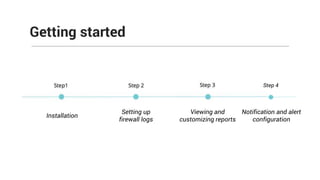
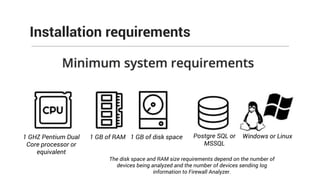
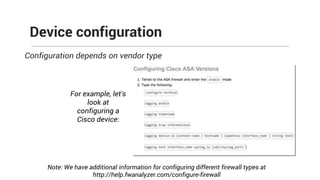
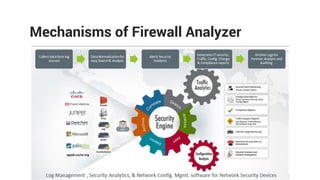
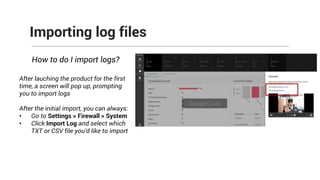
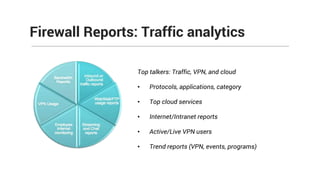
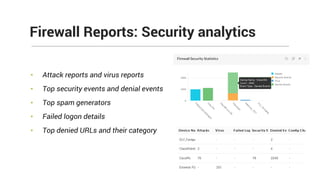
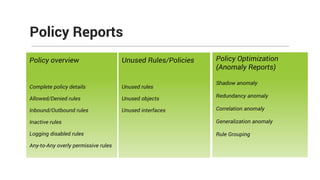
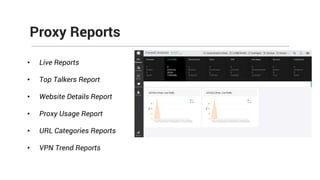
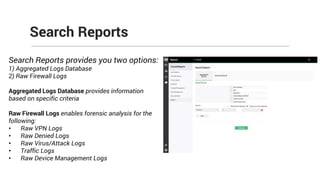
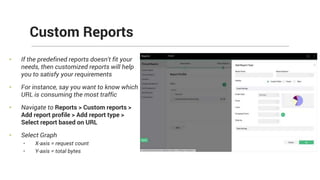
The document provides comprehensive training on the Firewall Analyzer, detailing its installation, configuration, and functionalities for analyzing firewall logs from various vendors. It emphasizes the importance of continuous monitoring for network security, introduces different reporting capabilities, and outlines common issues and solutions. Additionally, it offers guidance on alert configurations and user management features to enhance network security insights.