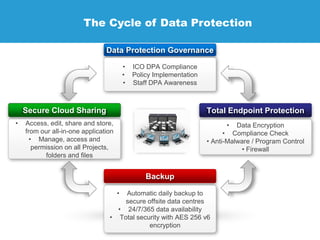
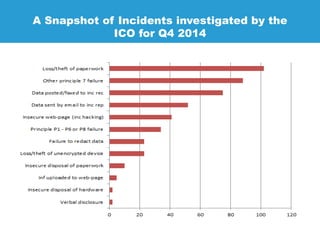
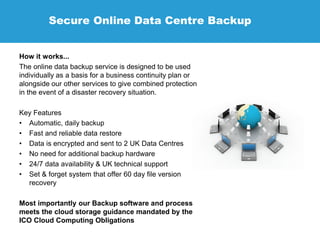
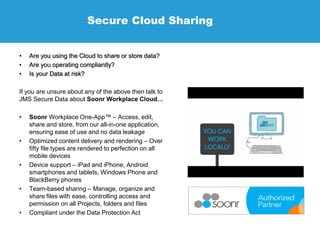
JMS Secure Data is a specialist in data protection services, offering solutions to ensure compliance for businesses with data protection licenses. Their services include risk assessments, technical implementation, and ongoing support to safeguard confidential data across various sectors. They emphasize the necessity of encryption to protect sensitive information, detailing their offerings such as secure cloud sharing, data backup, and compliance with data protection regulations.