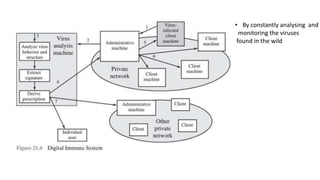
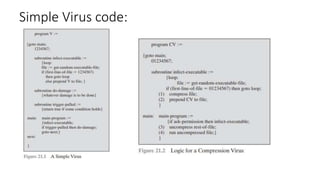
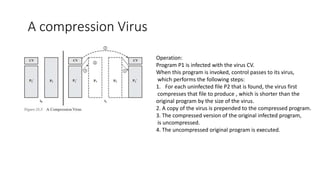
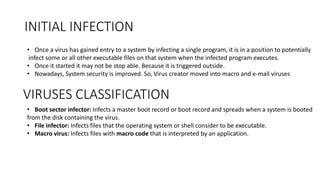
The document provides a comprehensive overview of computer viruses, explaining their definitions, mechanisms, phases of infection, and classification methods, as well as discussing modern virus types such as macro and e-mail viruses. It also covers various virus countermeasures, including antivirus software evolution, detection and removal techniques, and advanced methods like generic decryption and behavior-blocking software. Additionally, it describes the concept of a digital immune system, which helps in the rapid identification and neutralization of viruses in organizational environments.










![[STEP93] IDENTIFIES FOUR GENERATIONS OF
ANTIVIRUS SOFTWARE:
1.First generation: simple scanners
2.Second generation: heuristic scanners
3.Third generation: activity traps
4.Fourth generation: full-featured protection](https://image.slidesharecdn.com/virusesandviruscountetmeasures-201026071443/85/Viruses-and-virus-countetmeasures-14-320.jpg)

![4. Fourth-generation: scanning and activity trap components.
Advanced Antivirus Techniques:
Generic decryption (GD):
• technology enables the antivirus program to easily detect even the most
complex polymorphic viruses while maintaining fast scanning speeds [NACH97].
• decrypt itself to activate. In order to detect such a structure , executable files are run
• through a GD scanner
1. CPU emulator:
• A software-based virtual computer . Instructions in an executable file are interpreted by the emulator
rather than executed on the underlying processor . The emulator includes software versions of all
Registers and other processor hardware , so that the underlying processor is unaffected by programs
interpreted on the emulator.](https://image.slidesharecdn.com/virusesandviruscountetmeasures-201026071443/85/Viruses-and-virus-countetmeasures-16-320.jpg)