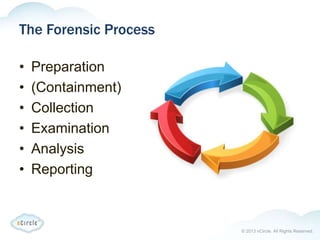
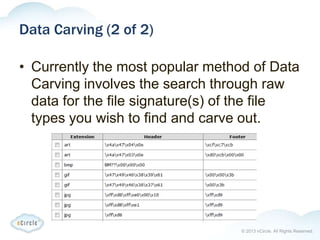
The document provides an overview of forensics, particularly focusing on computer forensics which involves techniques for gathering digital evidence related to crimes. It highlights legal considerations, types of cyber crimes, the forensic process, and analysis techniques, emphasizing the importance of chain-of-custody and proper documentation. Additionally, it discusses incident response processes and when to involve law enforcement.