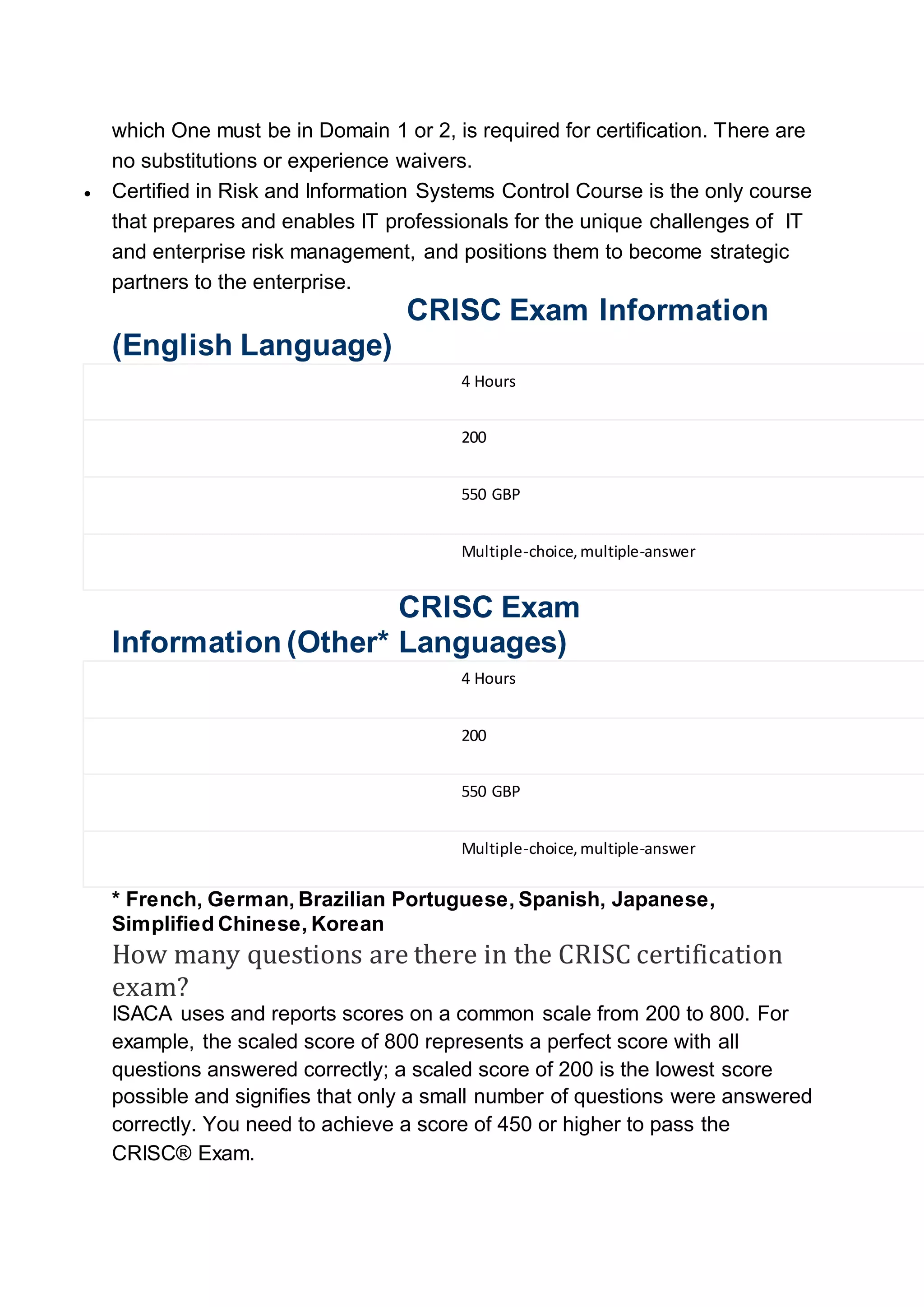
The CRISC certification course is designed to provide IT professionals with the knowledge and skills required for risk and information systems management, with a training duration of 35 hours and a high certification success rate. It focuses on four key domains: IT risk identification, assessment, response, and control monitoring, ensuring participants can implement effective risk management strategies. To obtain certification, candidates must have relevant work experience, pass a 200-question exam, and demonstrate proficiency in risk management practices.