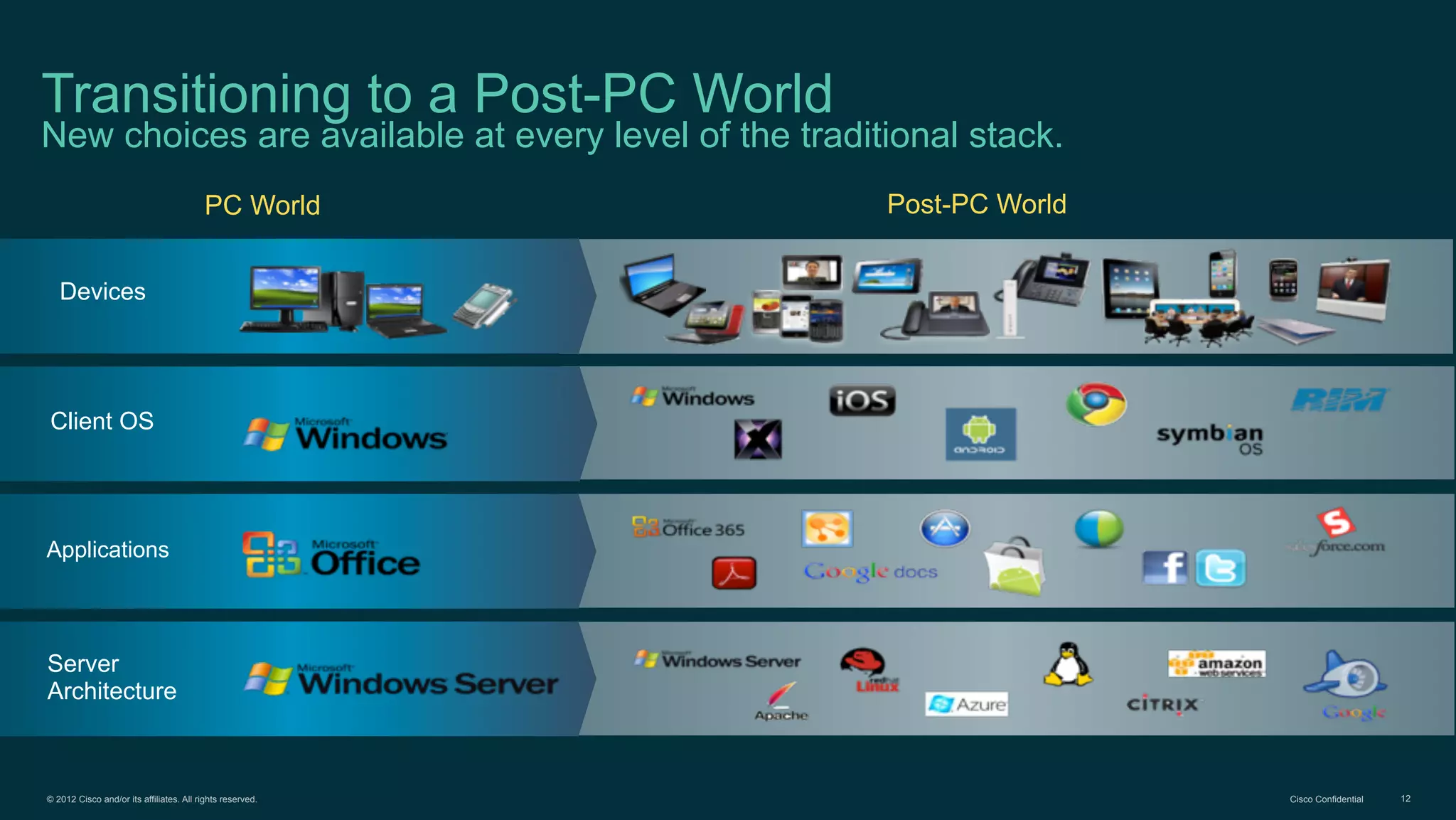
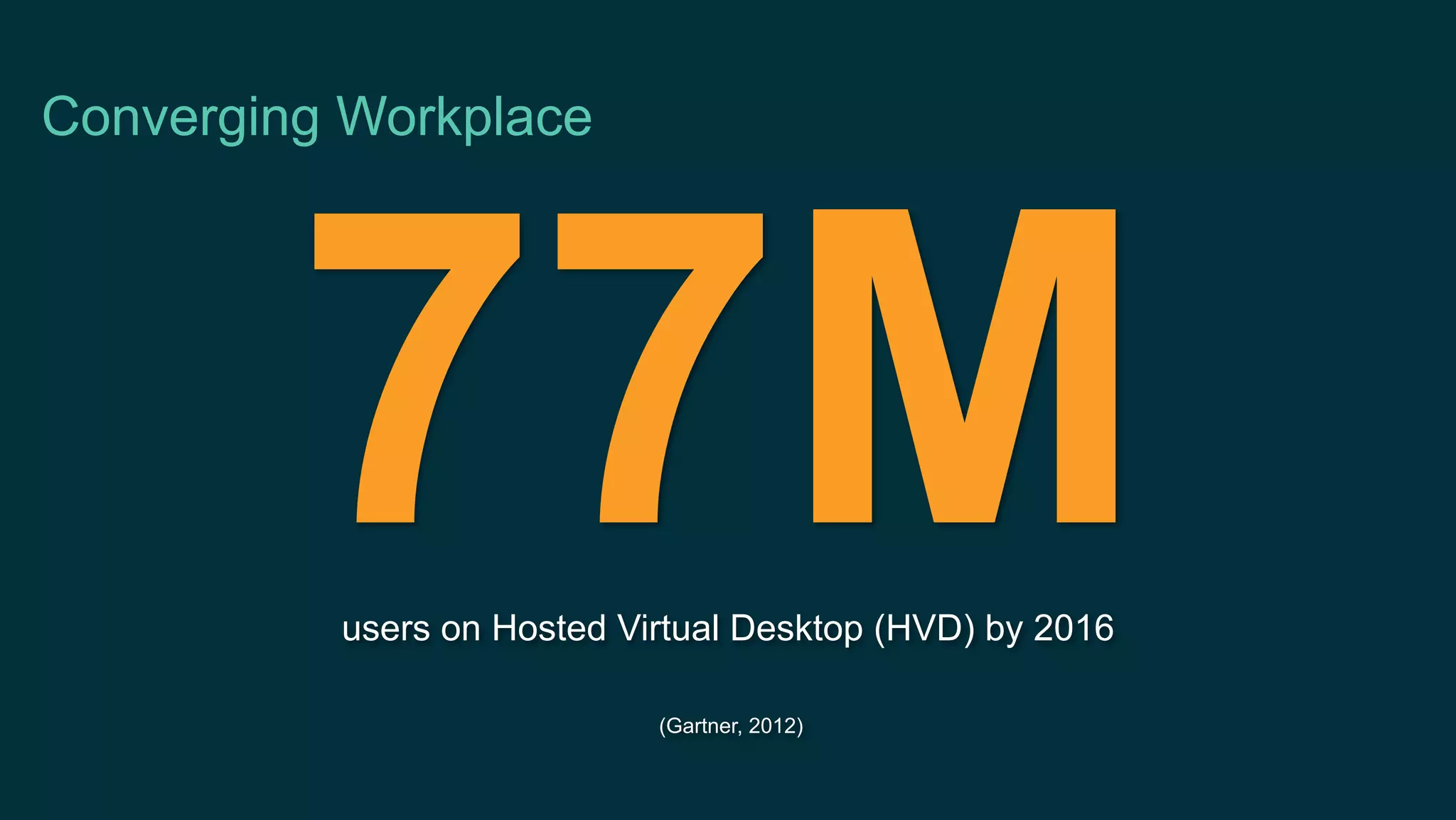
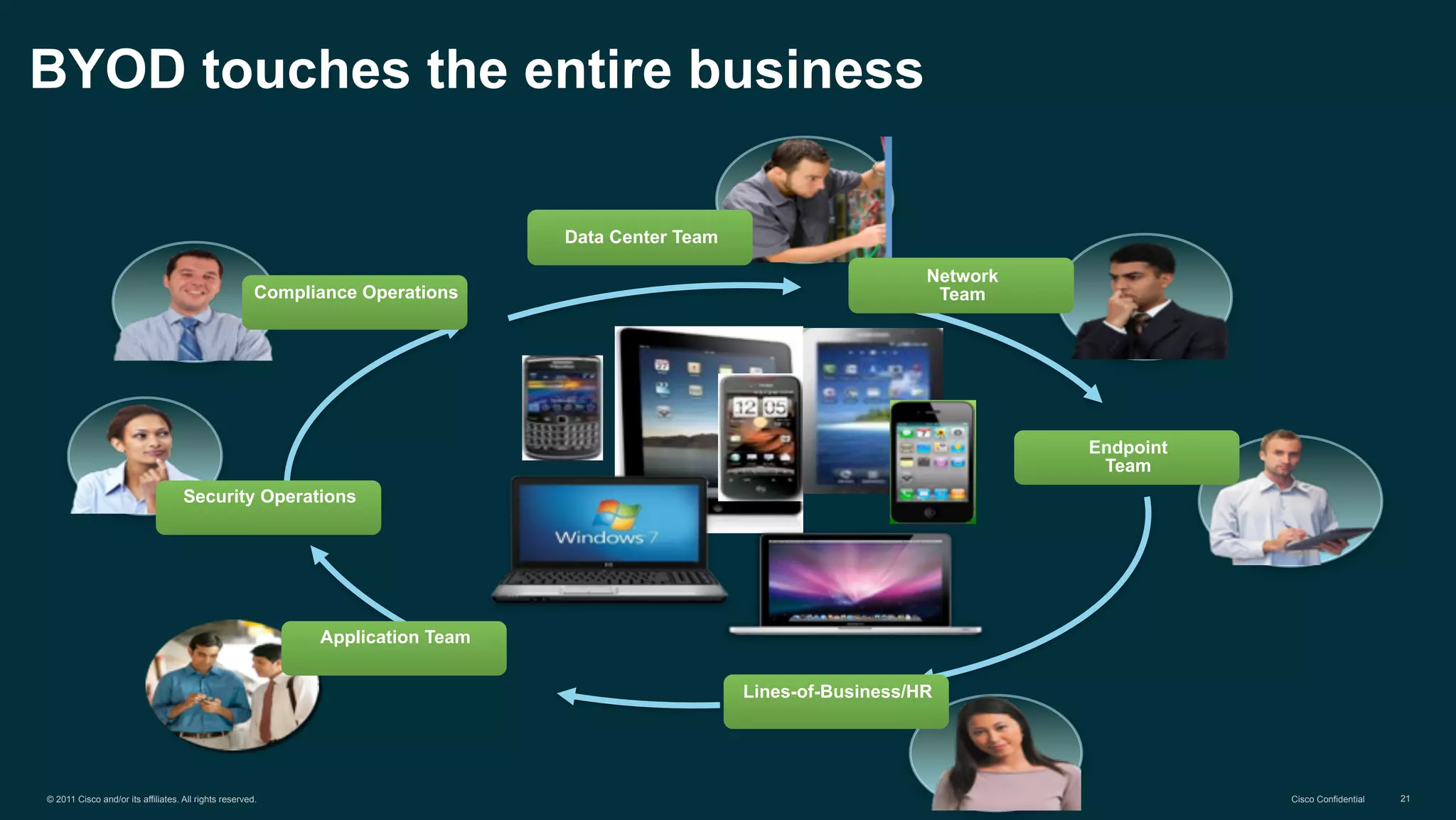
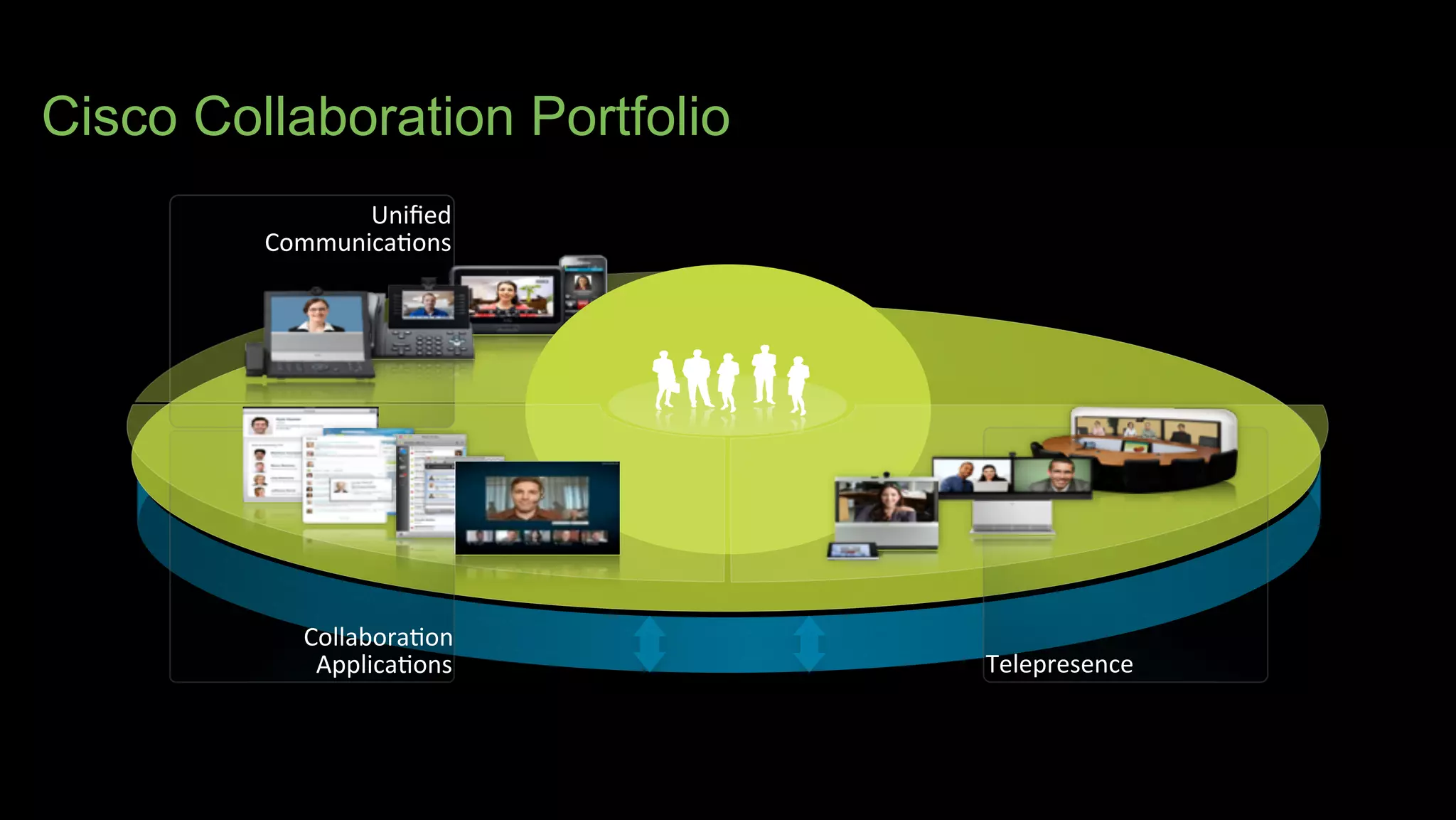
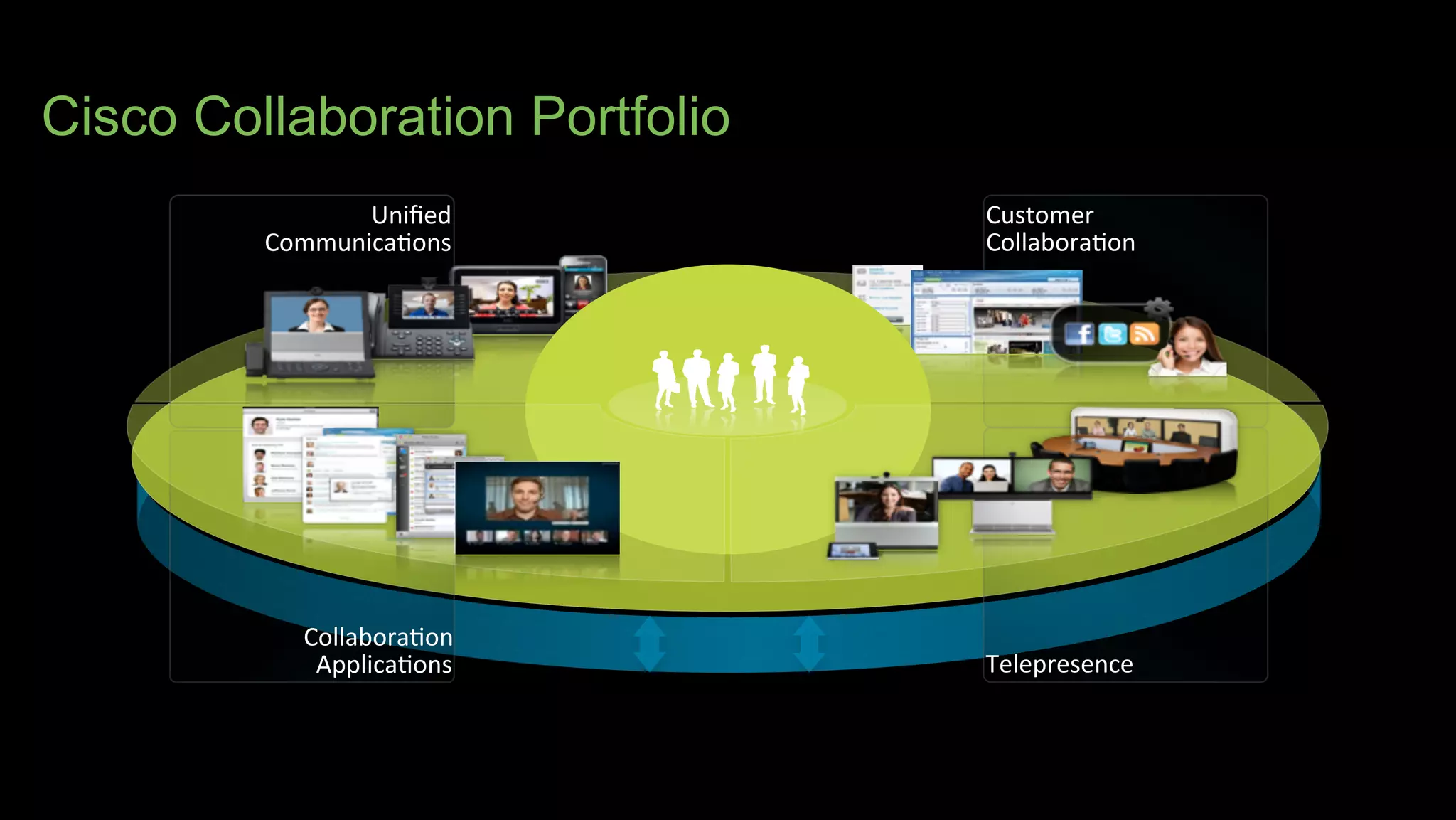
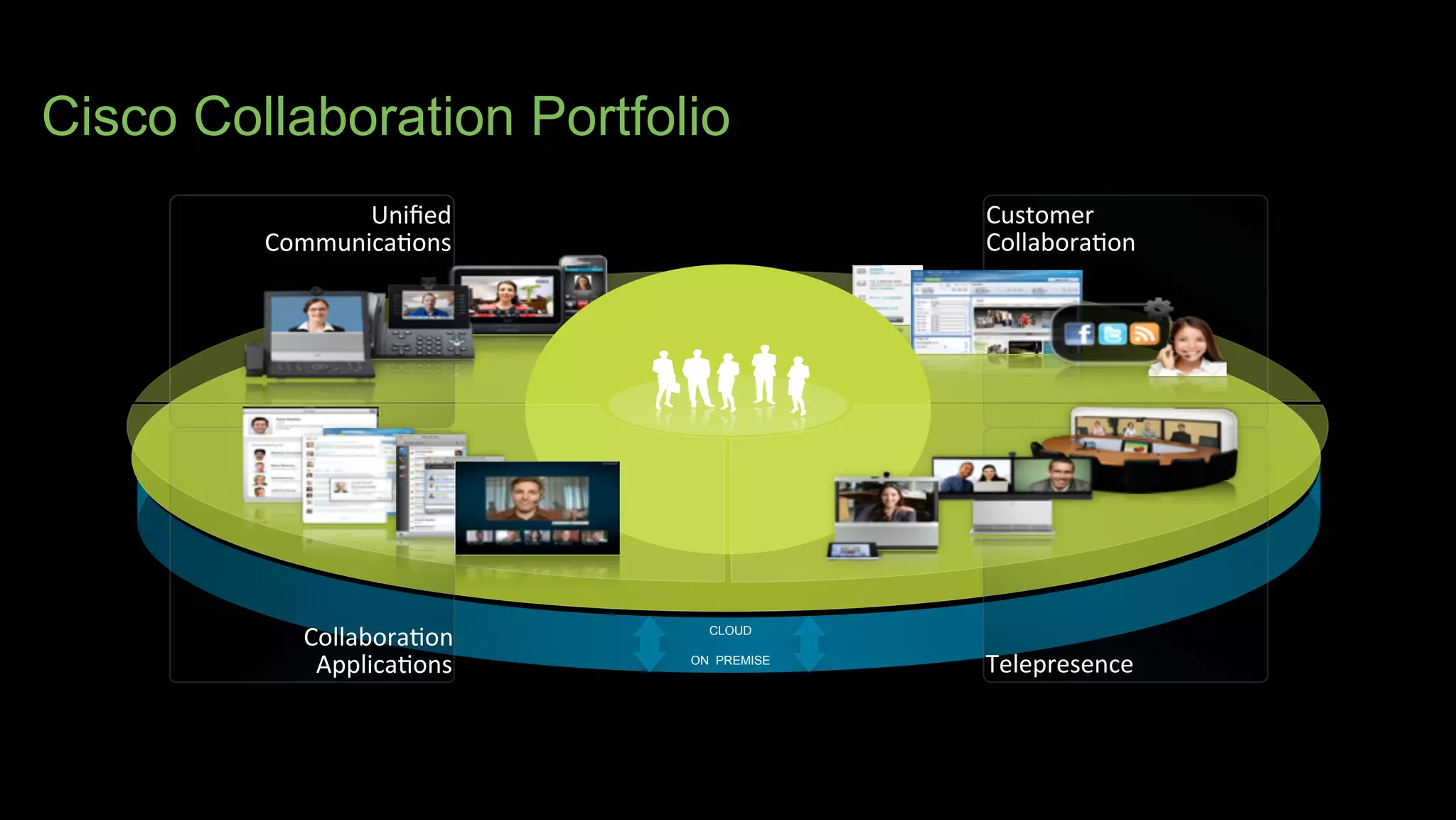
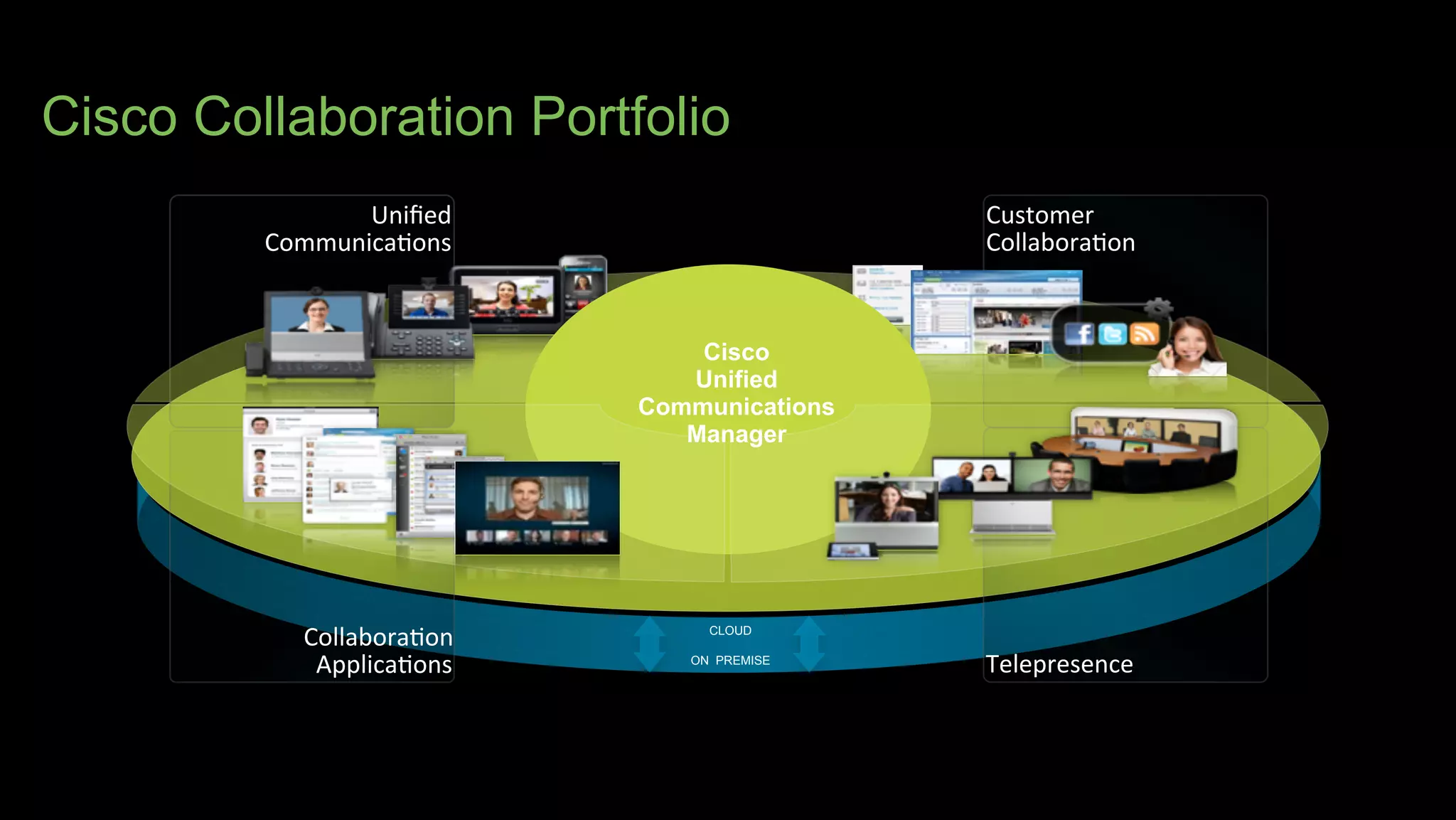
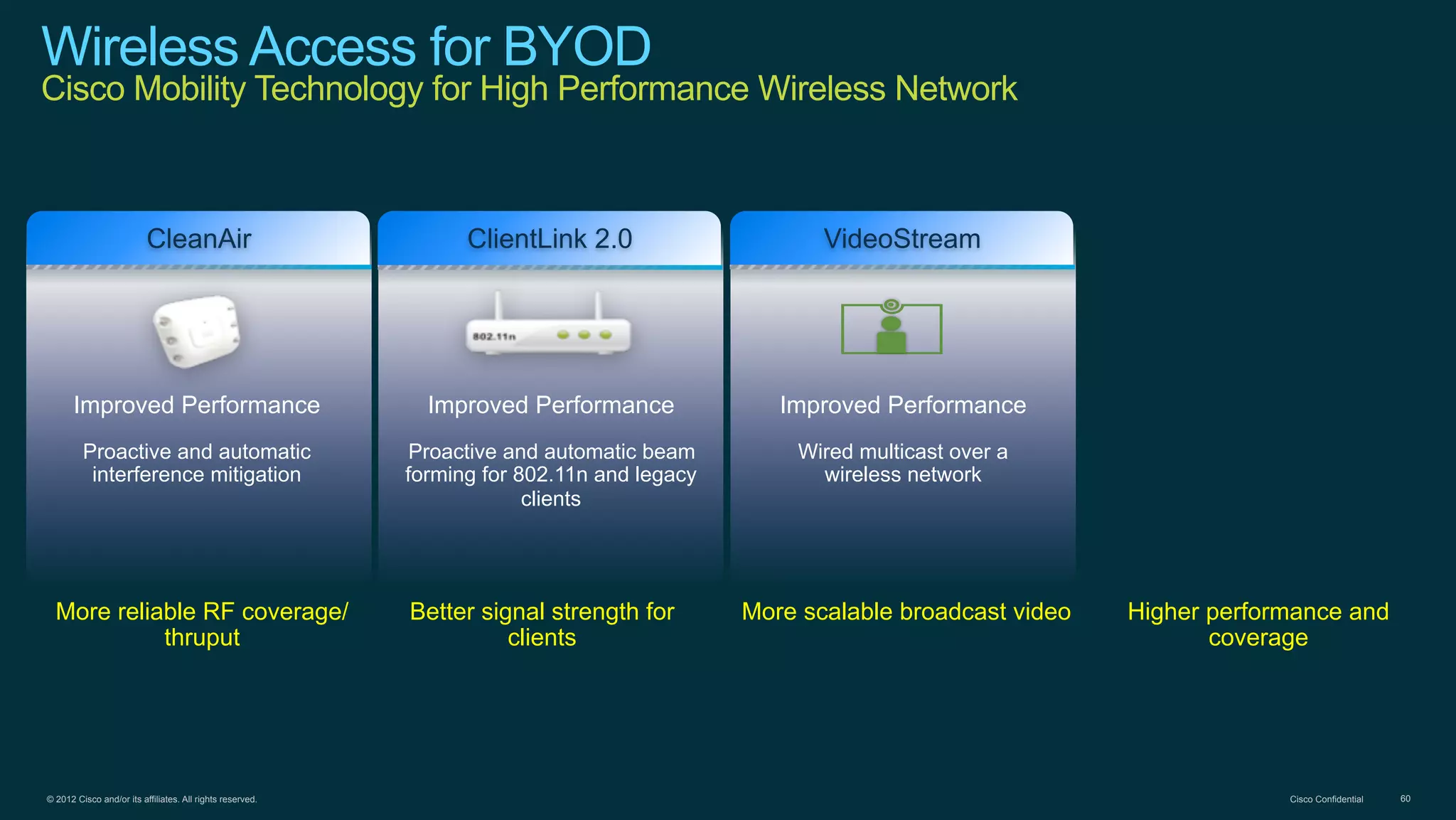
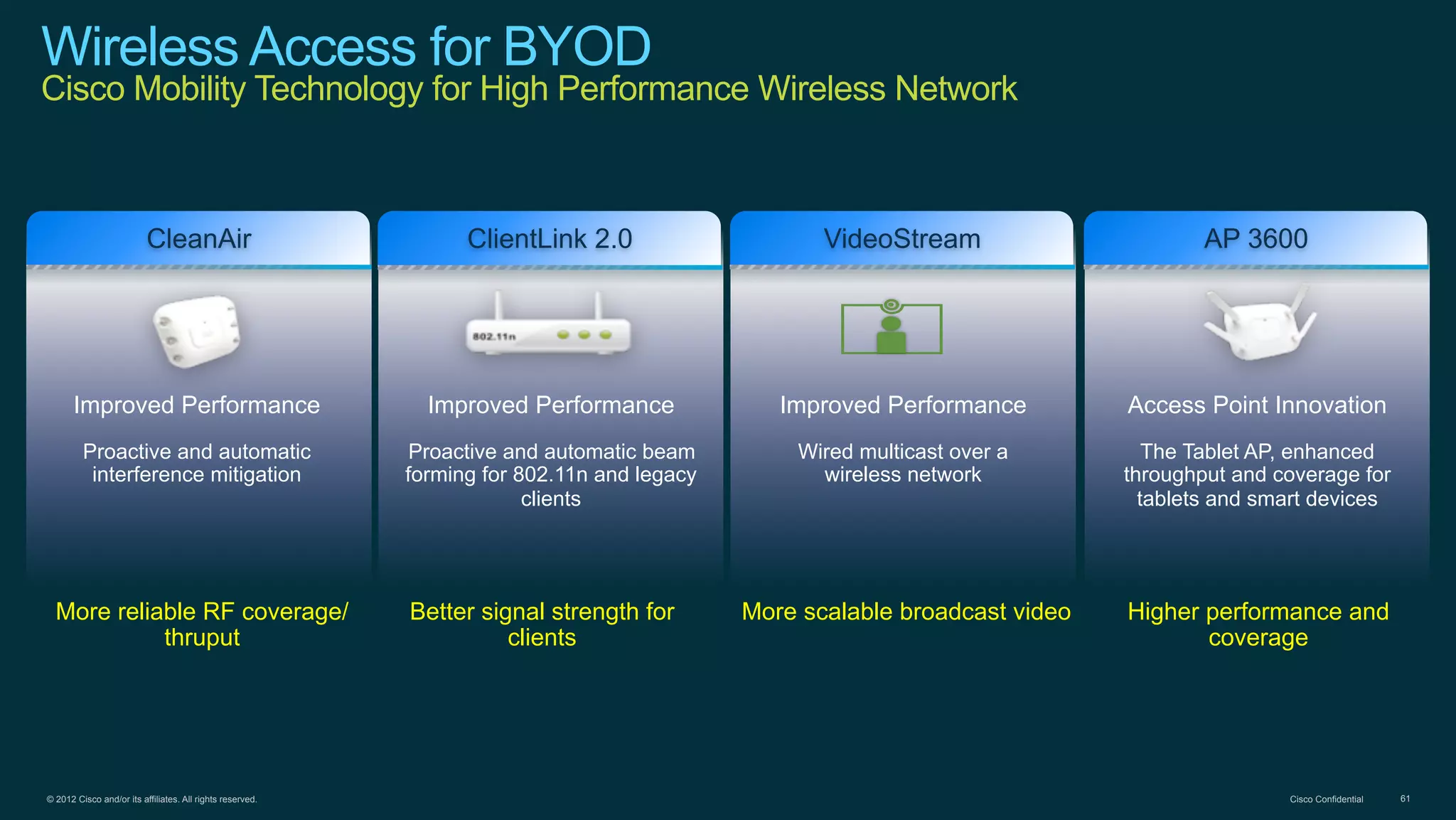
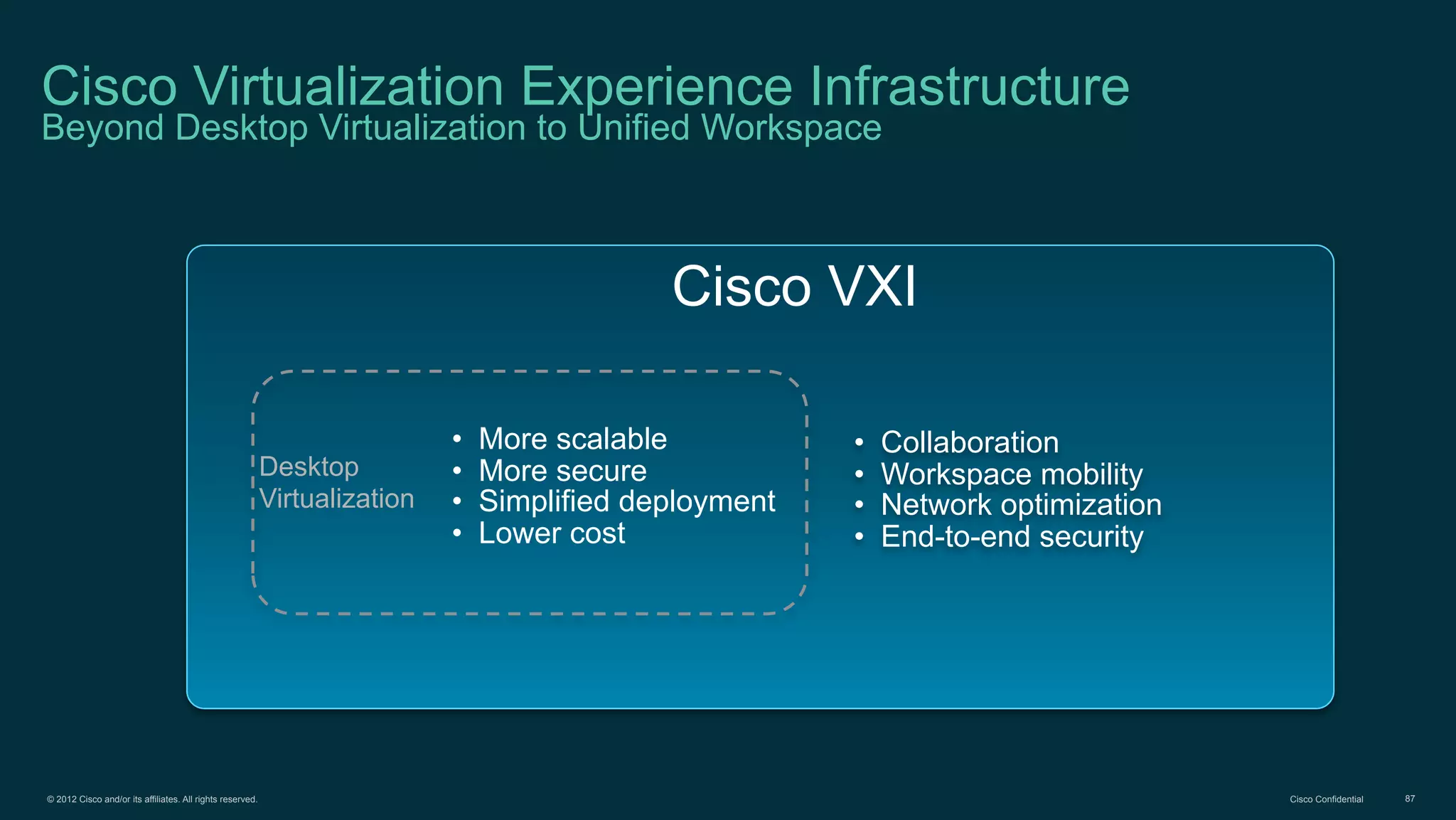
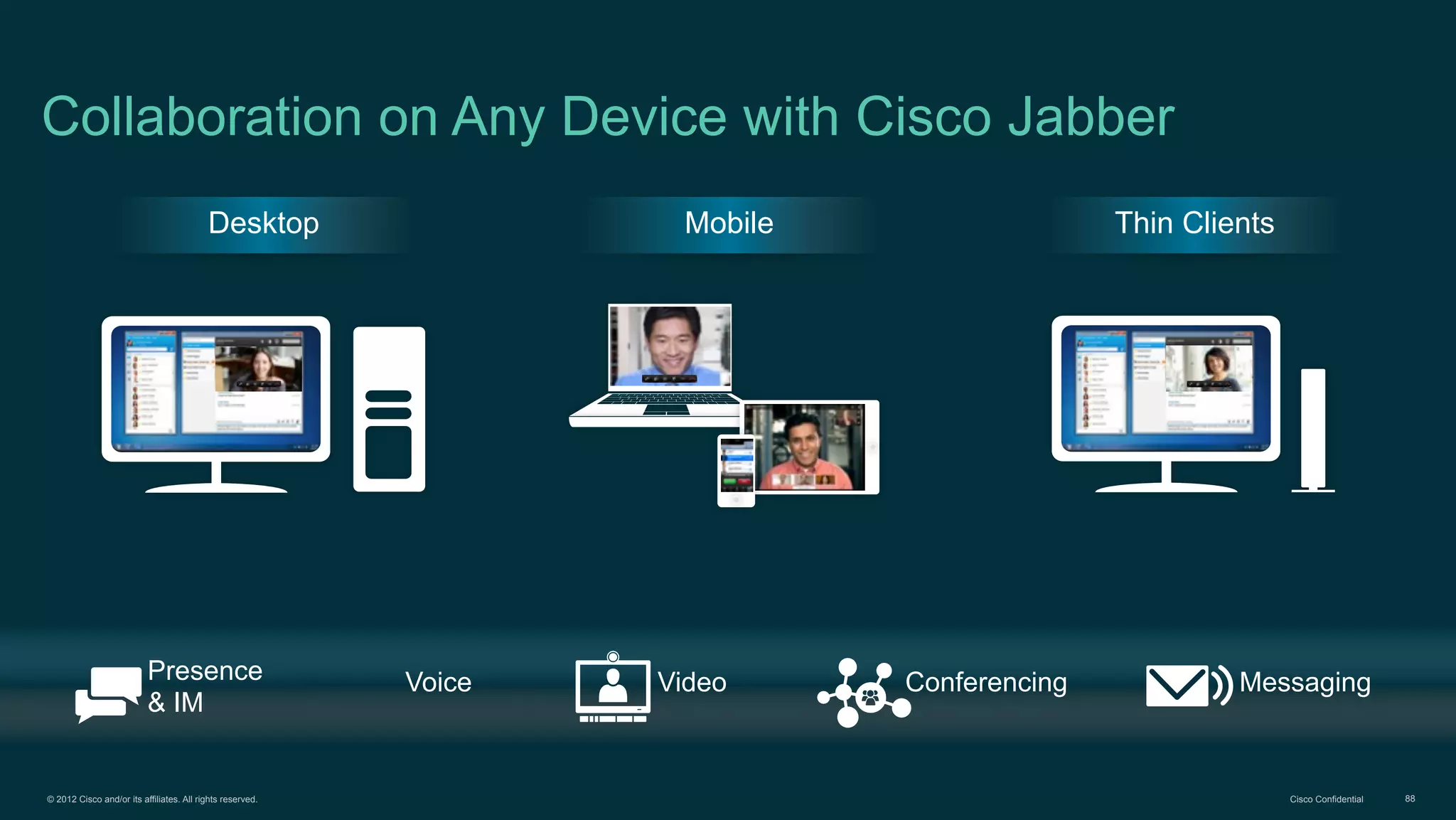
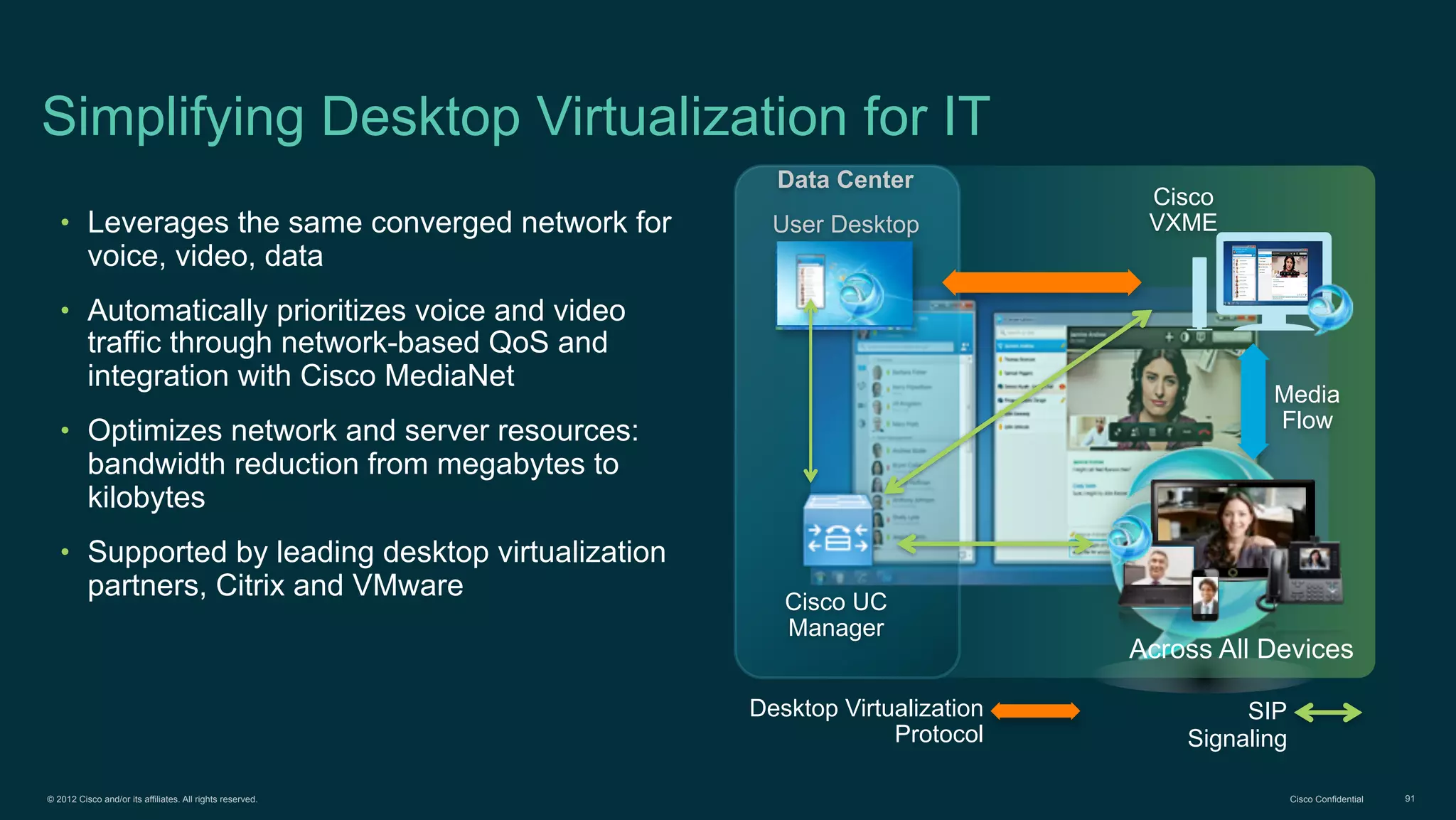
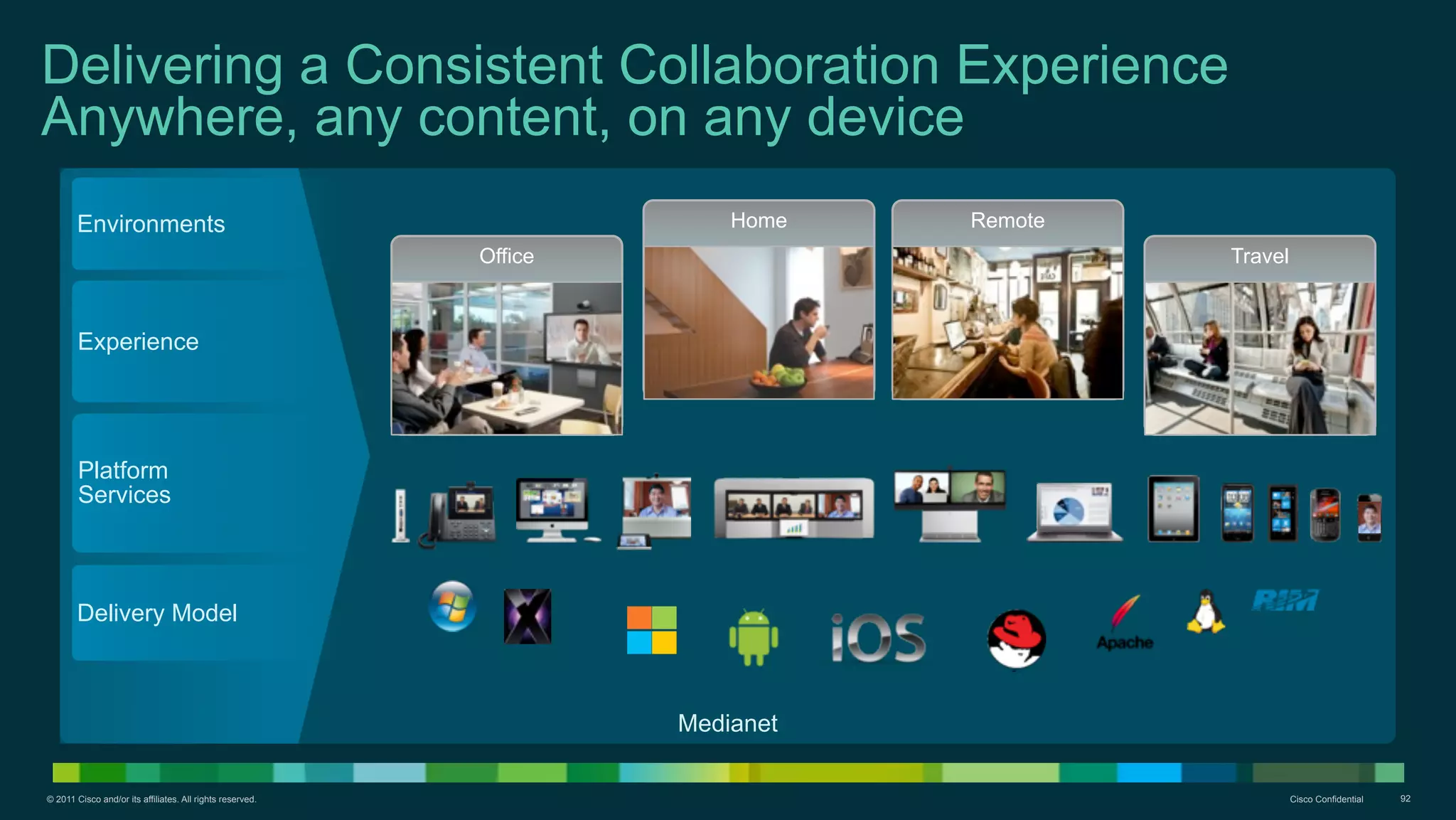
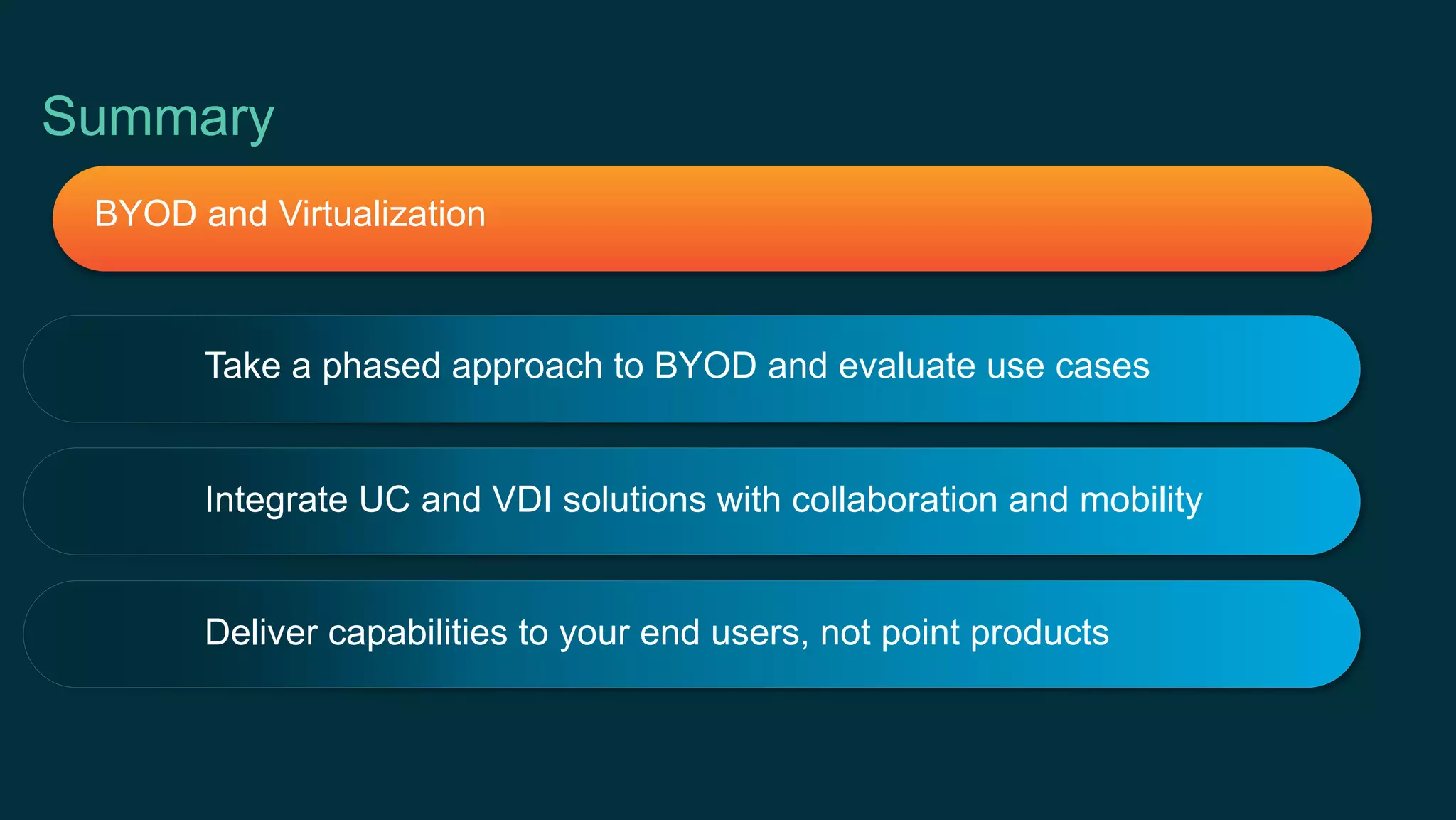
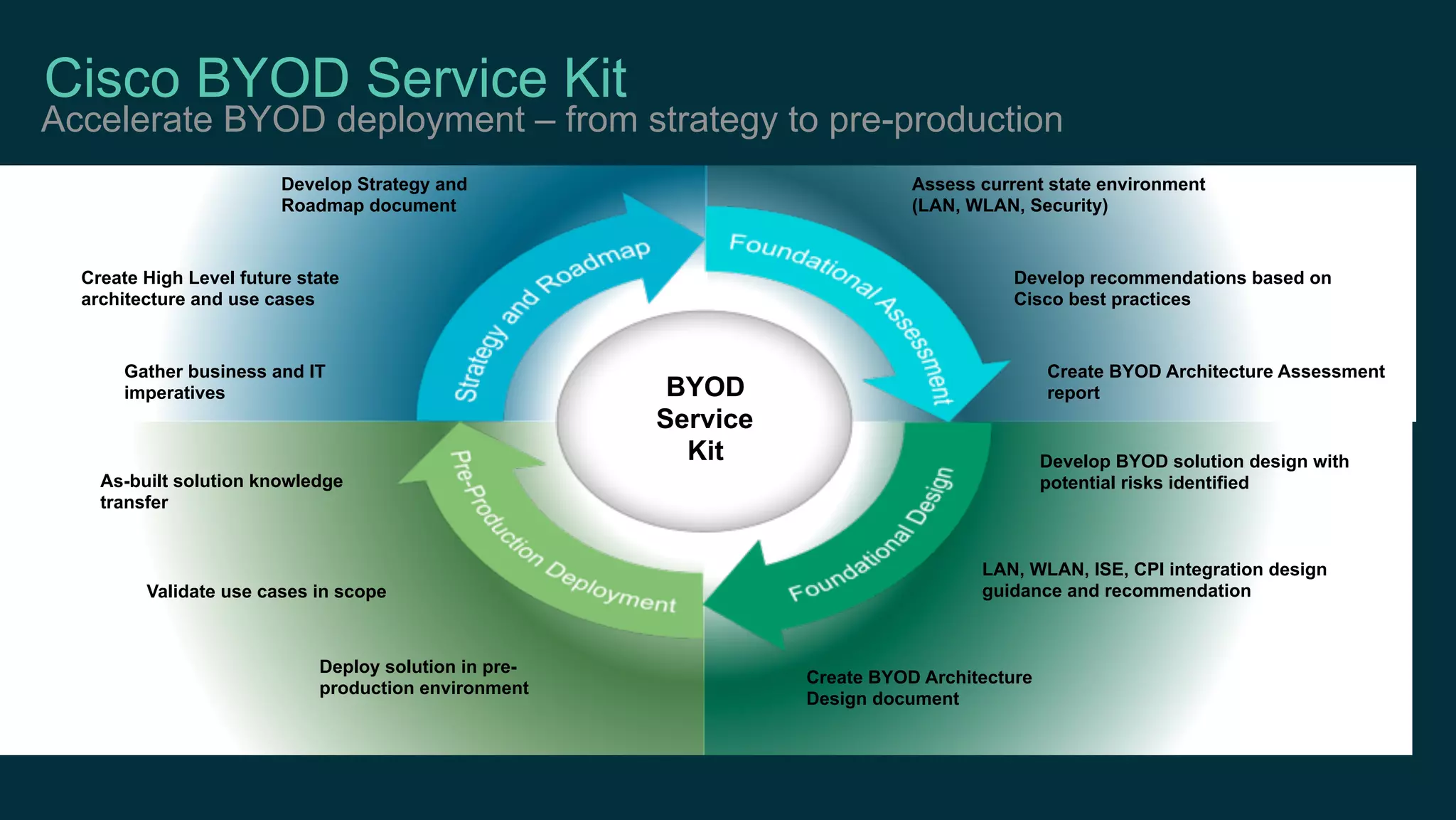
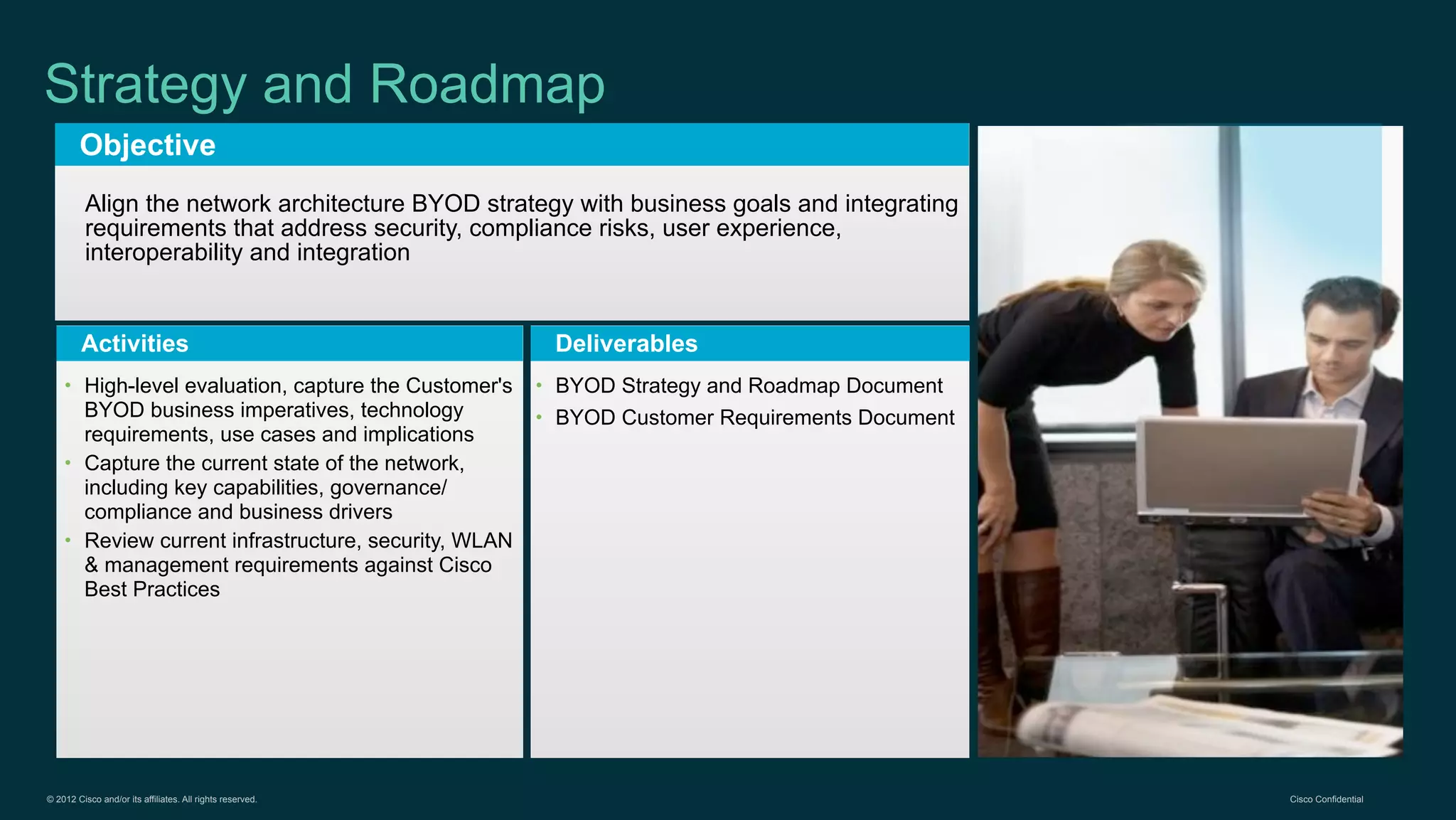
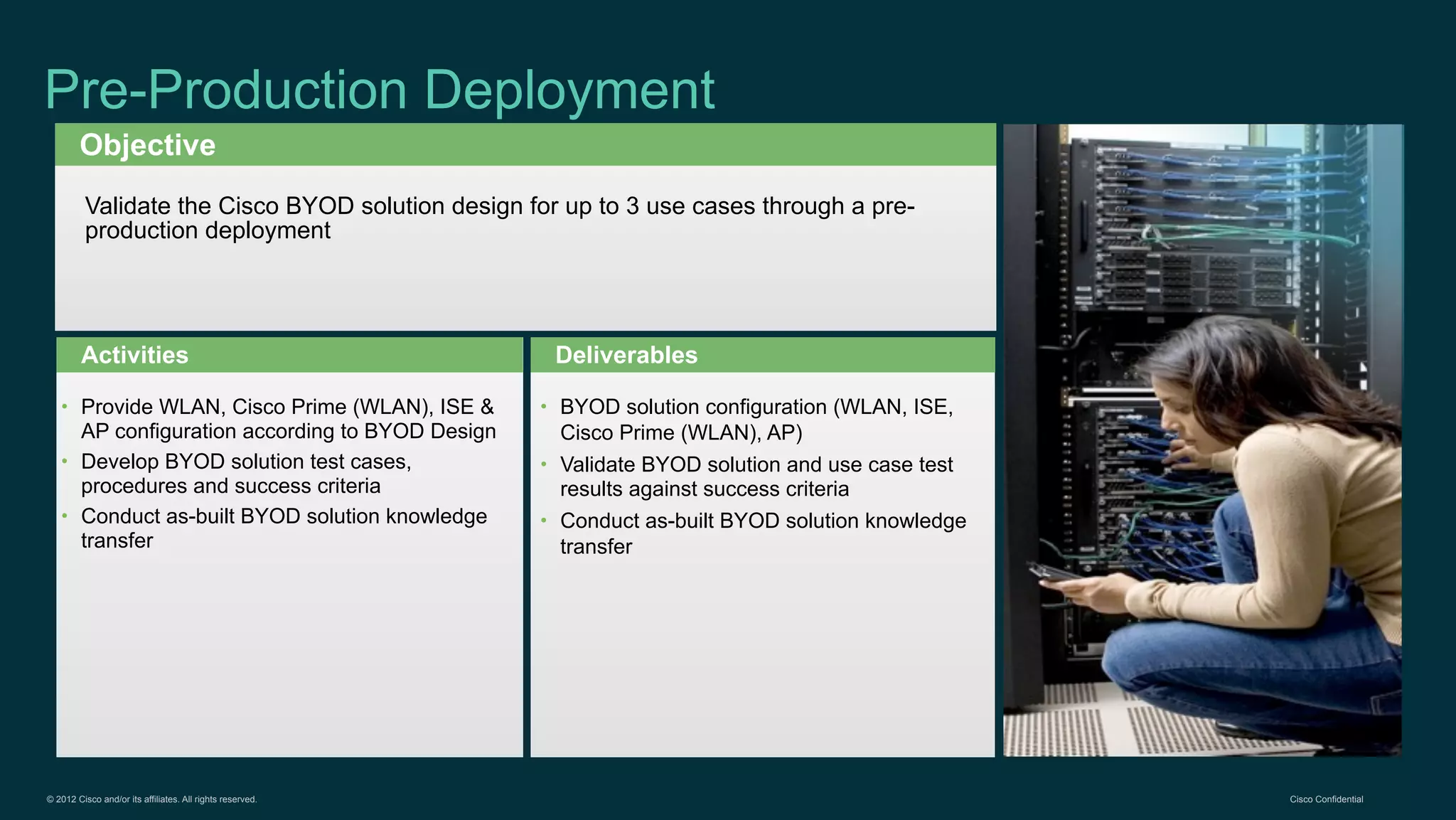
The document discusses Bring Your Own Device (BYOD) and virtual desktop infrastructure (VDI). It provides an overview of Cisco's approach to enabling BYOD and VDI, including:
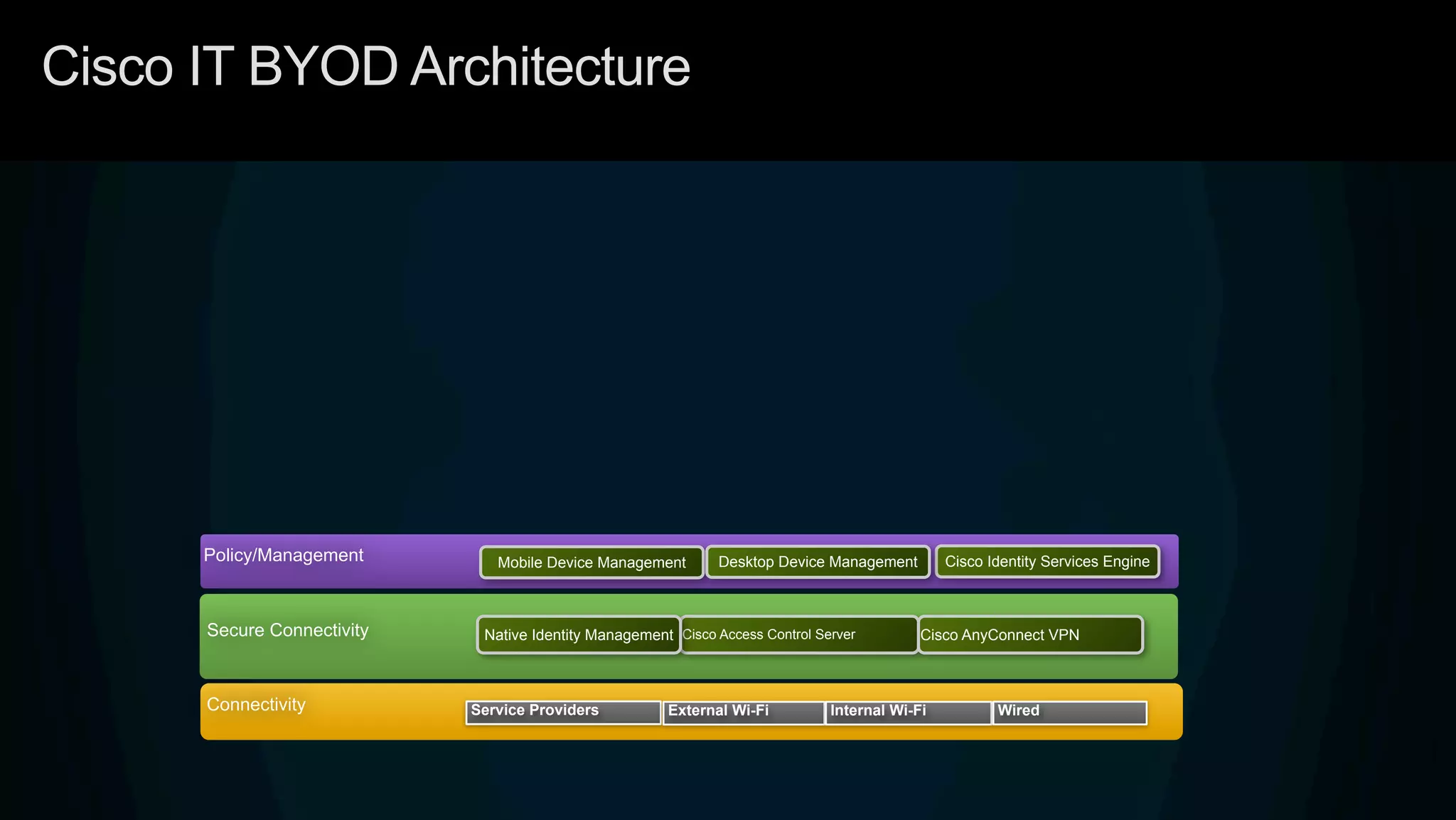
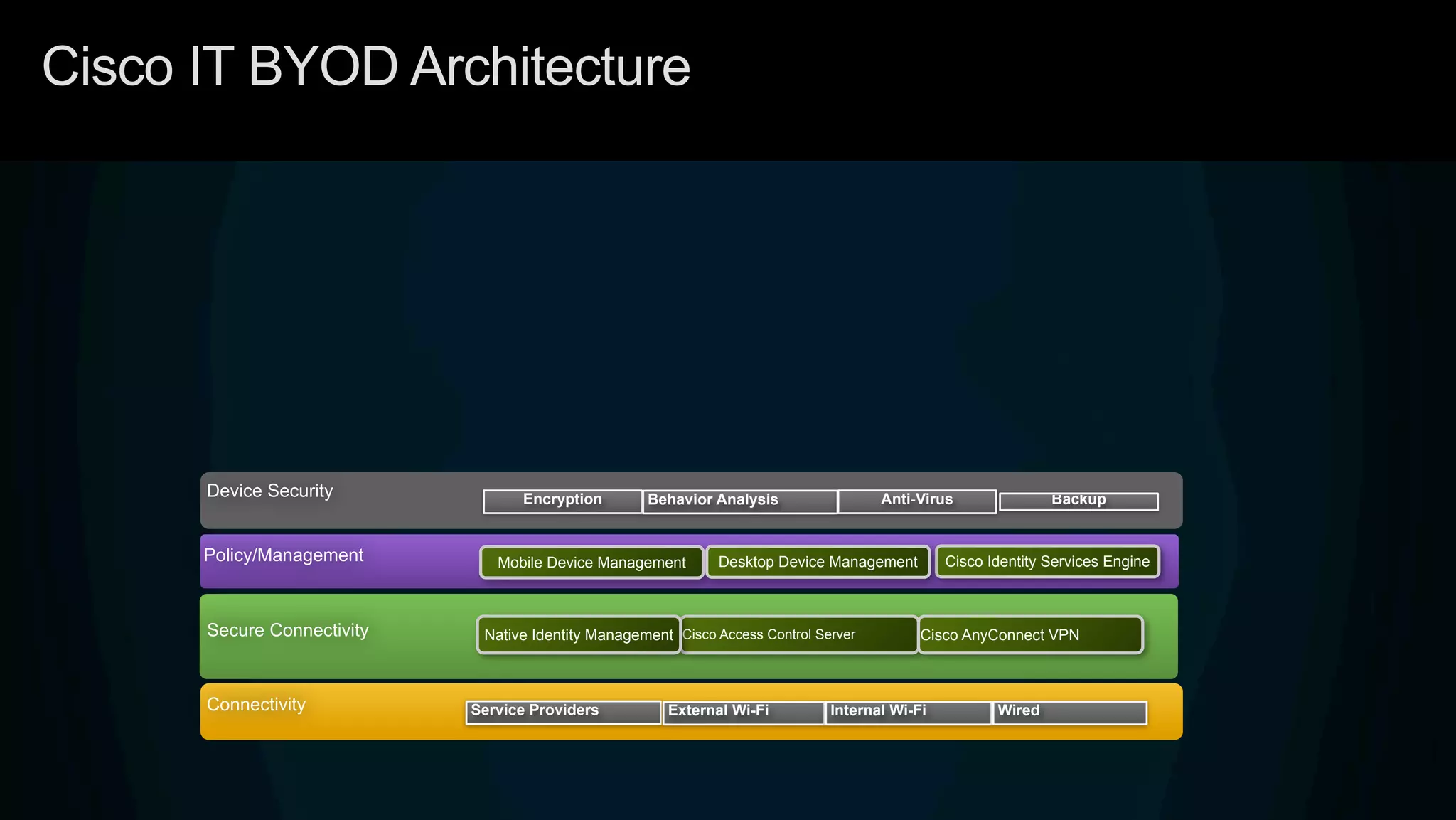
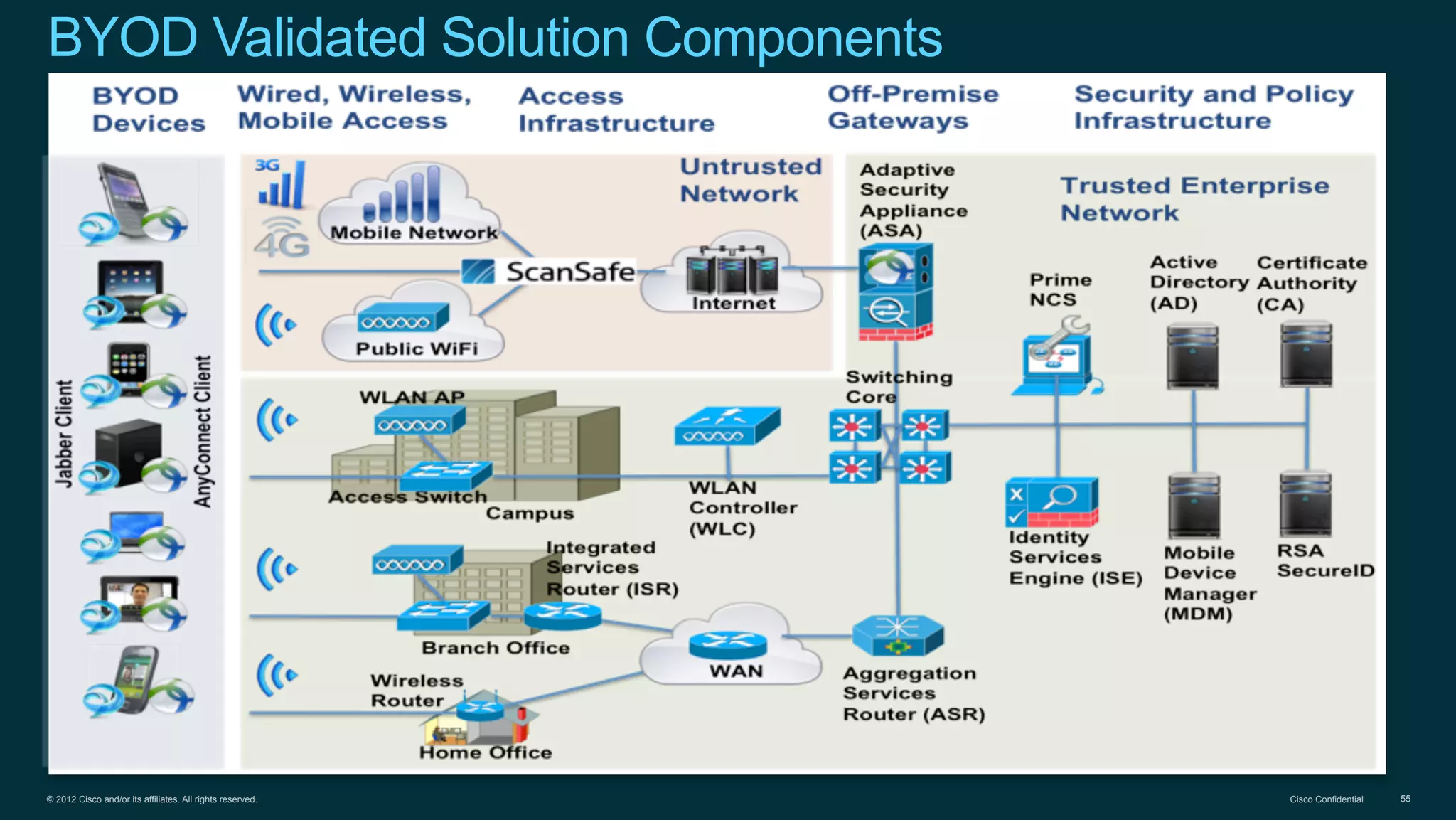
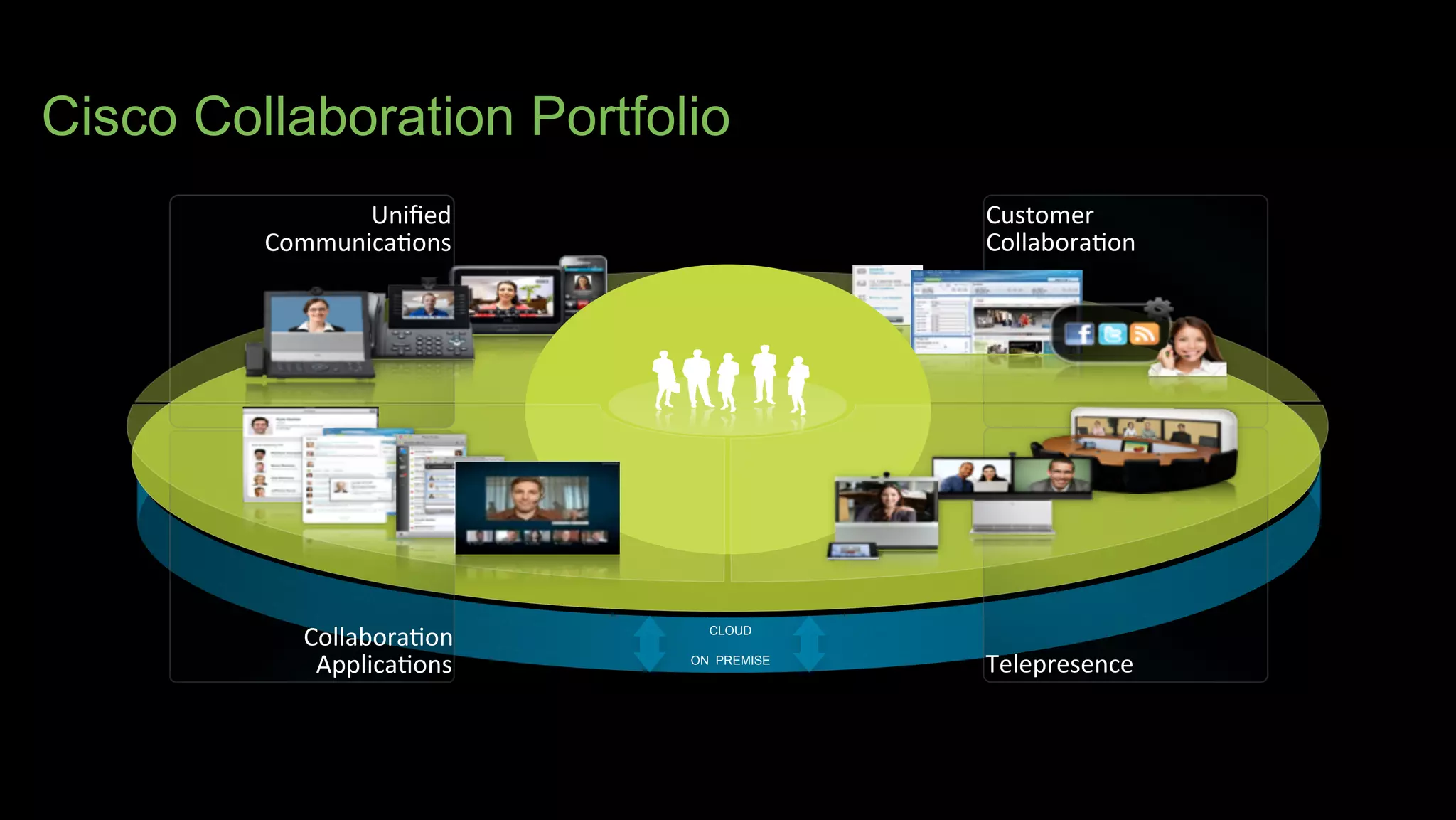
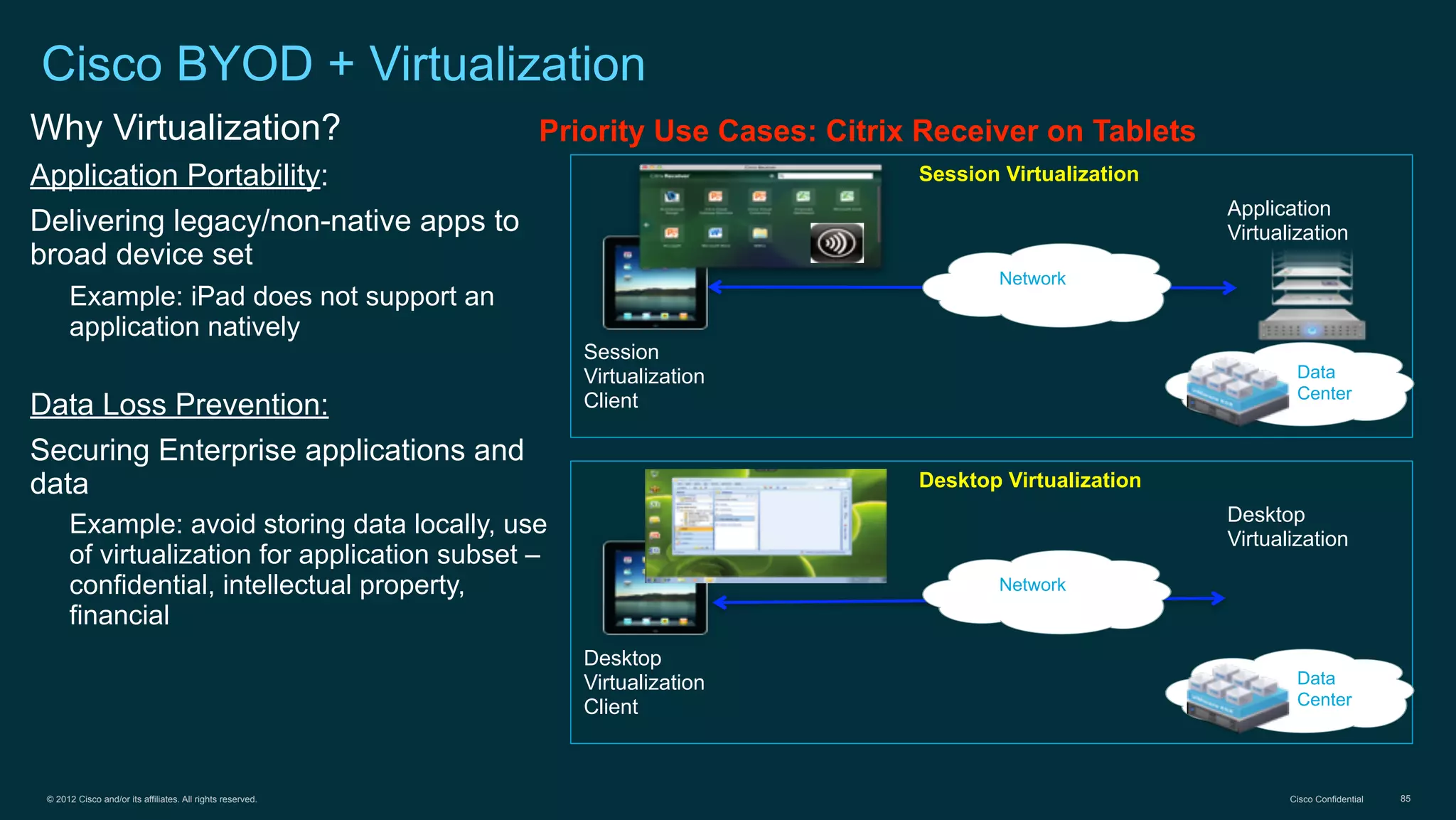
1. Cisco's distinct approach to securely supporting BYOD and VDI through technologies like mobile device management, secure connectivity solutions, and policy management.
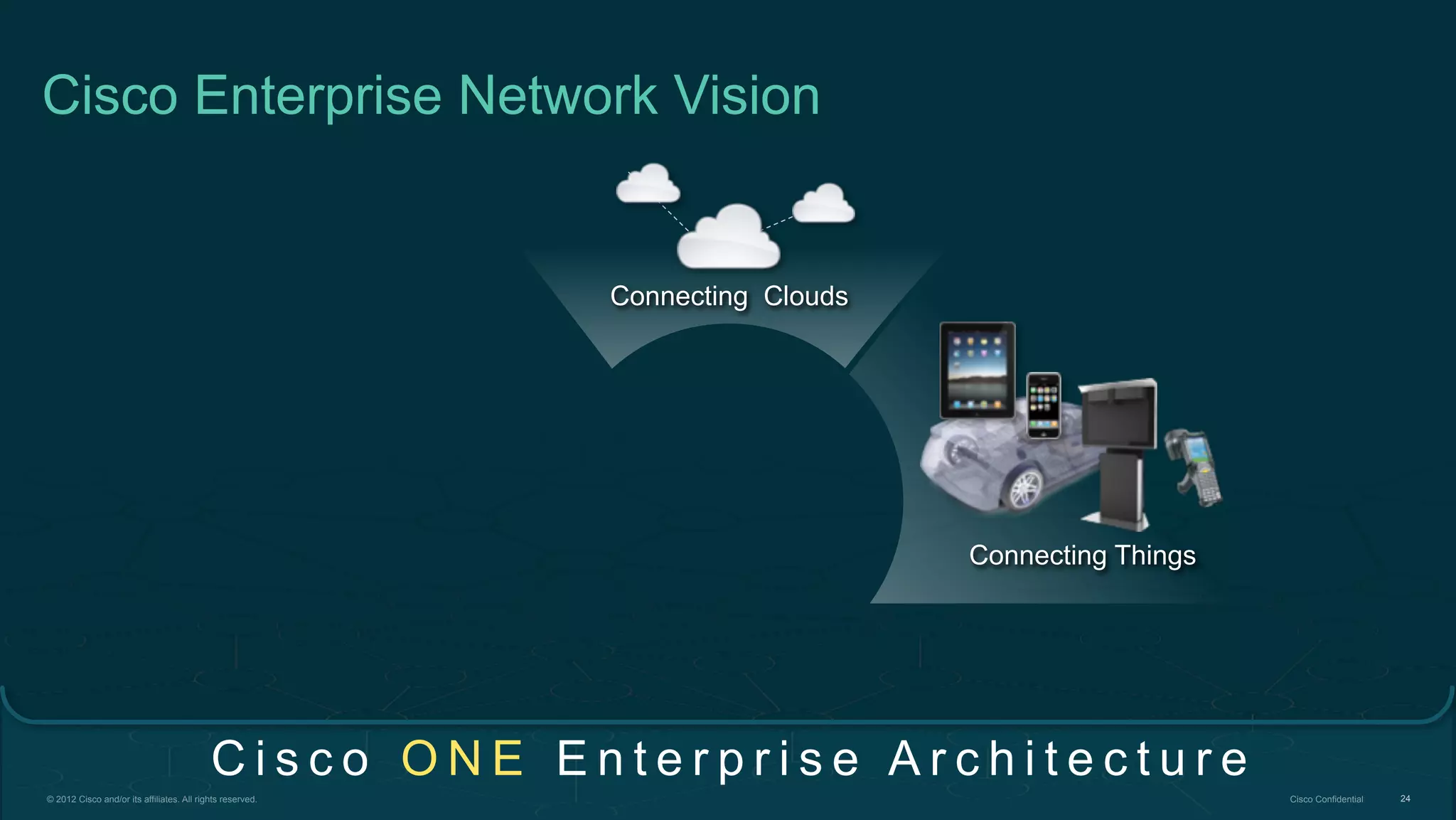
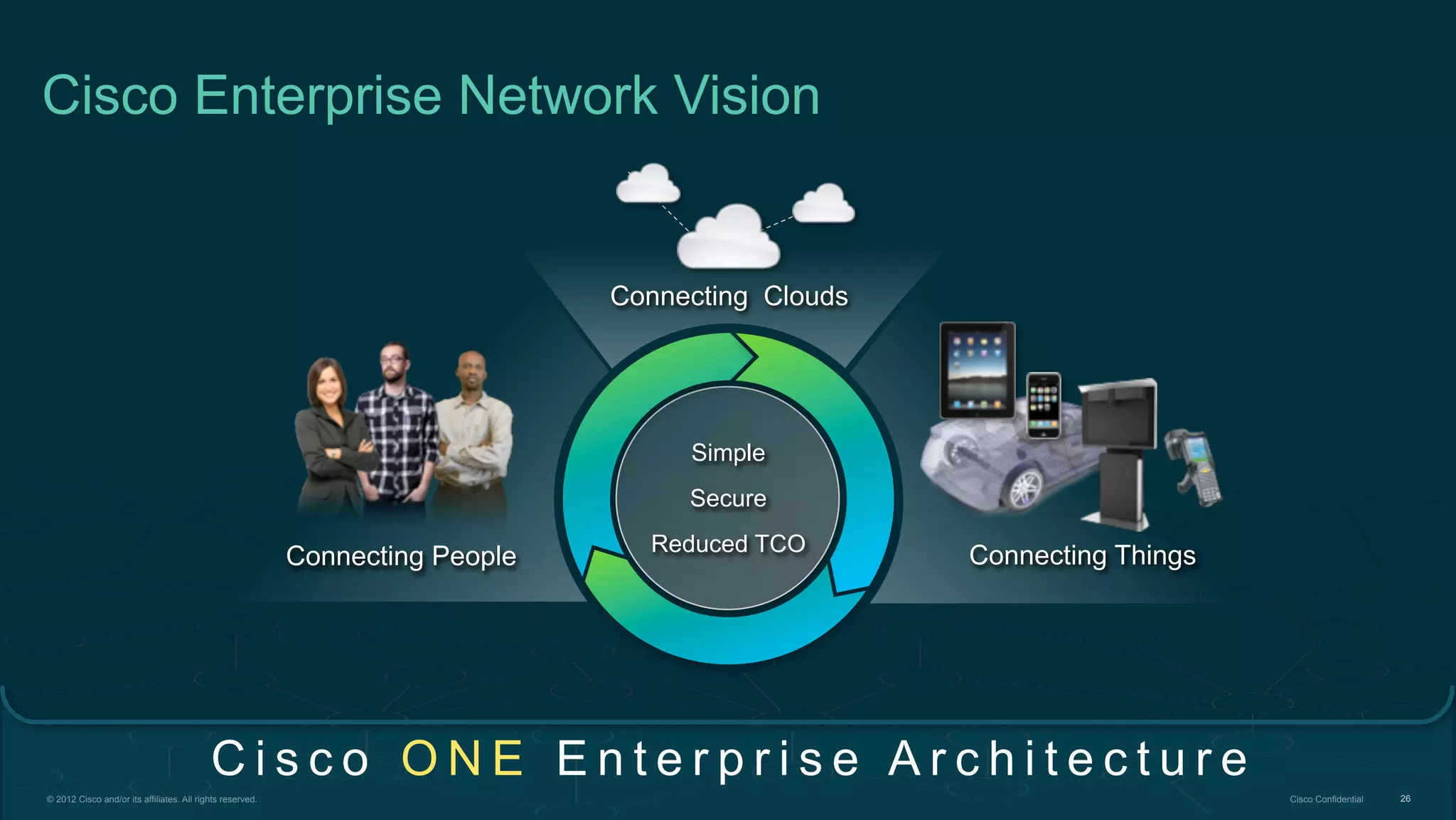
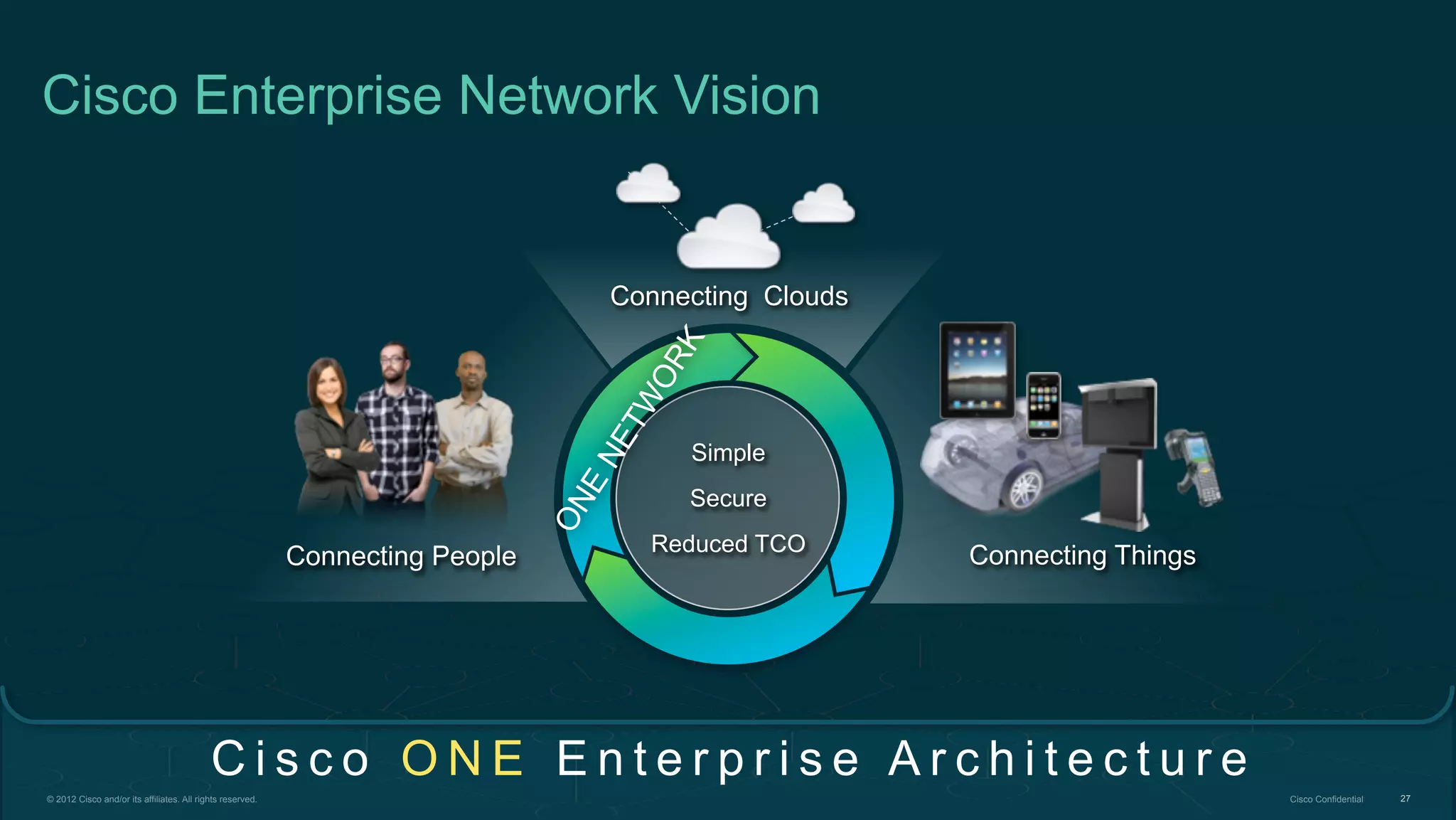
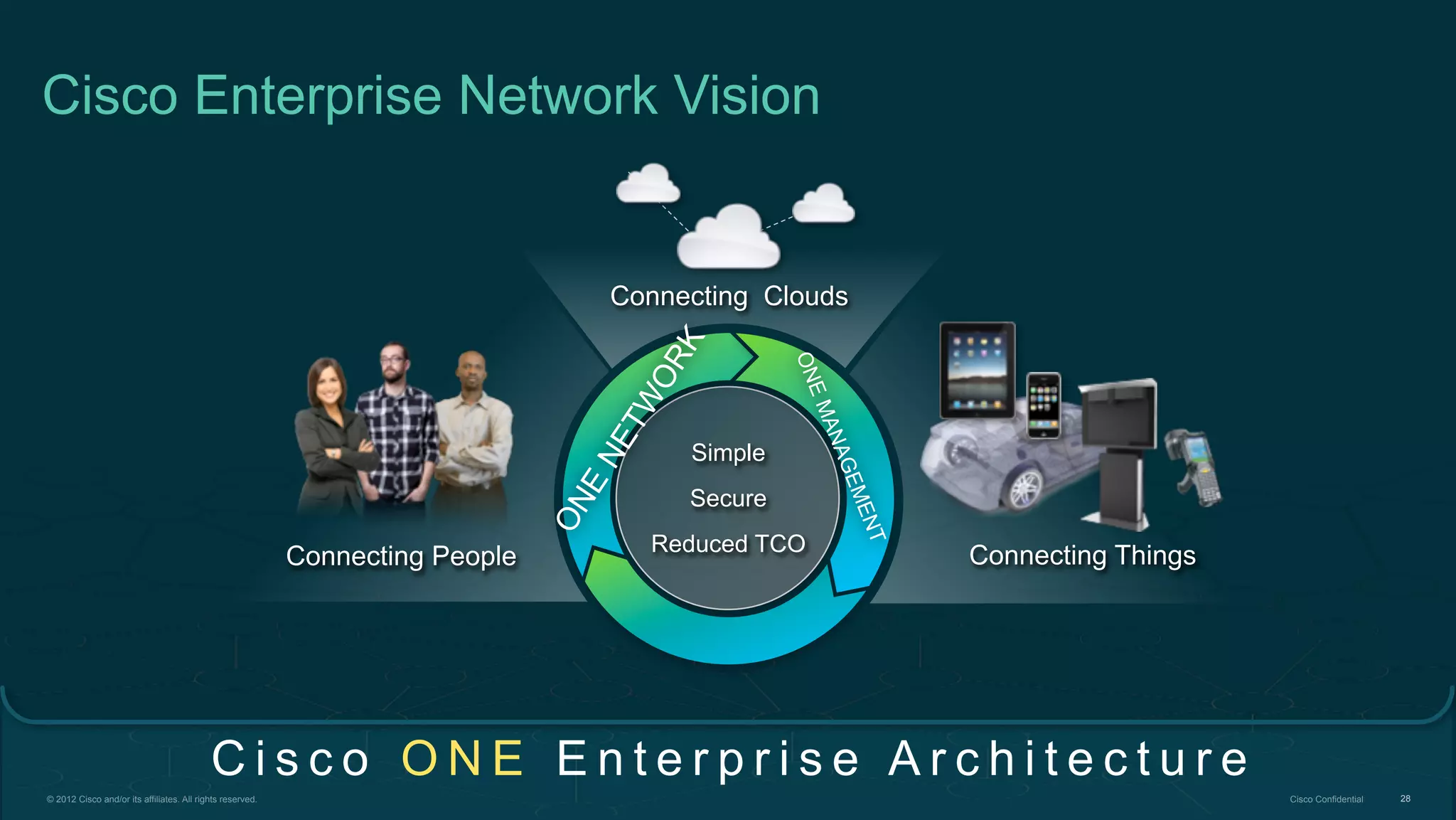
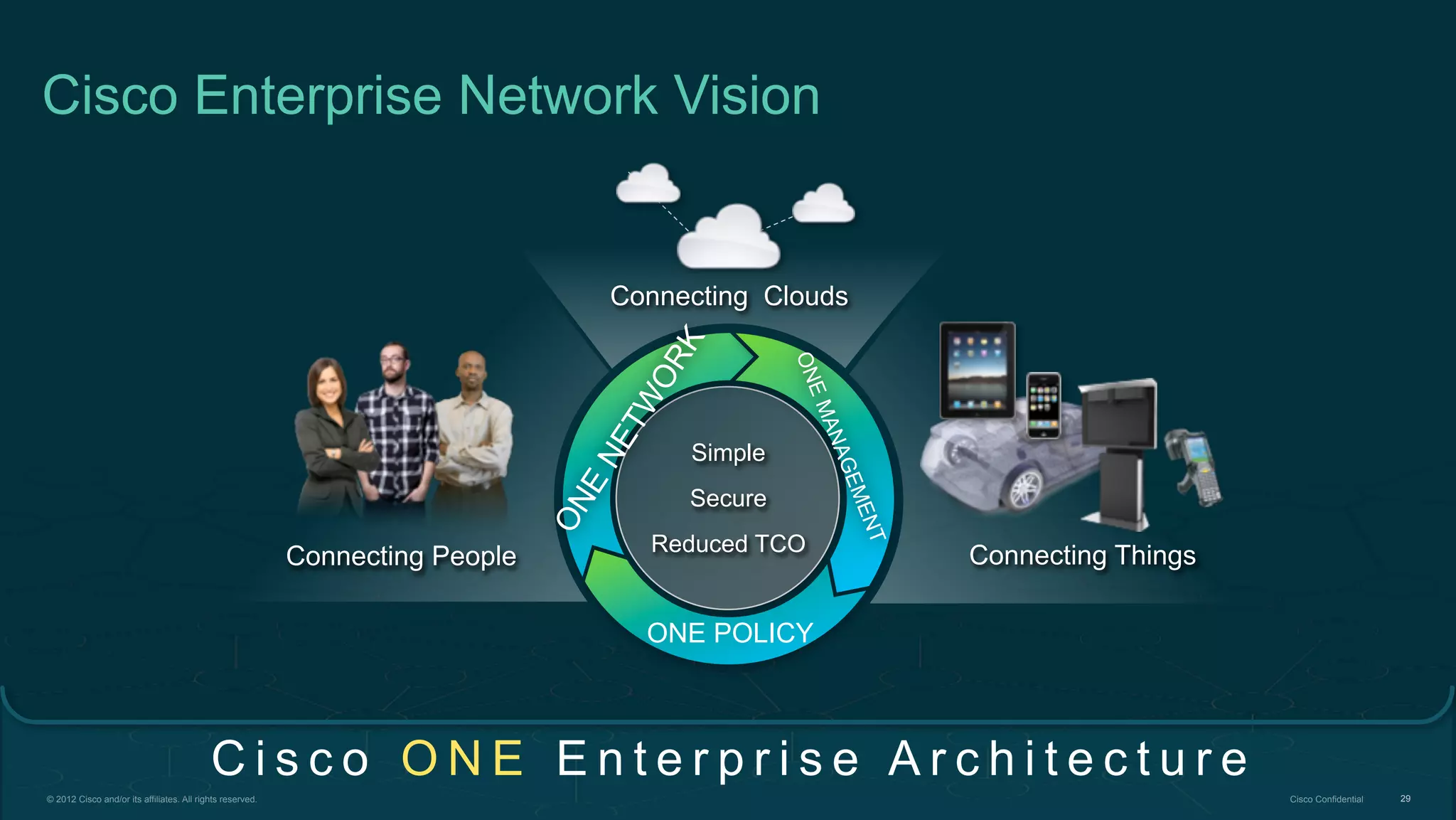
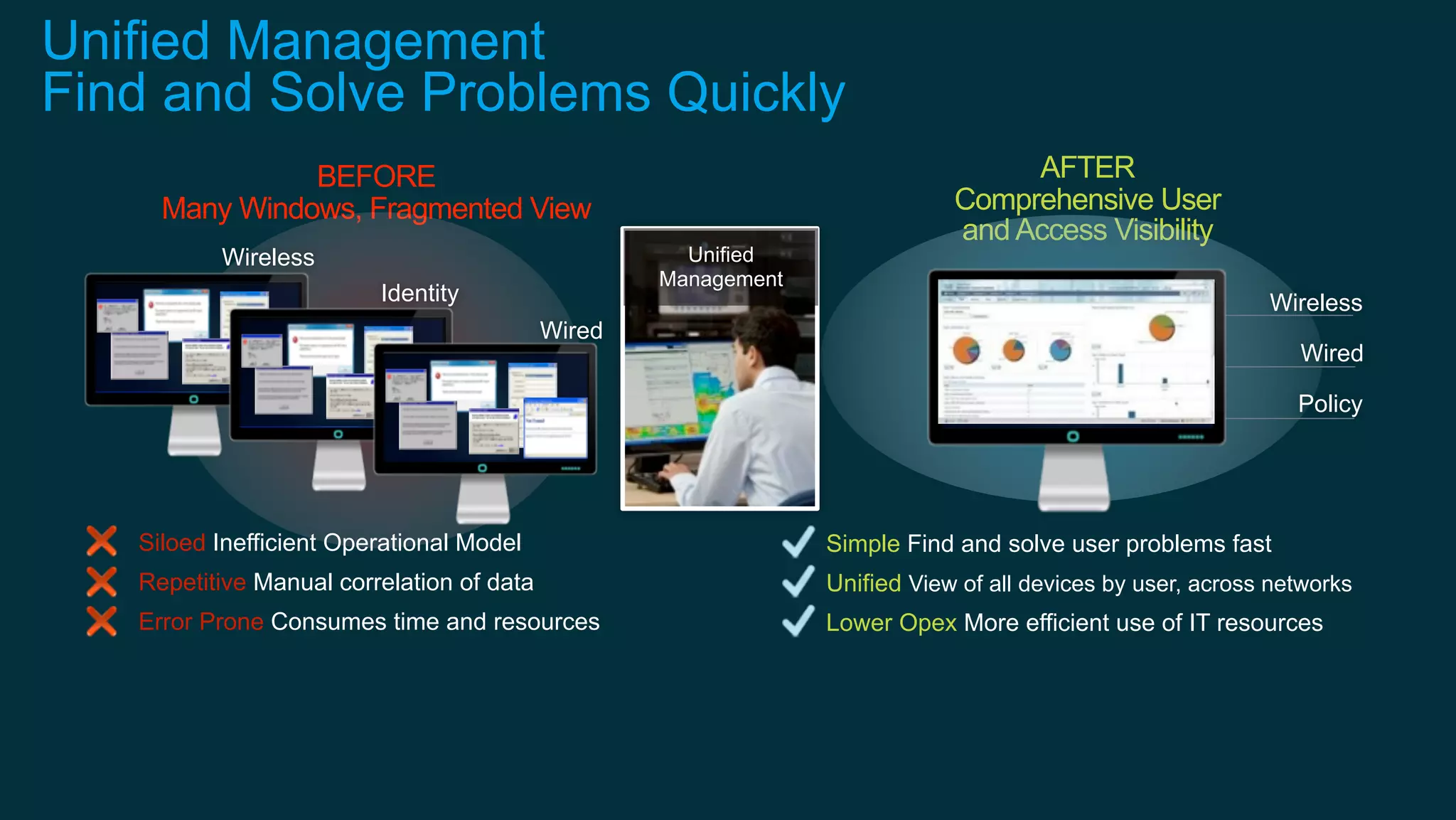
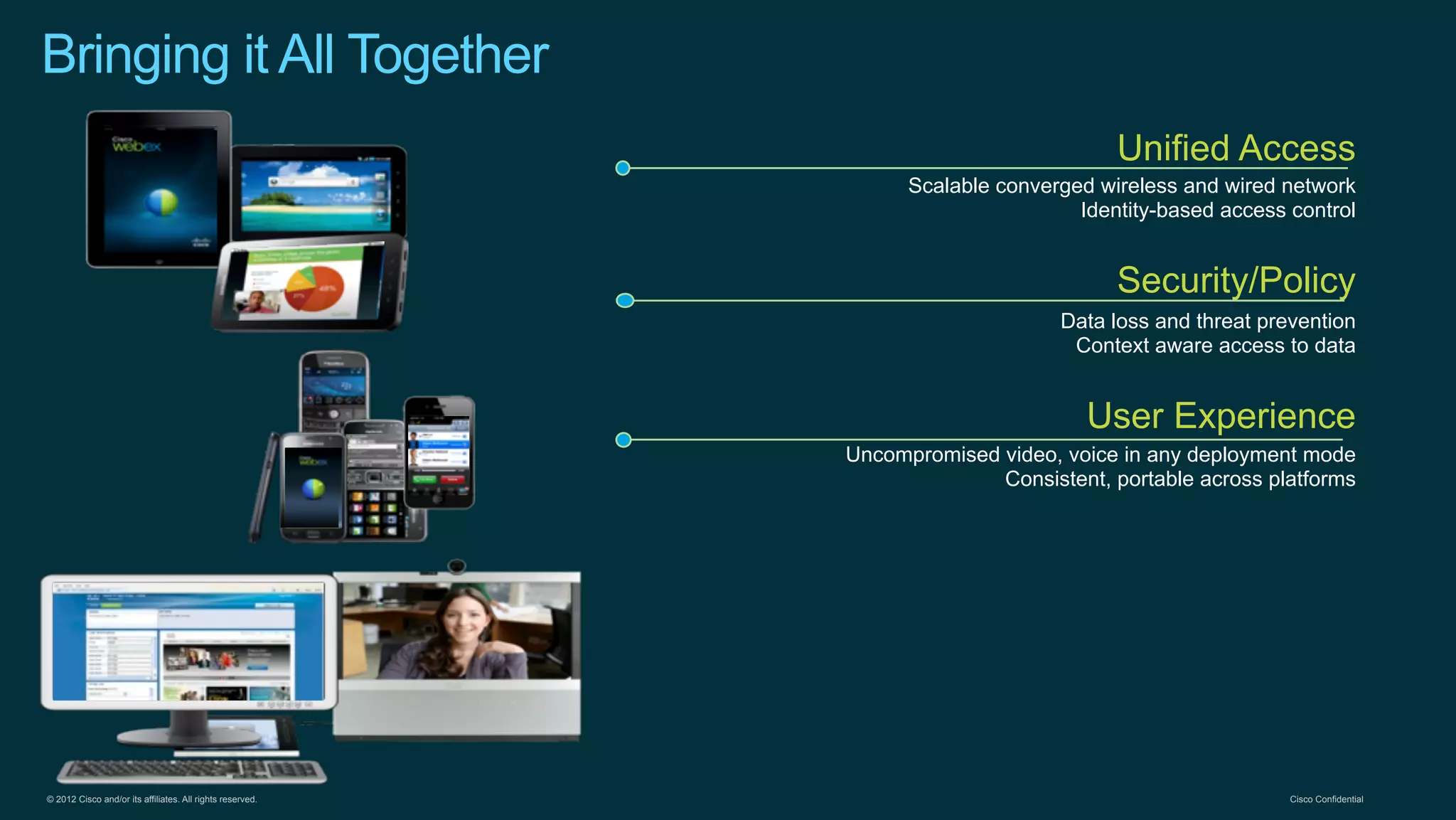
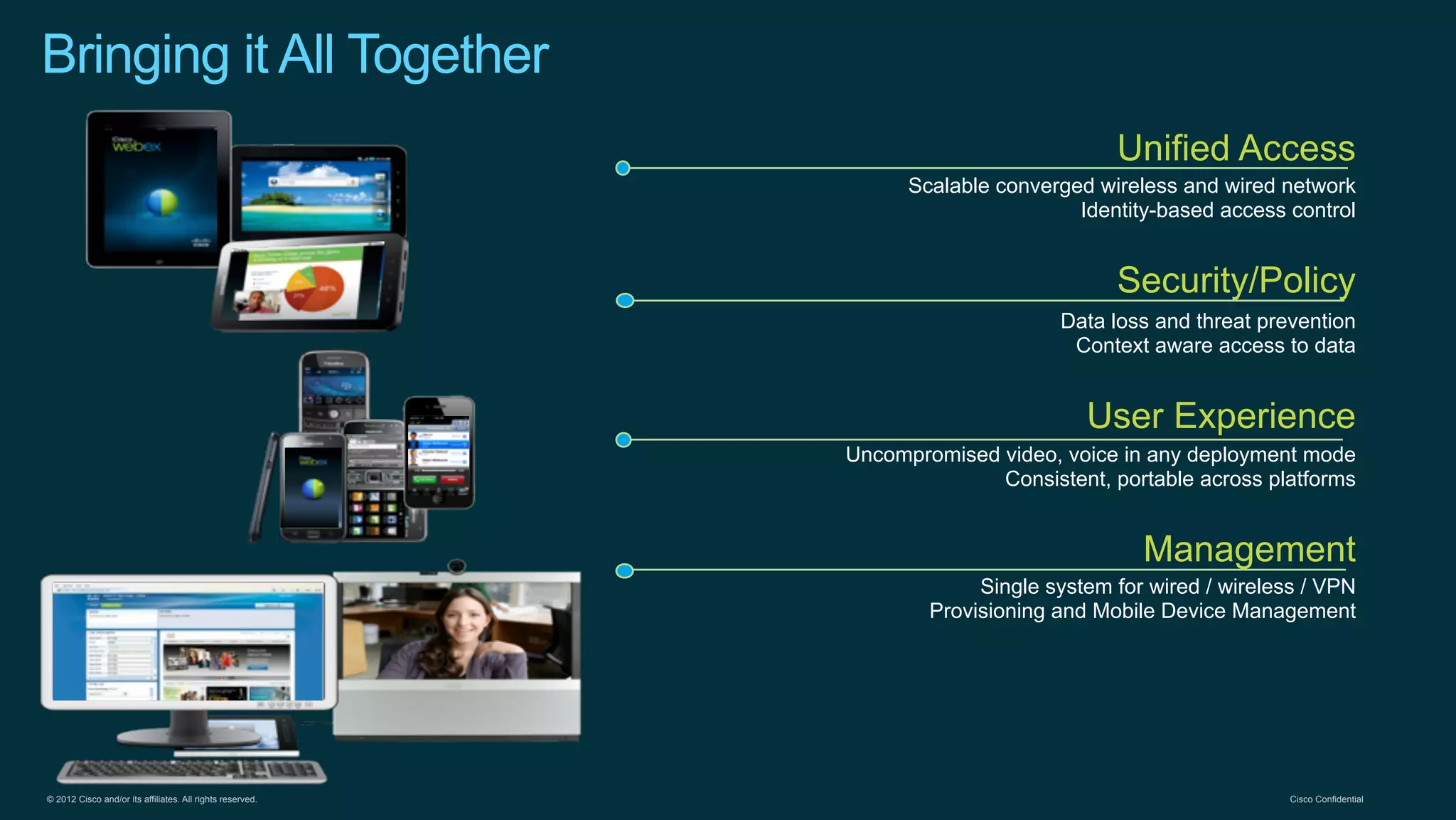
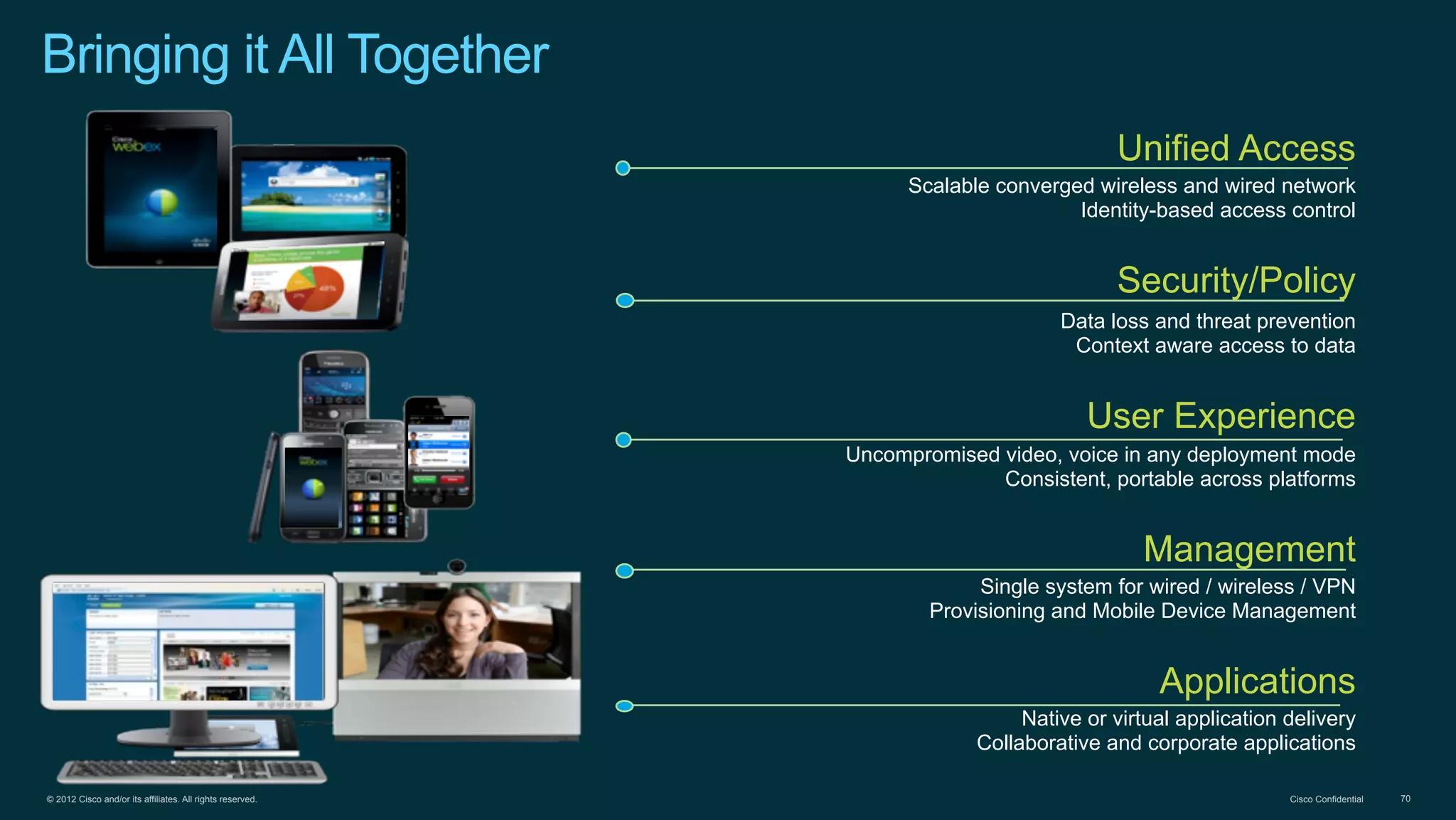
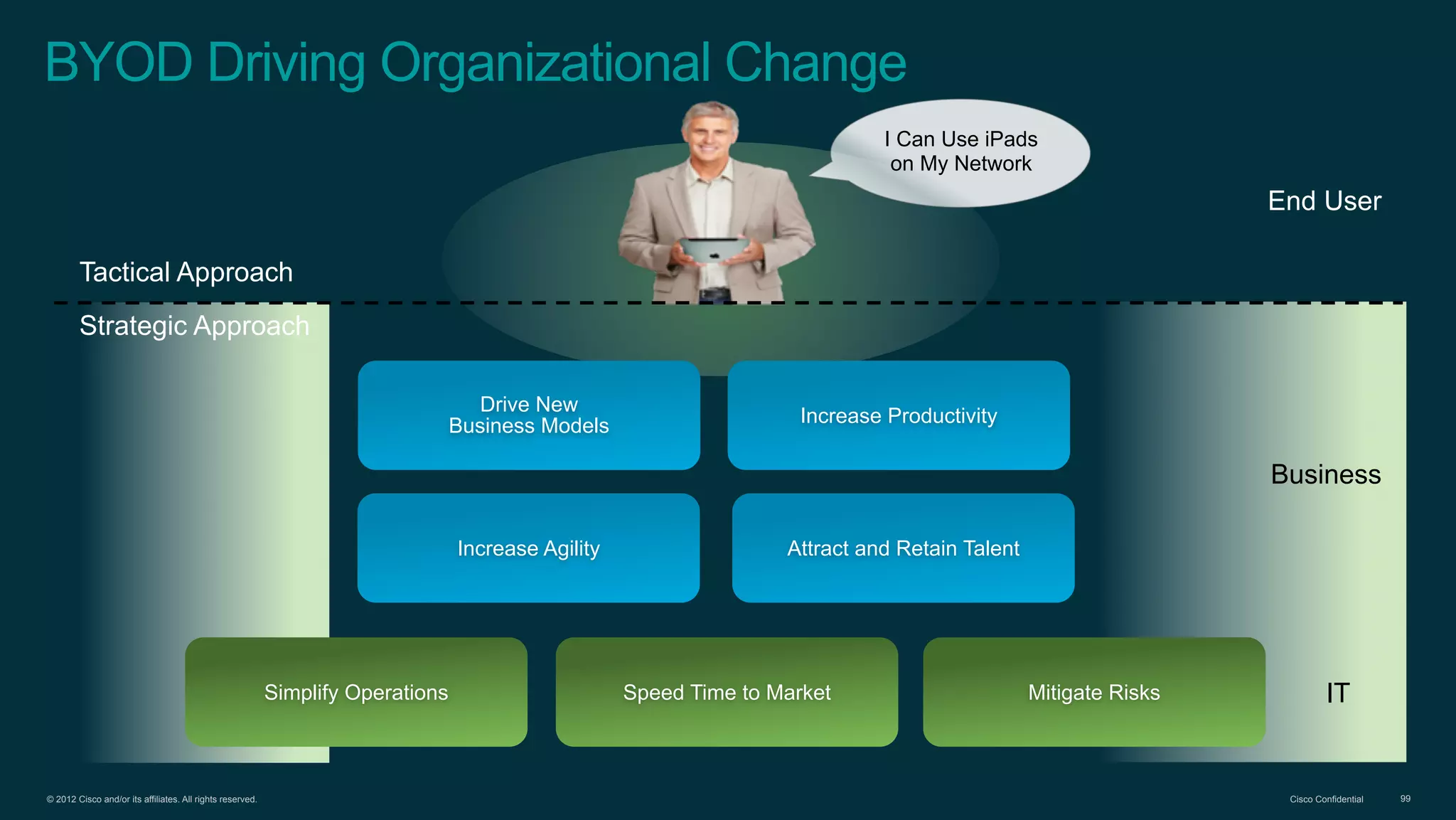
2. Cisco's Enterprise Network Vision which aims to securely connect people, clouds, and things through a simple, secure network with one policy and one management.
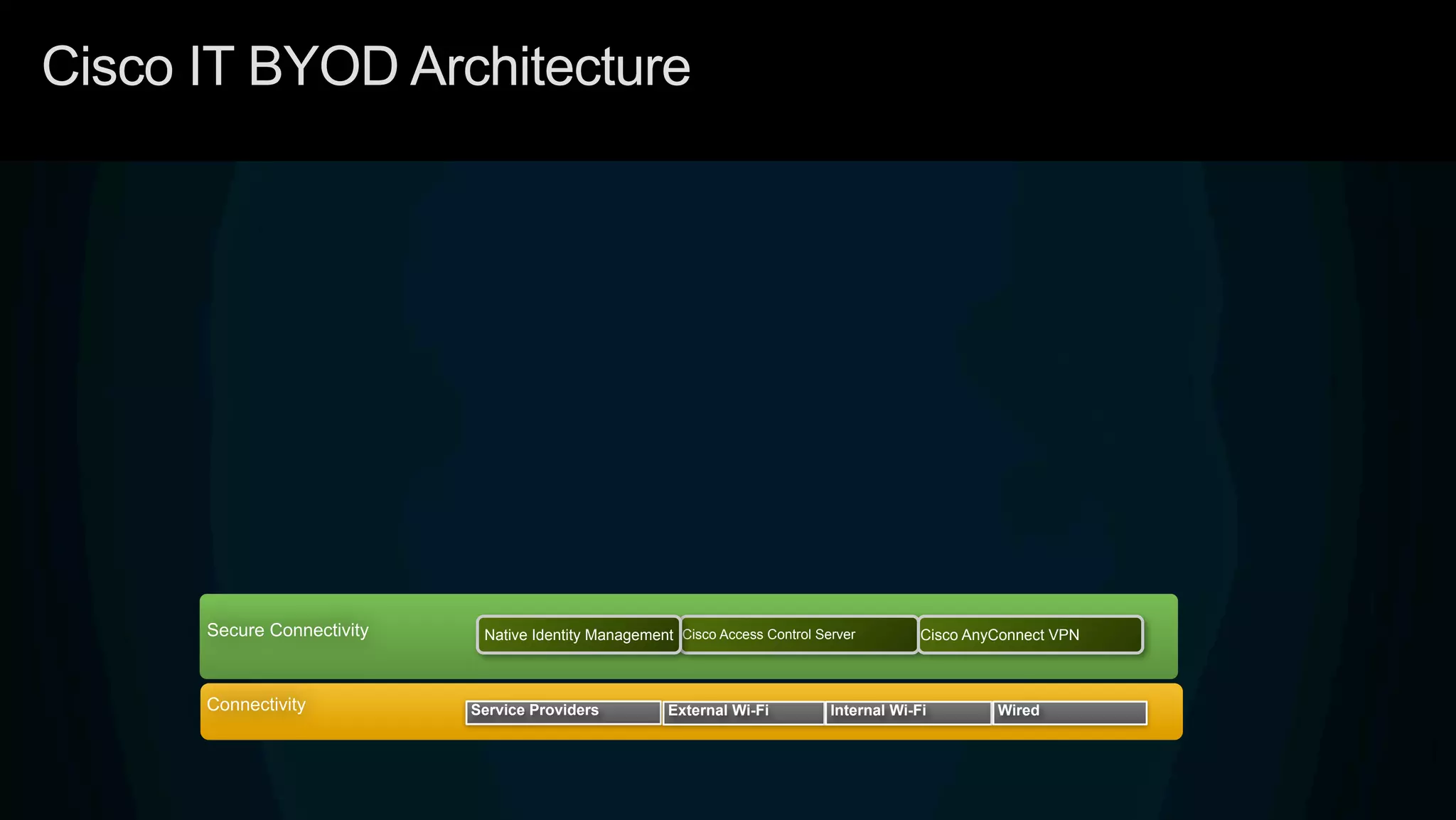
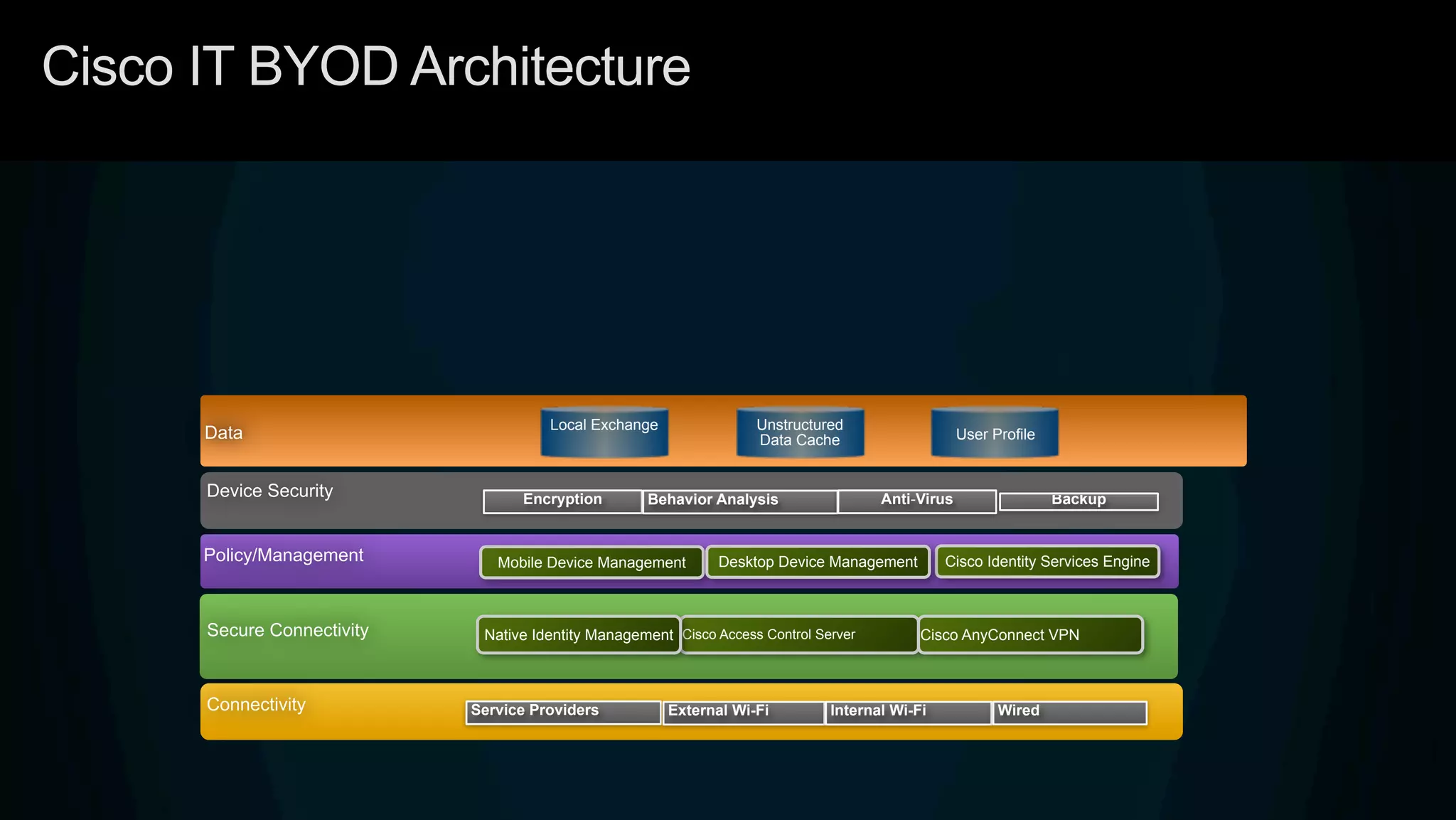
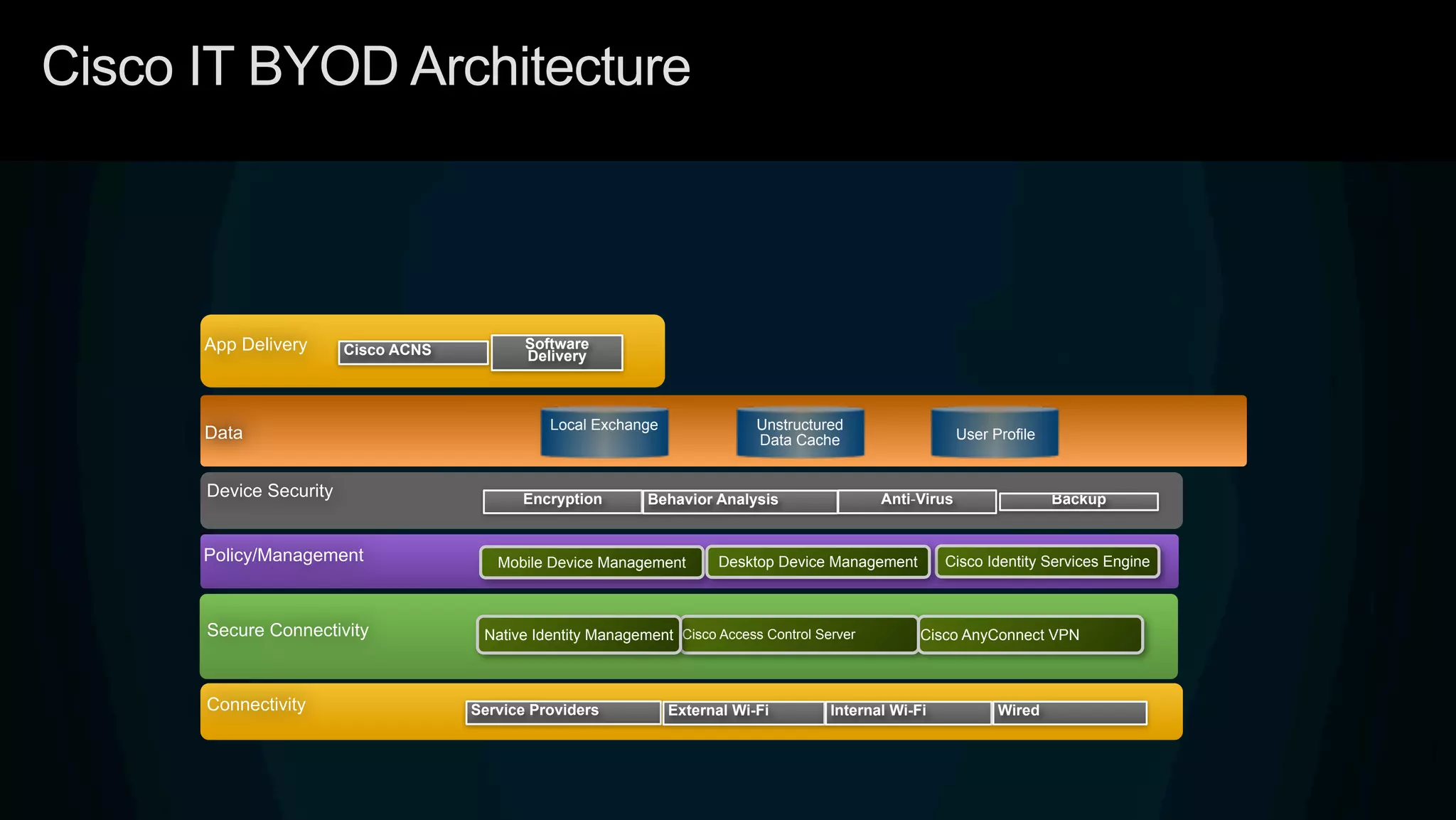
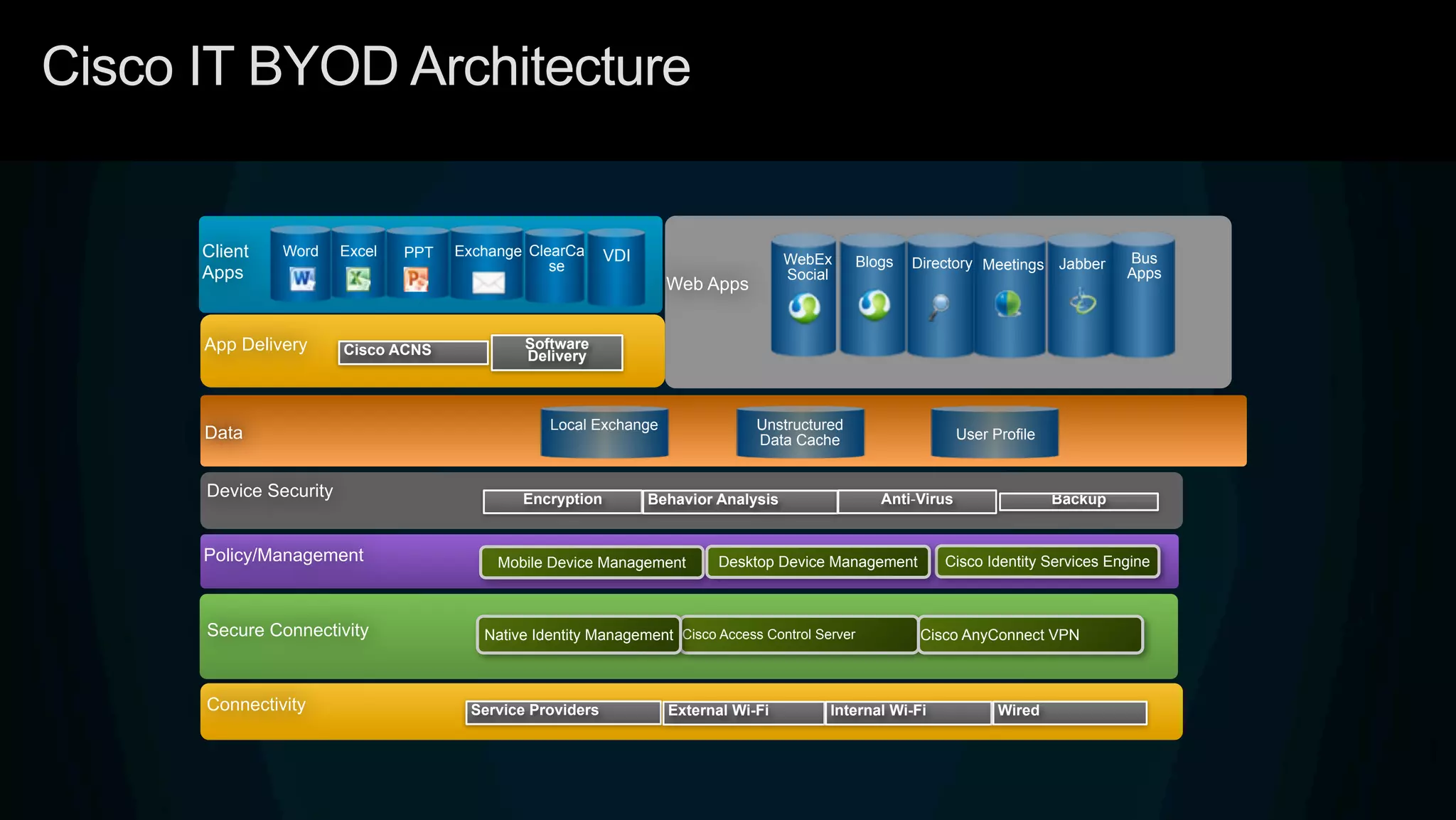
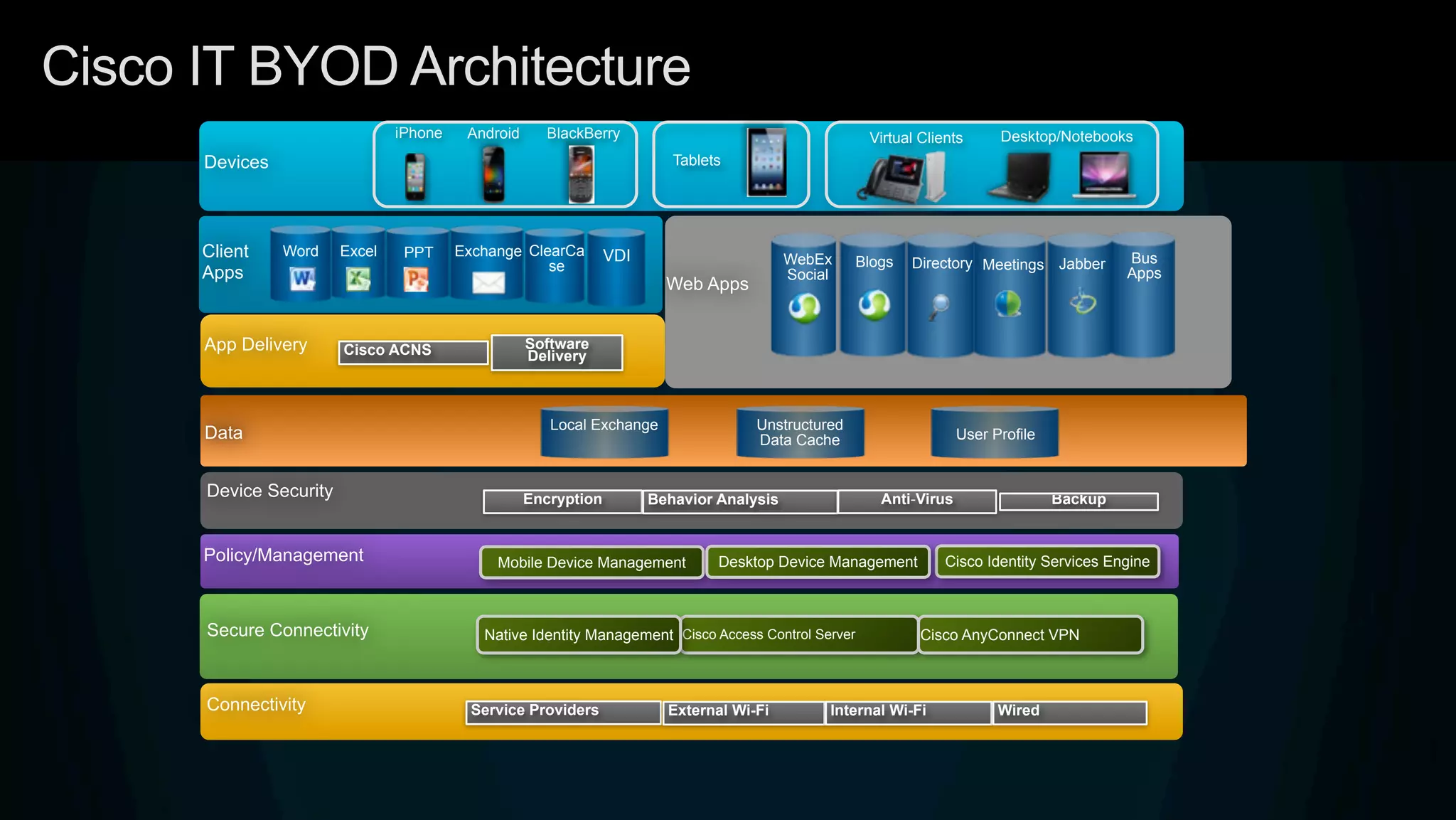
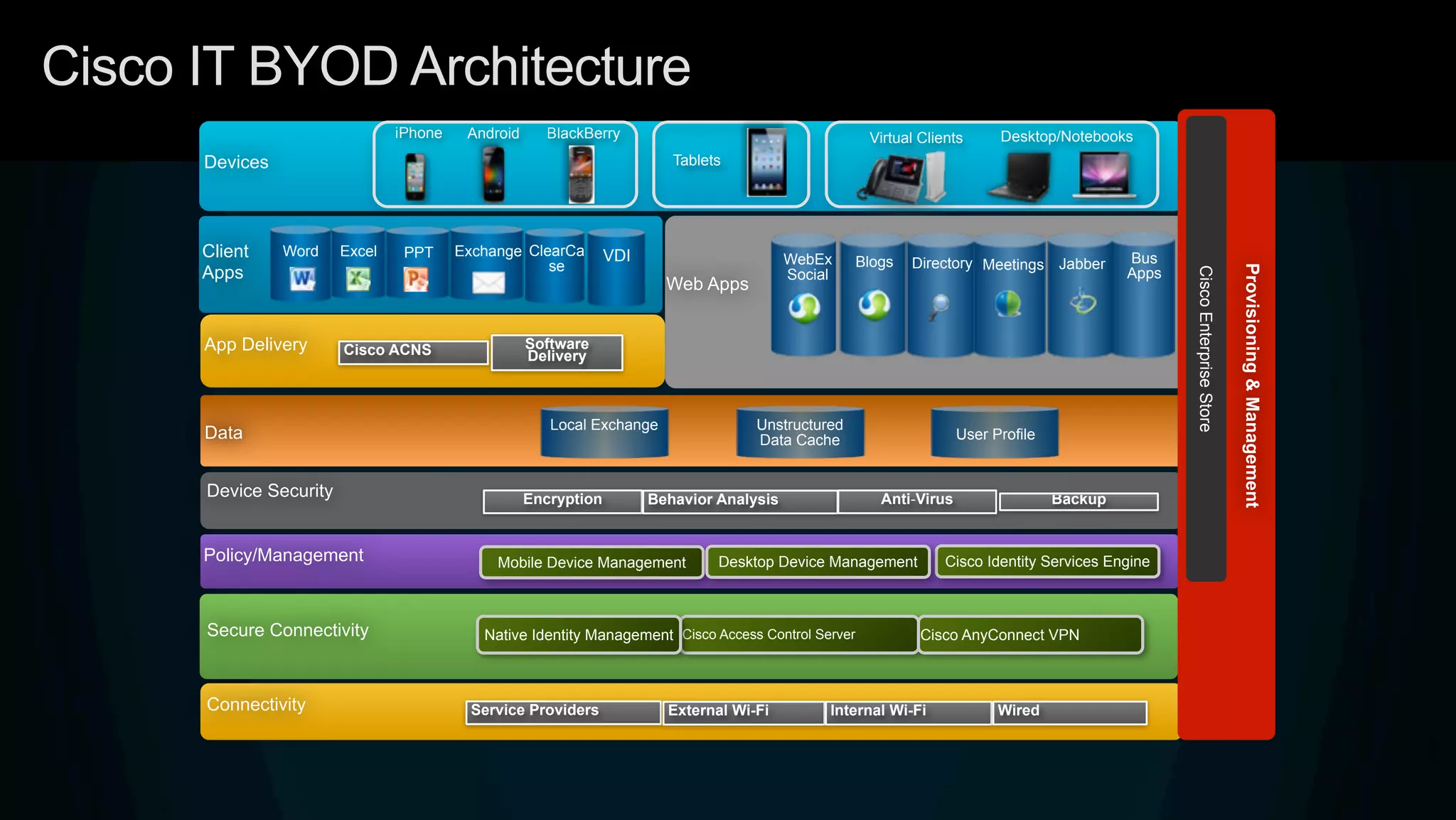
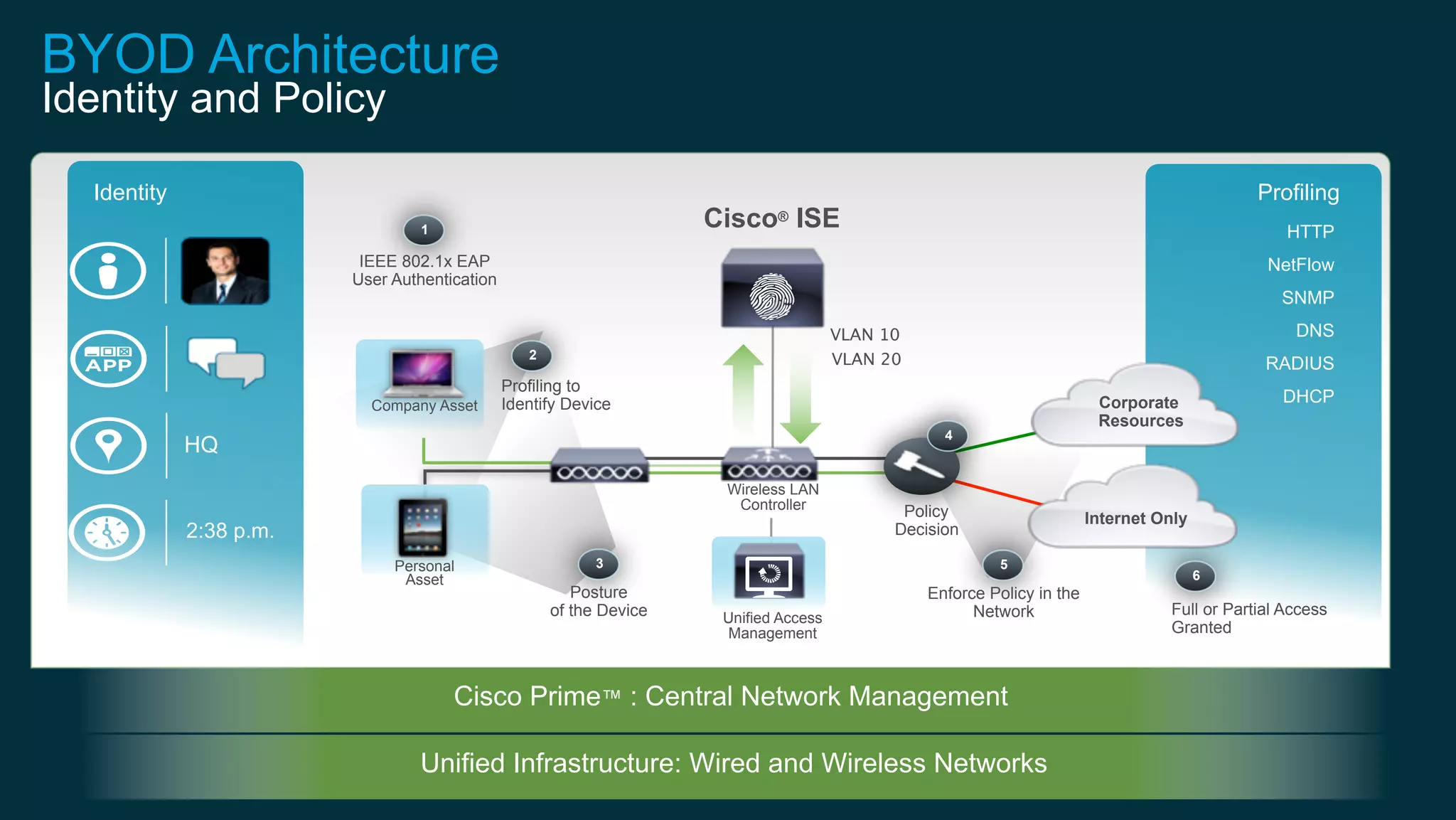
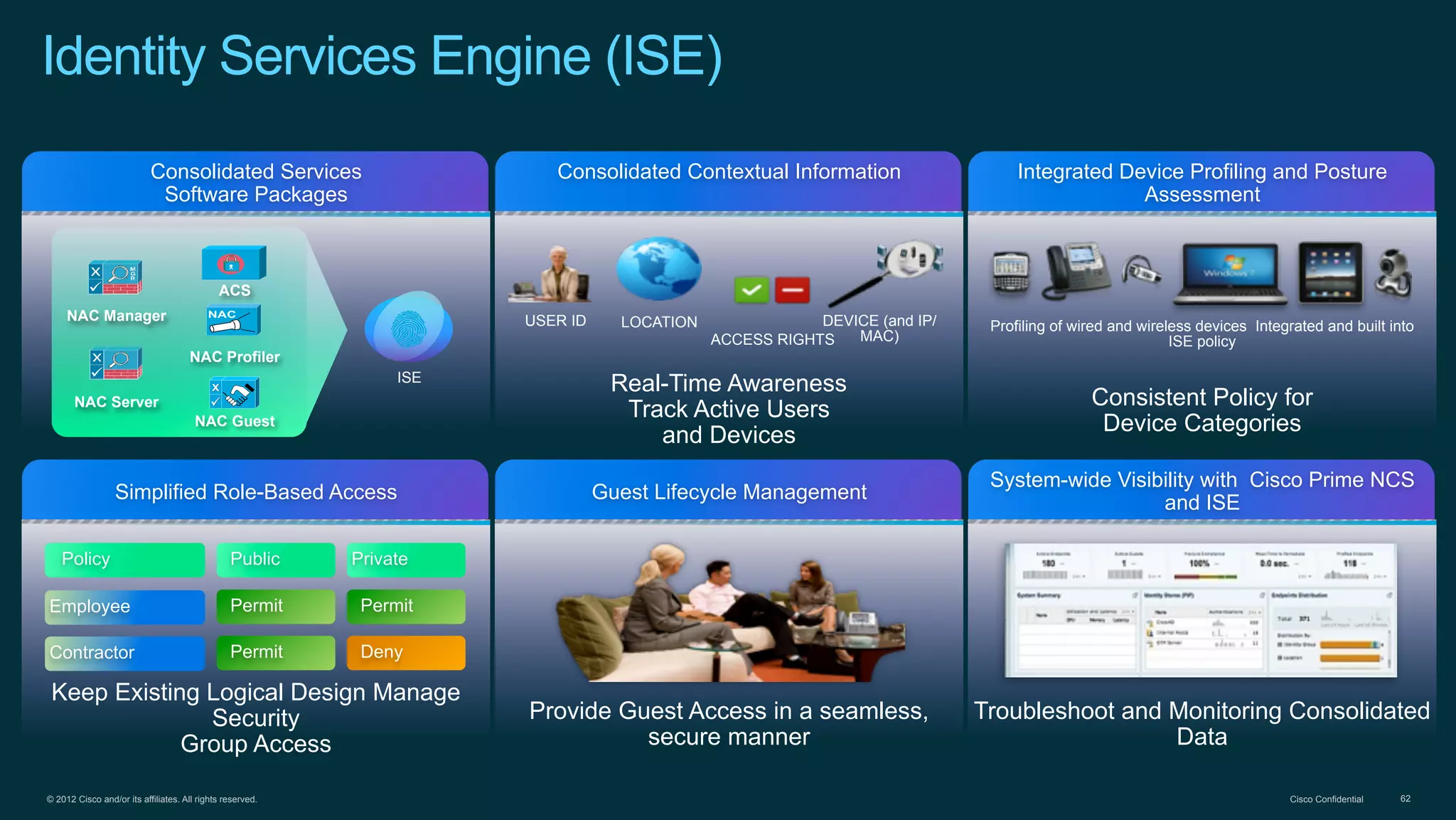
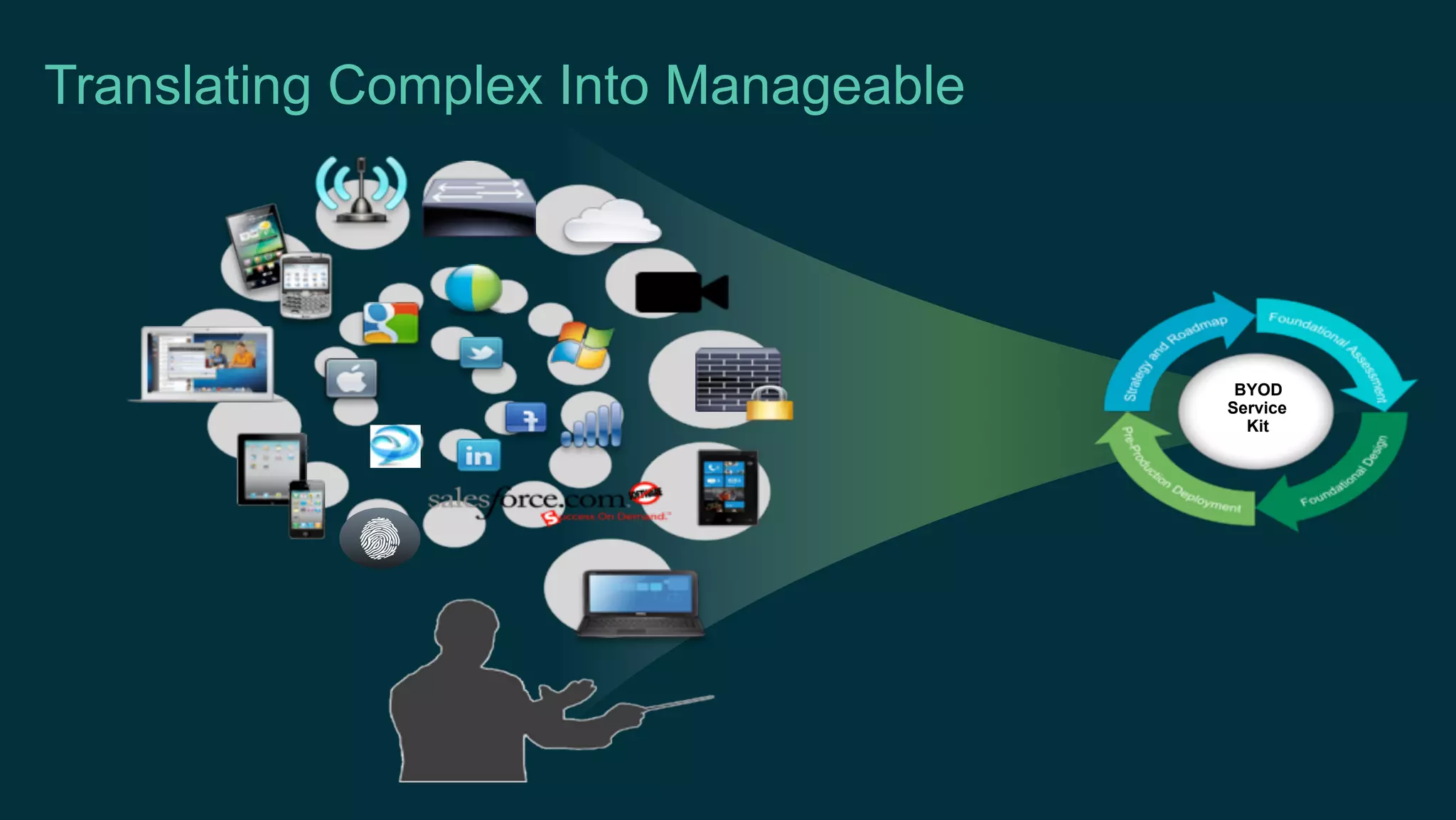
3. Cisco's BYOD architecture which leverages solutions like the Cisco Identity Services Engine and Cisco AnyConnect to provide secure connectivity, policy management, and application delivery to personal and corporate devices.