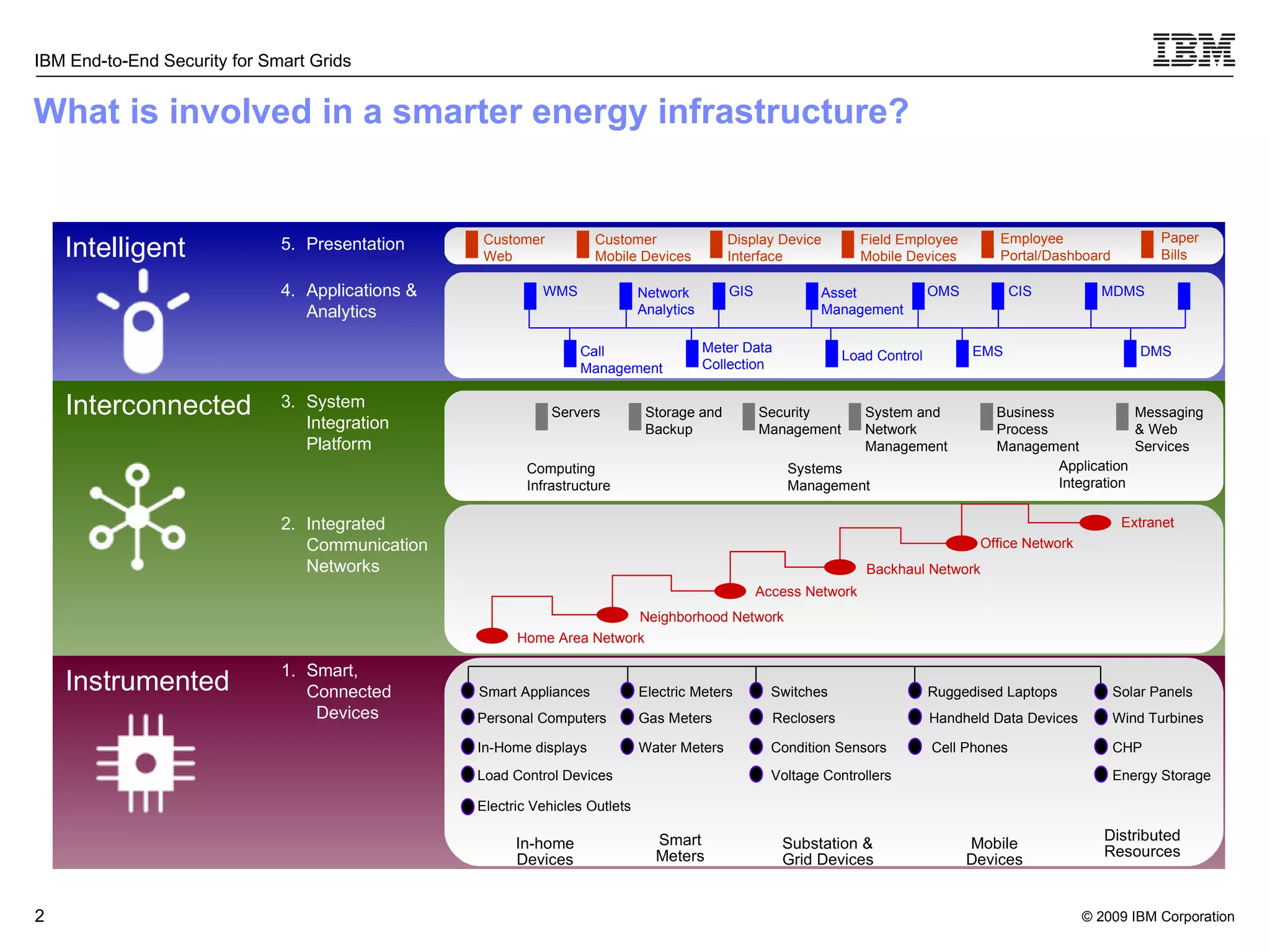
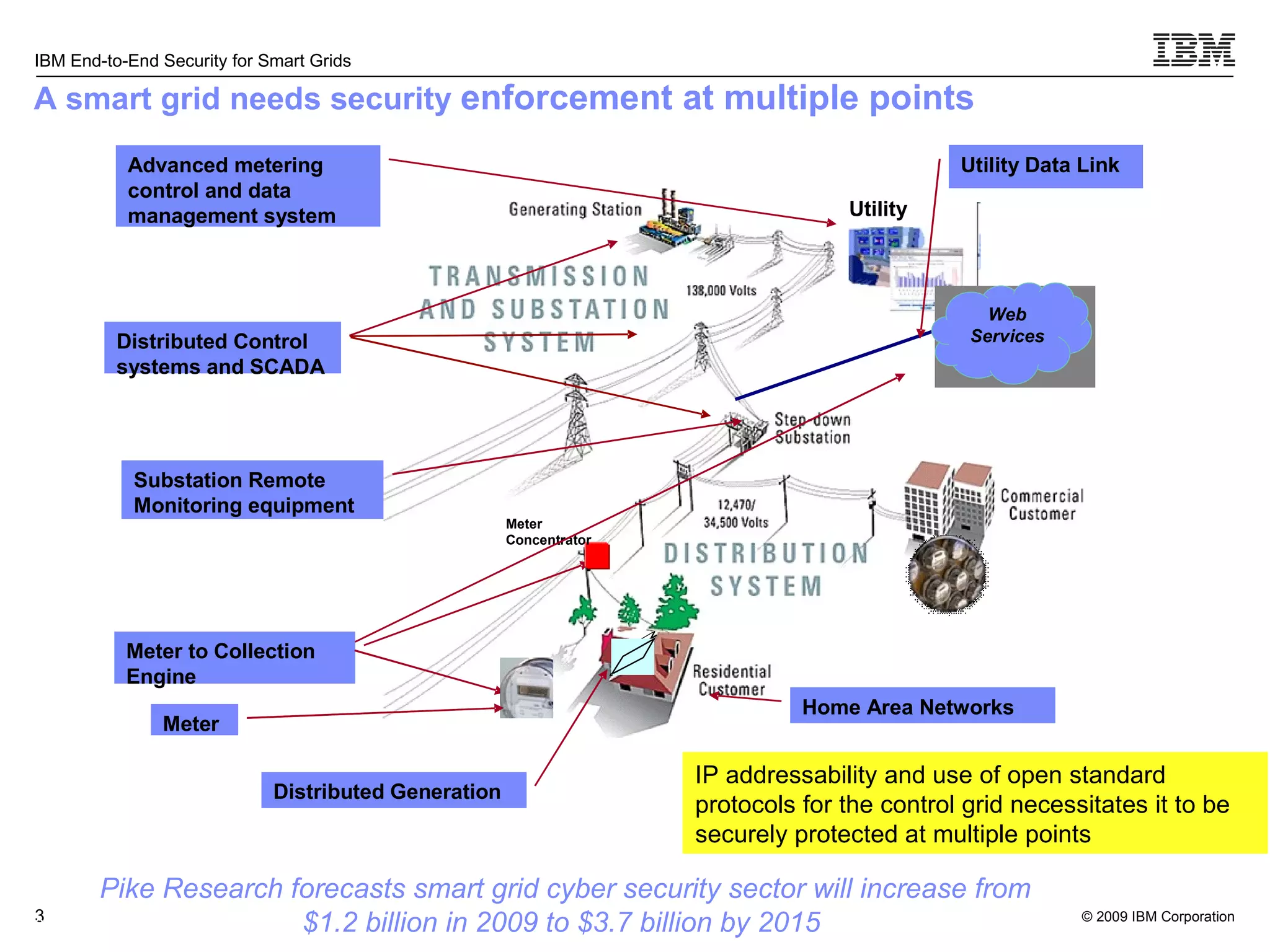
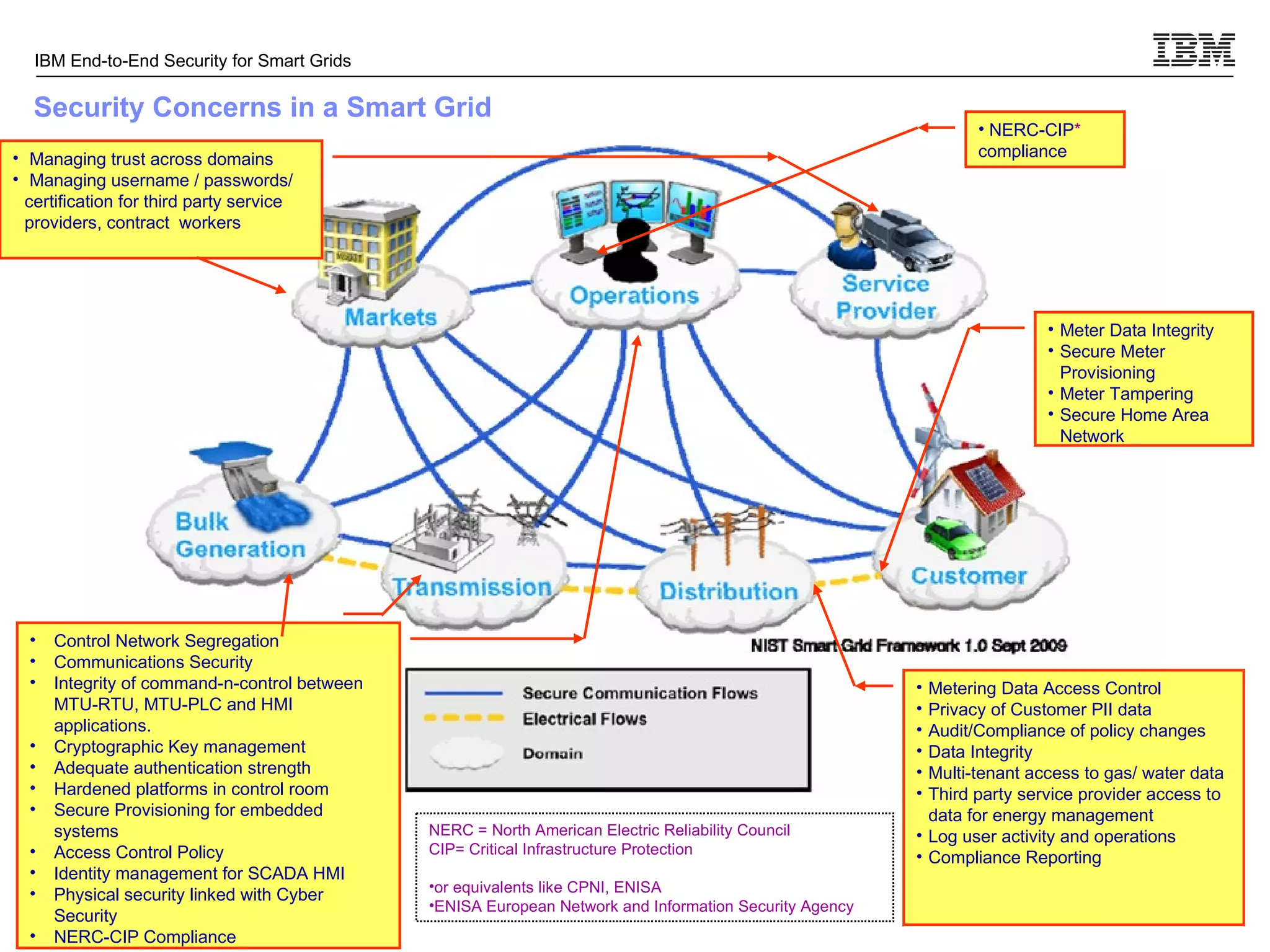
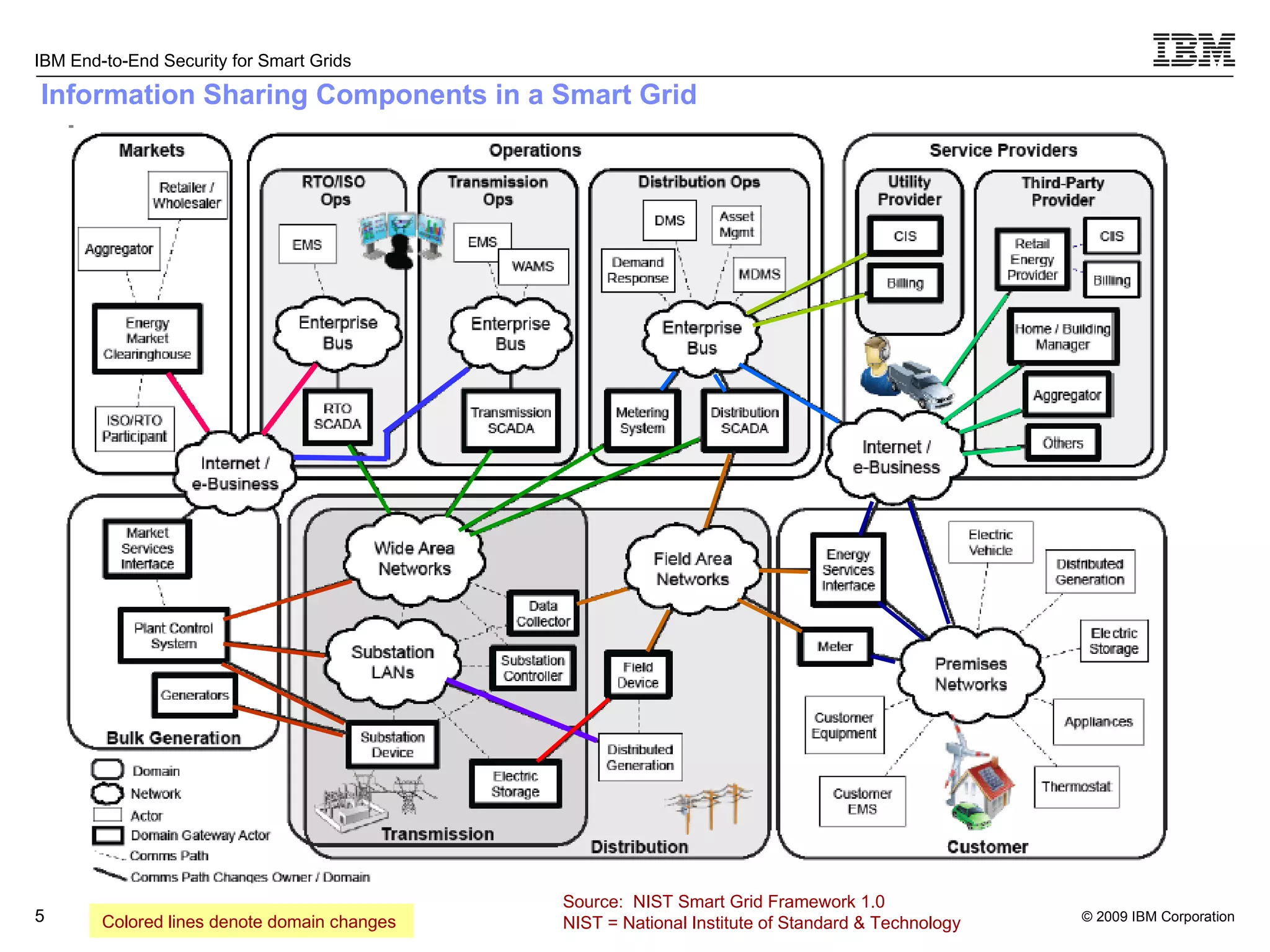
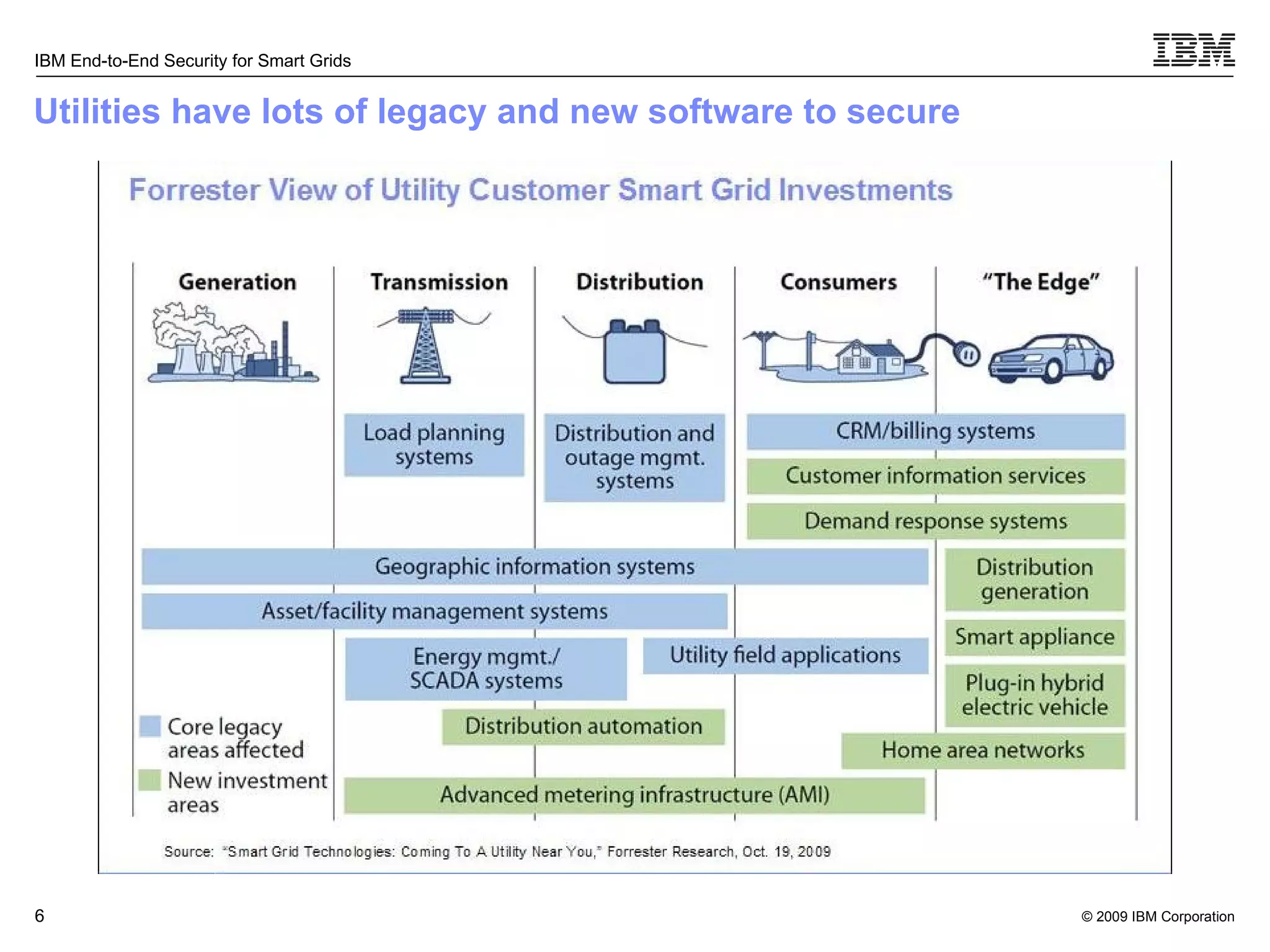
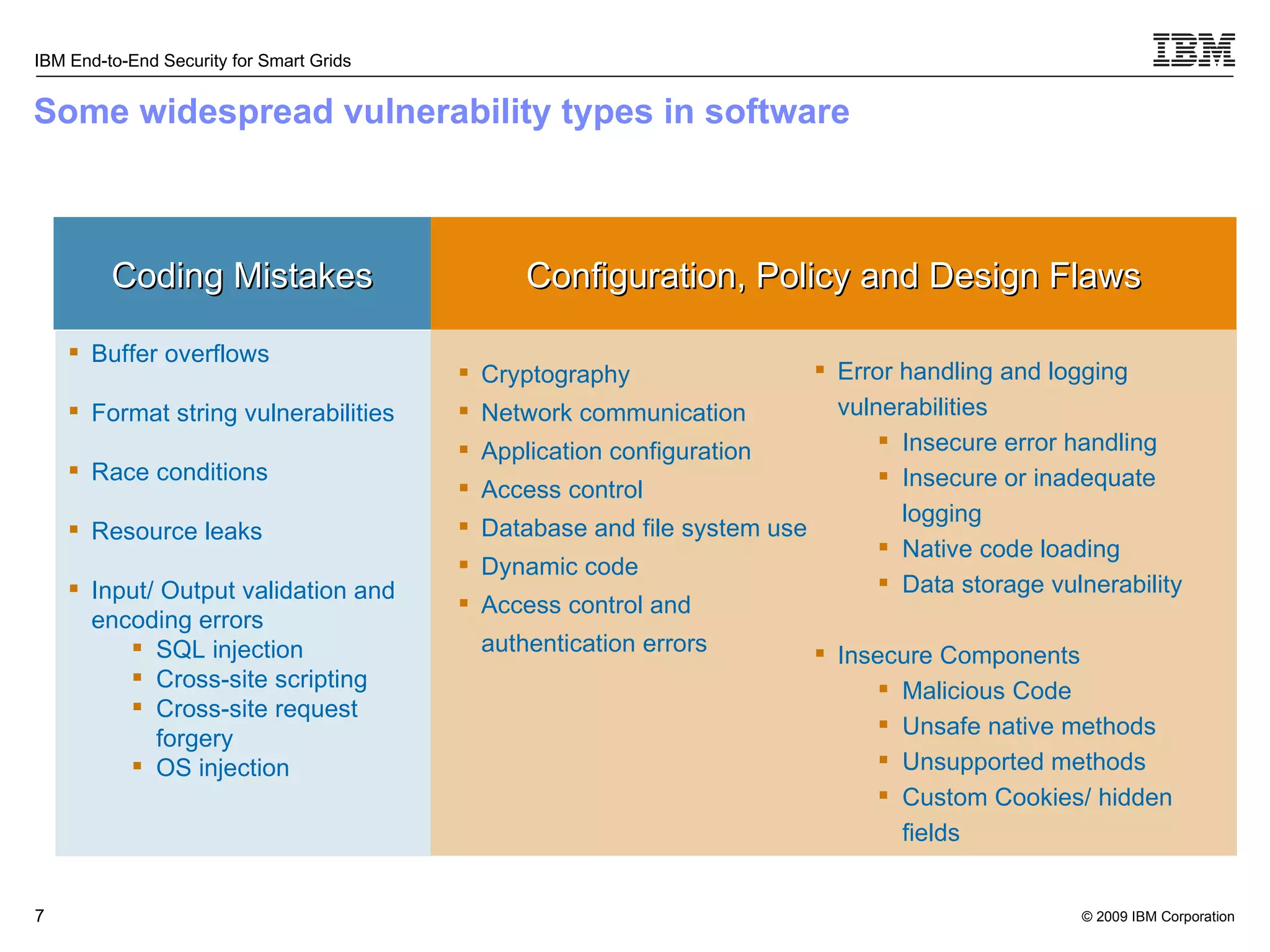
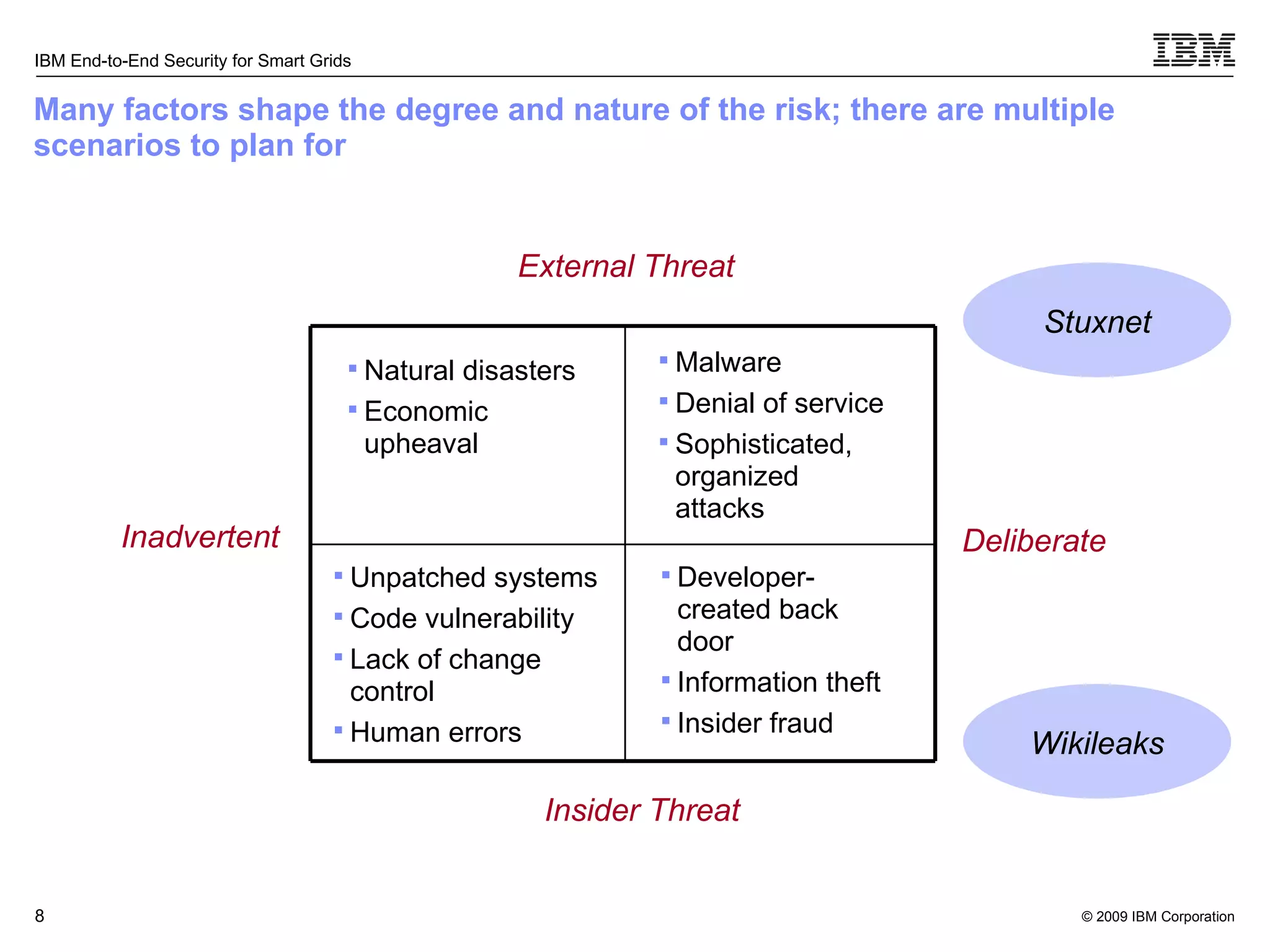
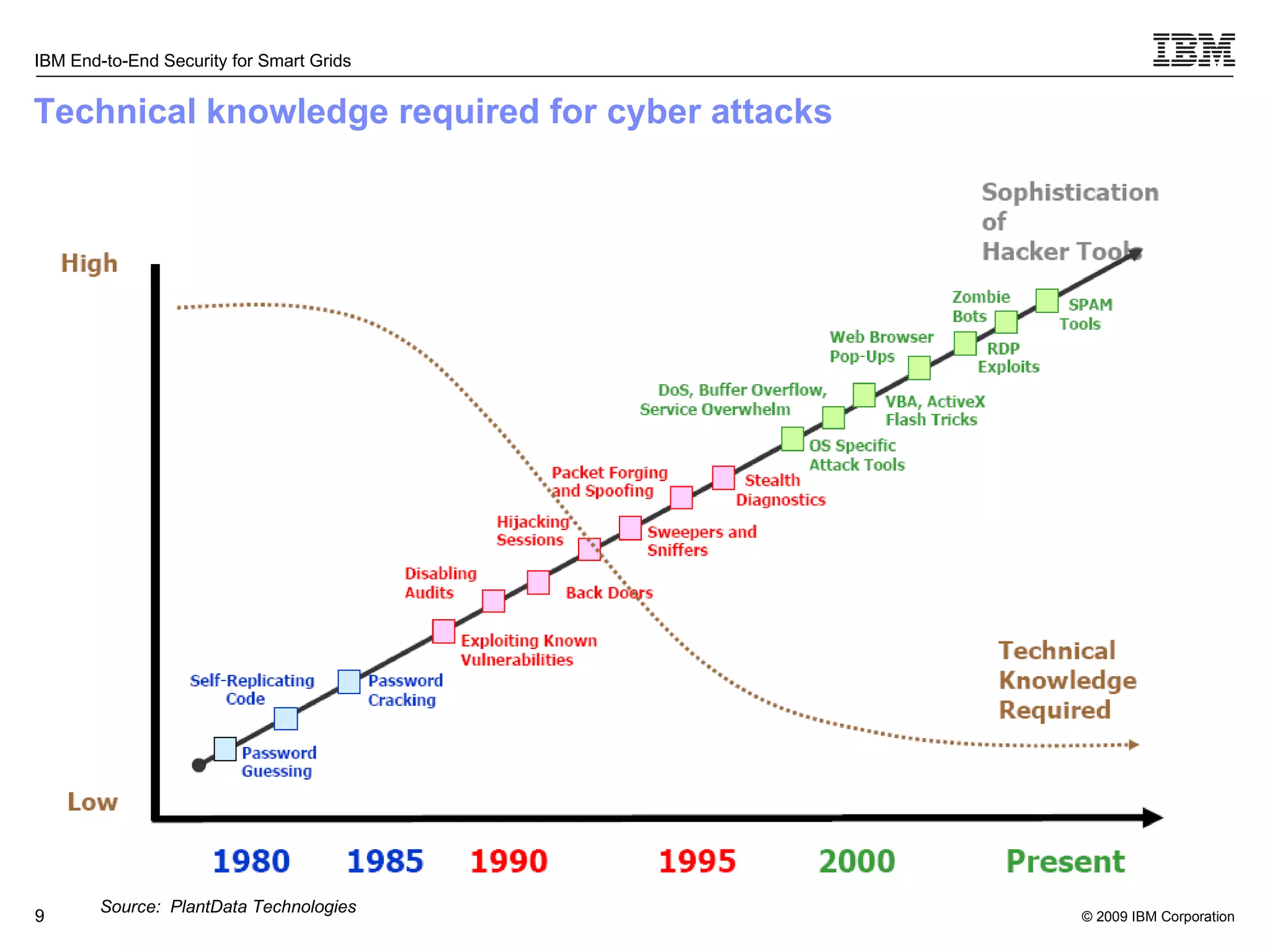
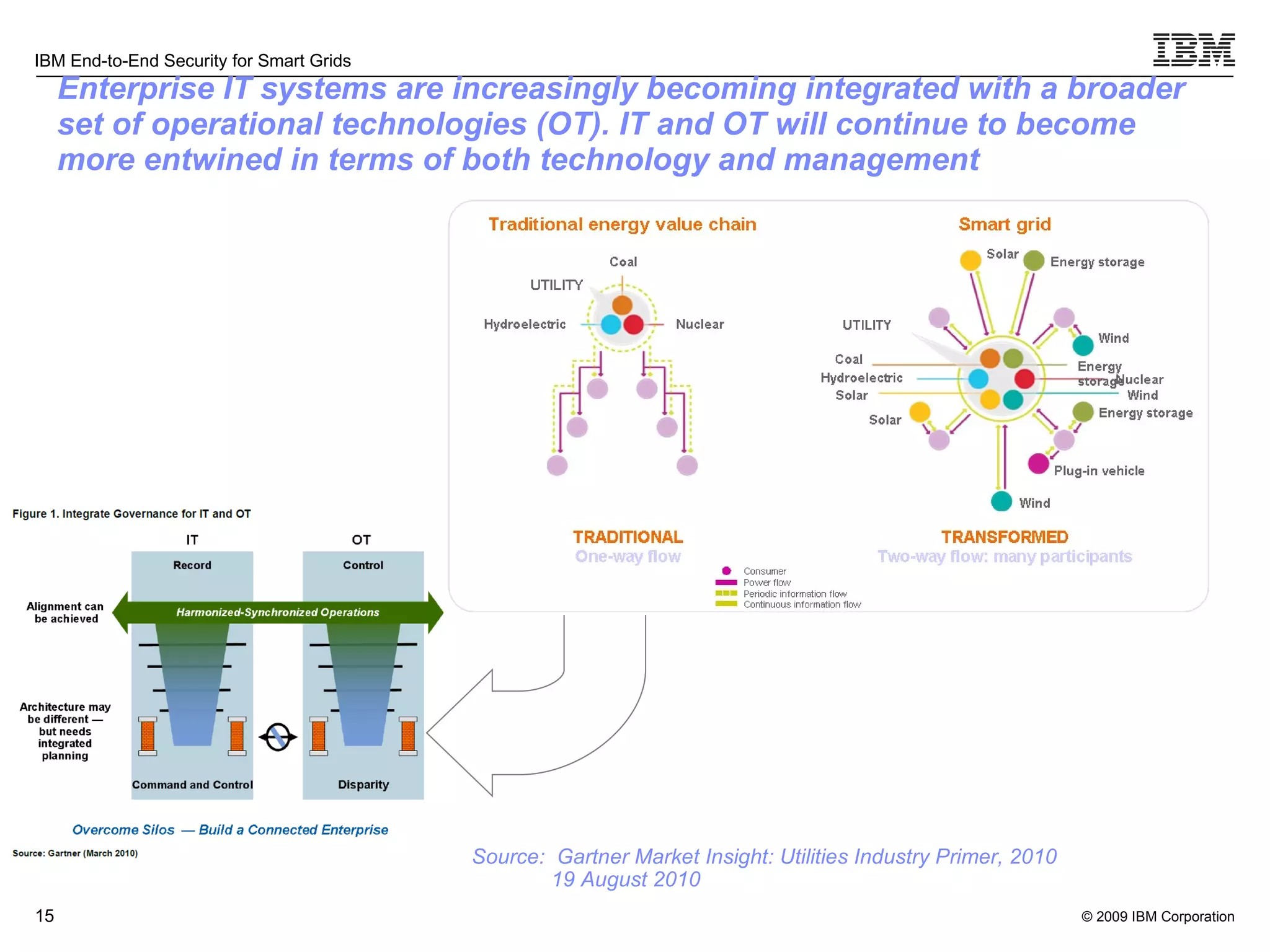
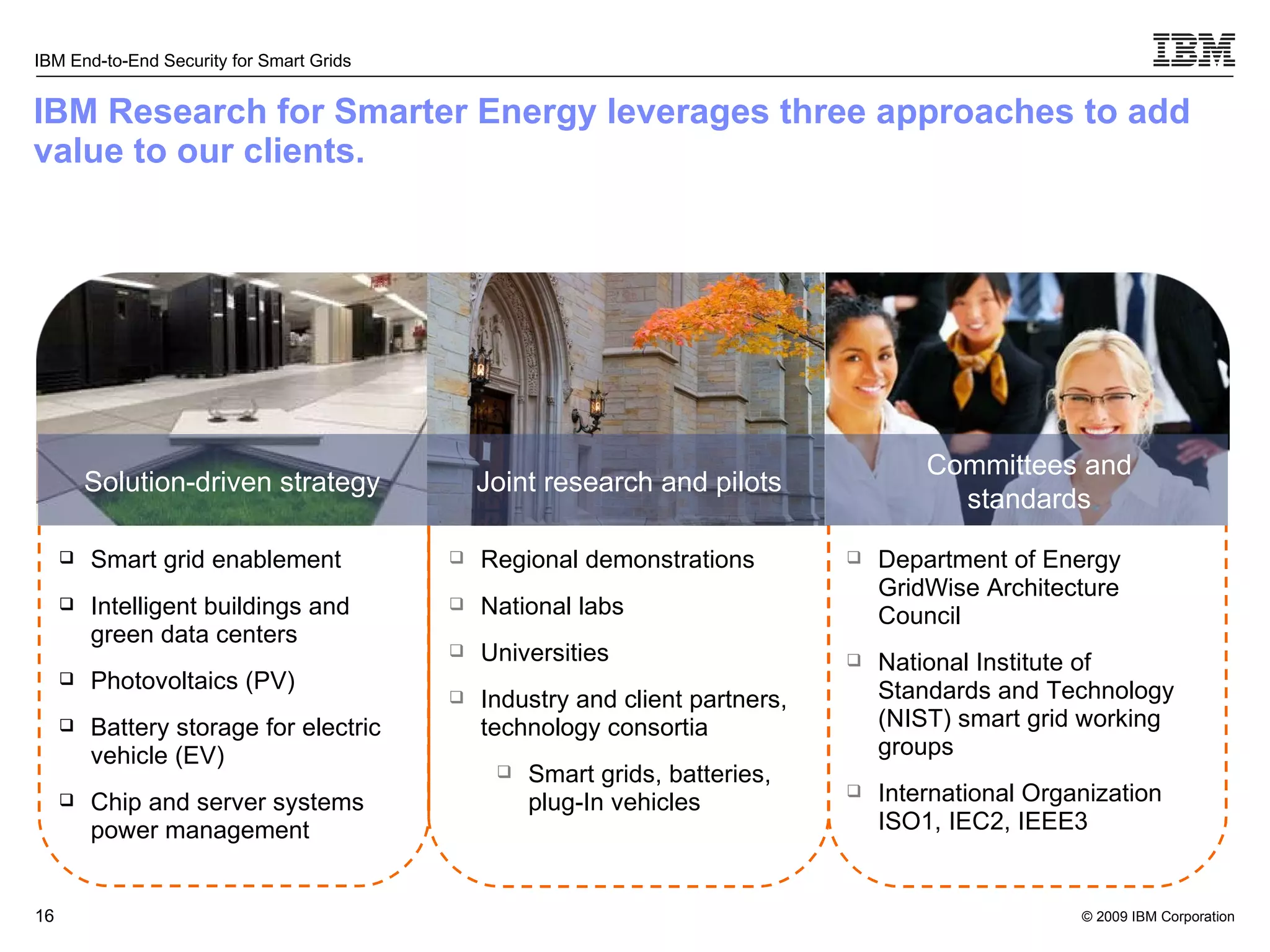
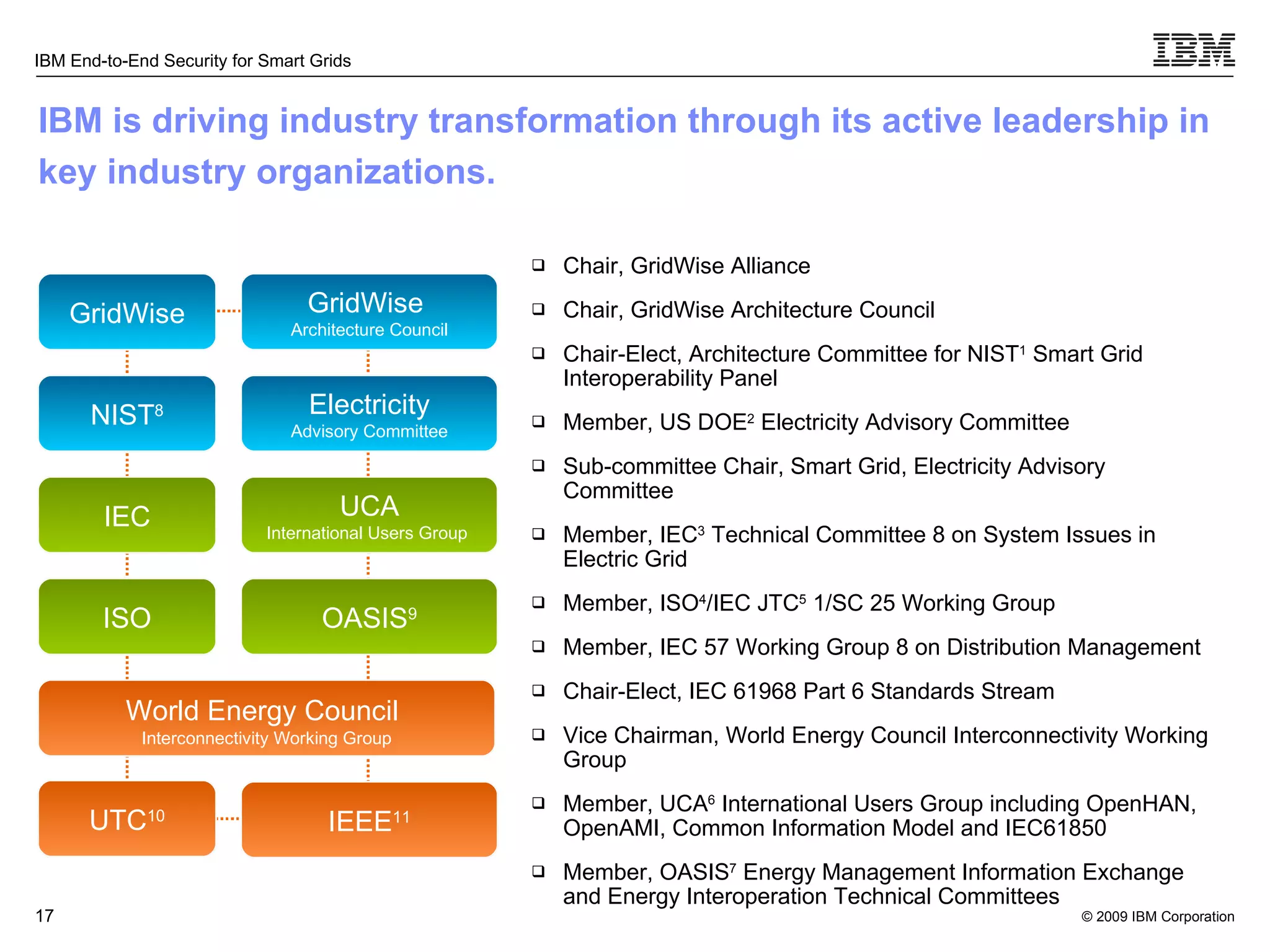
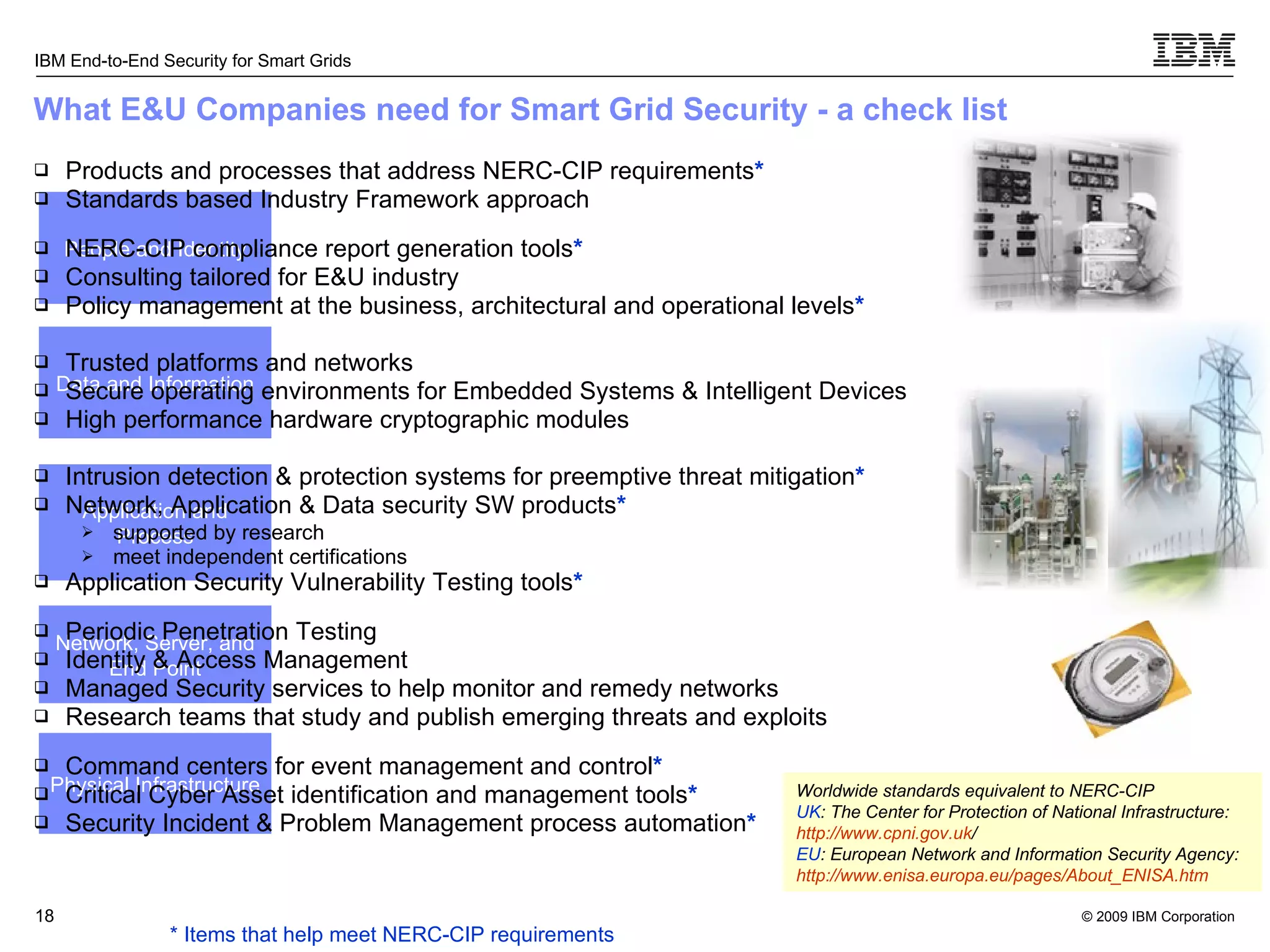
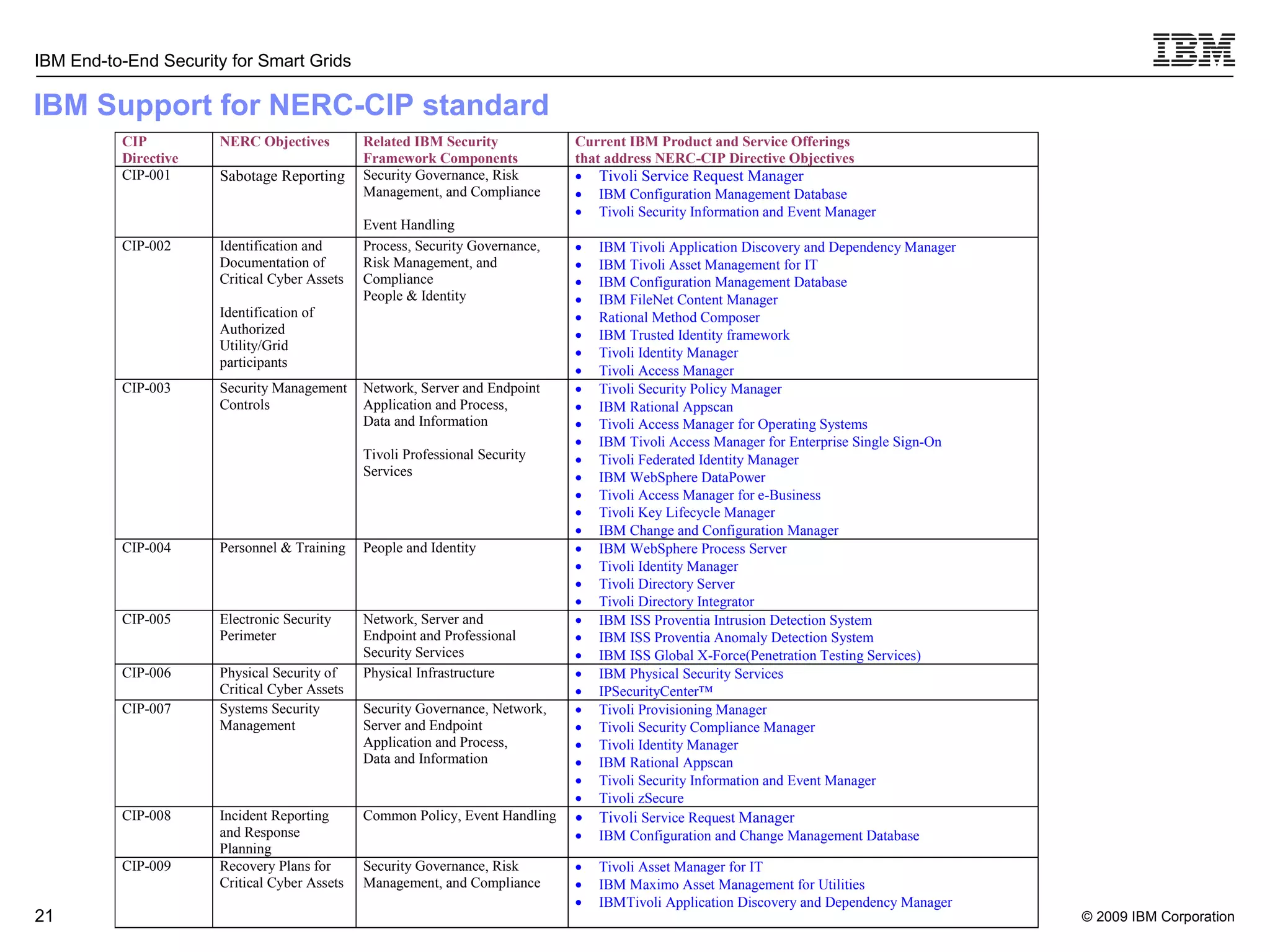
The document discusses security concerns for smart grids and outlines IBM's approach to addressing these concerns. It notes that smart grids require security at multiple points due to their use of IP protocols and open standards. It then lists IBM's portfolio of cybersecurity solutions for smart grids, which take a full lifecycle approach from defining security strategies to conducting security testing. The solutions are designed to help utilities meet NERC-CIP and other grid security standards.