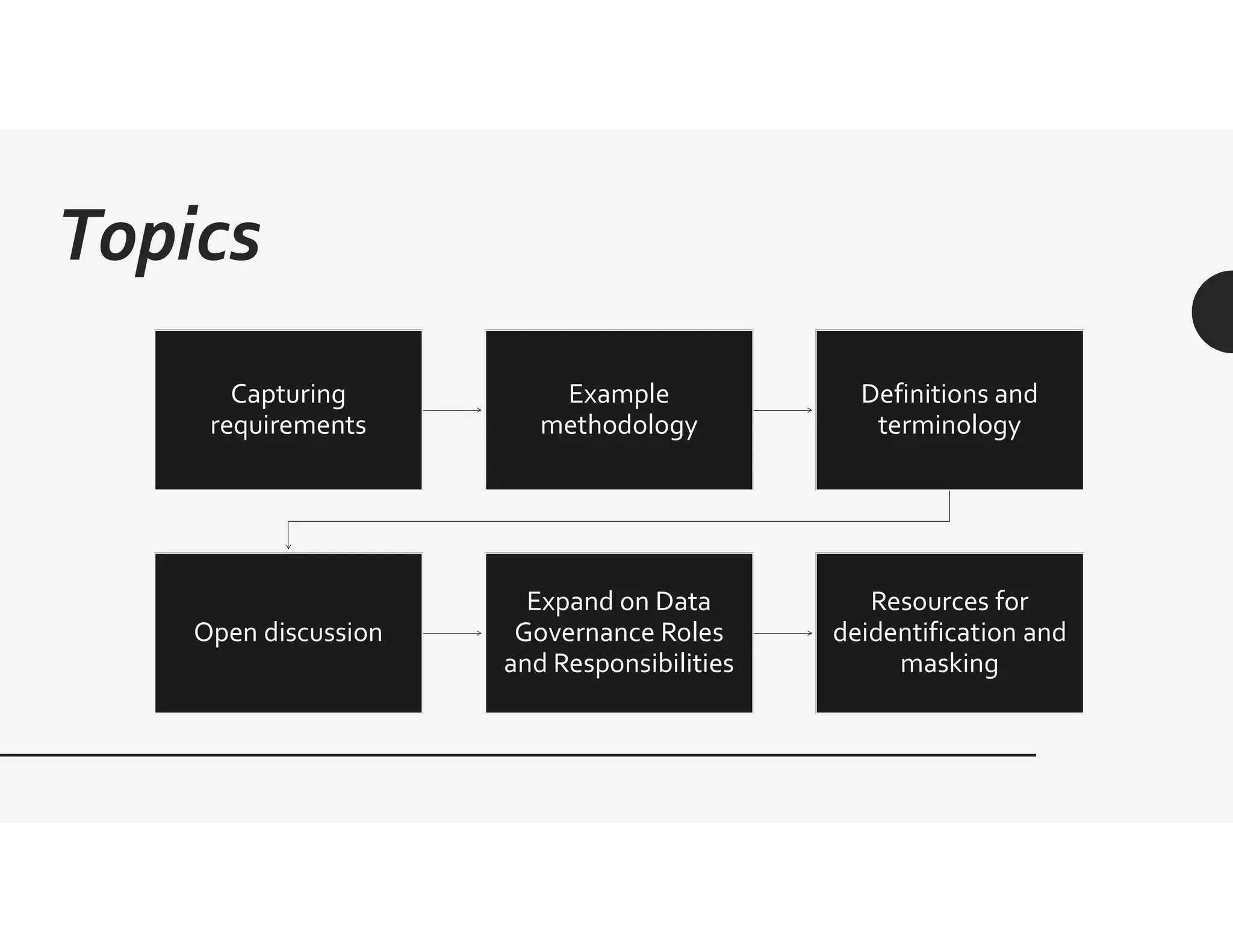
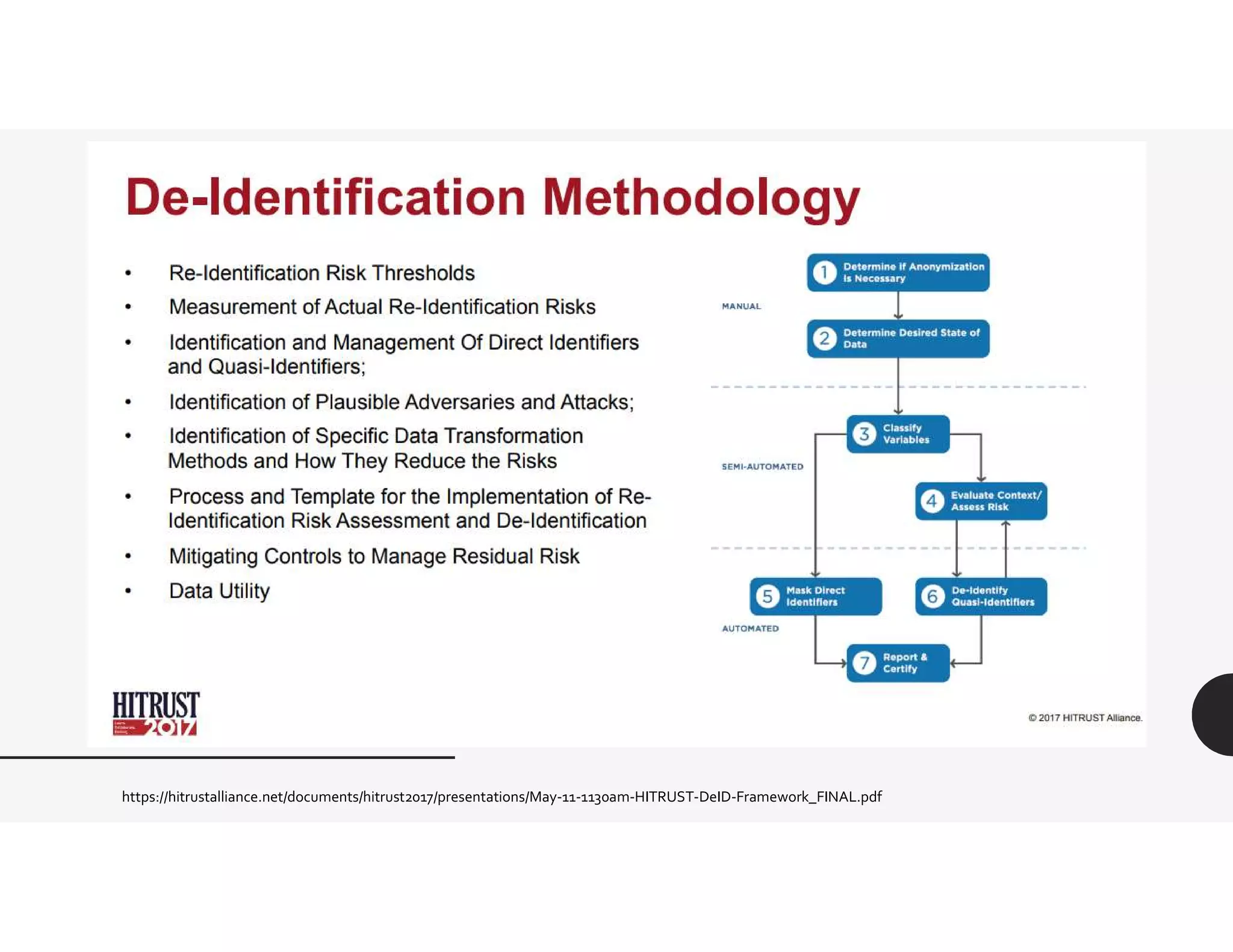
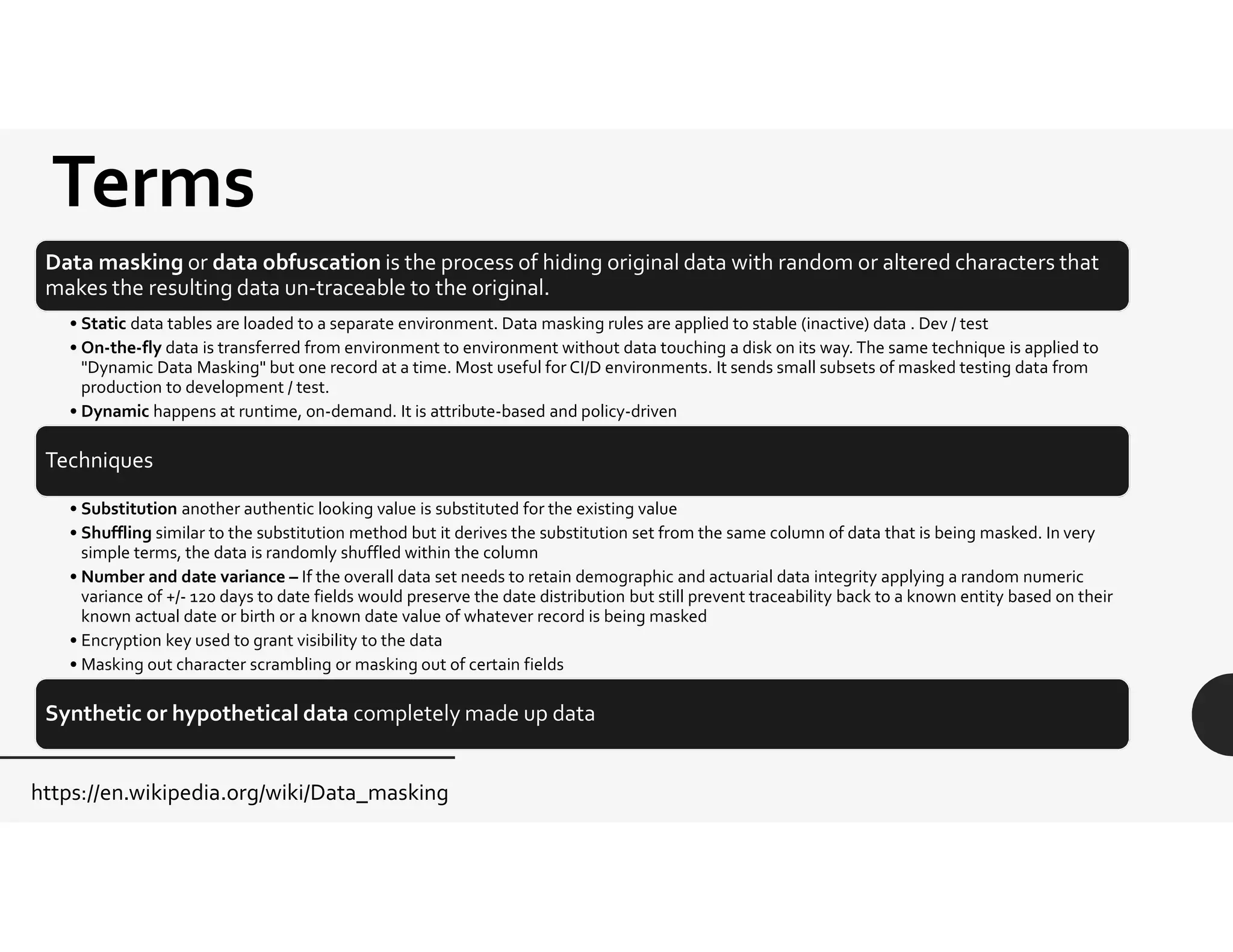
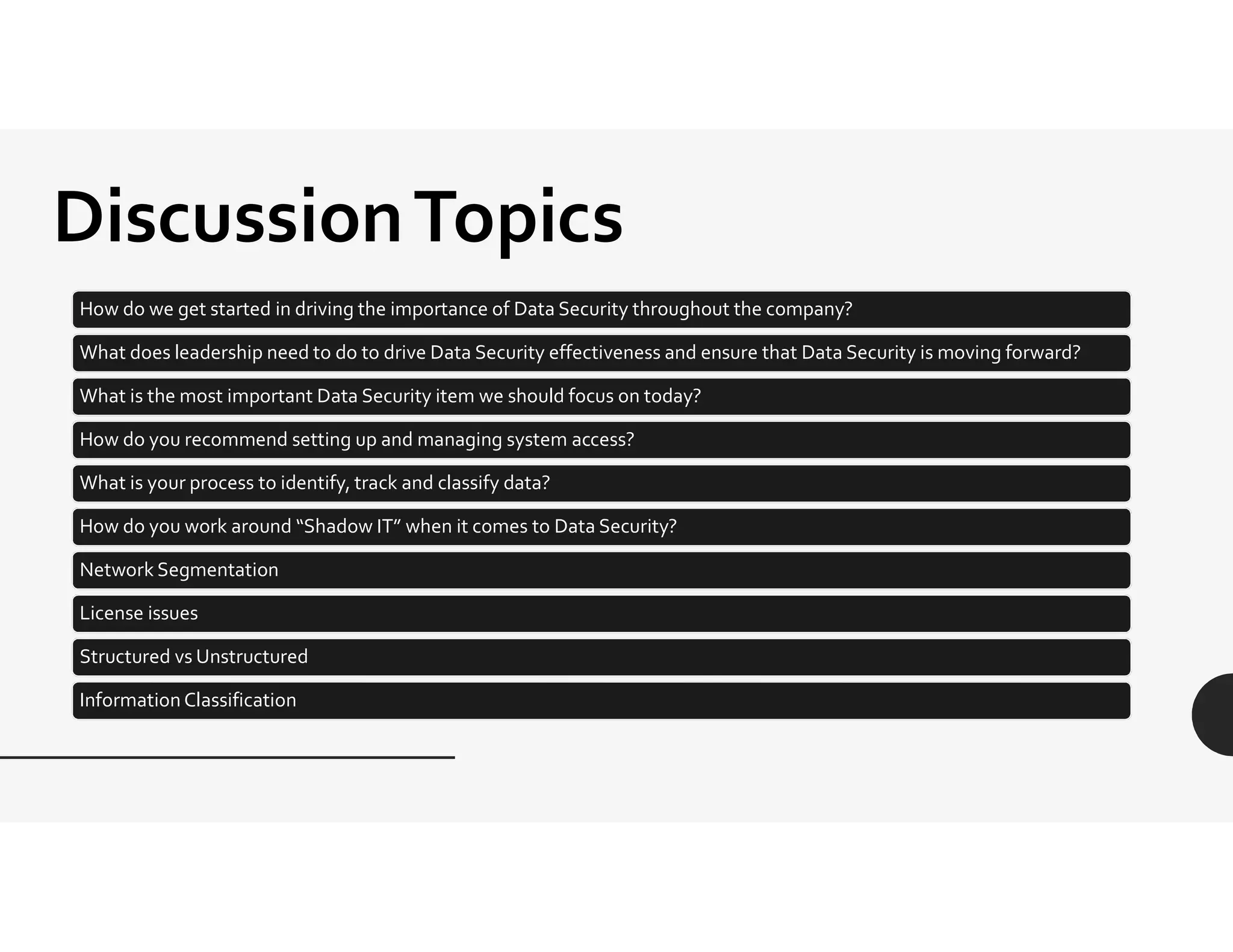
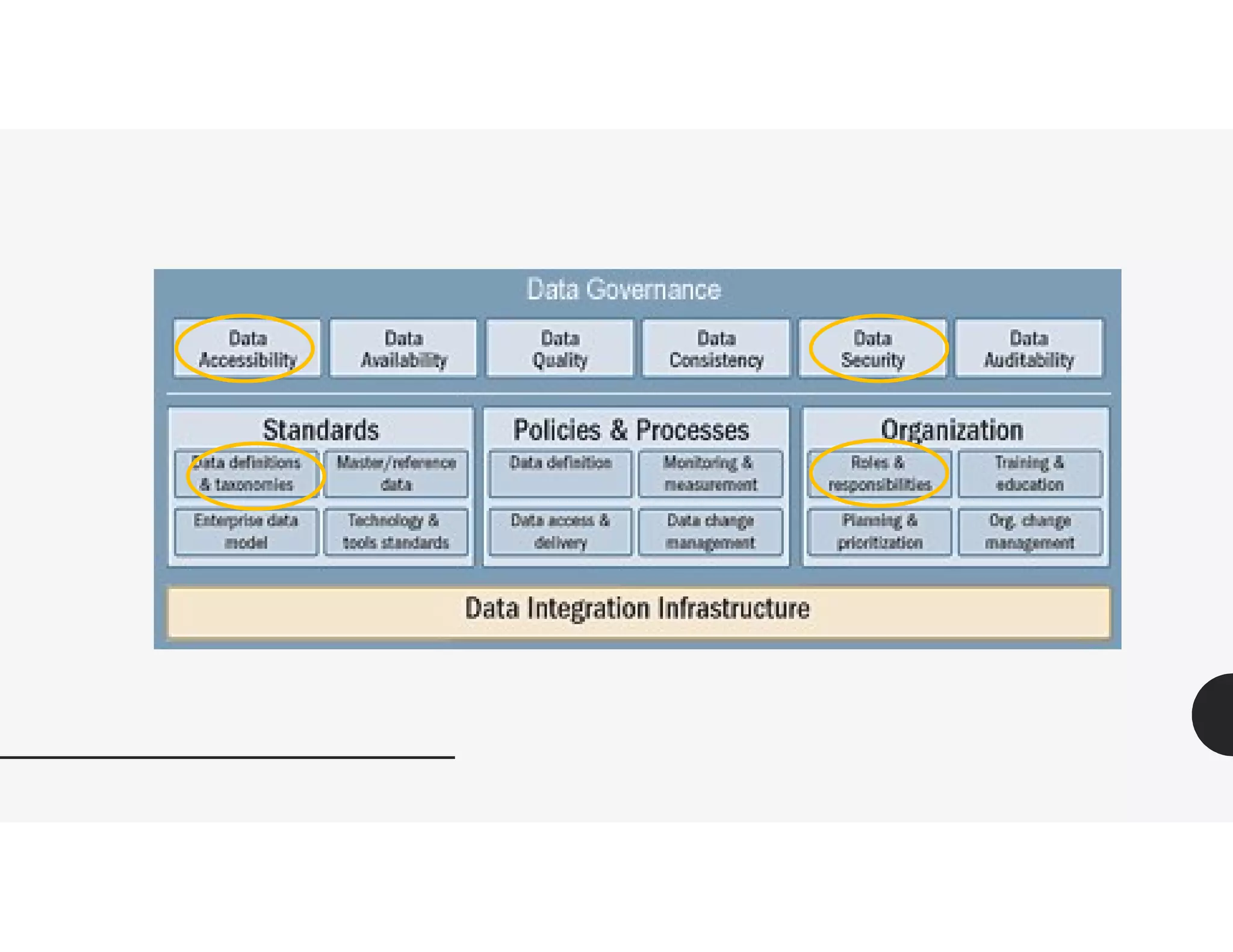
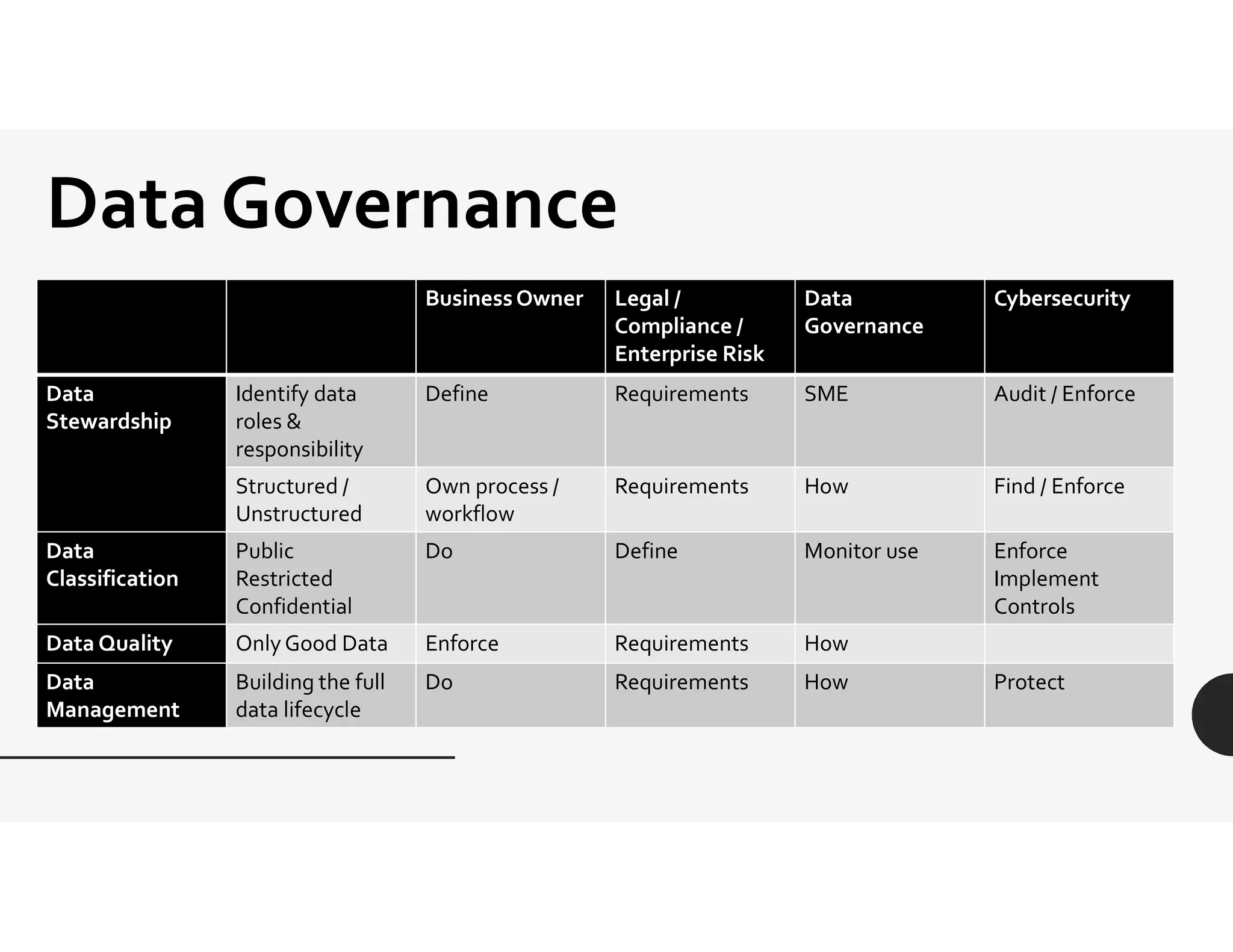
This document provides an overview of challenges related to deidentifying and masking data. It begins with a disclaimer and then lists topics to be covered, including capturing requirements, definitions and terminology, and data governance roles and responsibilities. Definitions of protected health information and personally identifiable information are given. The document discusses Idaho data breach laws and notification requirements. Techniques for data masking like substitution, shuffling, and encryption are defined. Links to resources on deidentification, data masking, and data privacy are provided.