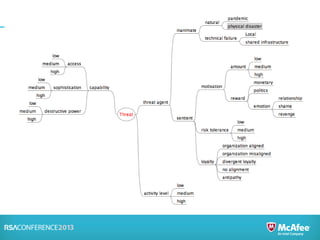
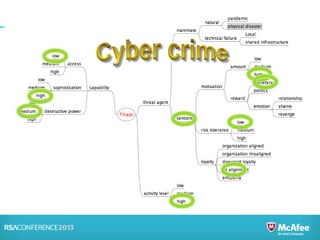
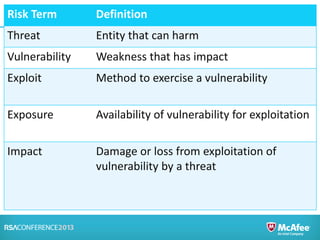
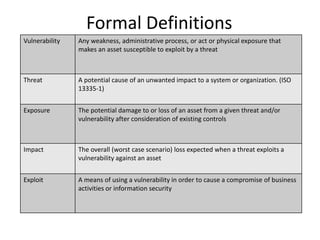
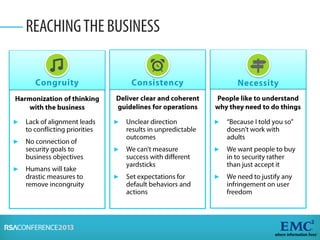
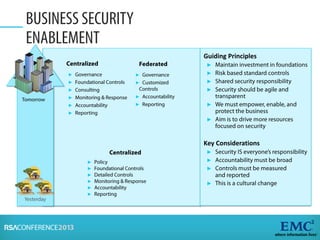
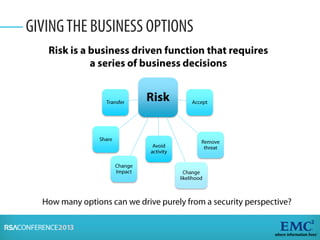
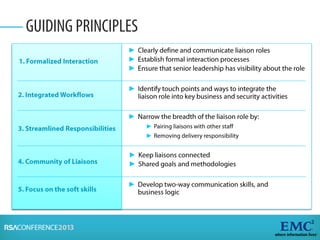
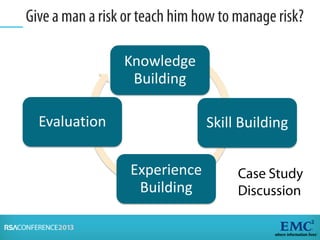
Risk analysis involves calculating risk based on probabilities from actuarial tables, while risk assessment identifies threats, vulnerabilities, impacts, and controls. The presenter notes that information security practitioners need a more precise way to articulate risk that accounts for subjective factors. An effective risk analysis method should capture both objective and subjective components of risk.