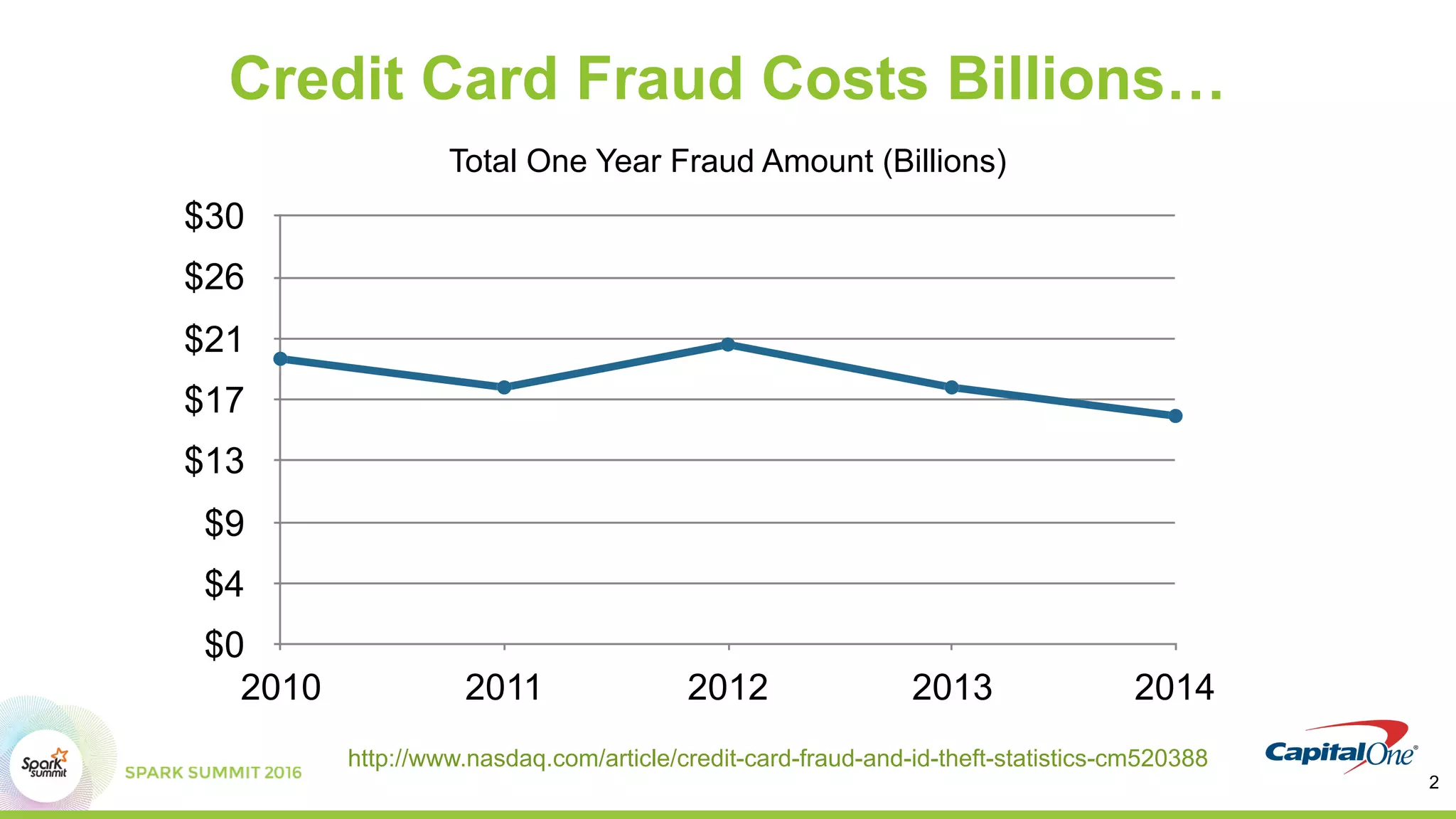
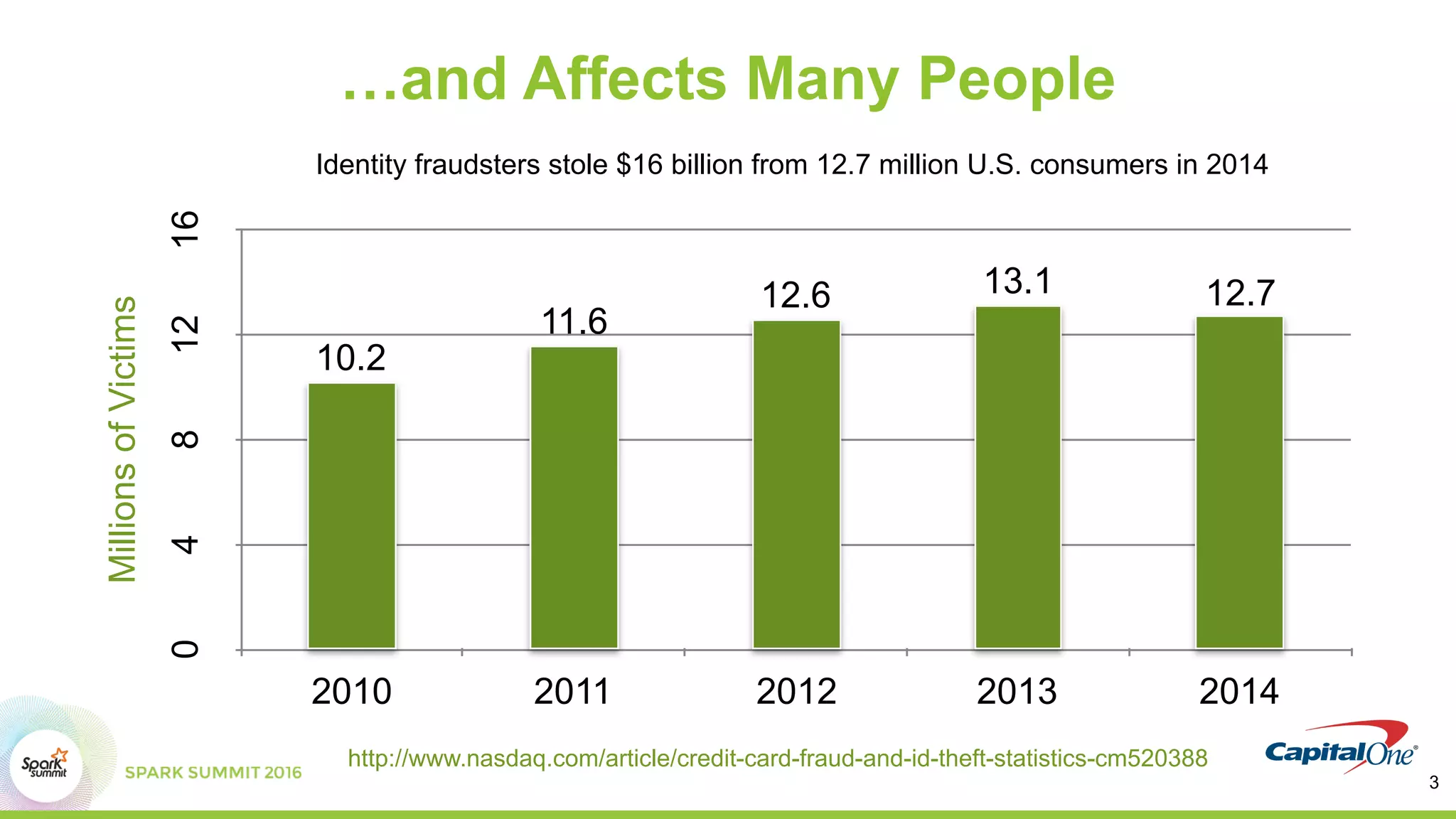
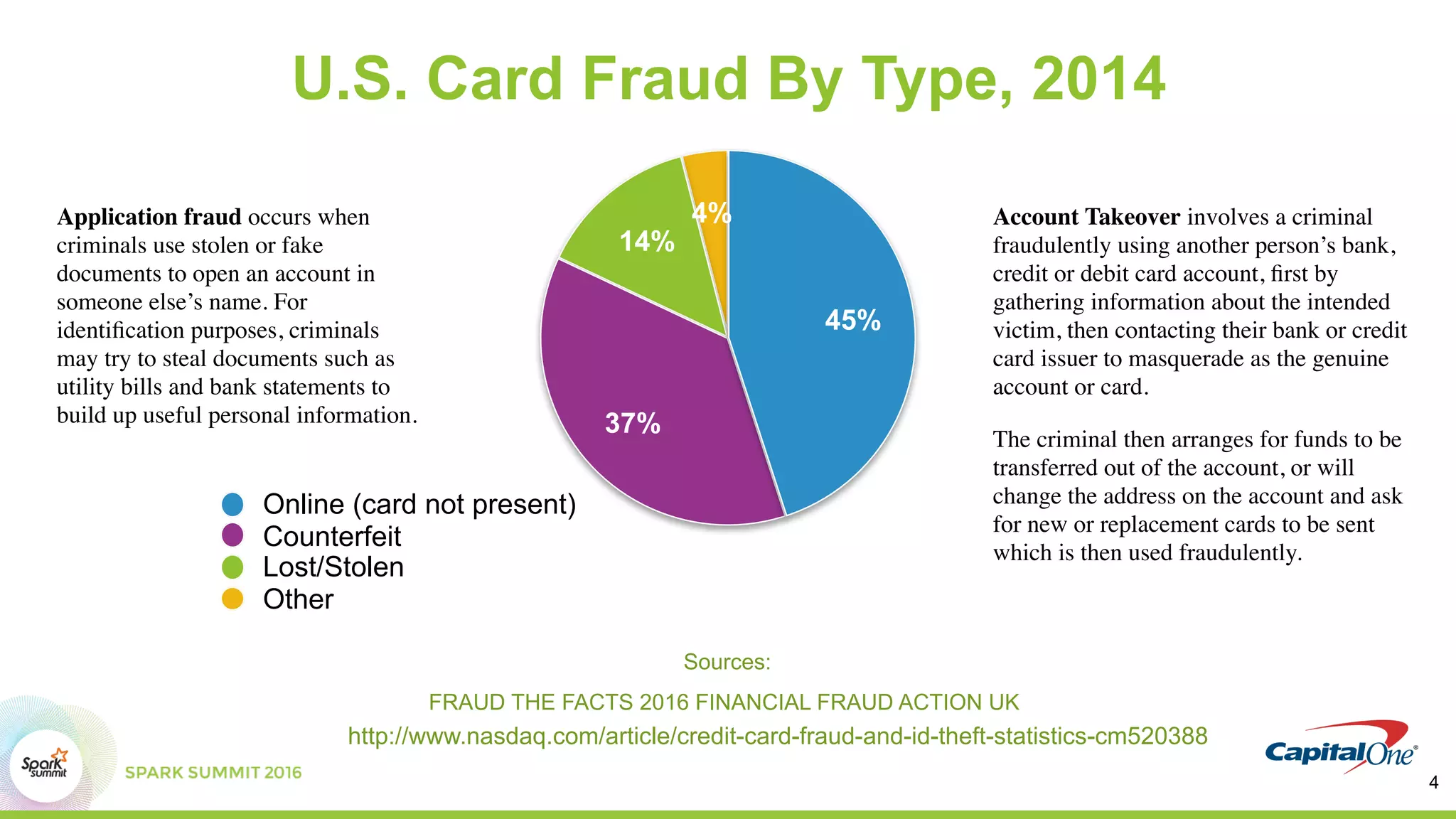
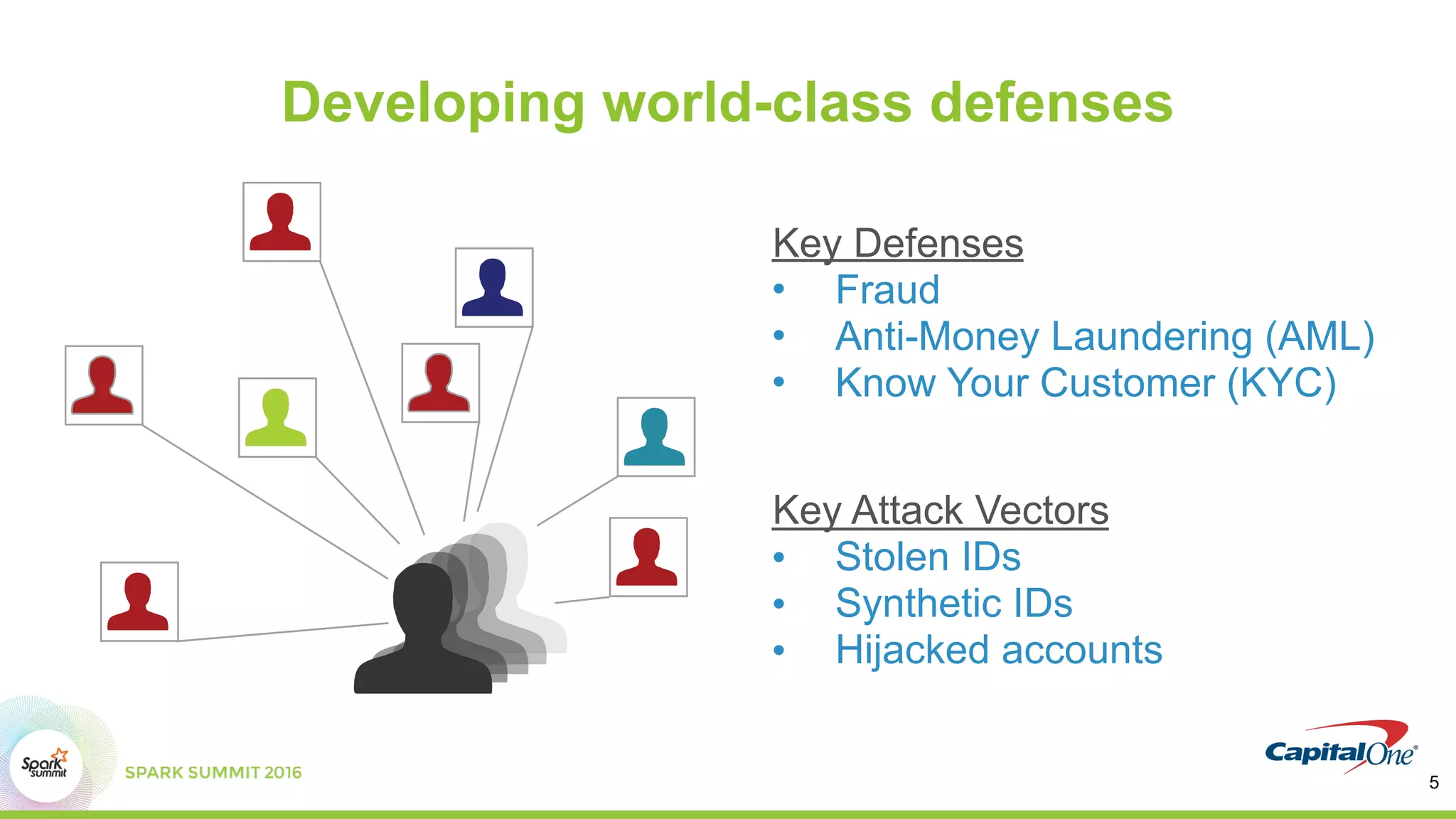
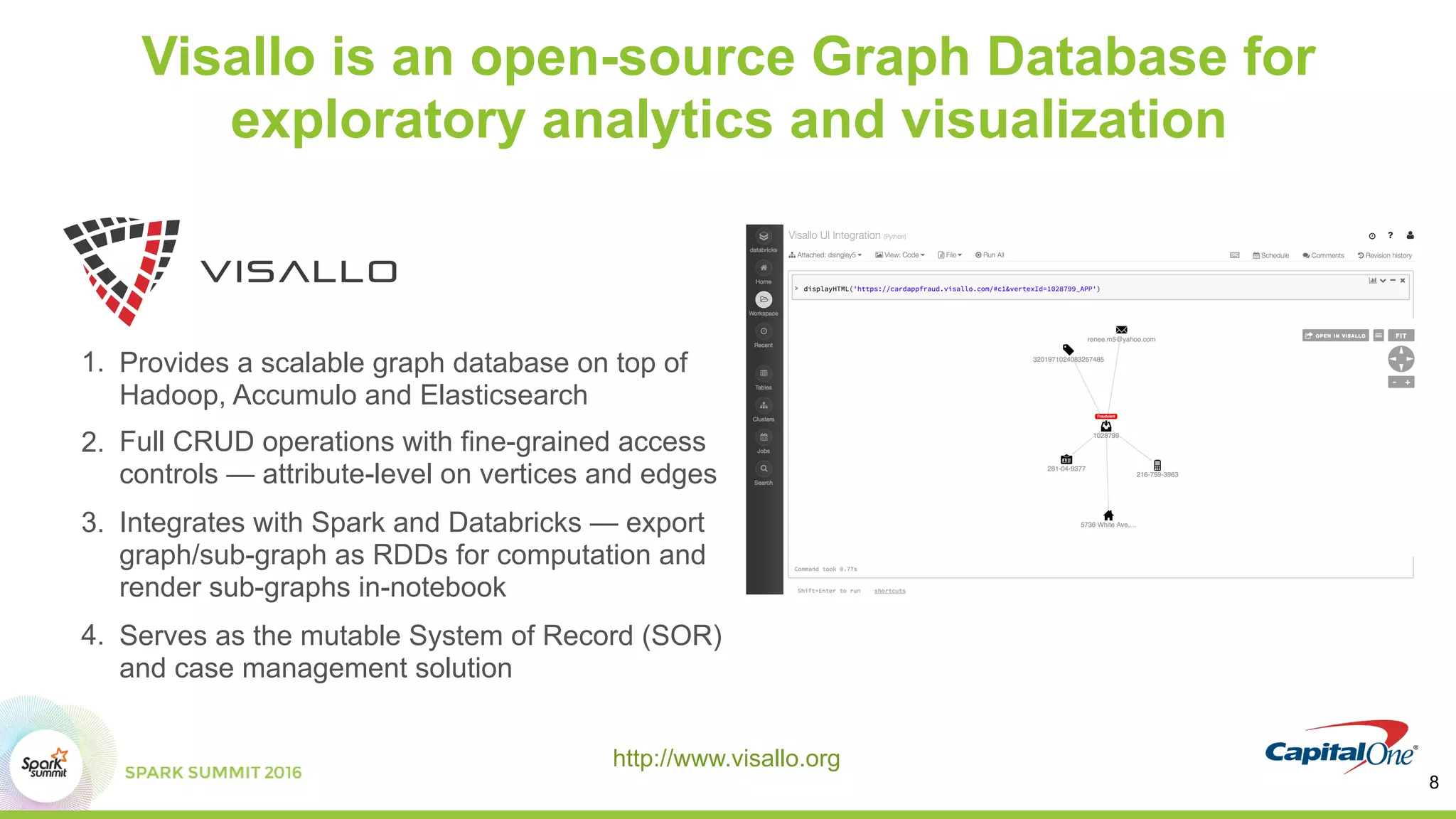
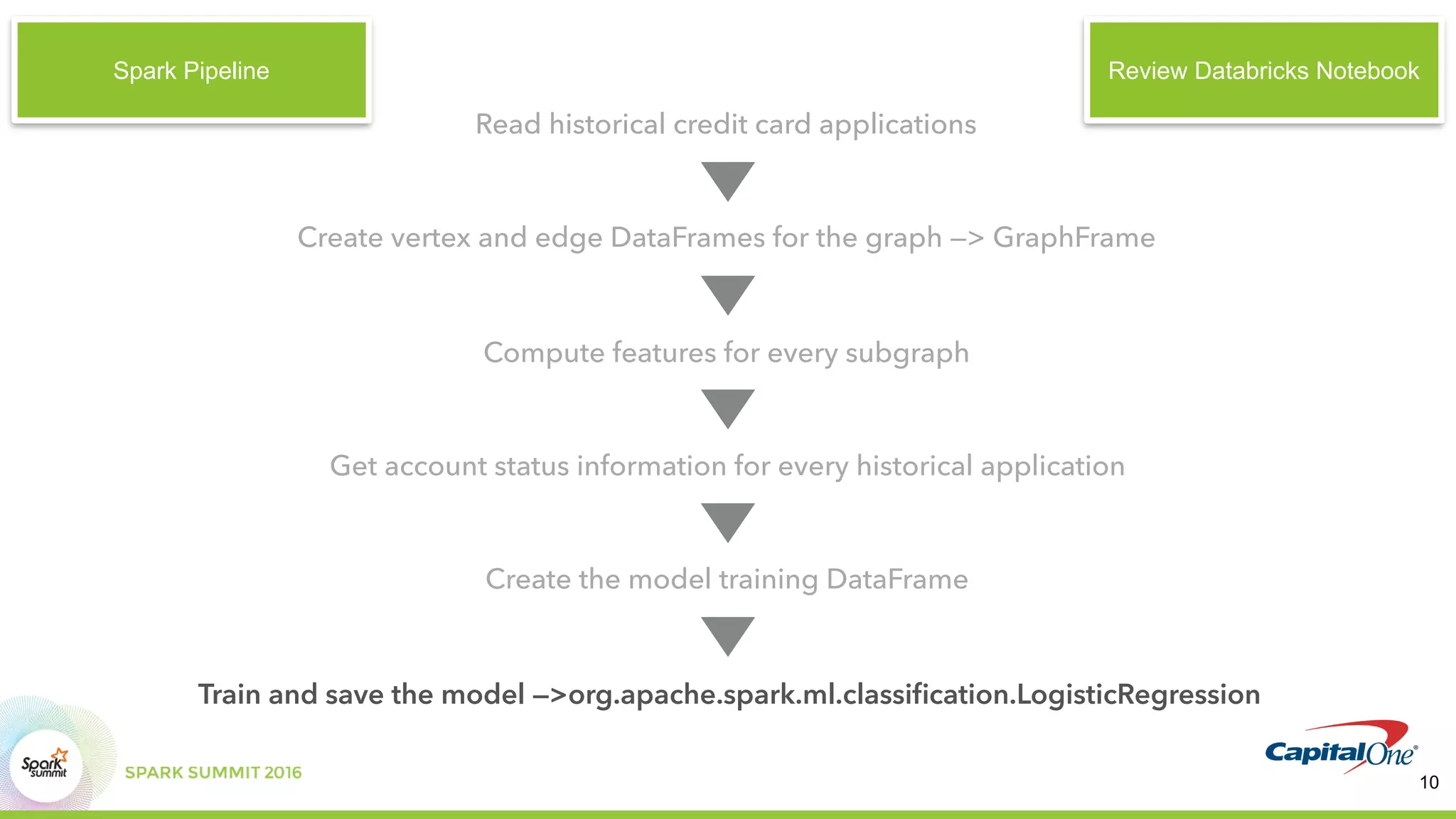
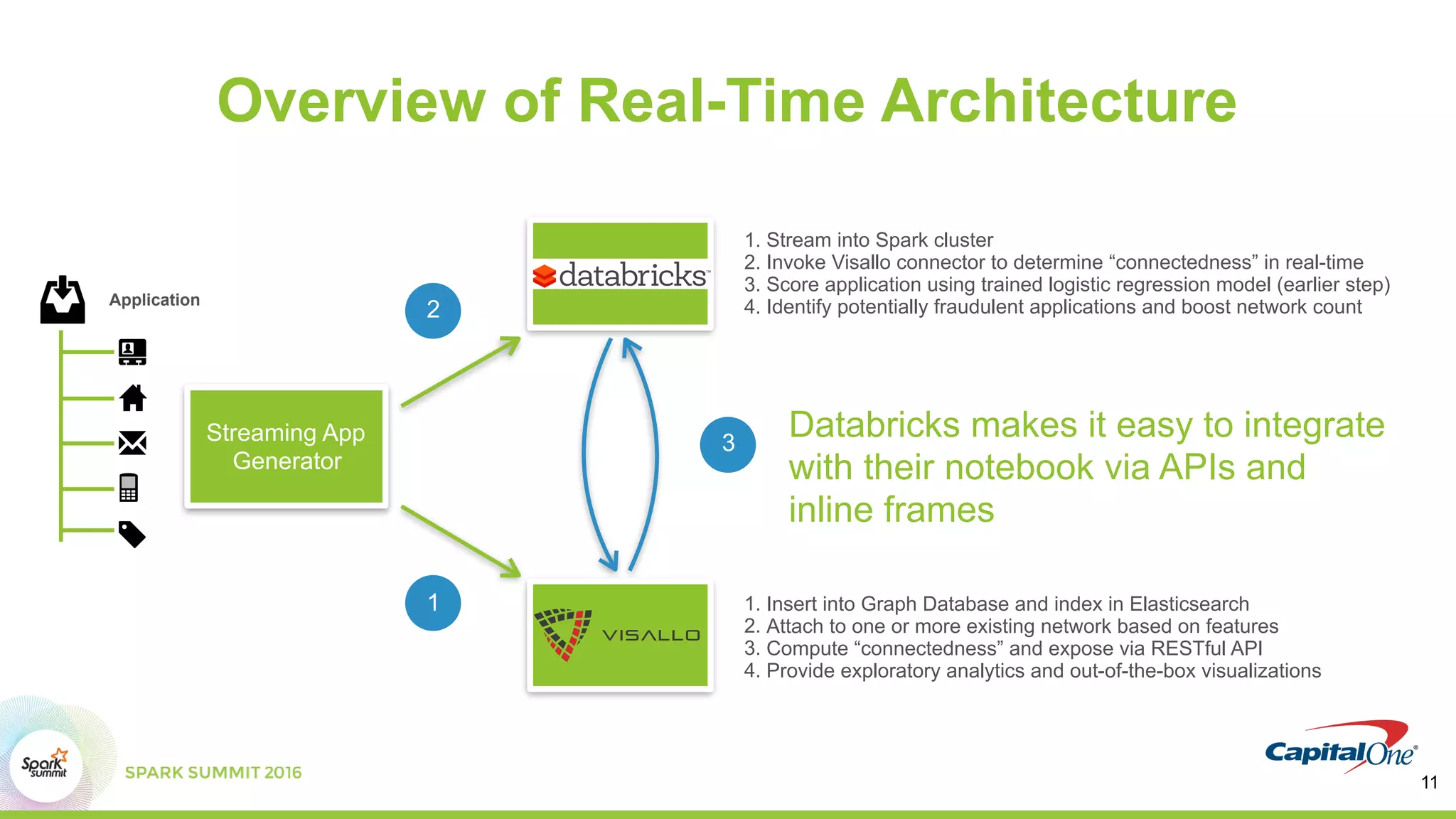
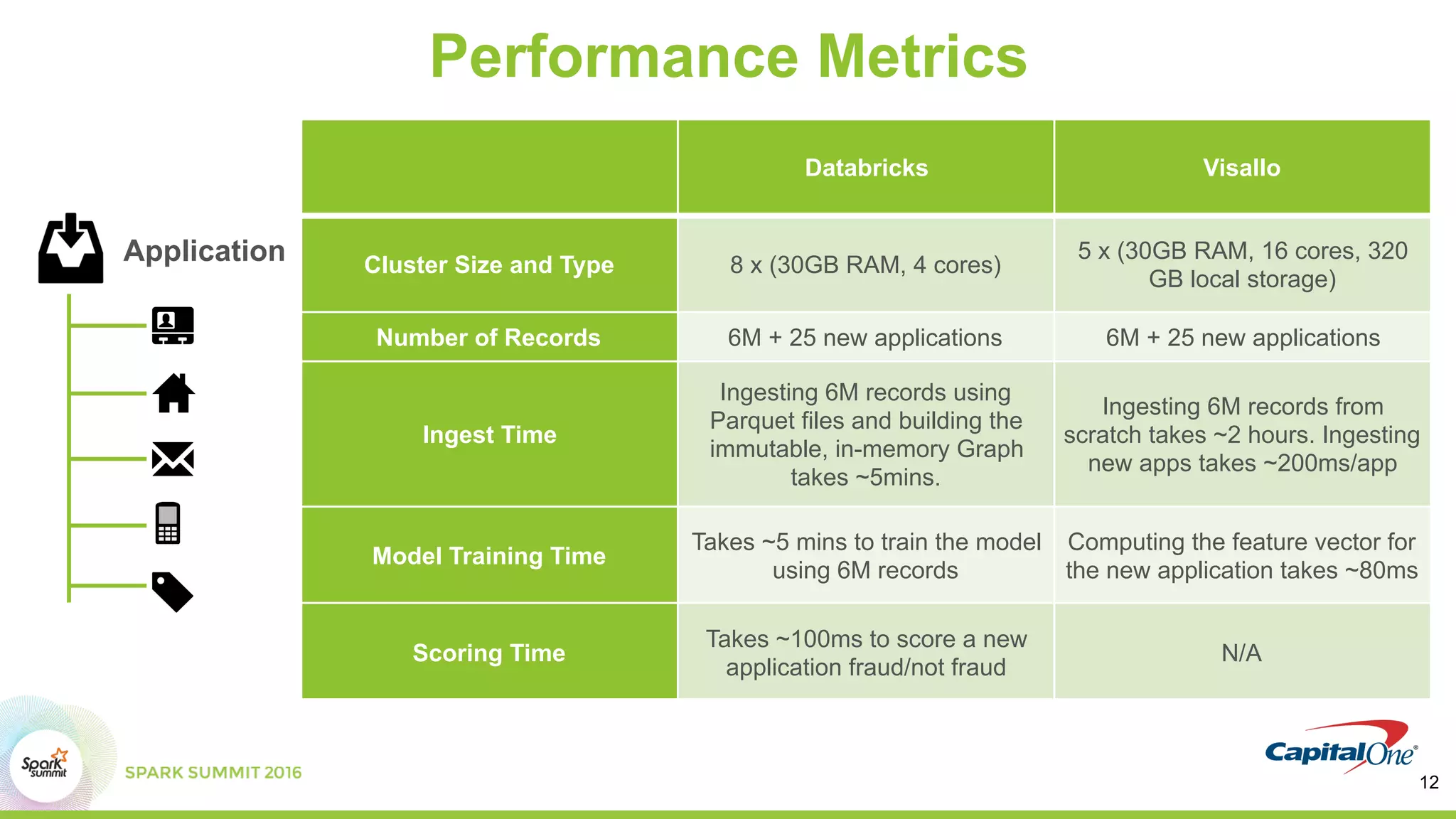
This document discusses using Spark and graph analysis to prevent credit card fraud in real-time. It describes how fraud costs billions annually and affects millions of people. Common fraud types are outlined. The solution involves combining multiple data sources using Spark and a graph database to score applications for fraud in real-time. A demo is shown using sample fraudulent data and a fraud prediction model. Performance metrics are provided for the Databricks and Visallo platforms used to ingest data and detect fraud.