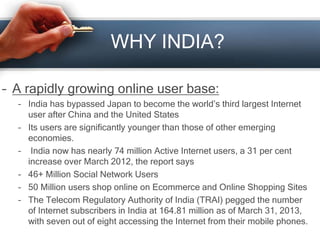
Cyber crime is a growing problem in India as internet usage increases. There are various types of cyber crimes like hacking, denial of service attacks, and software piracy. India is a major target for phishing scams due to its large number of internet and mobile users. The government has enacted laws like the Information Technology Act 2000 to combat cyber crimes. Individuals should take safety precautions like using antivirus software and firewalls to protect themselves from cyber criminals.