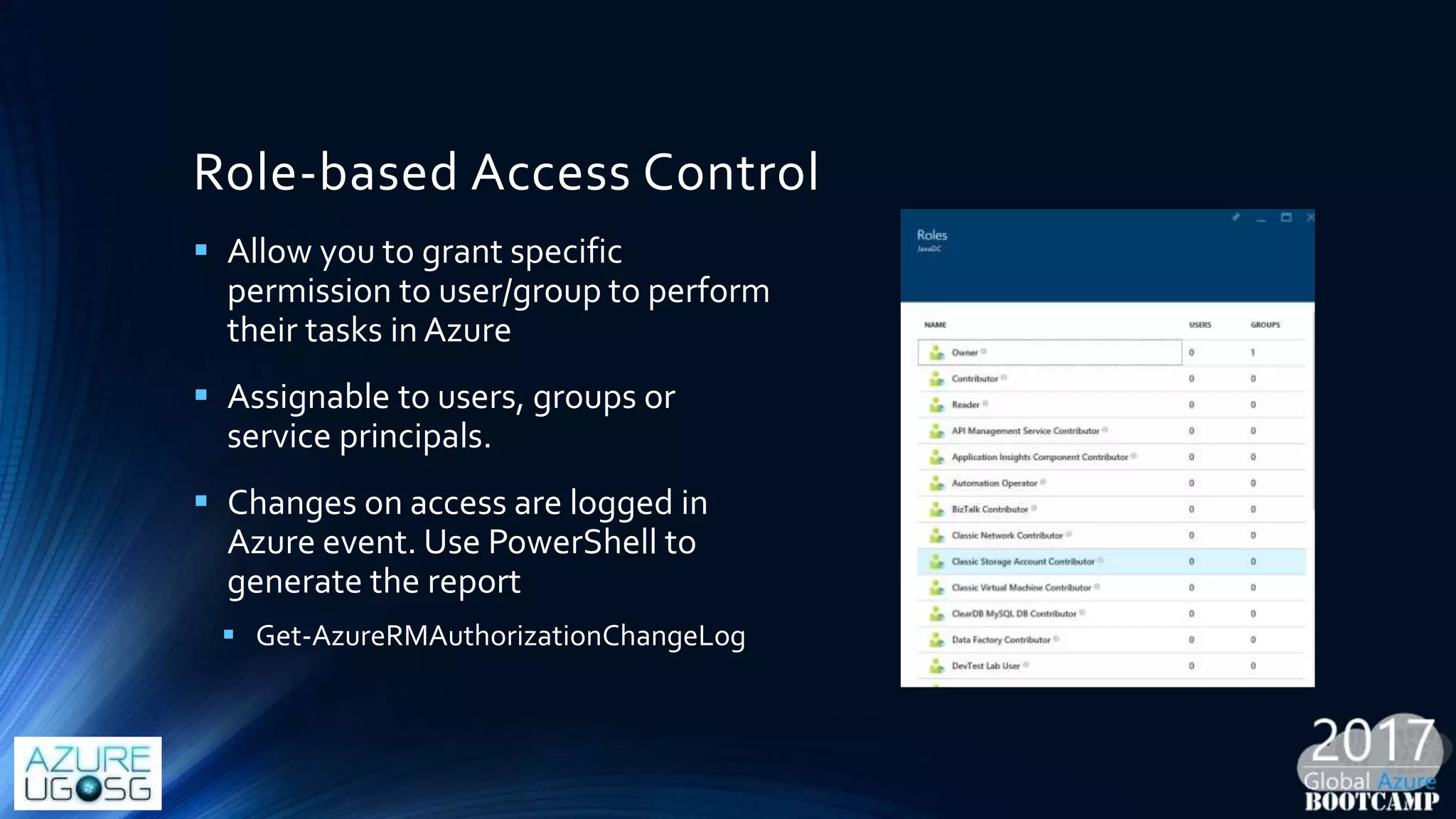
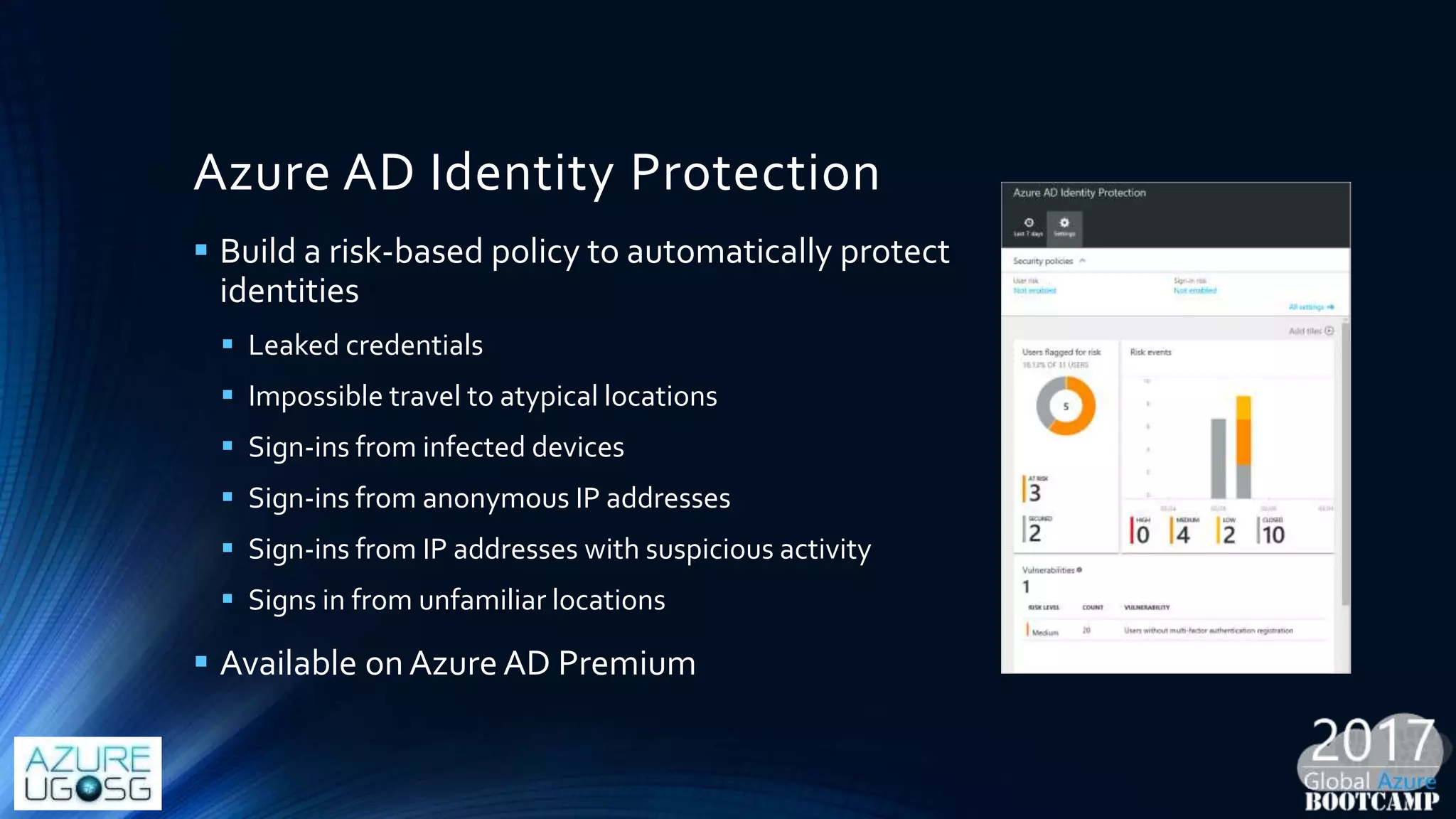
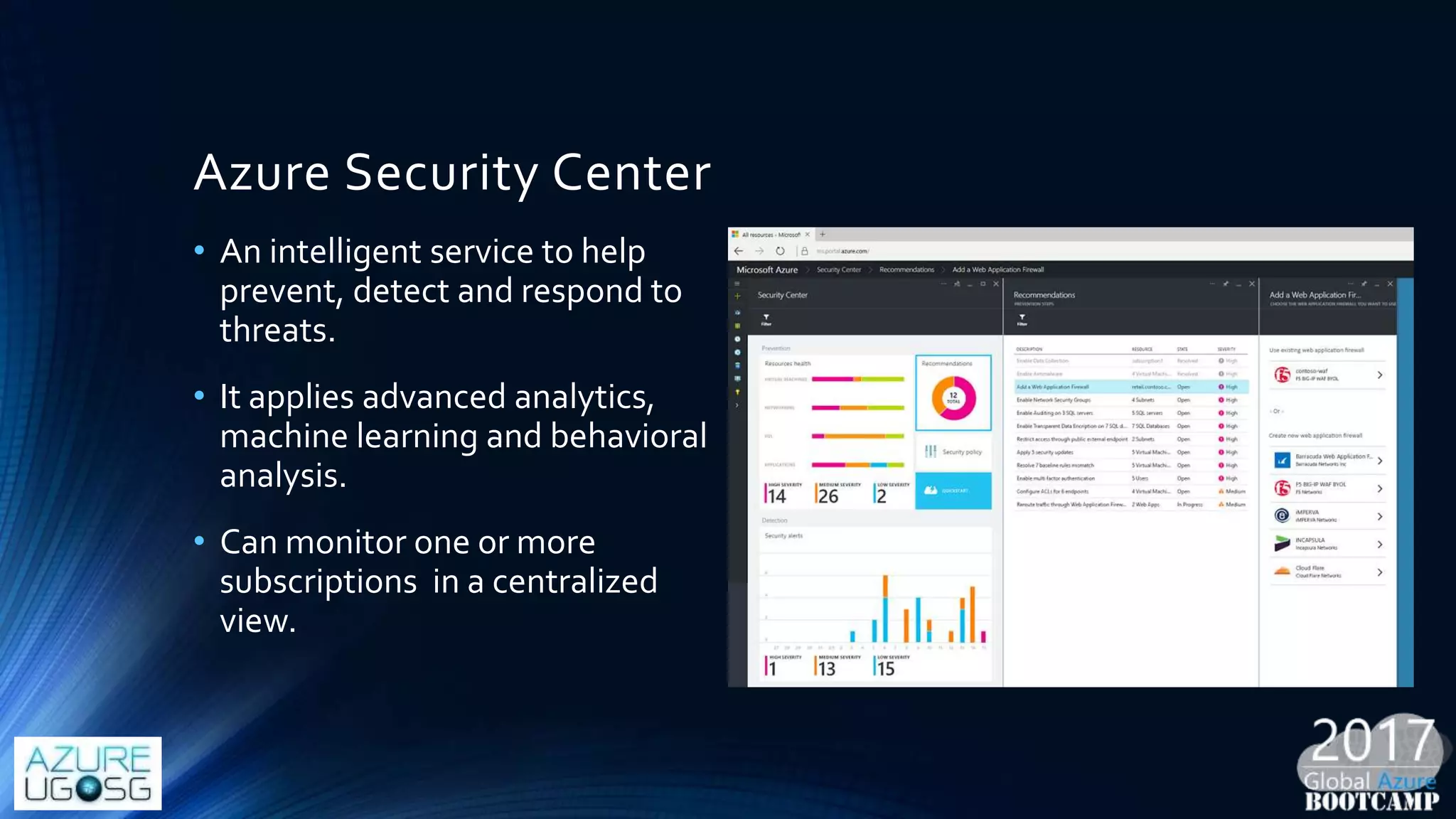
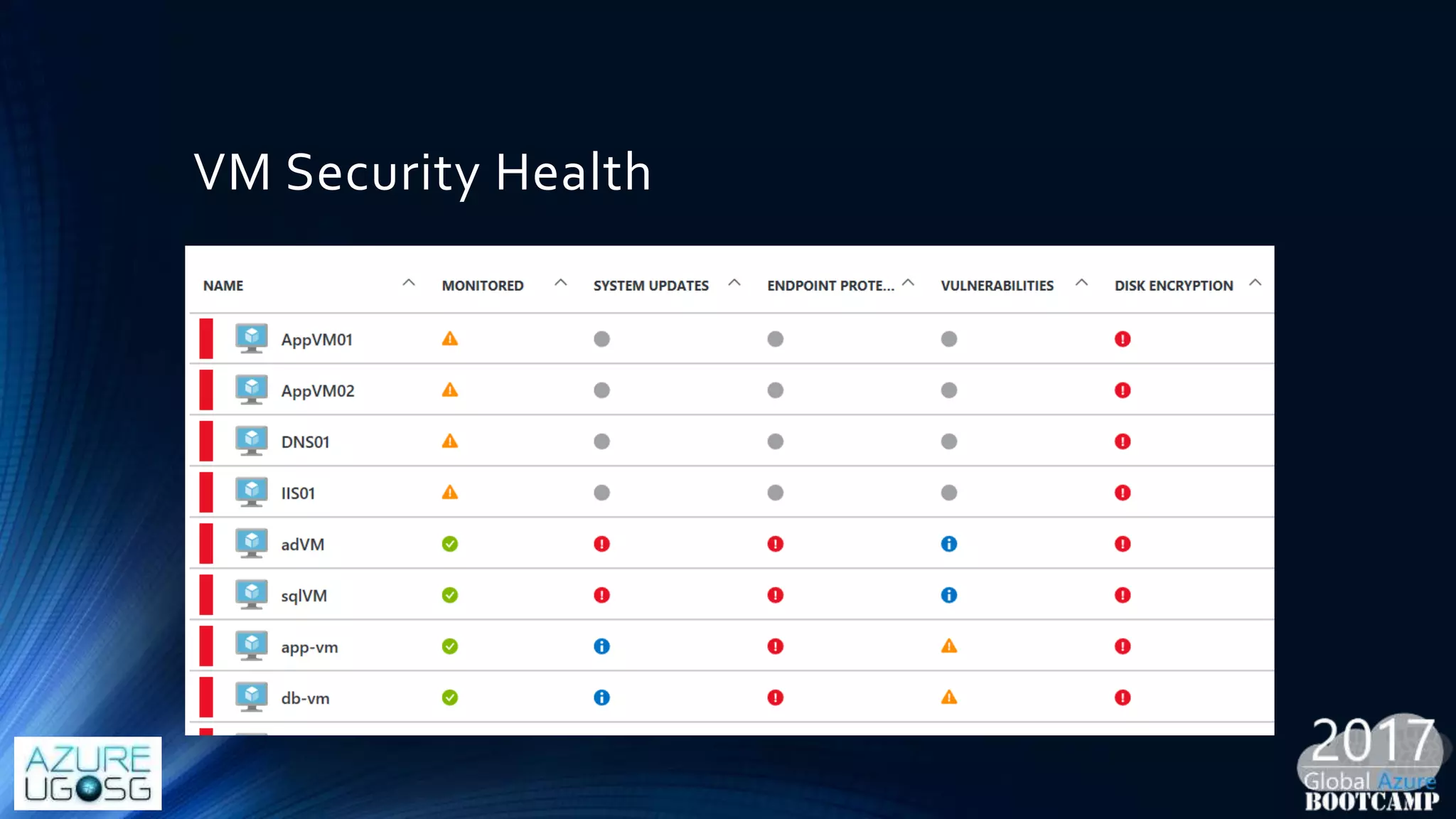
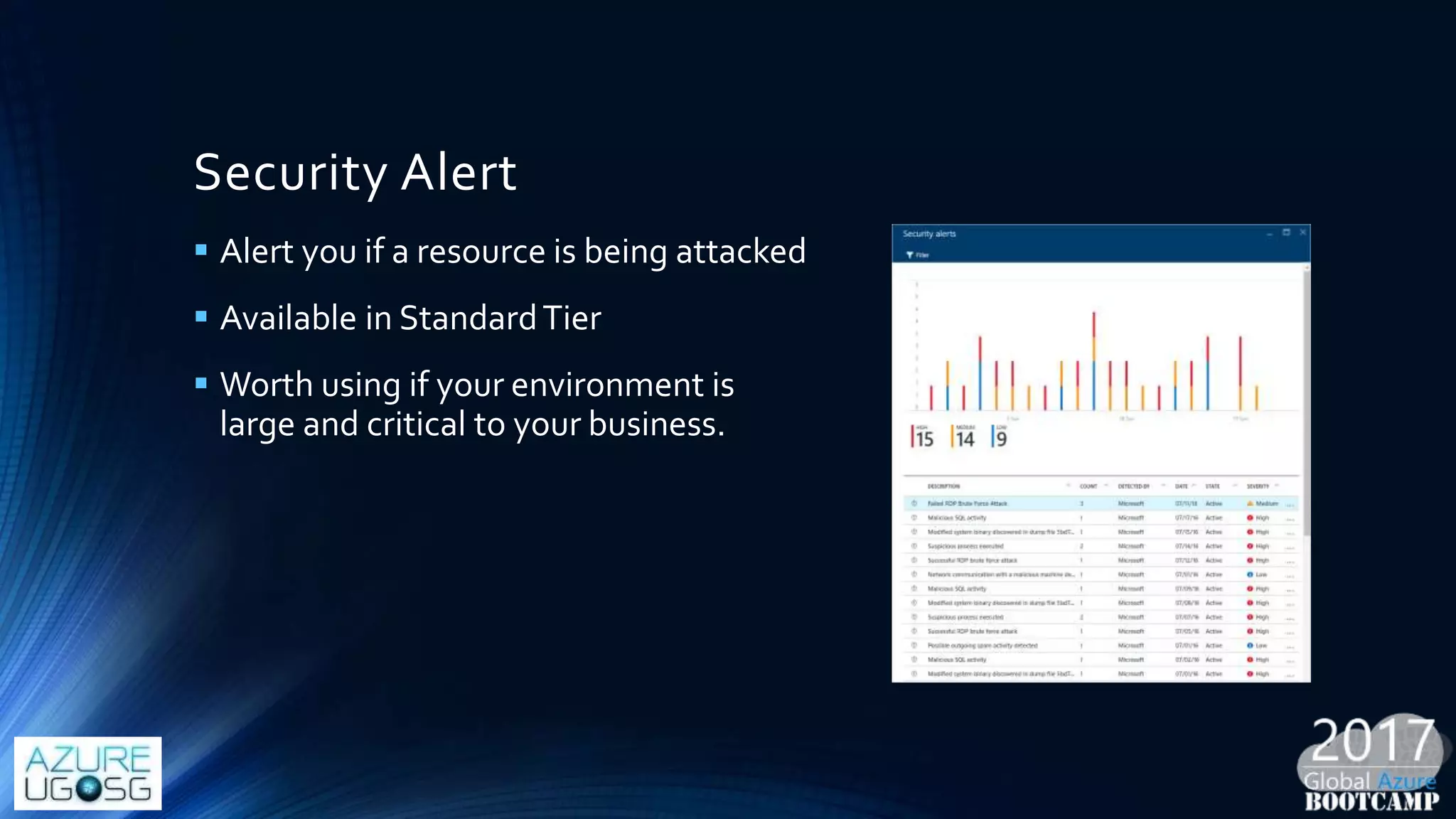
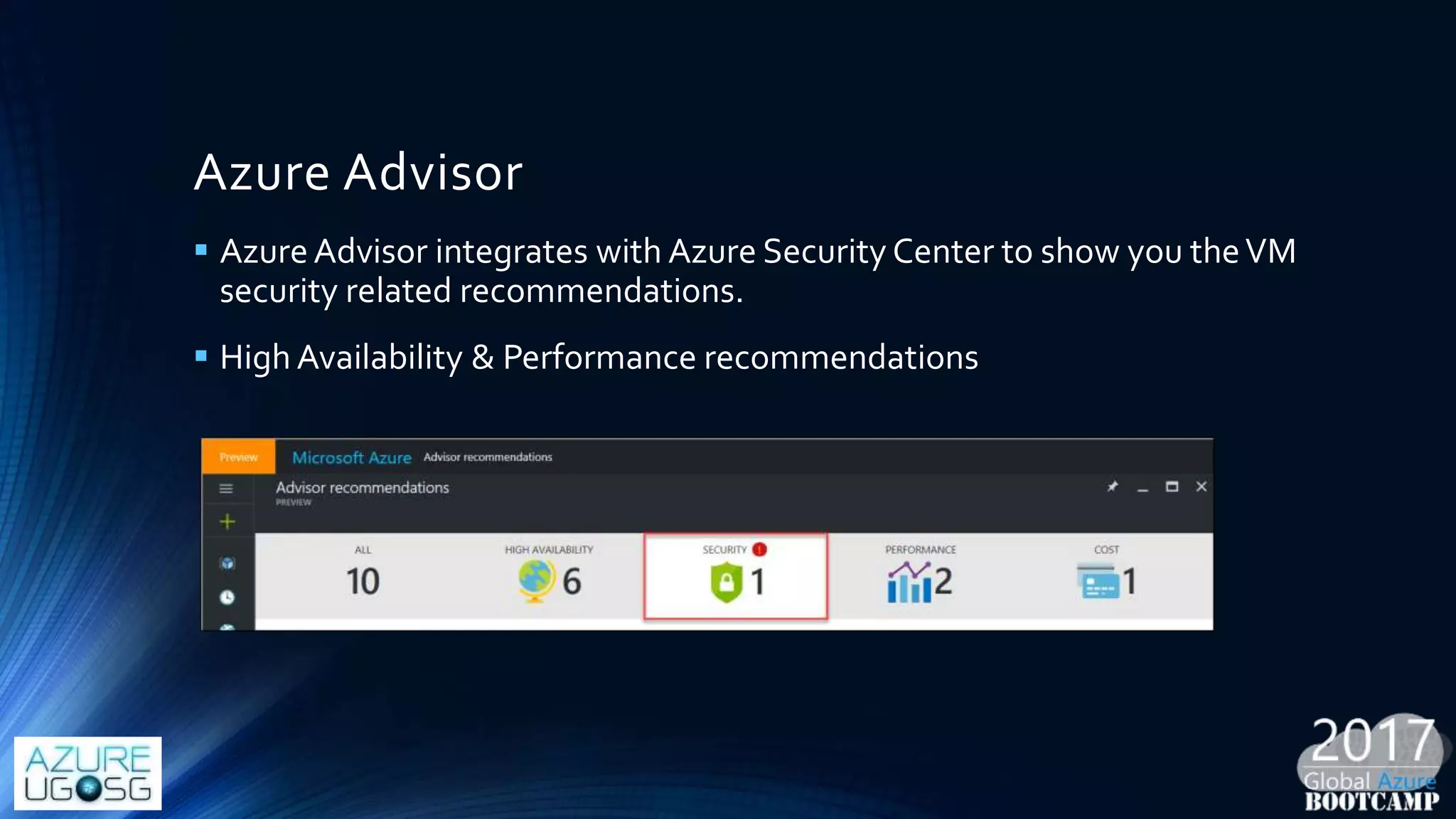
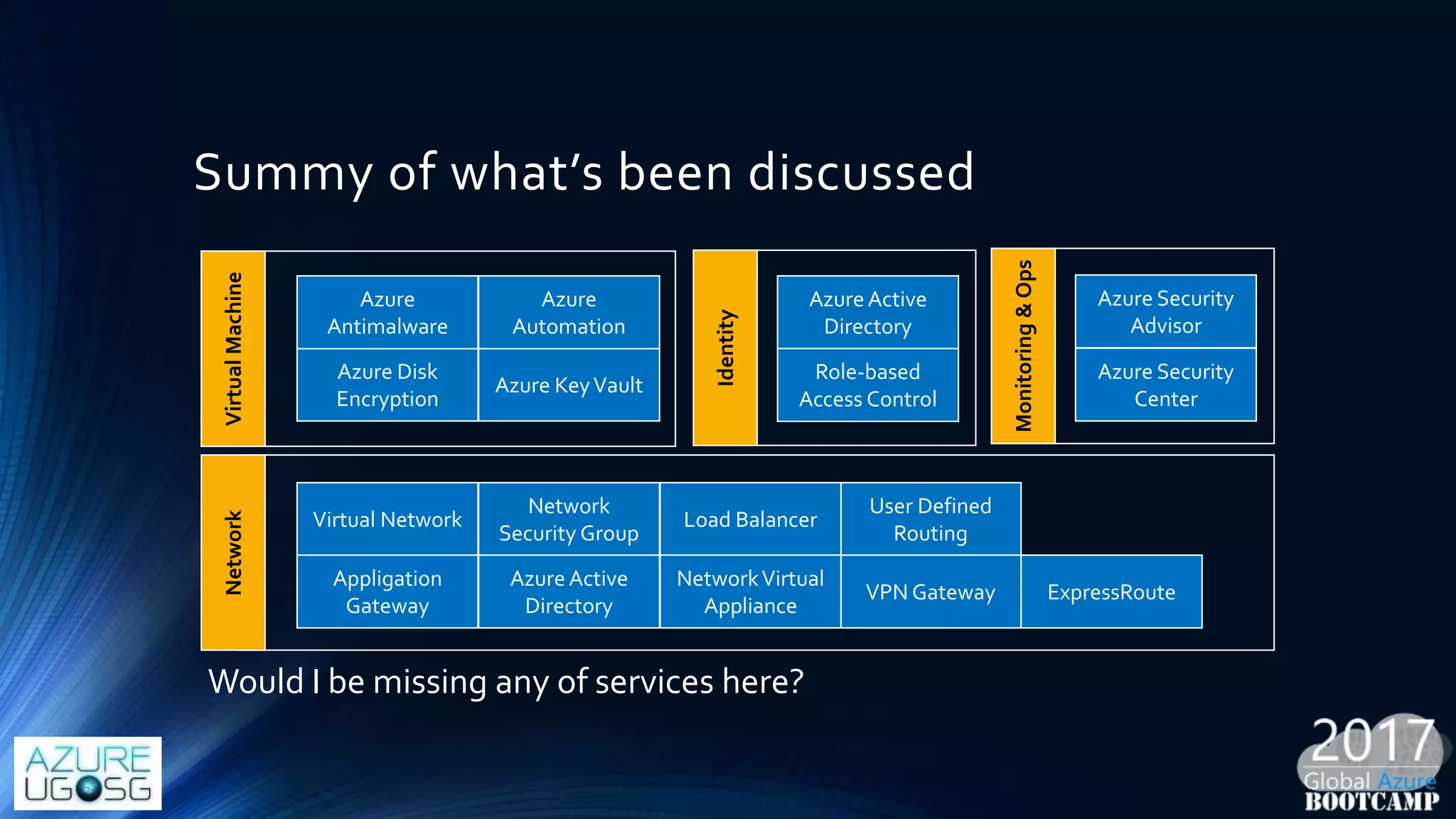
This document provides a comprehensive overview of designing secure Infrastructure as a Service (IaaS) on Microsoft Azure, with key lessons learned from experiences in government cloud. It discusses security principles, technical requirements, and best practices involving network security groups, demilitarized zones, and identity protection measures, emphasizing the importance of an integrated security framework. Additionally, it highlights the role of Azure security tools, compliance standards, and the necessity of proactive management to safeguard cloud resources.