Embed presentation
Downloaded 228 times








































































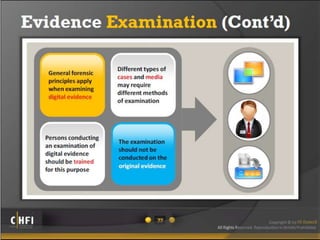





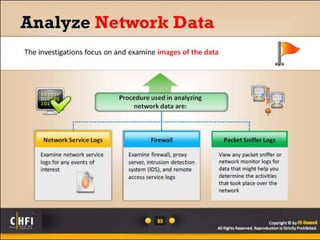




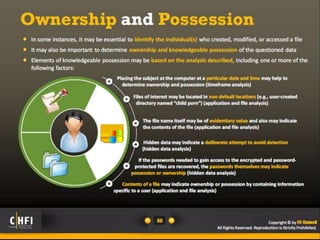
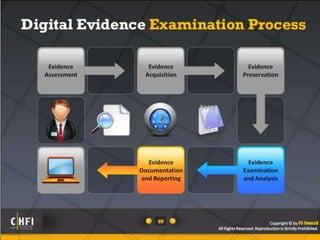

















The document discusses the benefits of exercise for mental health. Regular physical activity can help reduce anxiety and depression and improve mood and cognitive functioning. Exercise has also been shown to boost self-esteem and can serve as a healthy way to manage stress.










































































































