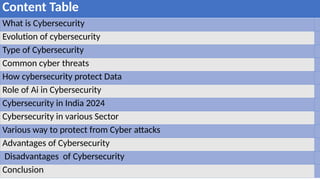
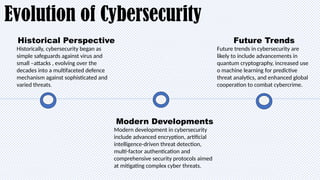
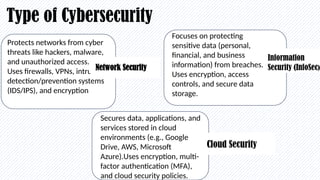
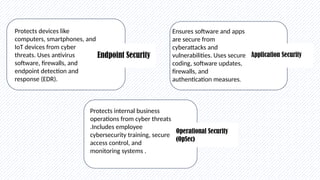
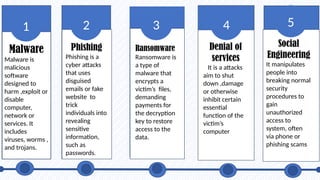
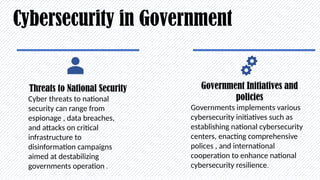
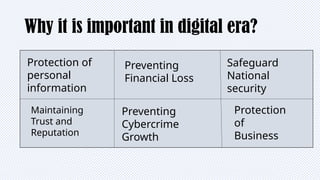
In today’s digital world, cybersecurity is more important than ever. This presentation explores the basics of cybersecurity, common cyber threats, and best practices for staying safe online. Designed specifically for students, it provides practical tips on protecting personal data, avoiding cyber scams, and understanding the role of cybersecurity in our daily lives.
Stay informed.
Stay safe. Be cyber-smart!