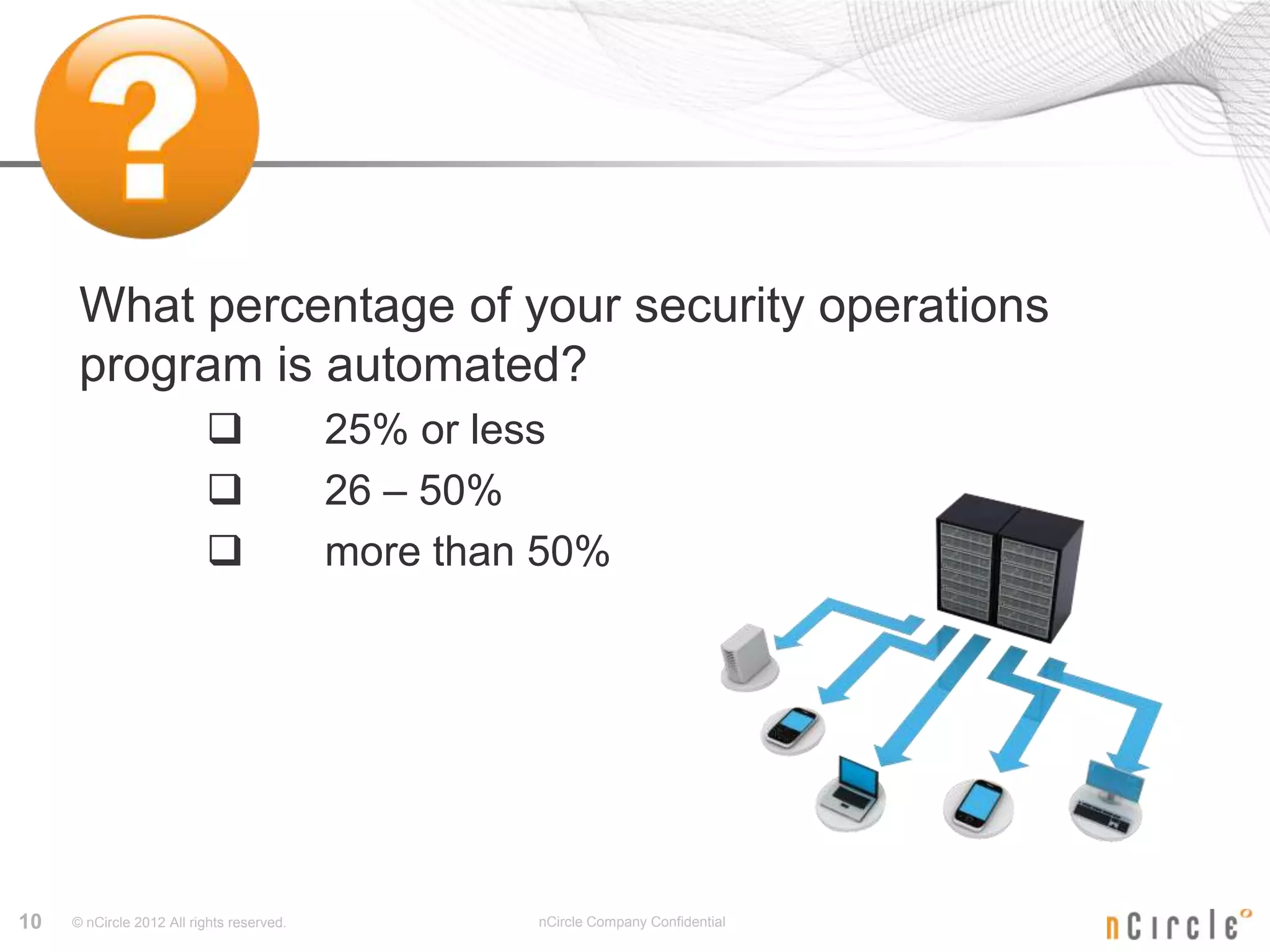
This document appears to be from a presentation on the topic of how security and compliance efforts are related. It includes polls for attendees on topics such as what regulations their organization needs to comply with, how often they have audits, whether security teams spend too much time on audits, and how aligned security and compliance efforts are. It also includes polls about executive support, how compliance requirements drive budgets, what percentage of security operations are automated, and what types of tools organizations have invested in.