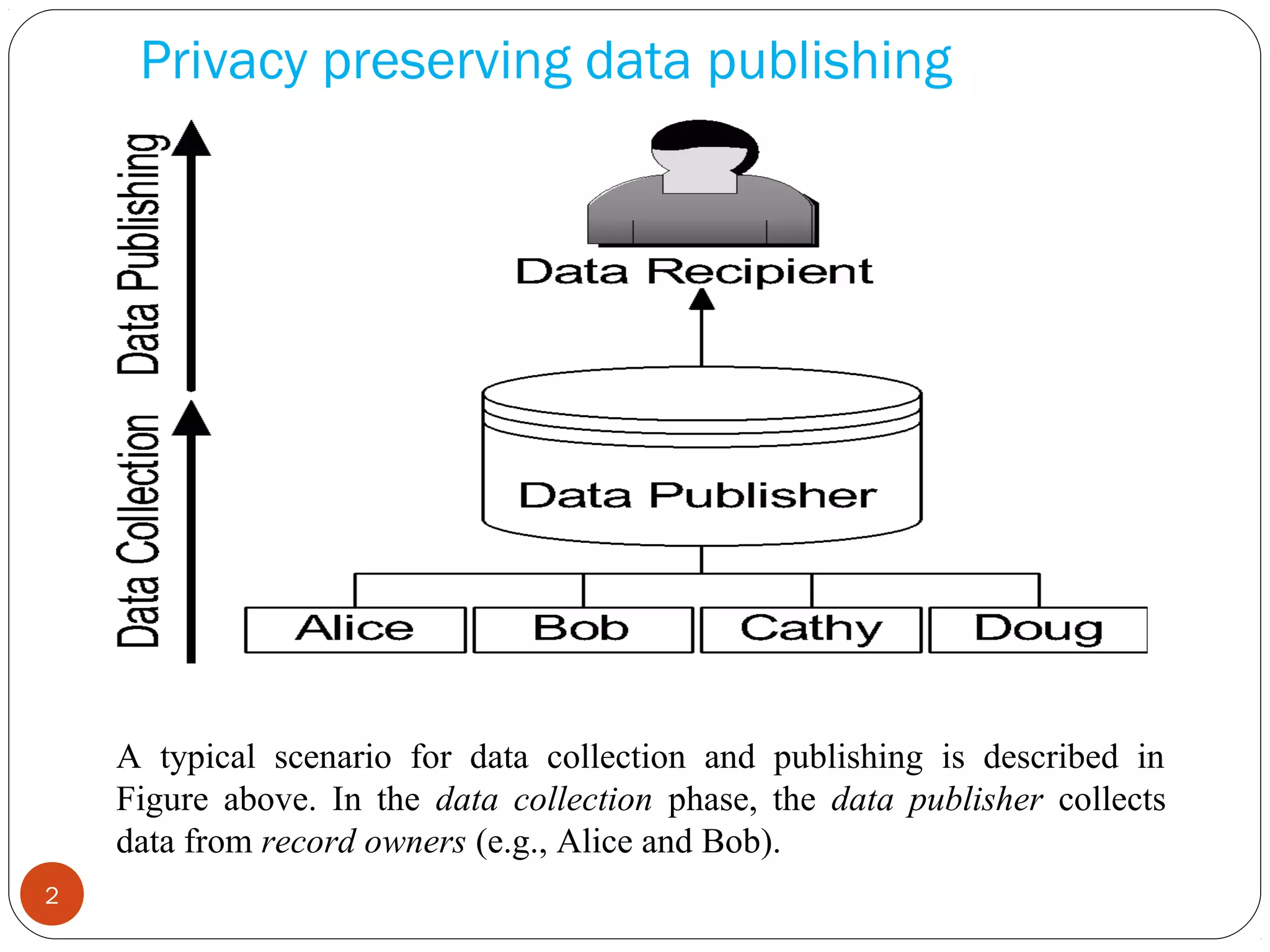
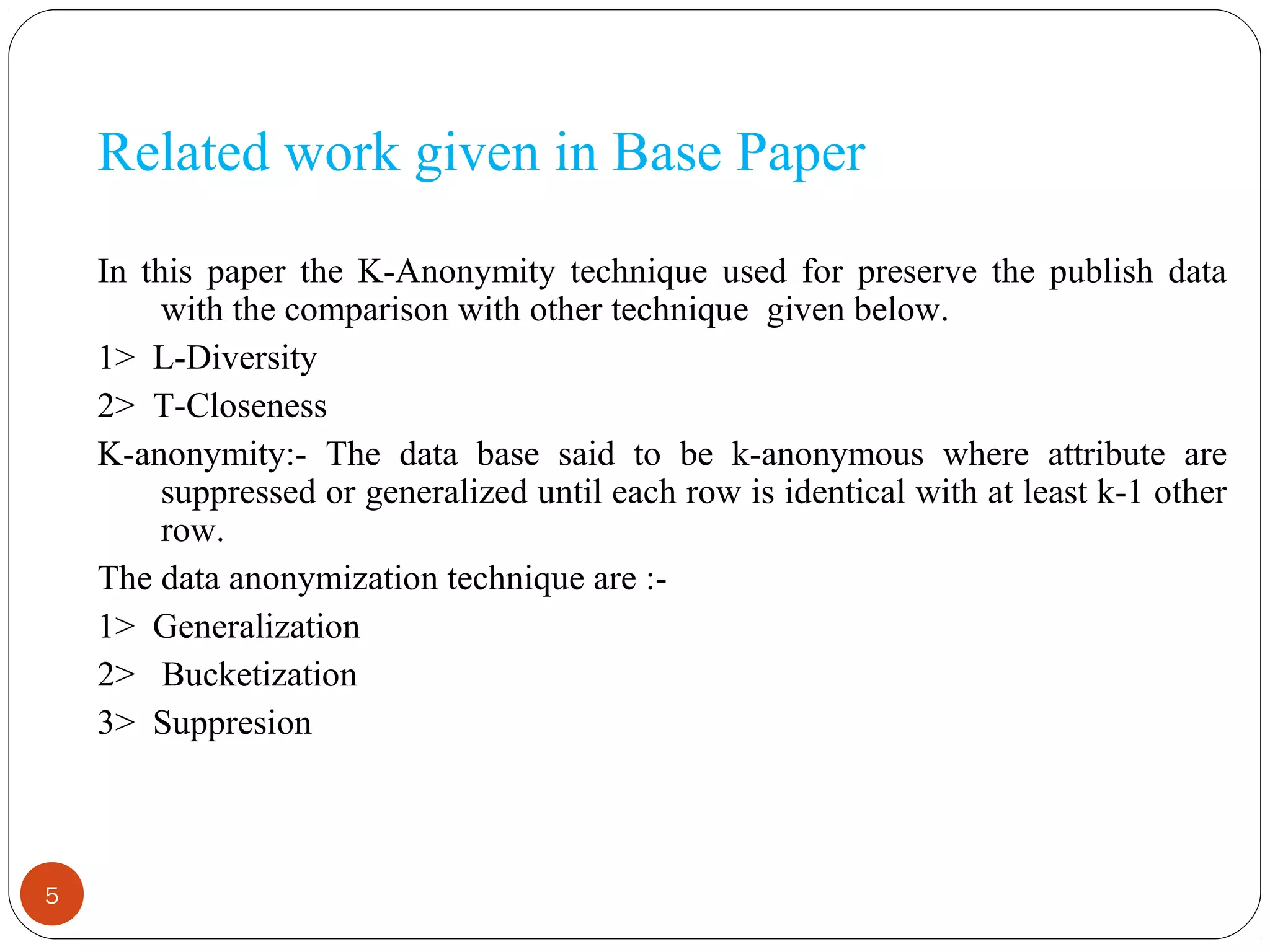
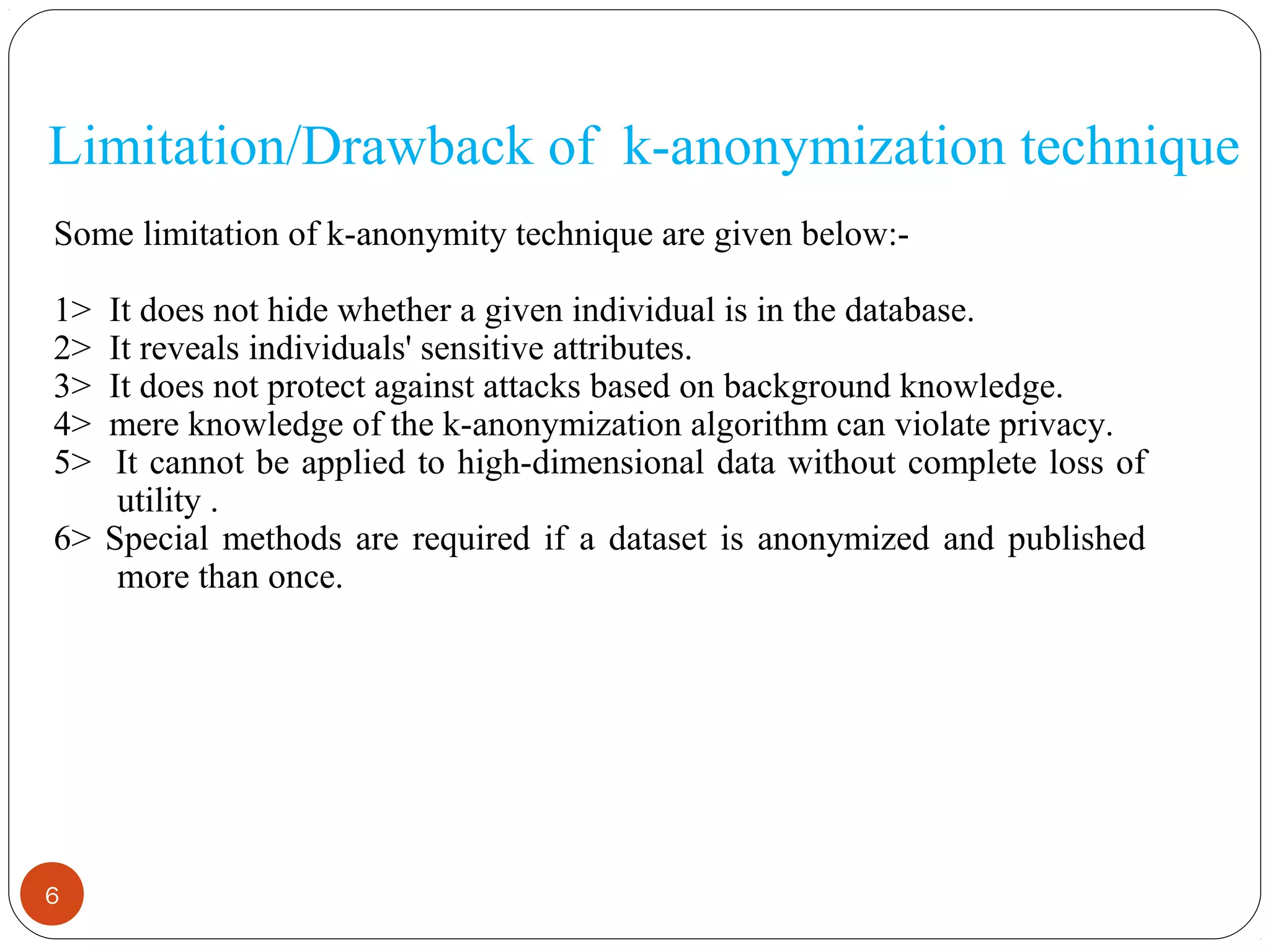
This document summarizes techniques for privacy-preserving data publishing. It discusses k-anonymity, which anonymizes data by suppressing or generalizing attributes until each record is identical to at least k-1 other records. The document also covers limitations of k-anonymity, including that it does not protect against background knowledge attacks. It proposes addressing these limitations by combining k-anonymity with generalization and slicing techniques.