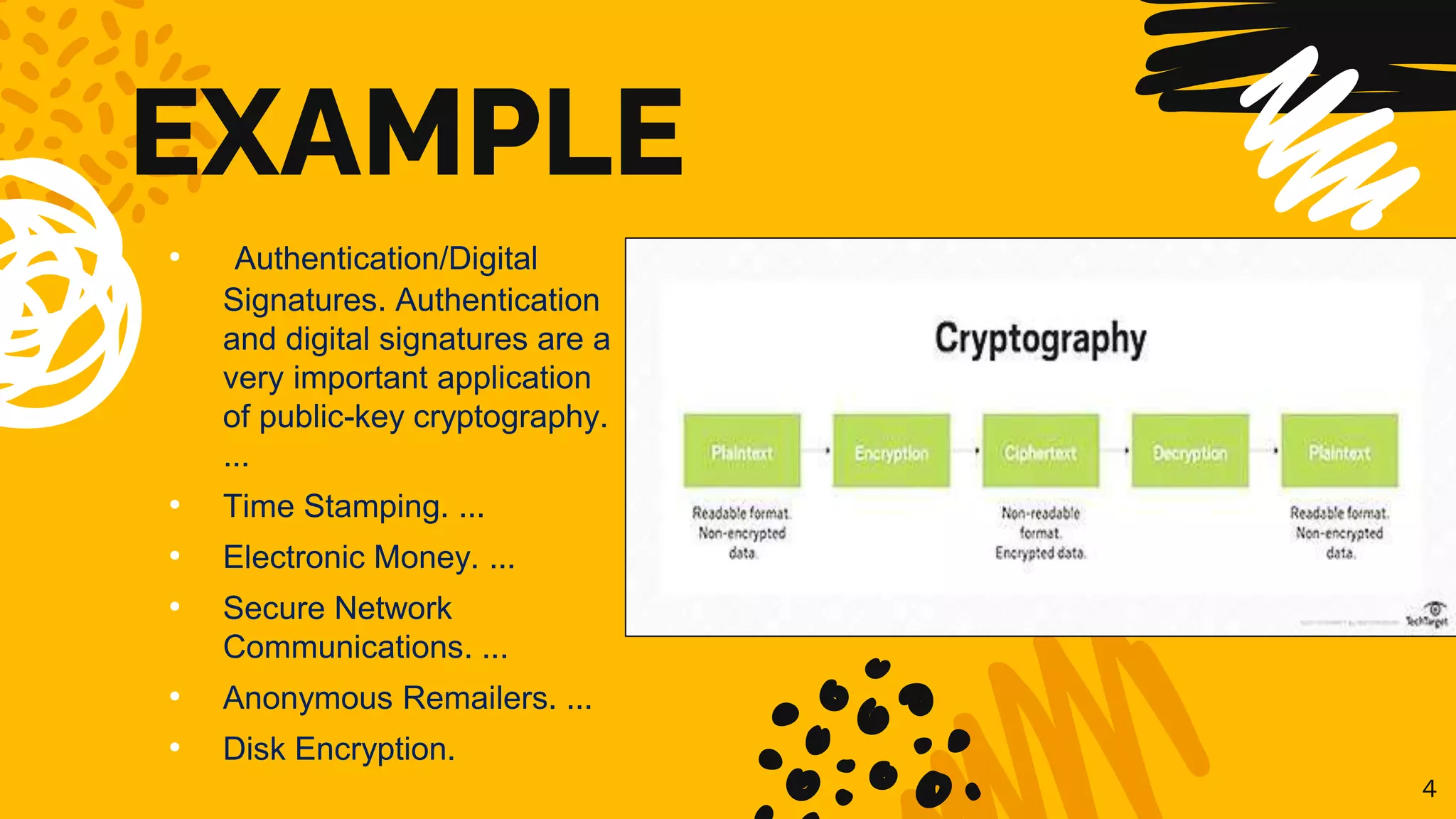
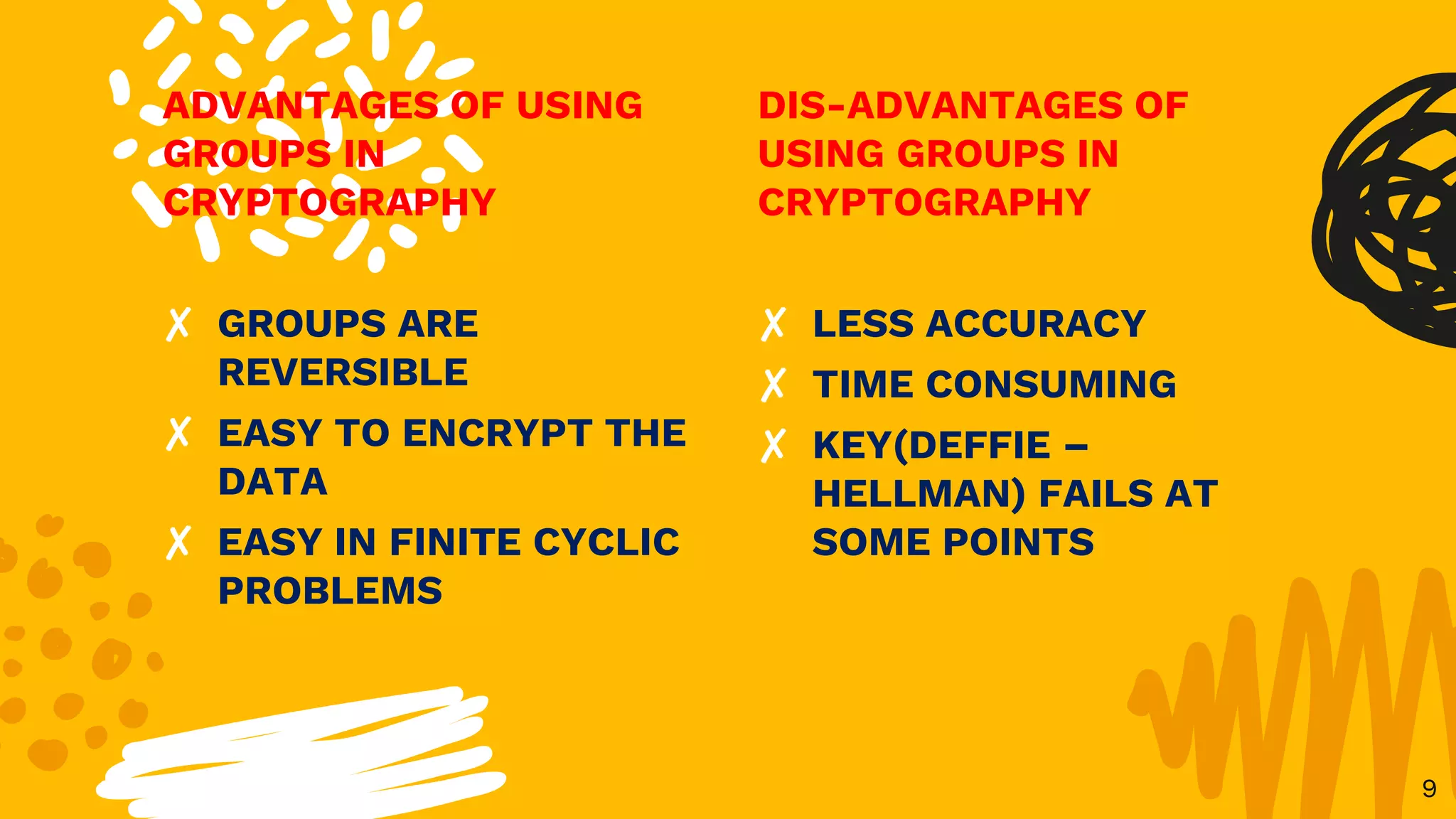
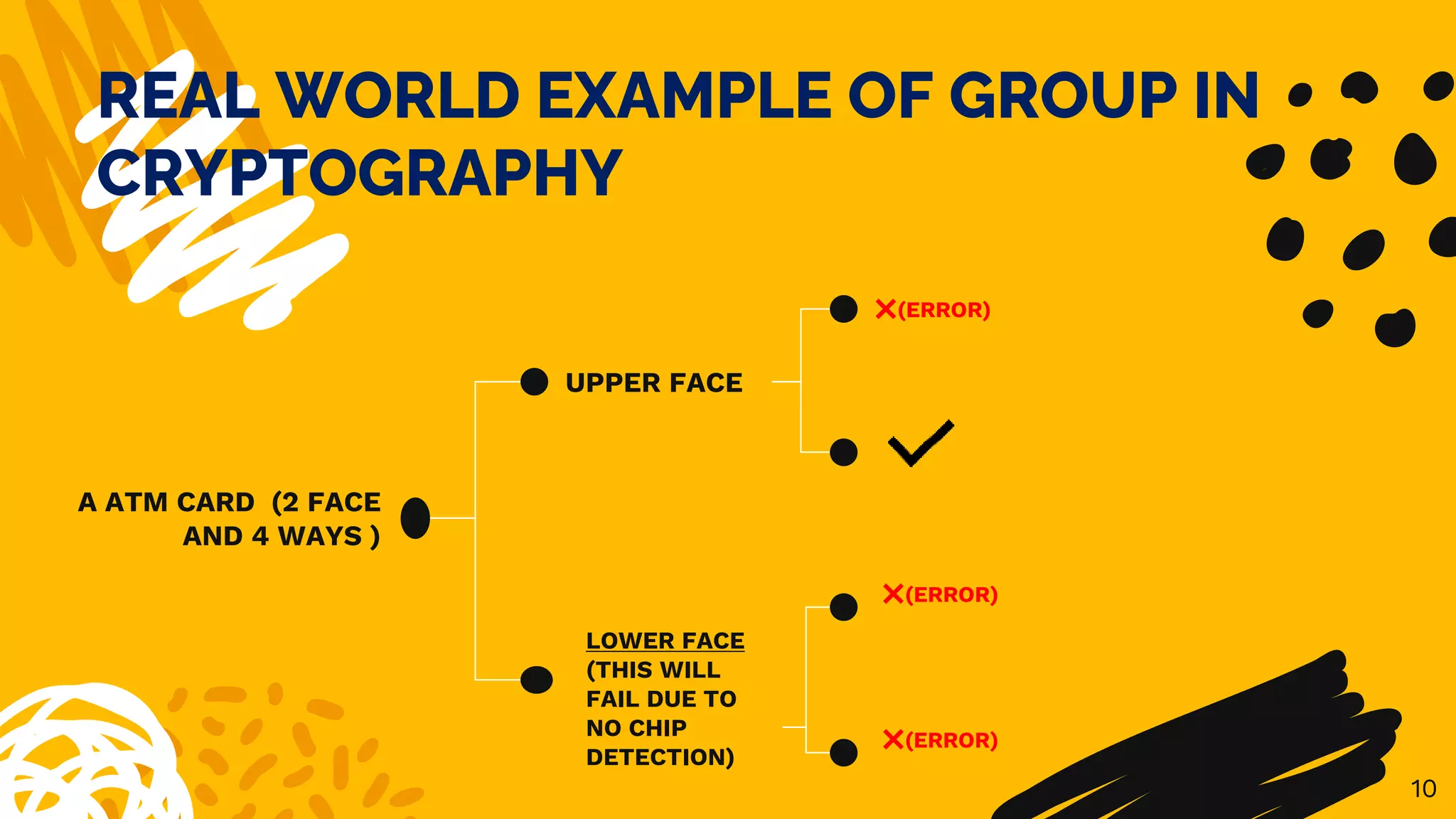
The document discusses the application of group theory in cryptography, particularly focusing on the use of groups for constructing cryptographic protocols. It covers key concepts such as Diffie-Hellman key exchange, the benefits and drawbacks of group-based cryptography, and various real-world applications. Additionally, it emphasizes the role of cyclic groups and nonabelian groups in modern cryptographic methods.