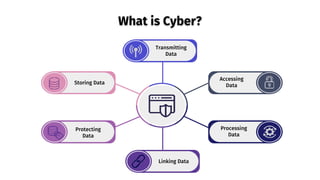
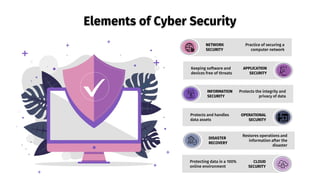
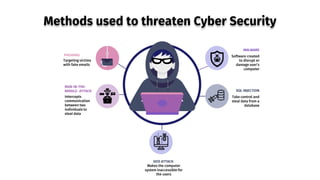
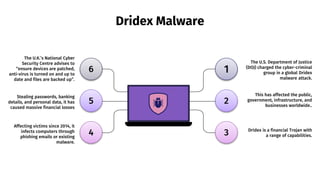
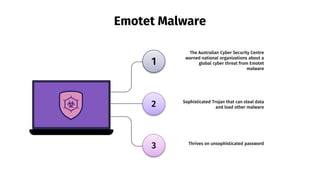
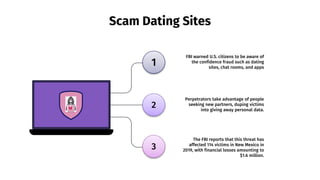
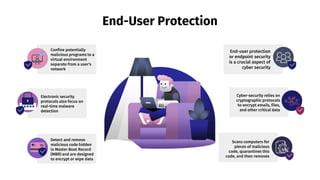
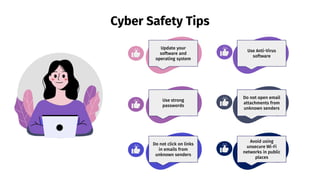
The document provides an overview of cyber security, defining it as the protection of networks, devices, programs, and data from unauthorized access and attacks. It discusses various elements of cyber security, types of cyber threats, and highlights the latest threats like Dridex and Emotet malware. Additionally, it offers end-user protection tips and emphasizes the importance of cyber security in safeguarding sensitive data across multiple sectors.