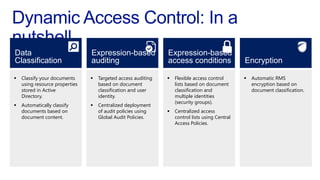
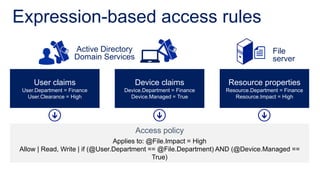
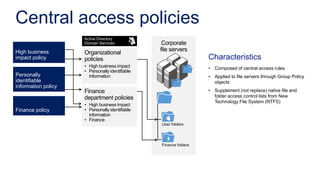
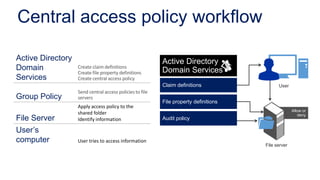
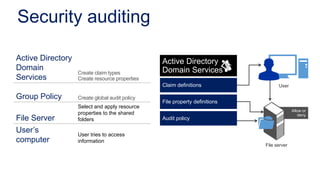
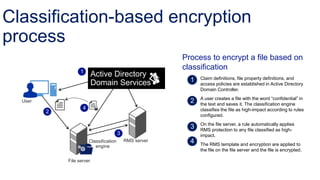
The document discusses data access control and compliance. It introduces dynamic access control capabilities in Windows Server 2012 that can authorize only authorized individuals to access confidential data. It discusses challenges around data compliance, regulatory standards, and granular control over auditing access. The document then demonstrates how to use features like data classification, expression-based auditing and access conditions, and encryption to address these challenges. It provides examples of using these features to audit specific types of access, control access based on multiple attributes, and automatically encrypt files based on classification. Finally, it describes a demonstration lab that shows how to set up claims, resource properties, central access policies and encryption in Active Directory and a file server.