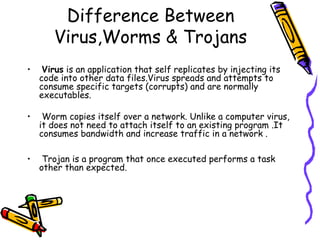
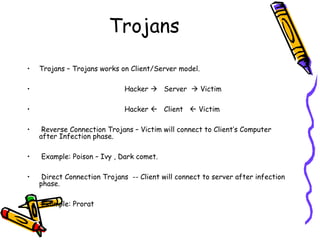
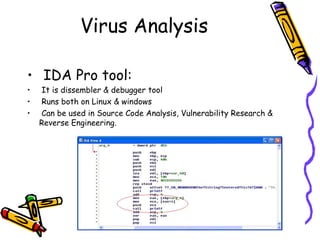
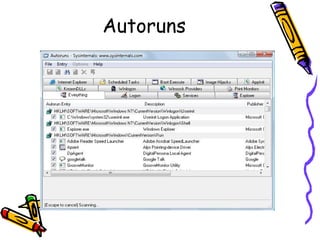
This document provides an overview of viruses, worms, trojans and spyware. It discusses the differences between these types of malware and their modes of transmission. The document then describes the life cycle of a virus, including the infection and attack phases. It outlines some common indications that a system may be infected with a virus. Finally, it discusses some methods that viruses use to avoid detection by antivirus software, such as killing antivirus tasks, self-modification, and encryption with variable keys.