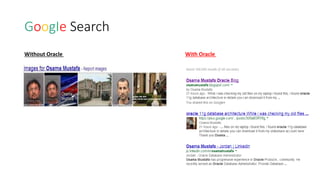
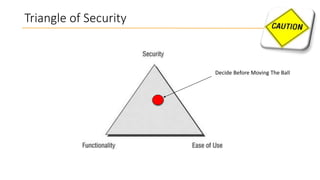
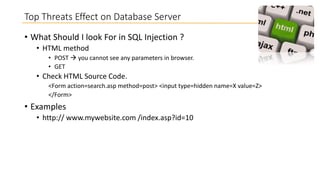
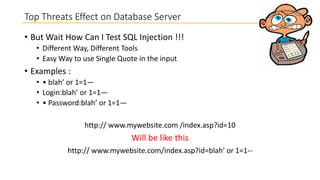
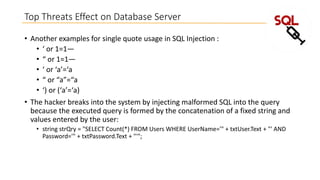
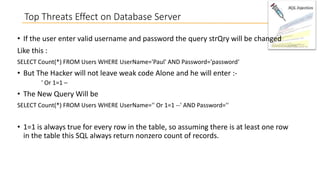
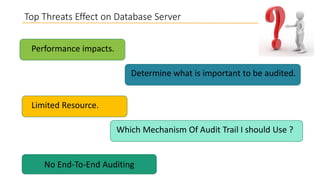
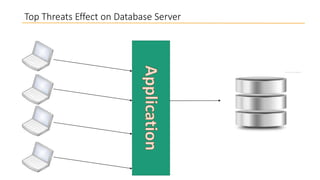
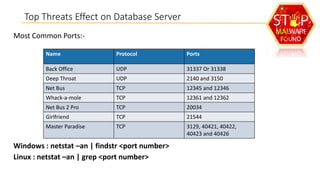
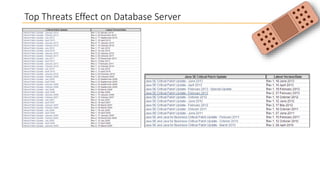
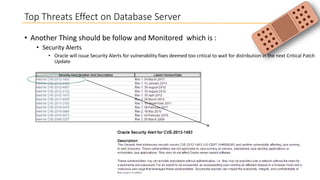
This document discusses database security and how databases can be hacked. It begins by introducing the presenter and their qualifications. It then discusses why database security is important for protecting financial, customer and organizational data. Common ways databases are hacked include gathering information through search engines or social media, scanning for vulnerabilities, gaining unauthorized access, and maintaining that access. Specific attacks on Oracle databases and the most common database security threats are outlined, such as weak authentication, denial of service attacks, and SQL injection. The document provides examples of how to test for and exploit SQL injection vulnerabilities. It emphasizes the importance of securing databases to prevent data theft and protect sensitive information.