This document provides an agenda and overview for a data protection seminar. It discusses:
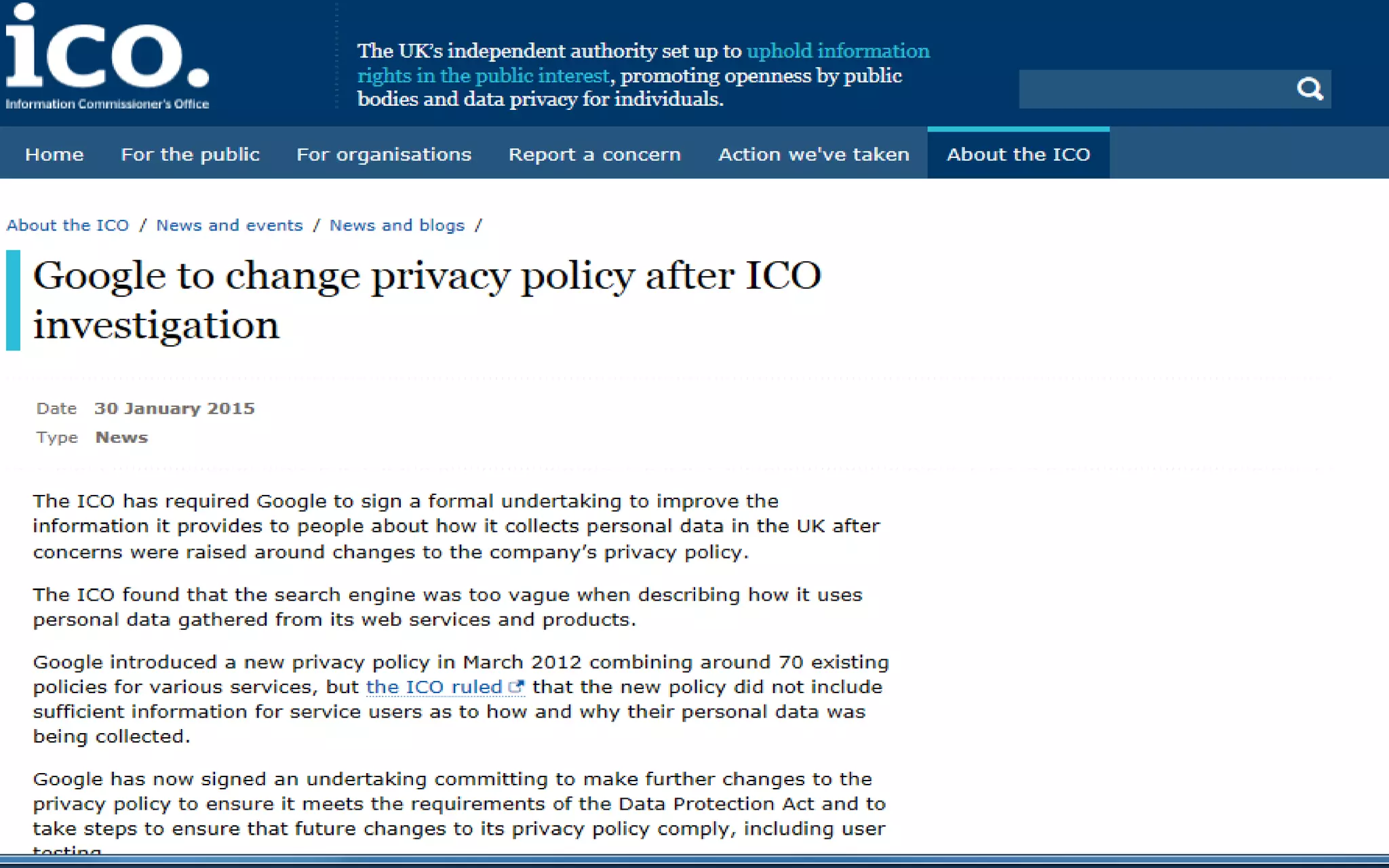
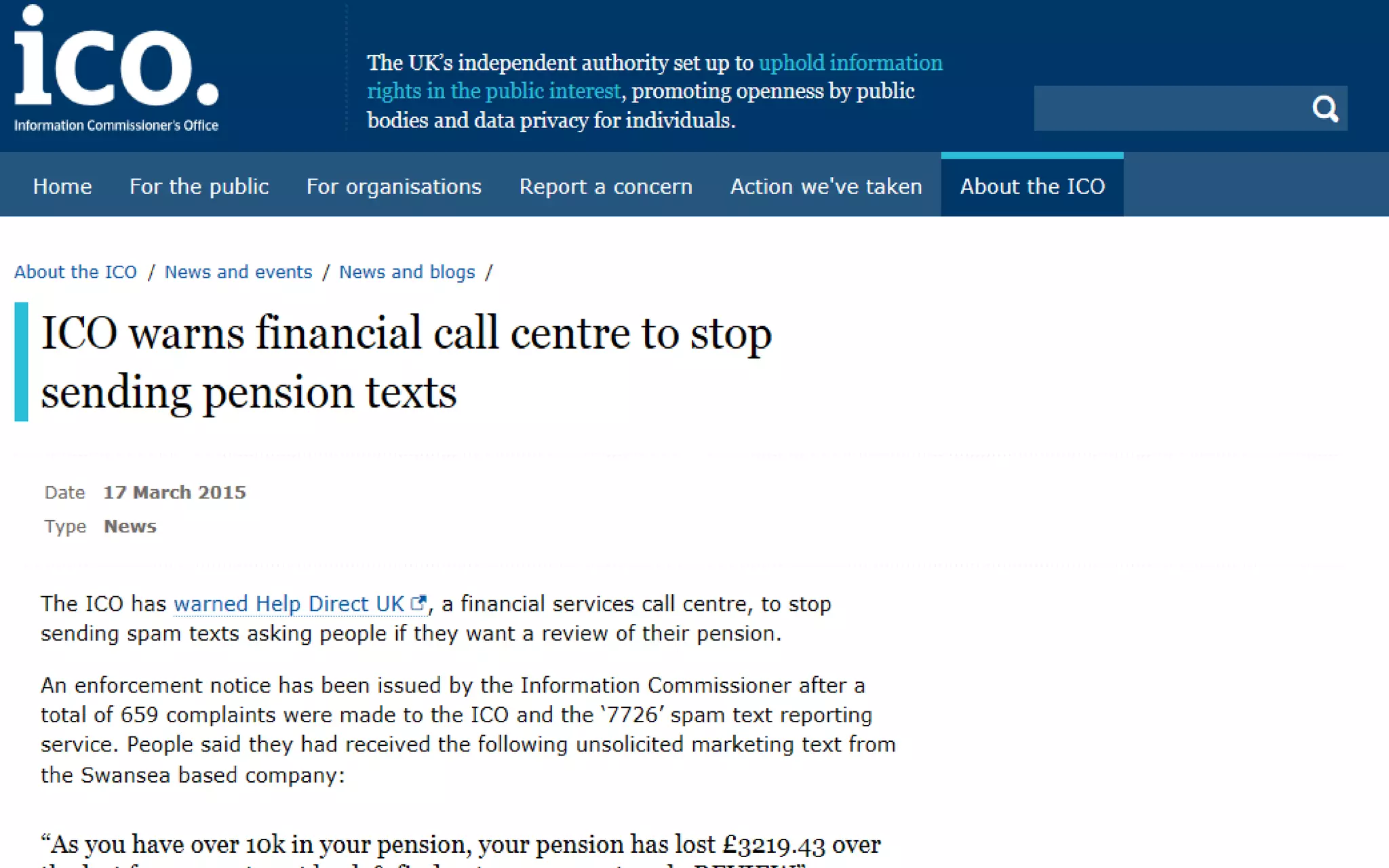
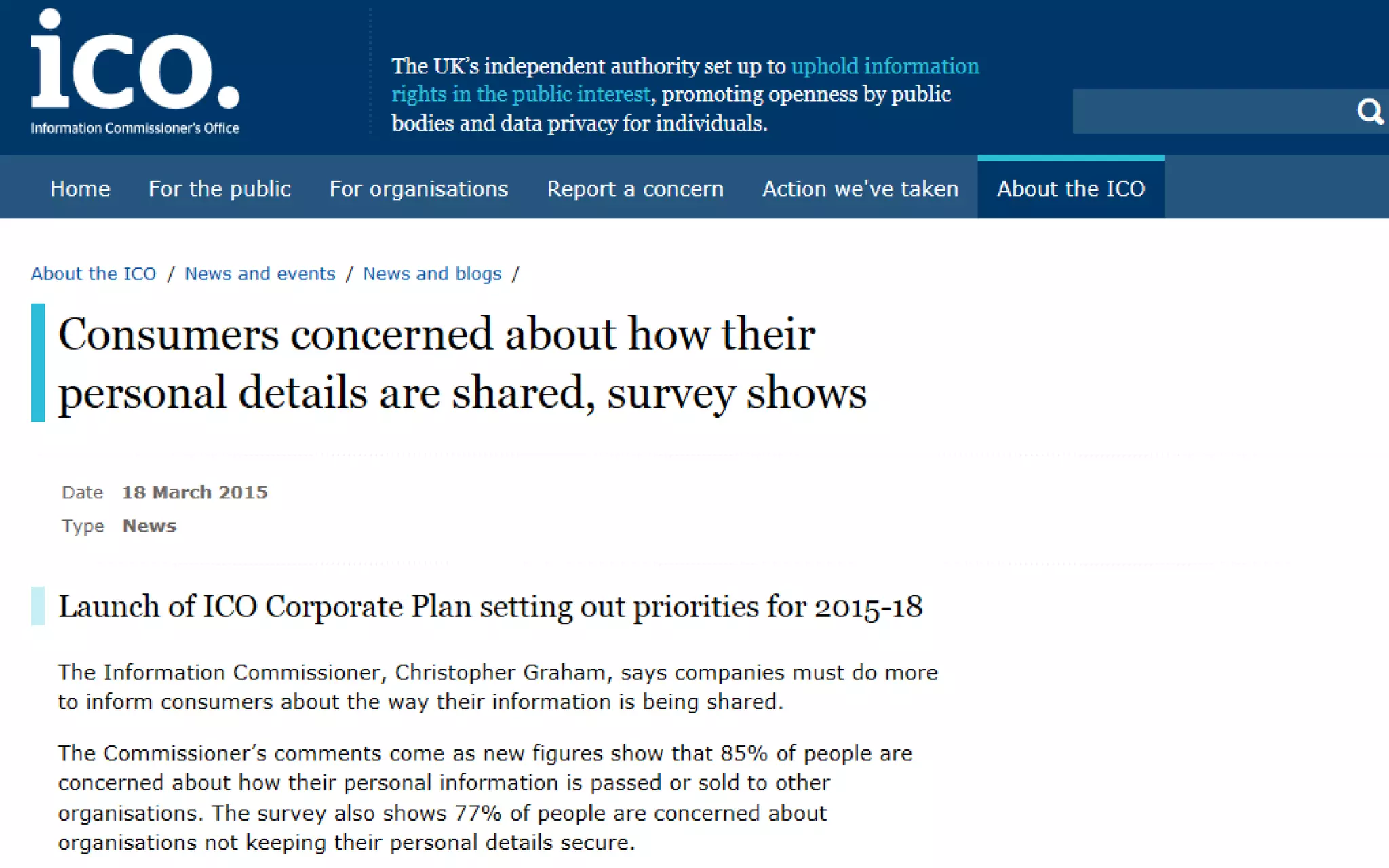
1. Why data protection is important for protecting information, avoiding reputational damage, and avoiding legal penalties.
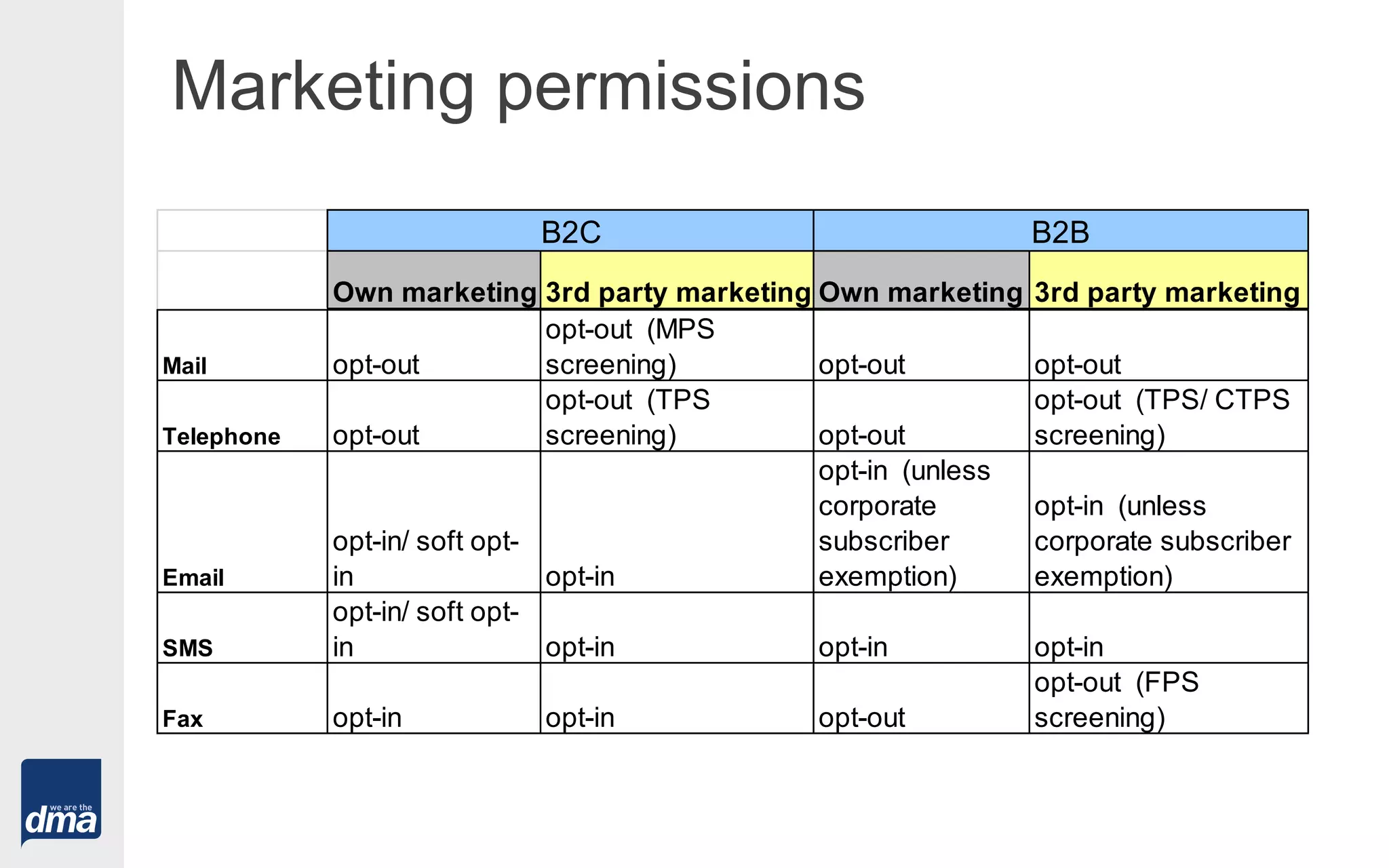
2. An overview of the key UK data protection laws: the Data Protection Act 1998 and the Privacy and Electronic Communications Regulation 2003. It defines important terms, outlines the 8 data protection principles, and reviews key rules around electronic communications.
3. Practical tips for marketers on capturing data, obtaining permissions, sourcing data from third parties, and regaining lost consent.