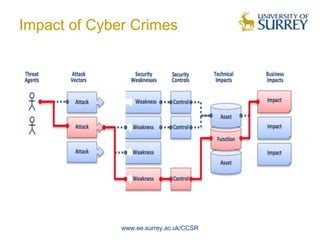
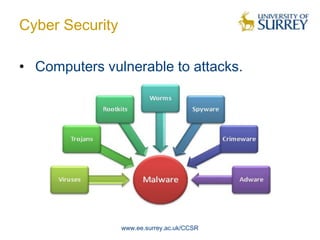
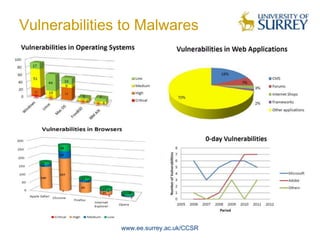
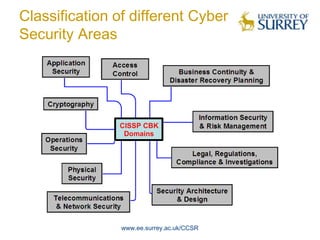
The document discusses trends in cyber security and the global cyber security landscape. It begins with a brief history of cyber security, then discusses current areas of cyber security including vulnerabilities, malware, and classifications. The presentation also covers future trends, policies of different regions, and top roles in cyber security. It aims to provide an overview of the cyber security domain and issues nations face in global cyber warfare.