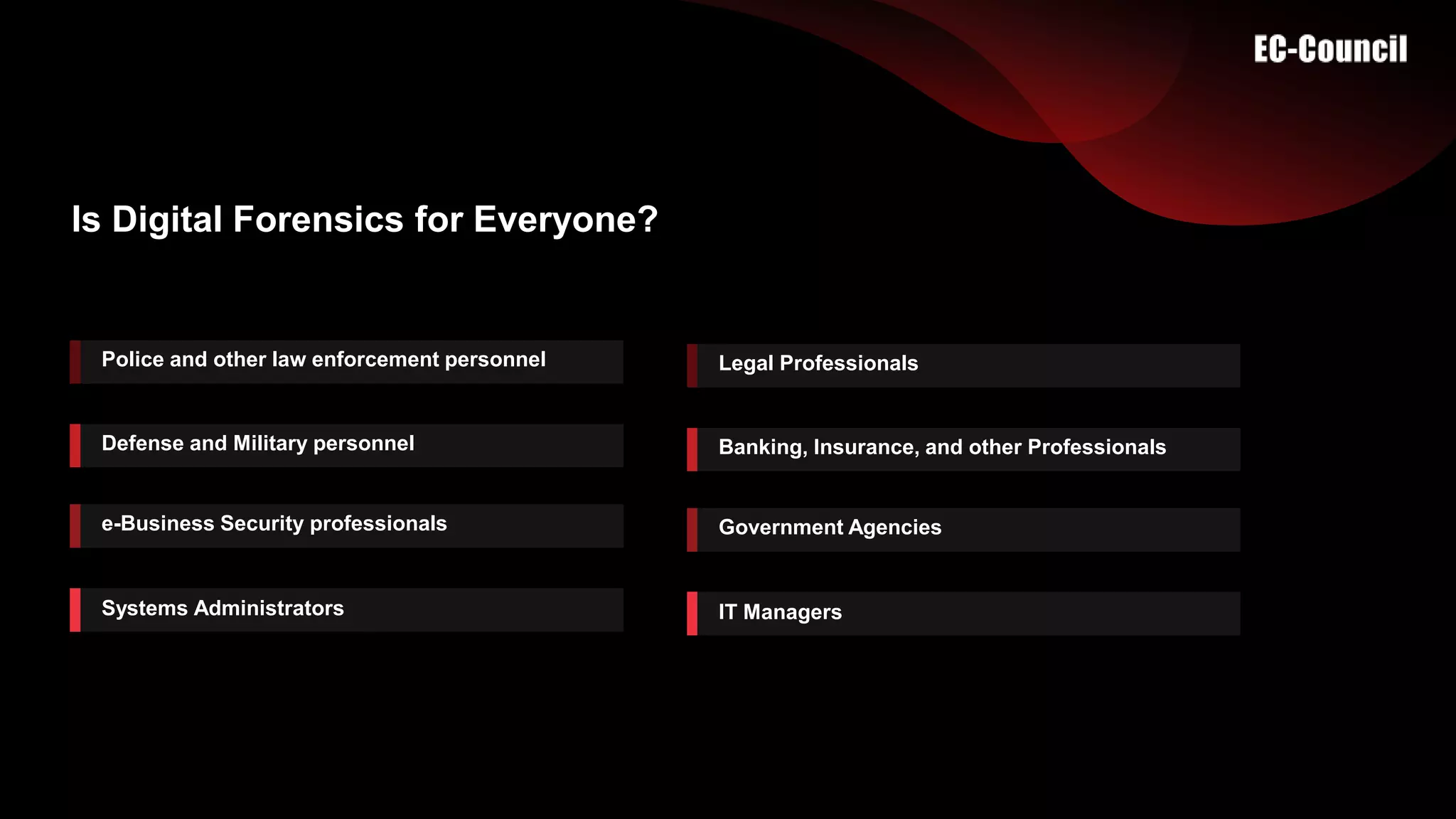
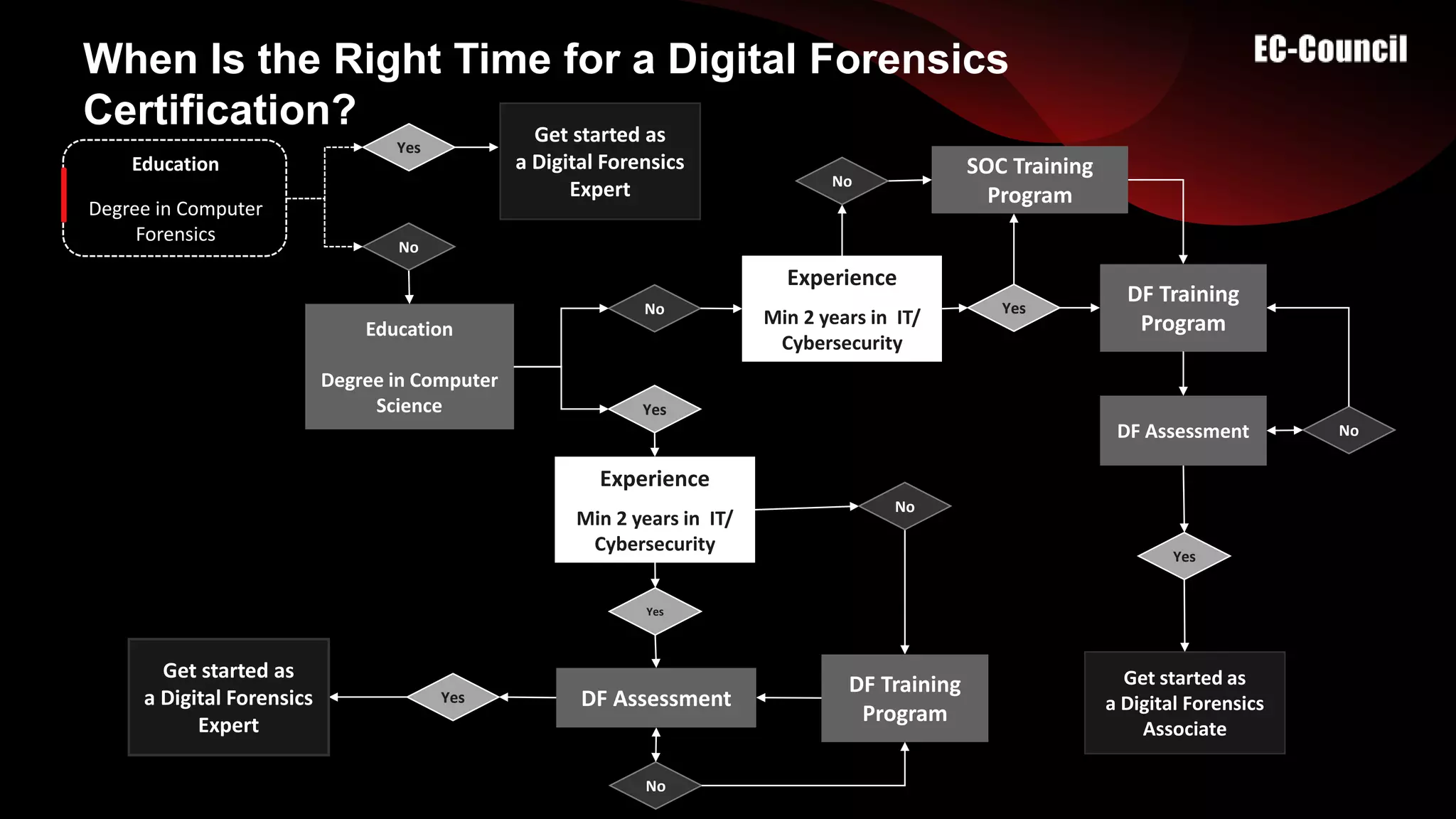
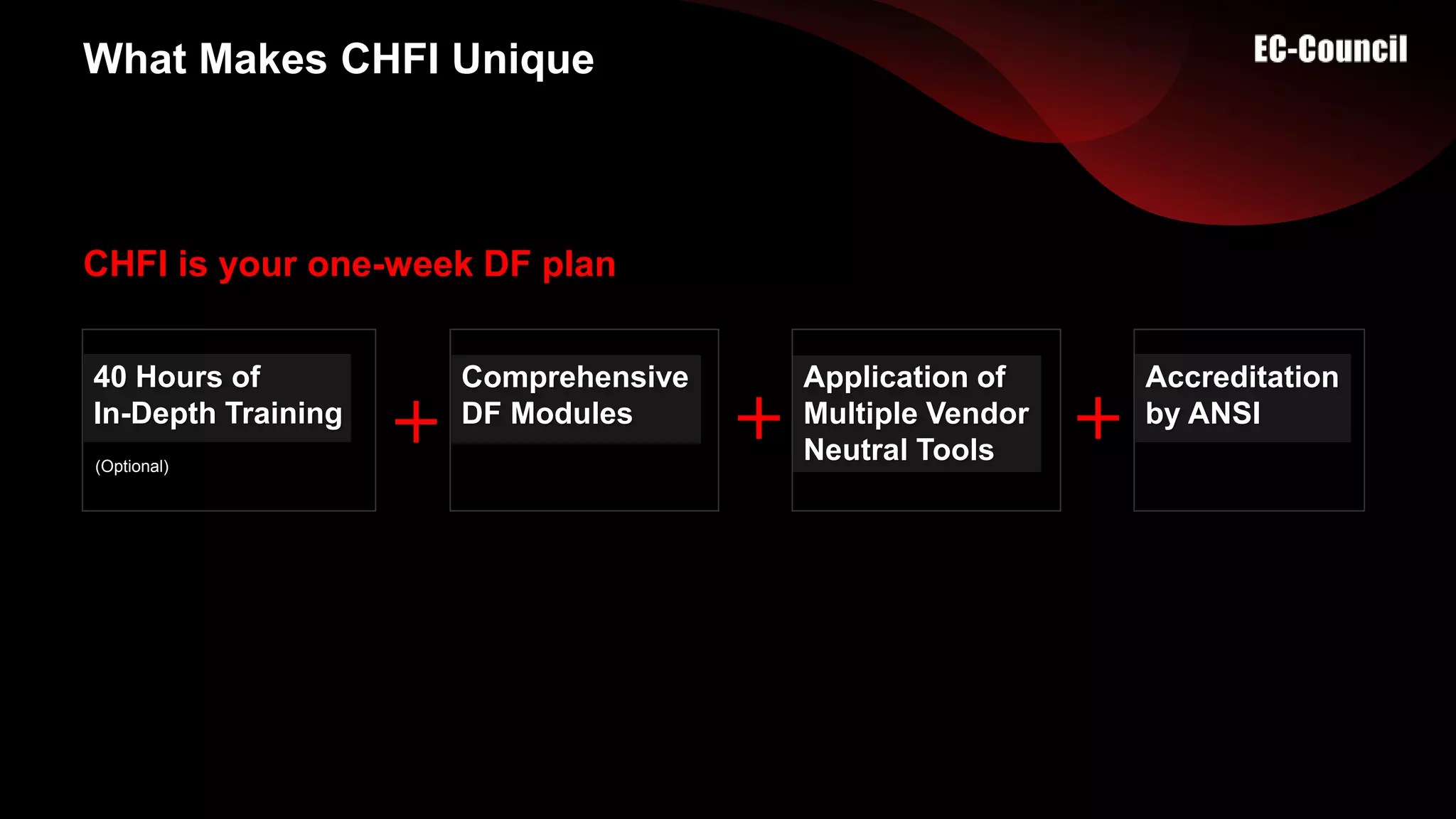
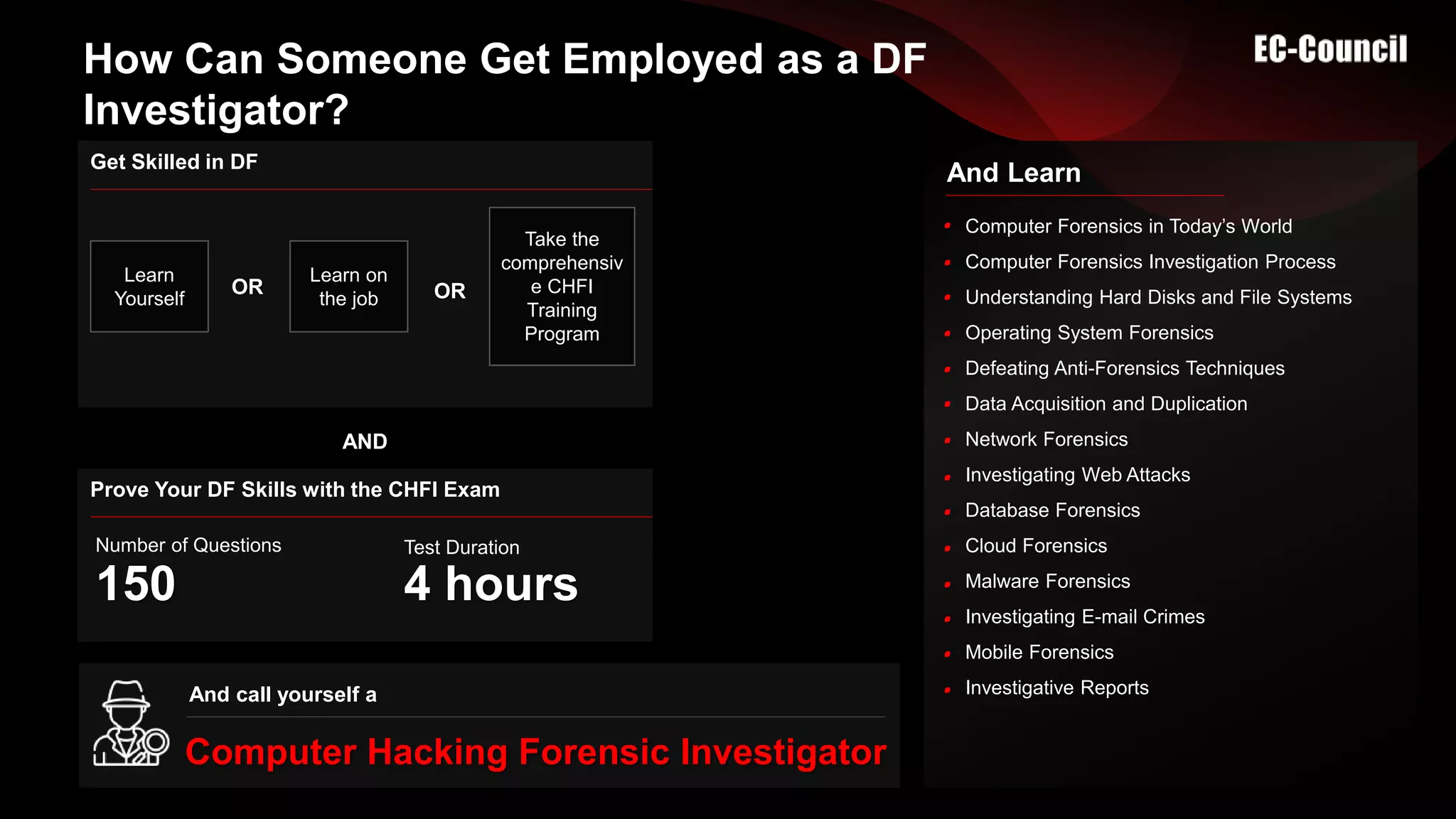
The document provides an overview of digital forensics certifications, emphasizing their importance for employers and job seekers in the expanding digital forensics market. It discusses the criteria for entering the field, educational requirements, and unique features of the CHFI certification program. The certification is positioned as a validation of skills that can significantly enhance job prospects and salary potential in the digital forensics realm.