The document discusses current trends in data security. It begins by defining data security and its goals of confidentiality and integrity. Traditional SQL-based access control and views are described as having limitations. Two main attacks are discussed: SQL injection due to poor application implementation of security policies, and unintended information leakage when published data is combined from multiple sources. Current research topics aim to address leakage, enforce complex privacy policies, and allow secure sharing of data through techniques like encryption and secure computation. The challenges of moving policy implementation closer to the database are also discussed.





![6
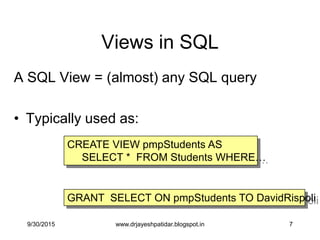
Access Control in SQL
GRANT privileges ON object TO users
[WITH GRANT OPTIONS]
privileges = SELECT | INSERT | DELETE | . . .
object = table | attribute
REVOKE privileges ON object FROM users
[CASCADE ]
[Griffith&Wade'76, Fagin'78]
9/30/2015 www.drjayeshpatidar.blogspot.in](https://image.slidesharecdn.com/currenttrendsindatasecuritynursingresearchppt-150930050904-lva1-app6891/85/Current-trends-in-data-security-nursing-research-ppt-6-320.jpg)

![9
Summary (cont)
• Most policies in middleware: slow, error
prone:
– SAP has 10**4 tables
– GTE over 10**5 attributes
– A brokerage house has 80,000 applications
– A US government entity thinks that it has 350K
• Today the database is not at the center of the
policy administration universe
[Rosenthal&Winslett‟2004]
9/30/2015 www.drjayeshpatidar.blogspot.in](https://image.slidesharecdn.com/currenttrendsindatasecuritynursingresearchppt-150930050904-lva1-app6891/85/Current-trends-in-data-security-nursing-research-ppt-9-320.jpg)
![10
Security in Statistical DBs
Goal:
• Allow arbitrary aggregate SQL queries
• Hide confidential data
SELECT count(*)
FROM Patients
WHERE age=42
and sex=„M‟
and diagnostic=„schizophrenia‟
OK
SELECT name
FROM Patient
WHERE age=42
and sex=„M‟
and diagnostic=„schizophrenia‟
[Adam&Wortmann‟89]
9/30/2015 www.drjayeshpatidar.blogspot.in](https://image.slidesharecdn.com/currenttrendsindatasecuritynursingresearchppt-150930050904-lva1-app6891/85/Current-trends-in-data-security-nursing-research-ppt-10-320.jpg)
![11
Security in Statistical DBs
What has been tried:
• Query restriction
– Query-size control, query-set overlap control, query
monitoring
– None is practical
• Data perturbation
– Most popular: cell combination, cell suppression
– Other methods, for continuous attributes: may introduce bias
• Output perturbation
– For continuous attributes only
[Adam&Wortmann‟89]
9/30/2015 www.drjayeshpatidar.blogspot.in](https://image.slidesharecdn.com/currenttrendsindatasecuritynursingresearchppt-150930050904-lva1-app6891/85/Current-trends-in-data-security-nursing-research-ppt-11-320.jpg)


![14
Search claims by:
SQL Injection
Your health insurance company lets you see the claims online:
Now search through the claims :
Dr. Lee
First login: User:
Password:
fred
********
SELECT…FROM…WHERE doctor=„Dr. Lee‟ and patientID=„fred‟
[Chris Anley, Advanced SQL Injection In SQL]
9/30/2015 www.drjayeshpatidar.blogspot.in](https://image.slidesharecdn.com/currenttrendsindatasecuritynursingresearchppt-150930050904-lva1-app6891/85/Current-trends-in-data-security-nursing-research-ppt-14-320.jpg)










![25
First Last Age Race
Harry Stone 34 Afr-Am
John Reyser 36 Cauc
Beatrice Stone 47 Afr-am
John Ramos 22 Hisp
First Last Age Race
* Stone 30-50 Afr-Am
John R* 20-40 *
* Stone 30-50 Afr-am
John R* 20-40 *
Information Leakage:
k-Anonymity
Definition: each tuple is equal to at least k-1 others
Anonymizing: through suppression and generalization
Hard: NP-complete for supression only
Approximations exists
[Samarati&Sweeney‟98, Meyerson&Williams‟04]
9/30/2015 www.drjayeshpatidar.blogspot.in](https://image.slidesharecdn.com/currenttrendsindatasecuritynursingresearchppt-150930050904-lva1-app6891/85/Current-trends-in-data-security-nursing-research-ppt-25-320.jpg)
![26
Information Leakage:
Query-view Security
Secret Query View(s)
Disclosure
?
S(name) V(name,phone)
S(name,phone)
V1(name,dept)
V2(dept,phone)
S(name) V(dept)
S(name)
where
dept=„HR‟
V(name)
where
dept=„RD‟
TABLE Employee(name, dept, phone)Have data:
total
big
tiny
none
[Miklau&S‟04, Miklau&Dalvi&S‟05,Yang&Li‟04]
9/30/2015 www.drjayeshpatidar.blogspot.in](https://image.slidesharecdn.com/currenttrendsindatasecuritynursingresearchppt-150930050904-lva1-app6891/85/Current-trends-in-data-security-nursing-research-ppt-26-320.jpg)
![27
Summary on Information
Disclosure
• The theoretical research:
– Exciting new connections between
databases and information theory,
probability theory, cryptography
• The applications:
– many years away
[Abadi&Warinschi‟05]
9/30/2015 www.drjayeshpatidar.blogspot.in](https://image.slidesharecdn.com/currenttrendsindatasecuritynursingresearchppt-150930050904-lva1-app6891/85/Current-trends-in-data-security-nursing-research-ppt-27-320.jpg)
![28
Privacy
• “Is the right of individuals to determine
for themselves when, how and to what
extent information about them is
communicated to others”
• More complex than confidentiality
[Agrawal‟03]
9/30/2015 www.drjayeshpatidar.blogspot.in](https://image.slidesharecdn.com/currenttrendsindatasecuritynursingresearchppt-150930050904-lva1-app6891/85/Current-trends-in-data-security-nursing-research-ppt-28-320.jpg)
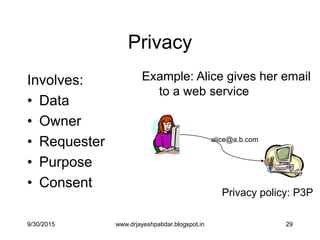
![30
Hippocratic Databases
DB support for implementing privacy
policies.
• Purpose specification
• Consent
• Limited use
• Limited retention
• …
[Agrawal‟03, LeFevrey‟04]
alice@a.b.com
Privacy policy: P3P
Hippocratic DB
Protection against:
Sloppy organizations
Malicious organizations
9/30/2015 www.drjayeshpatidar.blogspot.in](https://image.slidesharecdn.com/currenttrendsindatasecuritynursingresearchppt-150930050904-lva1-app6891/85/Current-trends-in-data-security-nursing-research-ppt-30-320.jpg)
![31
Privacy for Paranoids
• Idea: rely on trusted agents
alice@a.b.com
Agent
aly1@agenthost.com
lice27@agenthost.com
foreign keys ?
[Aggarwal‟04]
Protection against:
Sloppy organizations
Malicious attackers9/30/2015 www.drjayeshpatidar.blogspot.in](https://image.slidesharecdn.com/currenttrendsindatasecuritynursingresearchppt-150930050904-lva1-app6891/85/Current-trends-in-data-security-nursing-research-ppt-31-320.jpg)

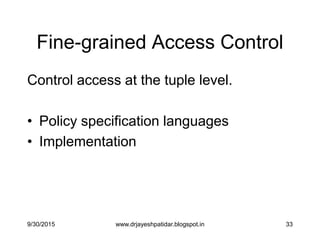


![36
Two Semantics
• The Truman Model = filter semantics
– transform reality
– ACCEPT all queries
– REWRITE queries
– Sometimes misleading results
• The non-Truman model = deny semantics
– reject queries
– ACCEPT or REJECT queries
– Execute query UNCHANGED
– May define multiple security views for a user
[Rizvi‟04]
SELECT count(*)
FROM Patients
WHERE disease=„flu‟
9/30/2015 www.drjayeshpatidar.blogspot.in](https://image.slidesharecdn.com/currenttrendsindatasecuritynursingresearchppt-150930050904-lva1-app6891/85/Current-trends-in-data-security-nursing-research-ppt-36-320.jpg)
![37
Summary of Fine Grained
Access Control
• Trend in industry: label-based security
• Killer app: application hosting
– Independent franchises share a single
table at headquarters (e.g., Holiday Inn)
– Application runs under requester‟s label,
cannot see other labels
– Headquarters runs Read queries over
them
• Oracle‟s Virtual Private Database
[Rosenthal&Winslett‟2004]
9/30/2015 www.drjayeshpatidar.blogspot.in](https://image.slidesharecdn.com/currenttrendsindatasecuritynursingresearchppt-150930050904-lva1-app6891/85/Current-trends-in-data-security-nursing-research-ppt-37-320.jpg)

![39
Data Encryption for Publishing
An XML tree protection:
<patient>
<privateData>
<name> <age>
<diagnostic>
JoeDoe 28
<address>
Seattle
<trial>
<drug>
flu
<placebo>
Kuser
Kpat (Knu Kadm) Knu Kdr
Kdr
Kpat Kmaster Kmaster
Tylenol Candy
[Miklau&S.‟03]
Doctor: Kuser, Kdr
Nurse: Kuser, Knu
Nurse+admin: Kuser, Knu, Kadm
9/30/2015 www.drjayeshpatidar.blogspot.in](https://image.slidesharecdn.com/currenttrendsindatasecuritynursingresearchppt-150930050904-lva1-app6891/85/Current-trends-in-data-security-nursing-research-ppt-39-320.jpg)
![40
Summary on Data Encryption
• Industry:
– Supported by all vendors:
Oracle, DB2, SQL-Server
– Efficiency issues still largely unresolved
• Research:
– Hard theoretical security analysis
[Abadi&Warinschi‟05]
9/30/2015 www.drjayeshpatidar.blogspot.in](https://image.slidesharecdn.com/currenttrendsindatasecuritynursingresearchppt-150930050904-lva1-app6891/85/Current-trends-in-data-security-nursing-research-ppt-40-320.jpg)

![42
Secure Shared Processing
[Agrawal‟03]
Alice Bob
a b c d c d e
h(a) h(b) h(c) h(d) h(c) h(d) h(e)
Compute one-way hash
Exchange
h(c) h(d) h(e) h(a) h(b) h(c) h(d)
What‟s wrong ?
Task: find intersection
without revealing the rest
9/30/2015 www.drjayeshpatidar.blogspot.in](https://image.slidesharecdn.com/currenttrendsindatasecuritynursingresearchppt-150930050904-lva1-app6891/85/Current-trends-in-data-security-nursing-research-ppt-42-320.jpg)
![43
Secure Shared Processing
Alice Bob
a b c d c d e
EB(c) EB(d) EB(e) EA(a) EA(b) EA(c) EA(d)
commutative encryption:
h(x) = EA(EB(x)) = EB(EA(x))
EA(a) EA(b) EA(c) EA(d) EB(c) EB(d) EB(e)
EA EB
h(c) h(d) h(e) h(a) h(b) h(c) h(d)
EA EB
h(a) h(b) h(c) h(d) h(c) h(d) h(e)
[Agrawal‟03]
9/30/2015 www.drjayeshpatidar.blogspot.in](https://image.slidesharecdn.com/currenttrendsindatasecuritynursingresearchppt-150930050904-lva1-app6891/85/Current-trends-in-data-security-nursing-research-ppt-43-320.jpg)





