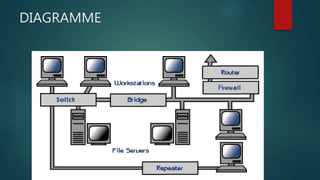
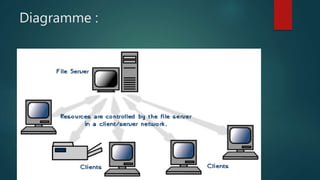
The document discusses different types of computer networks. A local area network (LAN) connects computers within a small area like a building, while a wide area network (WAN) connects networks over larger geographic areas or globally. LANs use servers to provide shared resources to workstations. Networking hardware connects devices, and bridges, routers and firewalls help manage traffic and security between networks. Network operating systems coordinate activity across multiple computers and come in peer-to-peer and client/server models.