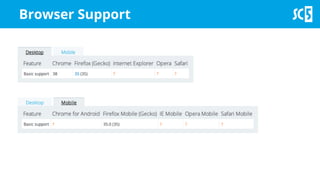
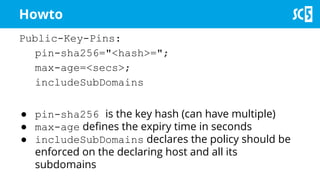
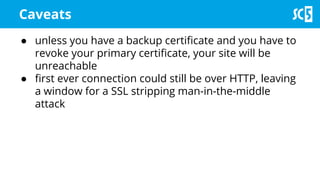
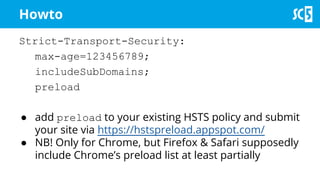
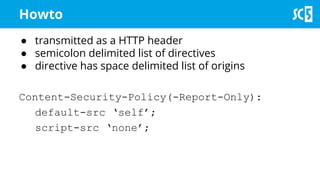
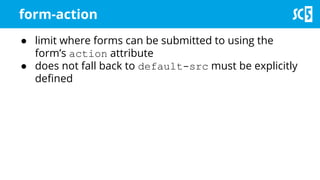
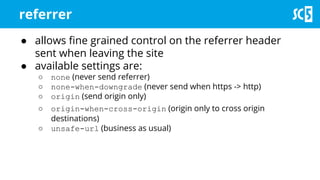
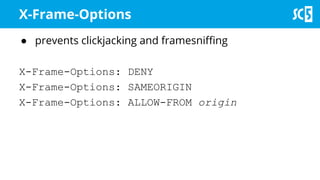
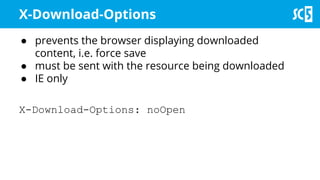
The document discusses various methods for securing client-side web applications, emphasizing the importance of HTTPS, content security policies (CSP), and sandboxing to mitigate security threats such as man-in-the-middle attacks and XSS. It outlines the implementation of protocols like HSTS and HPKP, and highlights the necessity of using secure practices in web development. Additionally, it provides resources for further reading and tools for building security policies.