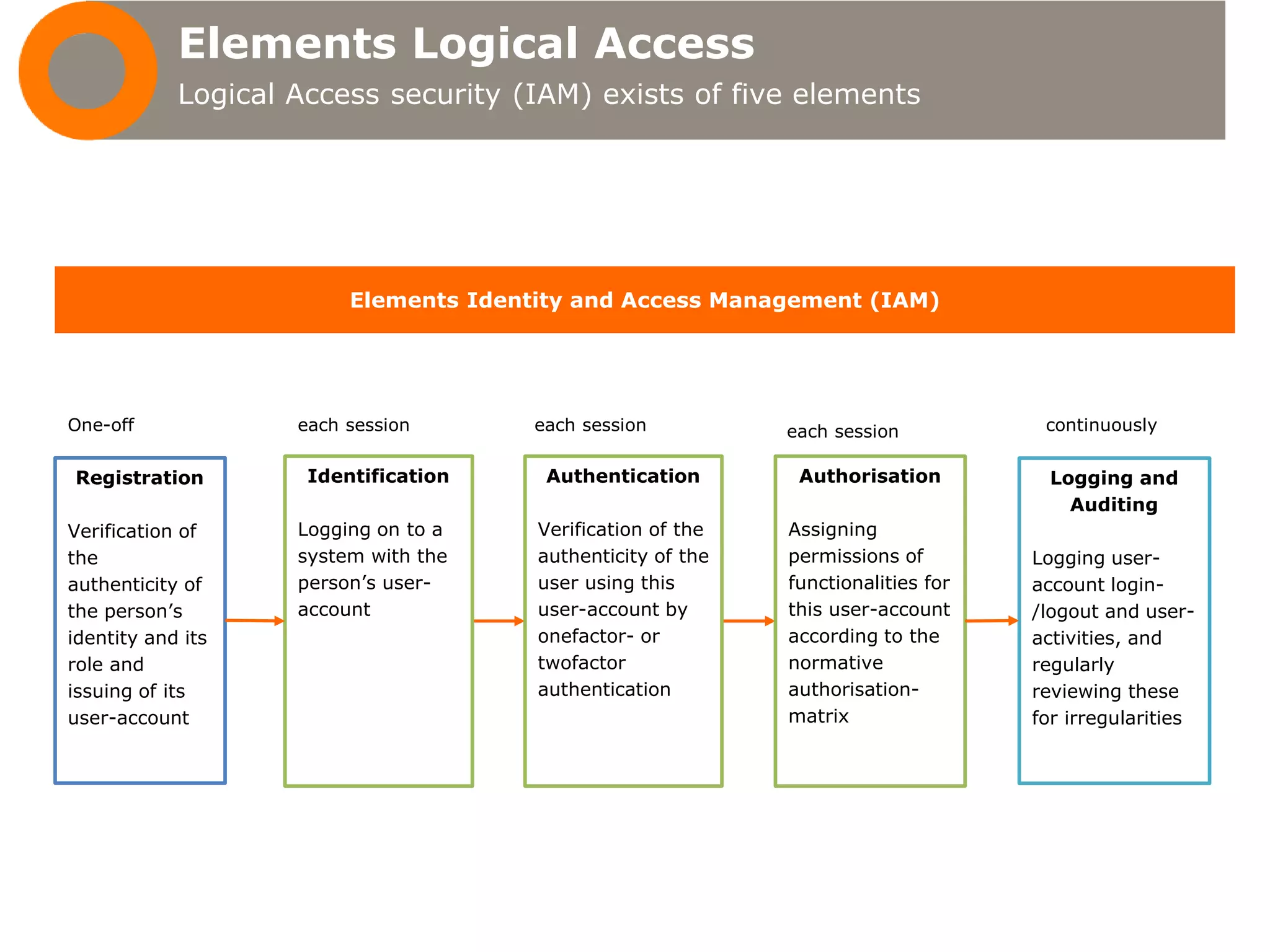
Logical access security consists of five elements - registration, identification, authentication, authorization, and logging and auditing. Registration verifies a person's identity and role to issue a user account. Identification and authentication verify a user by logging into and verifying their user account. Authorization assigns permissions to a user account based on their role. Logging and auditing monitors and reviews user login/logout activities and account use for irregularities.