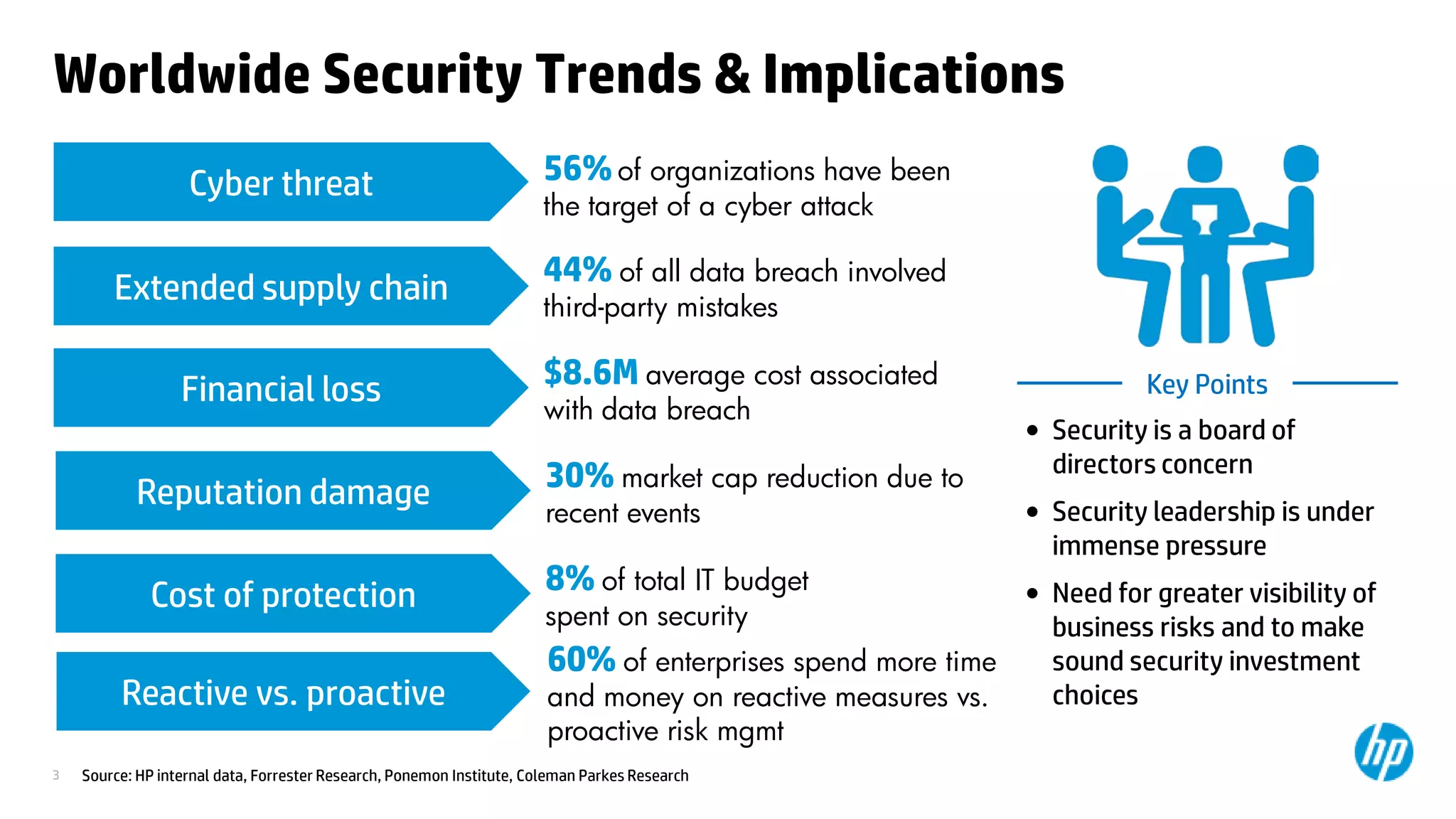
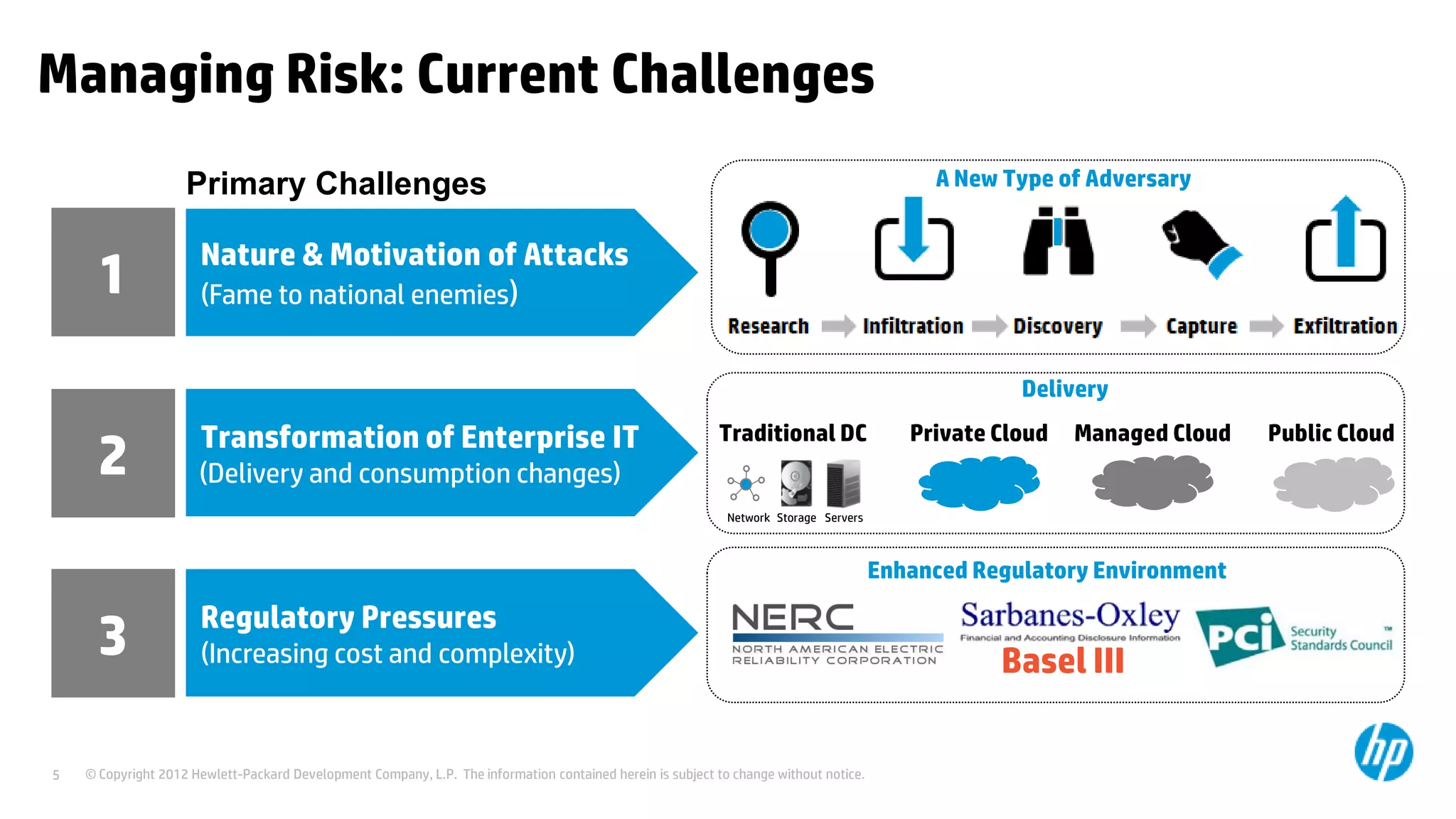
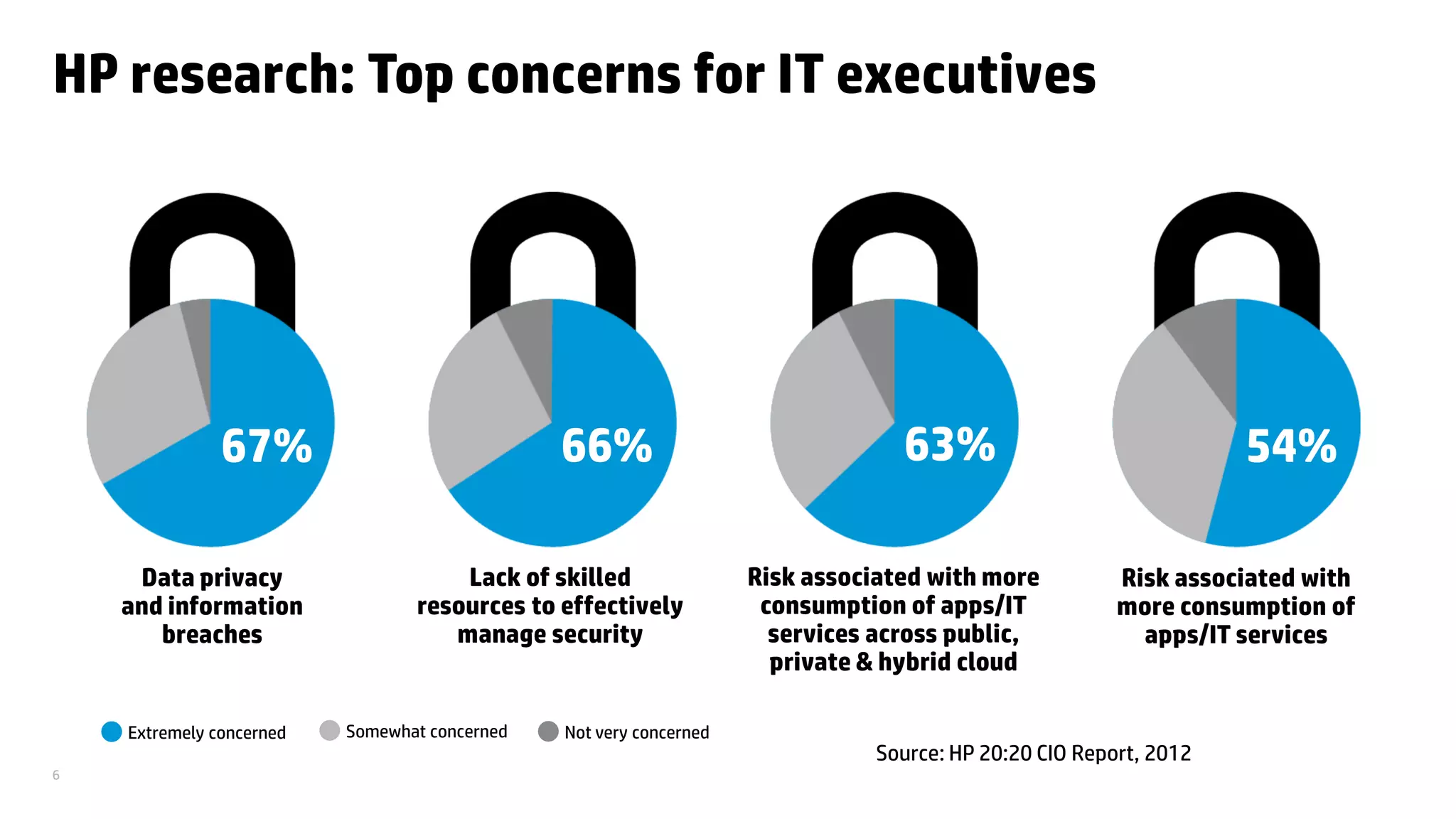
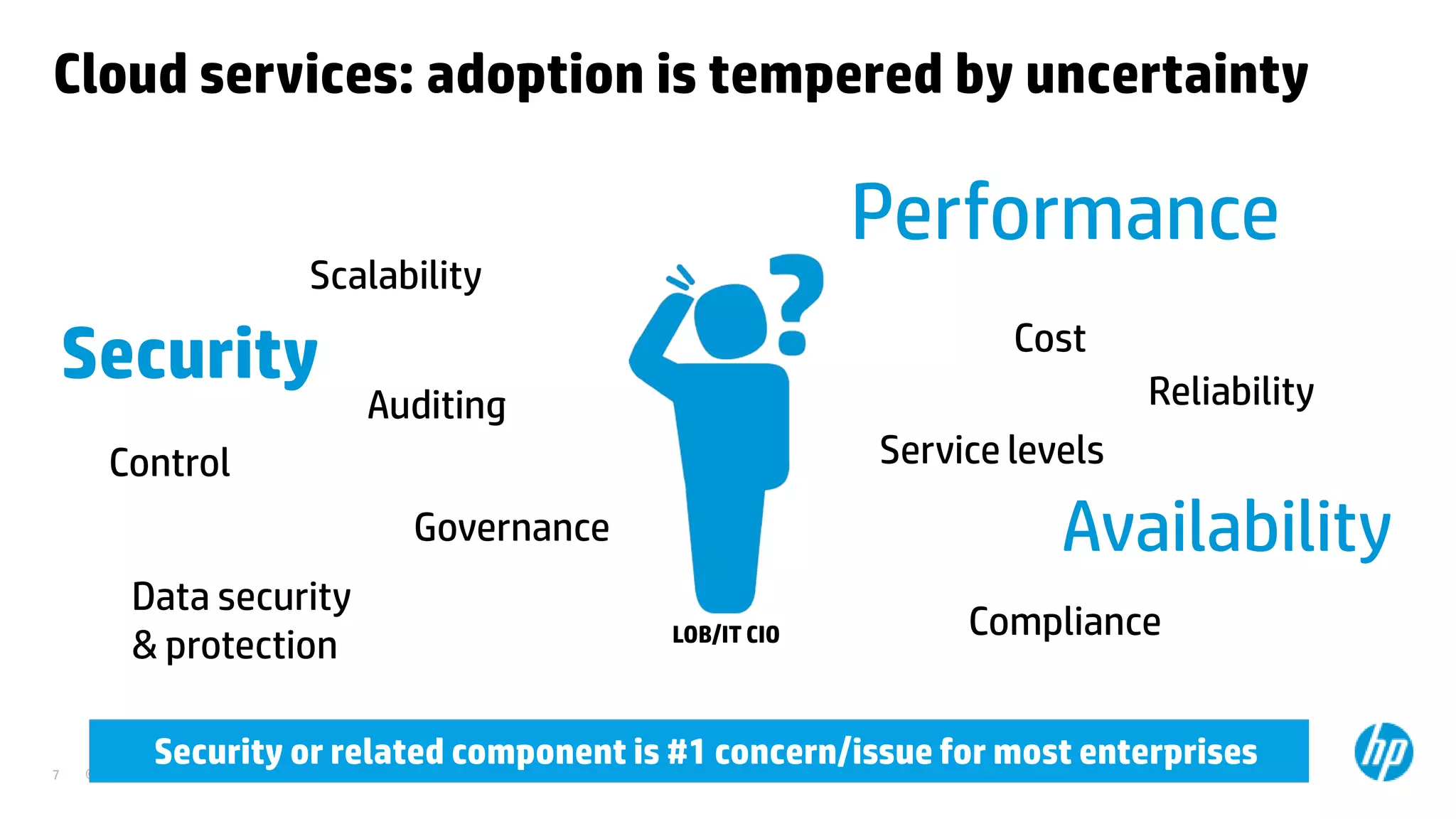
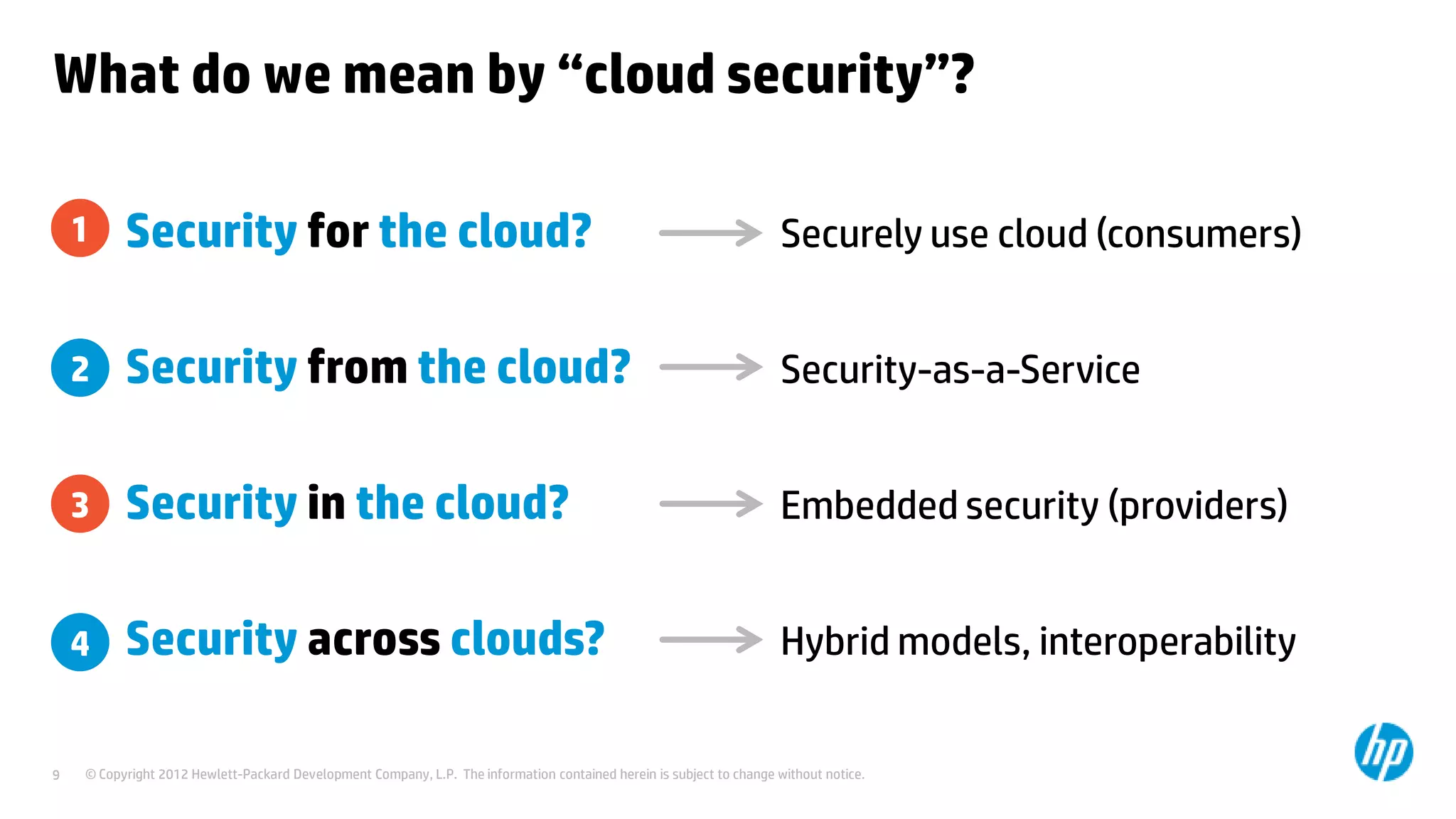
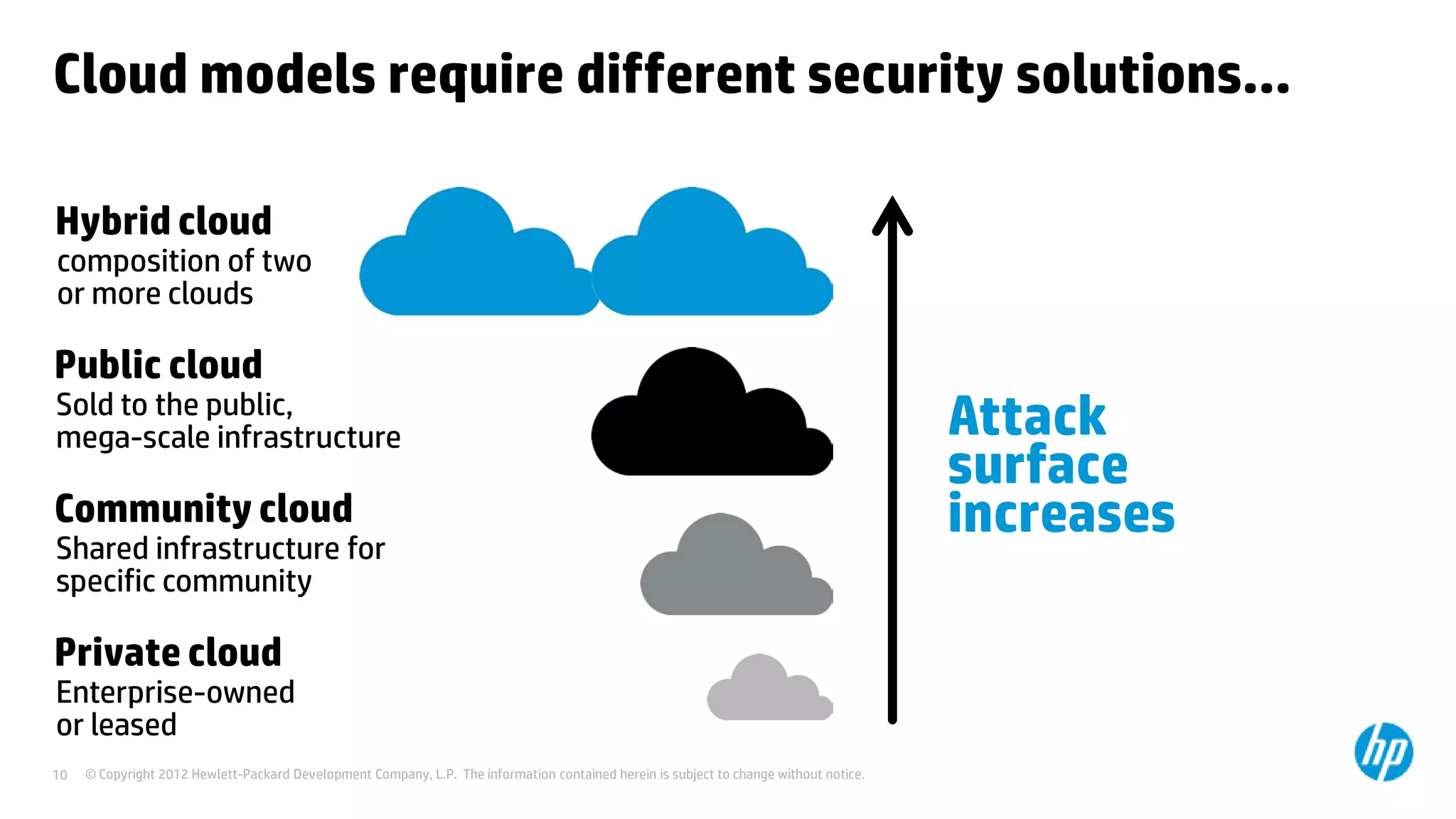
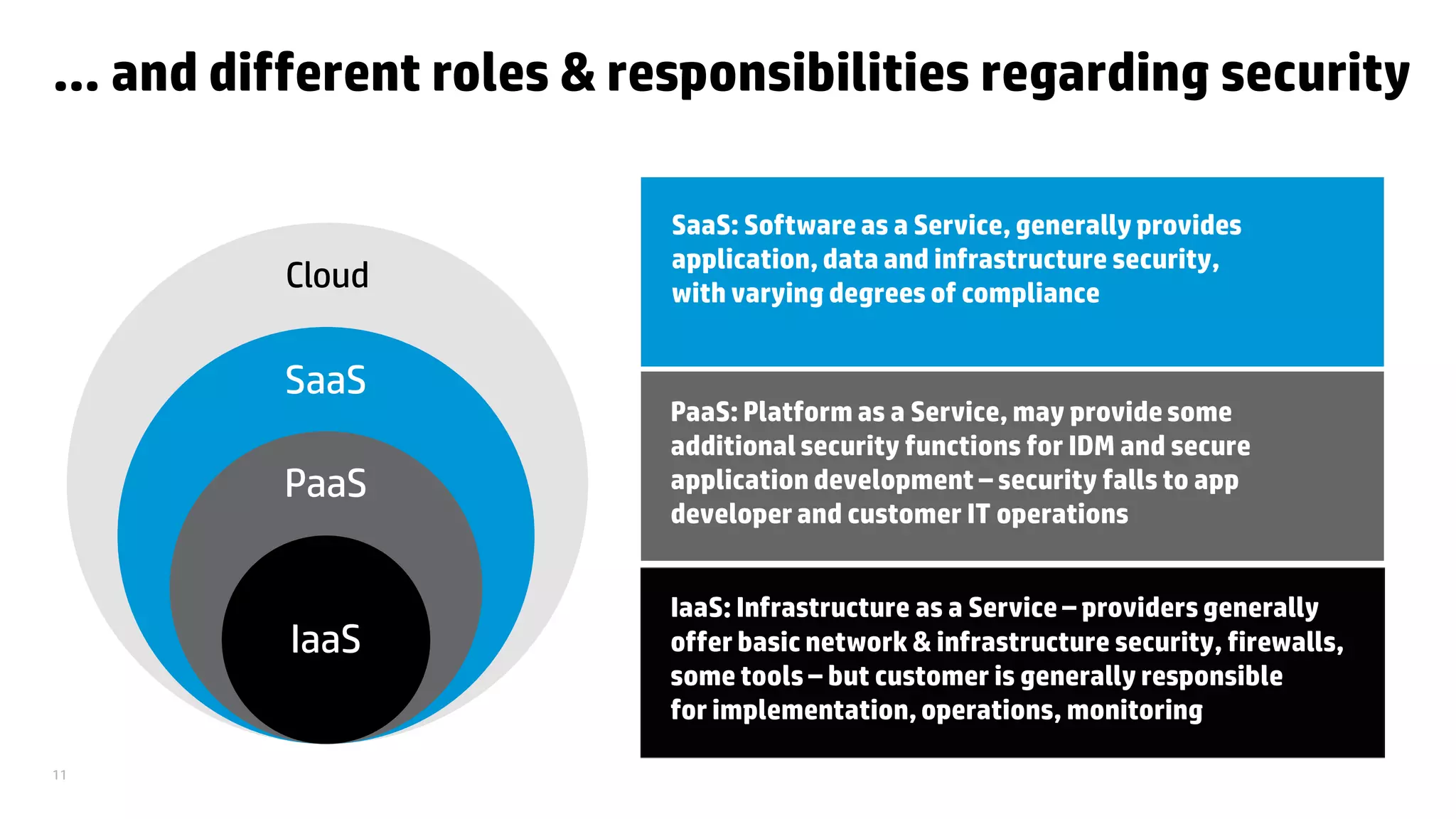
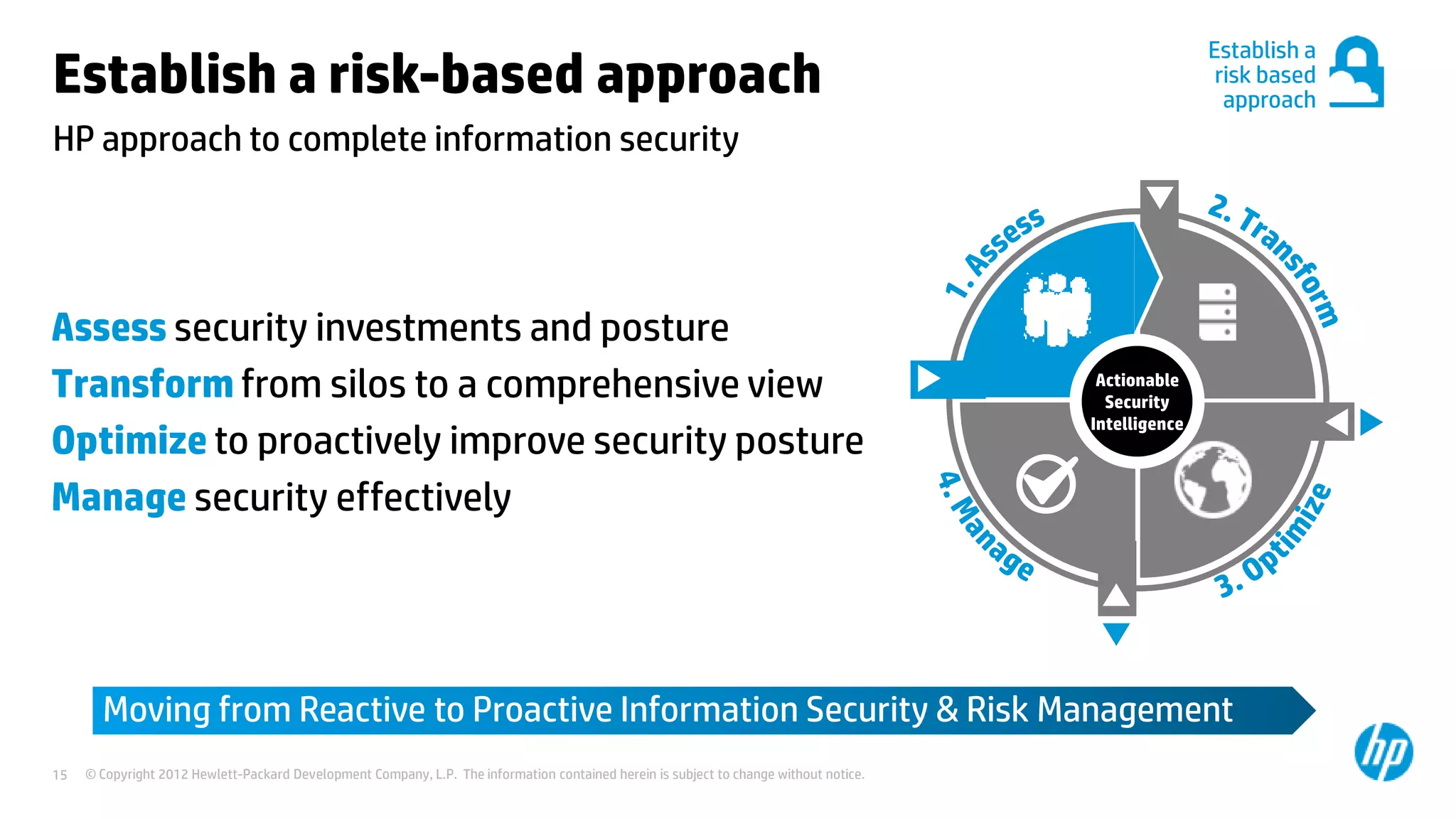
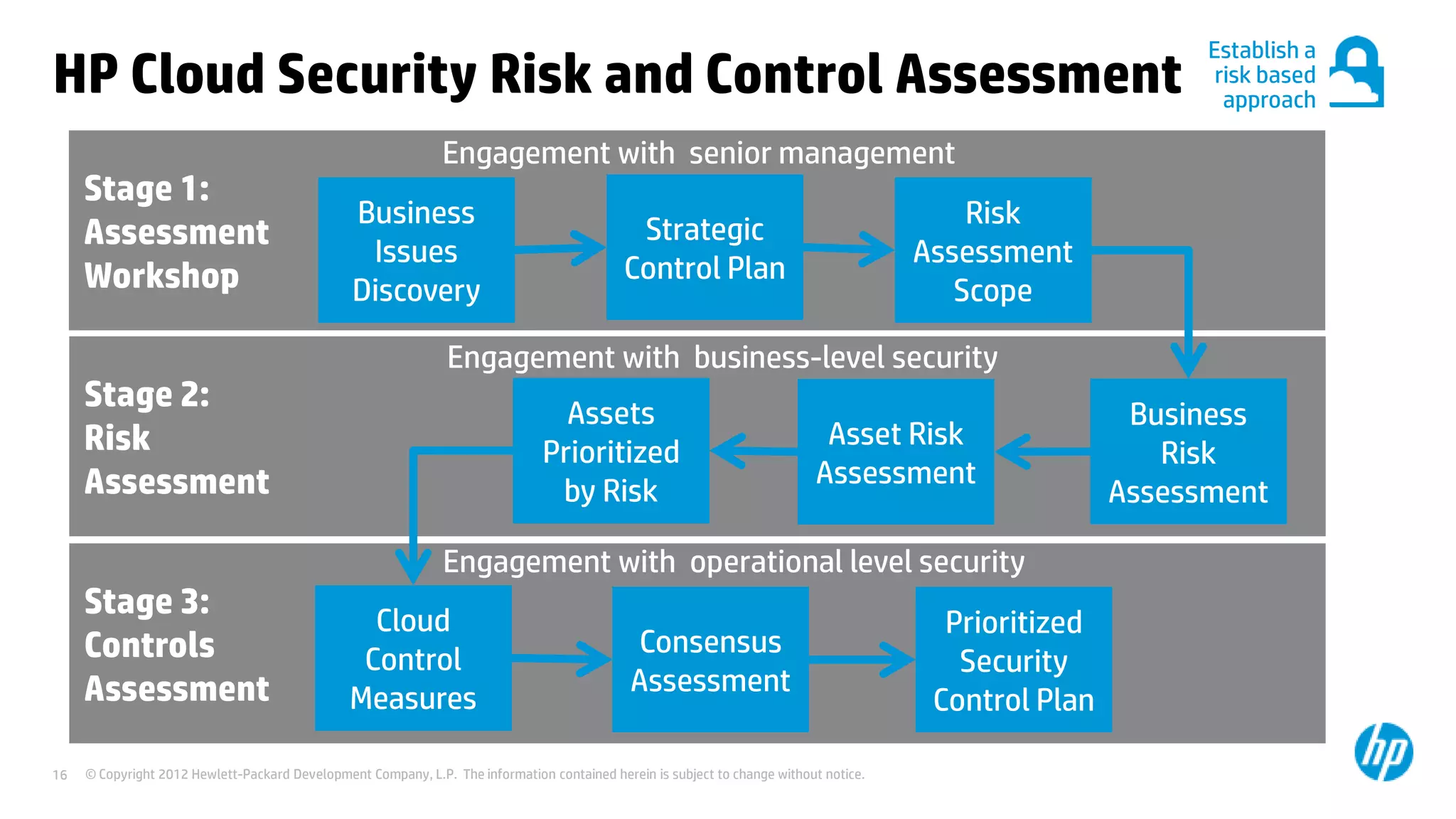
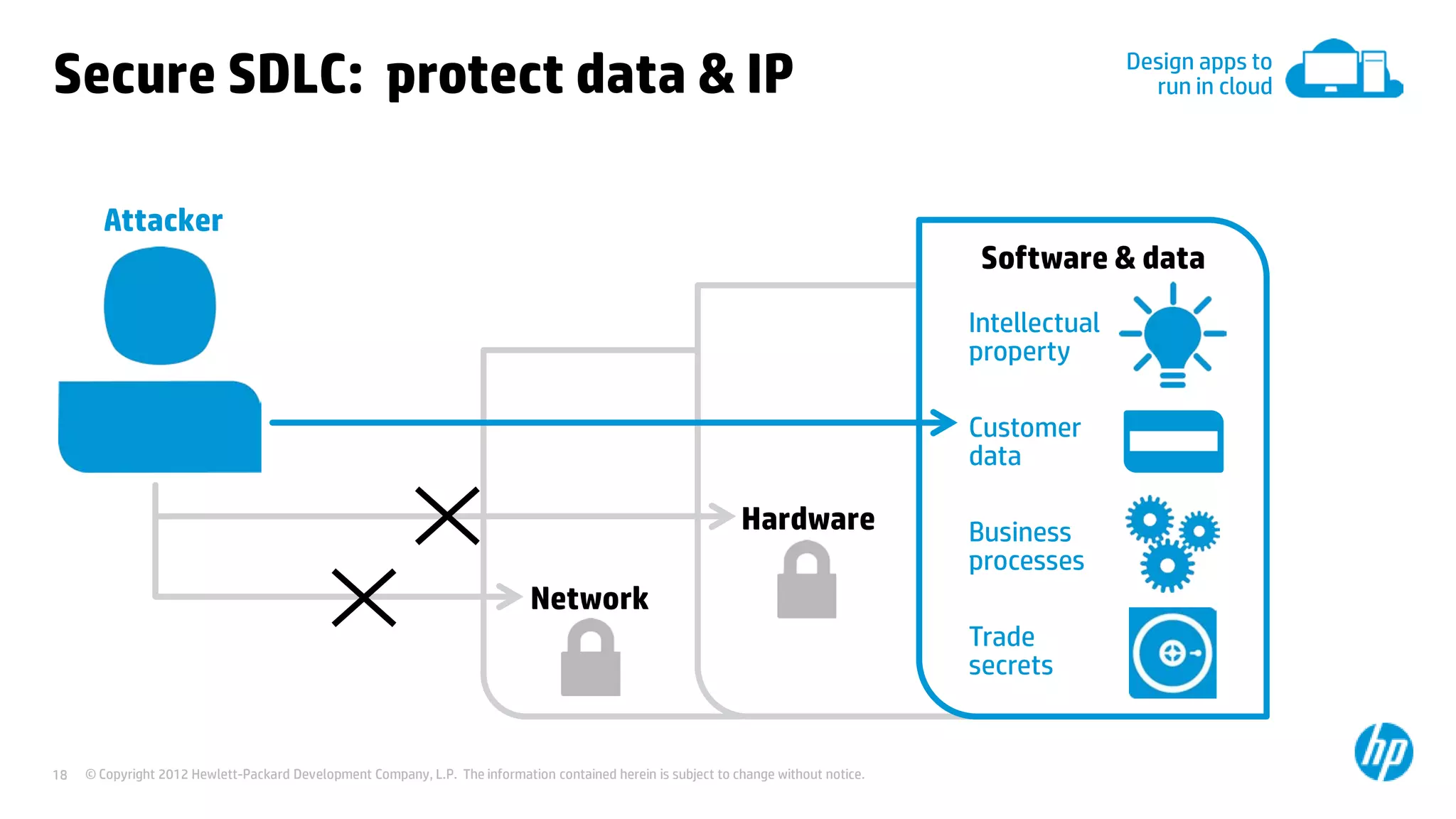
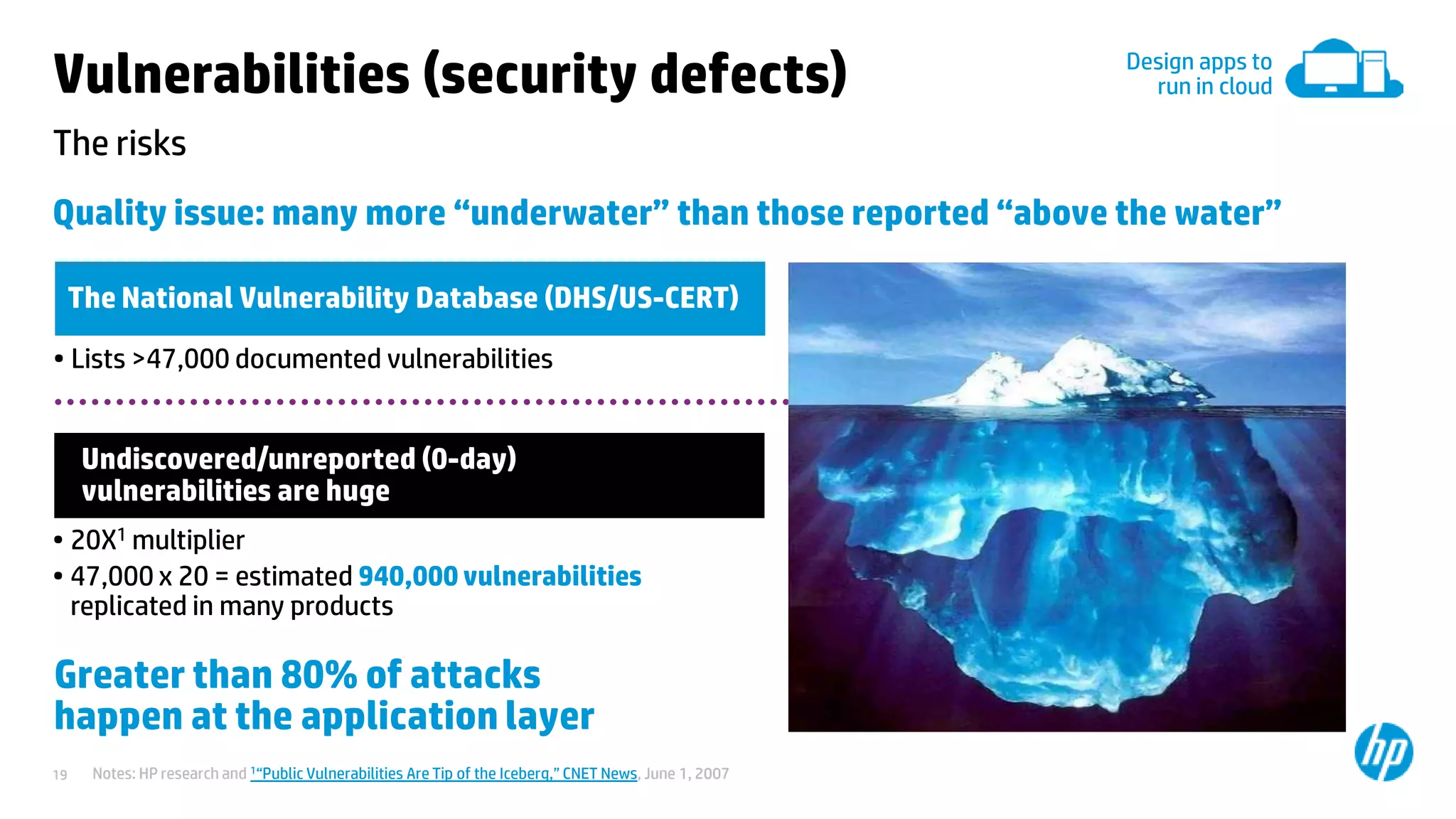
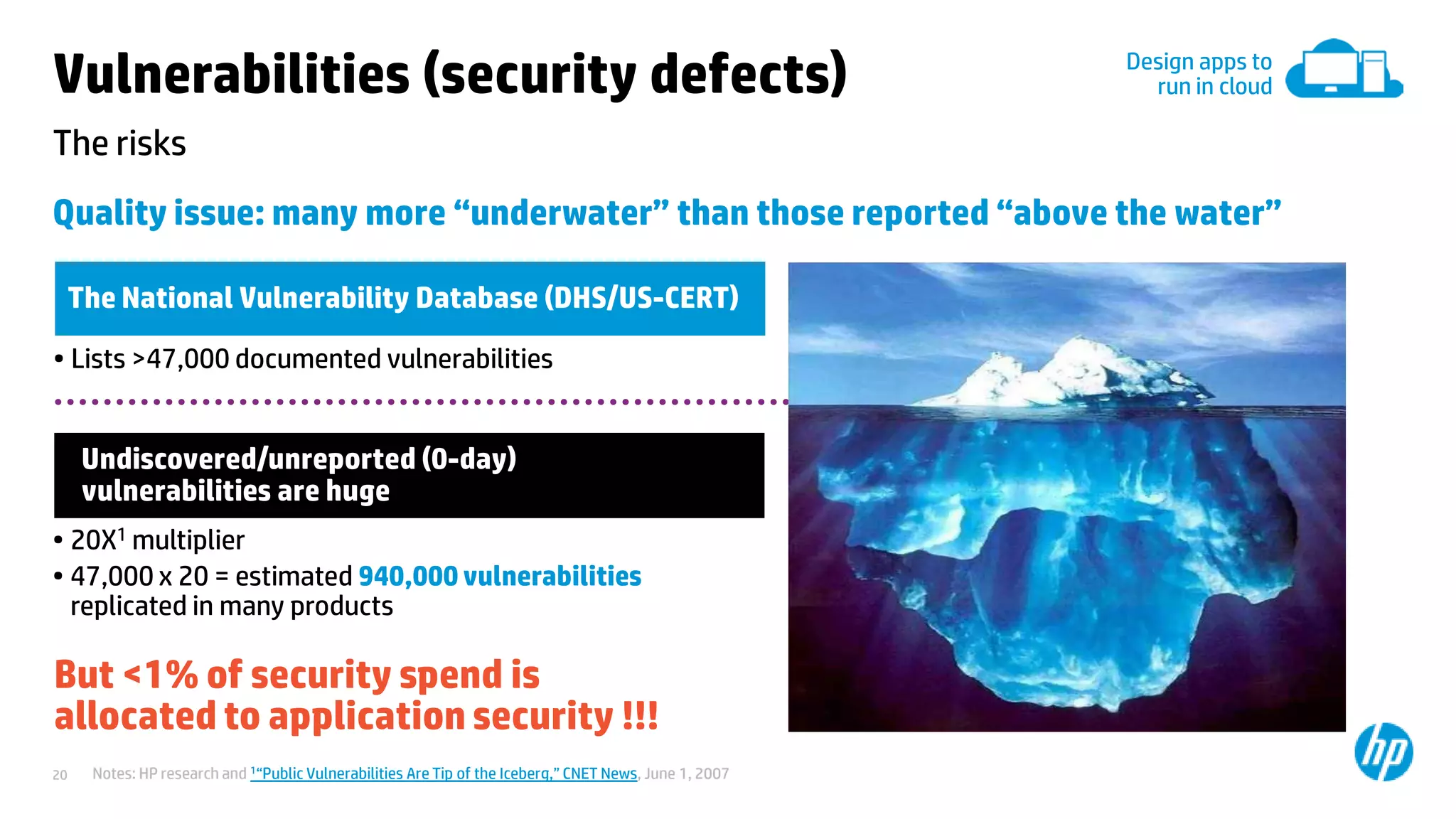
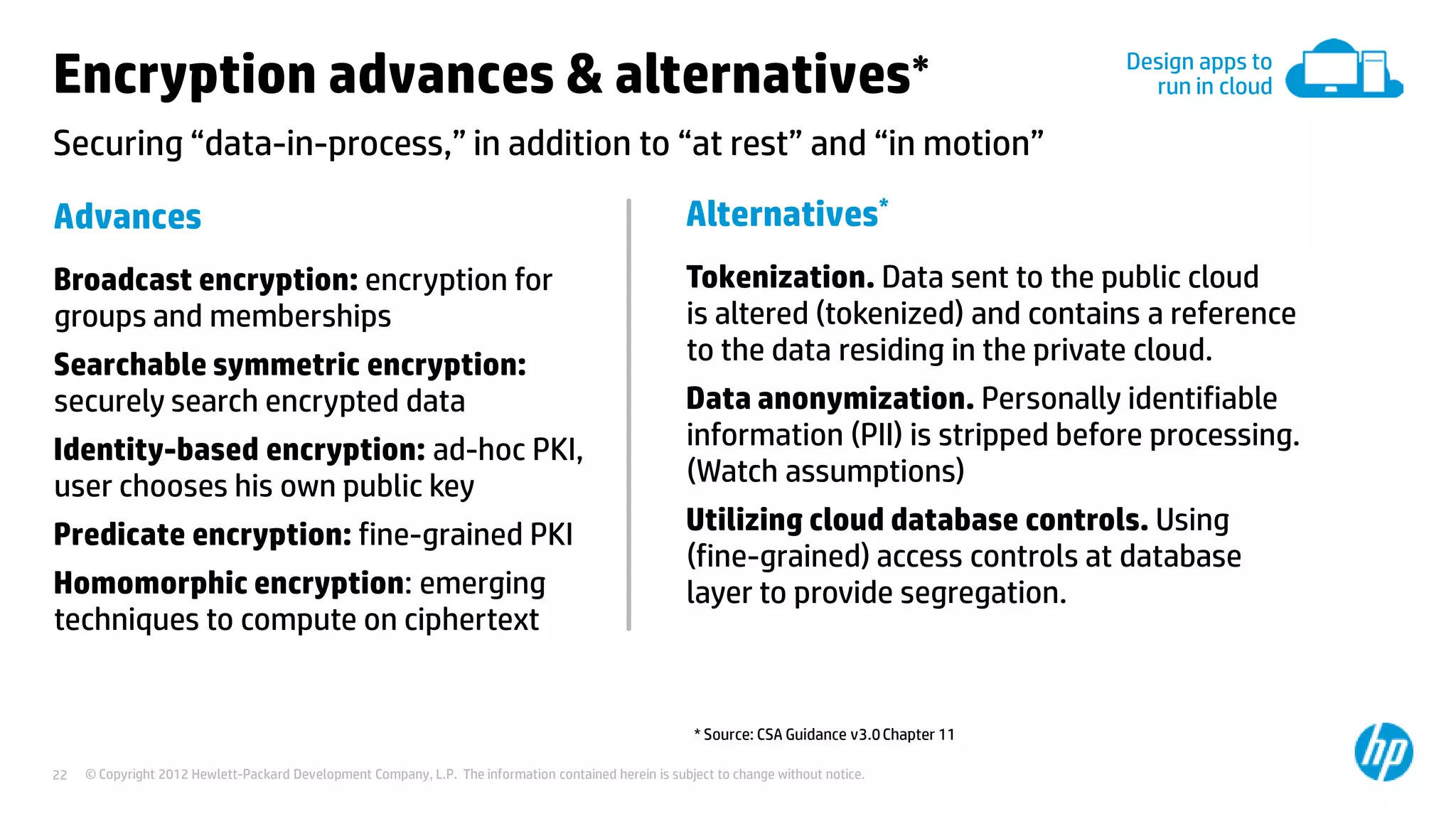
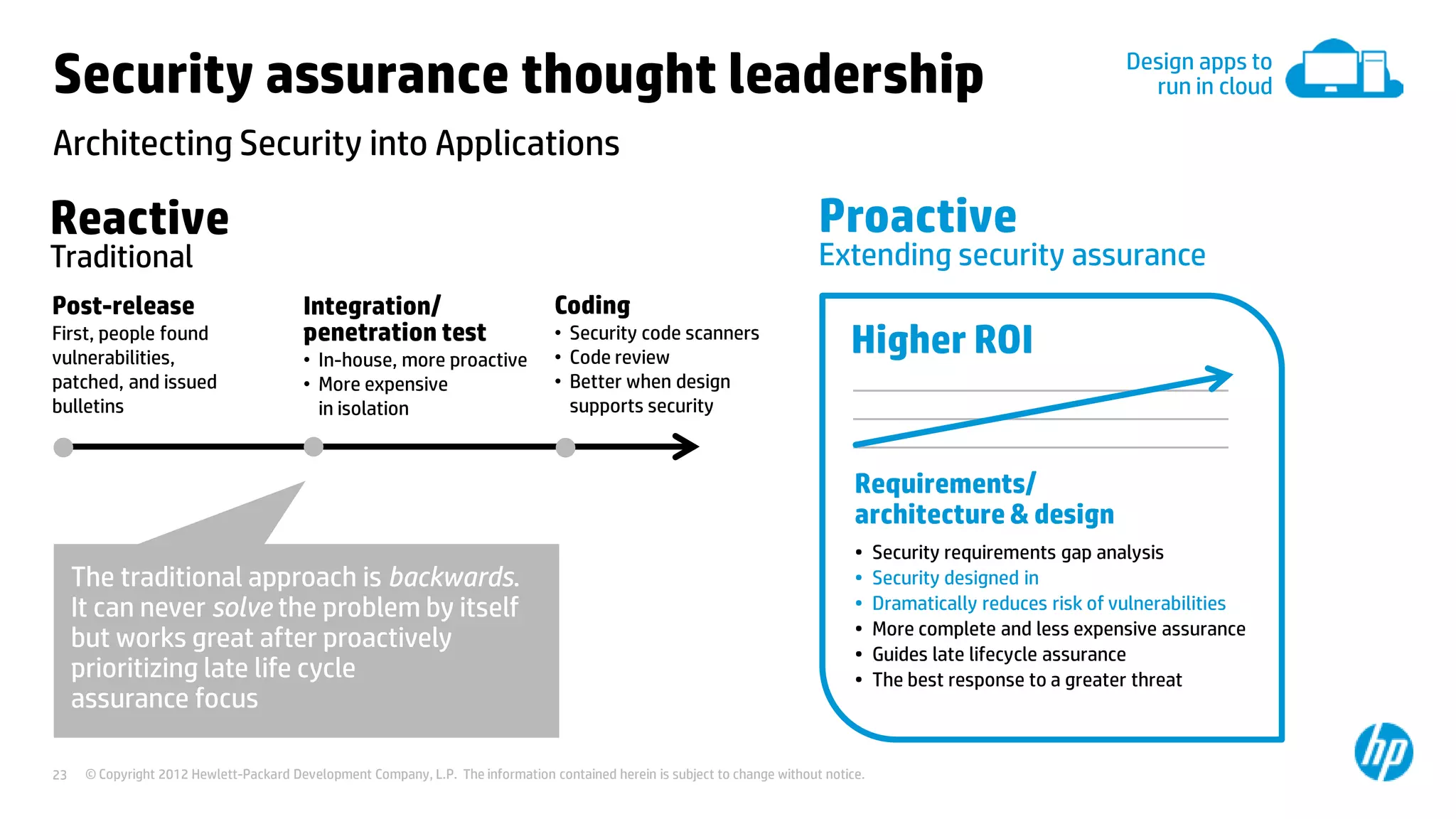
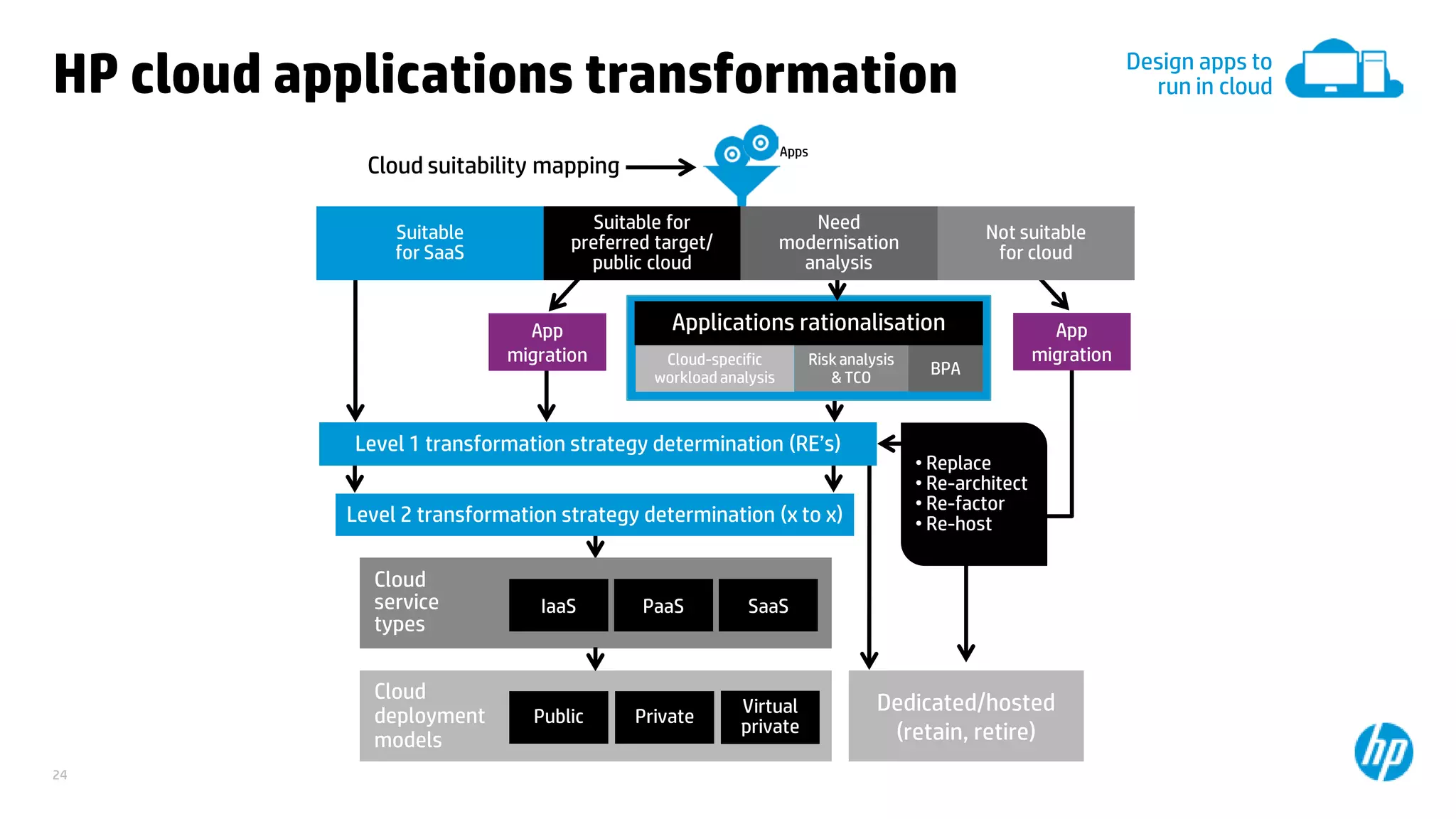
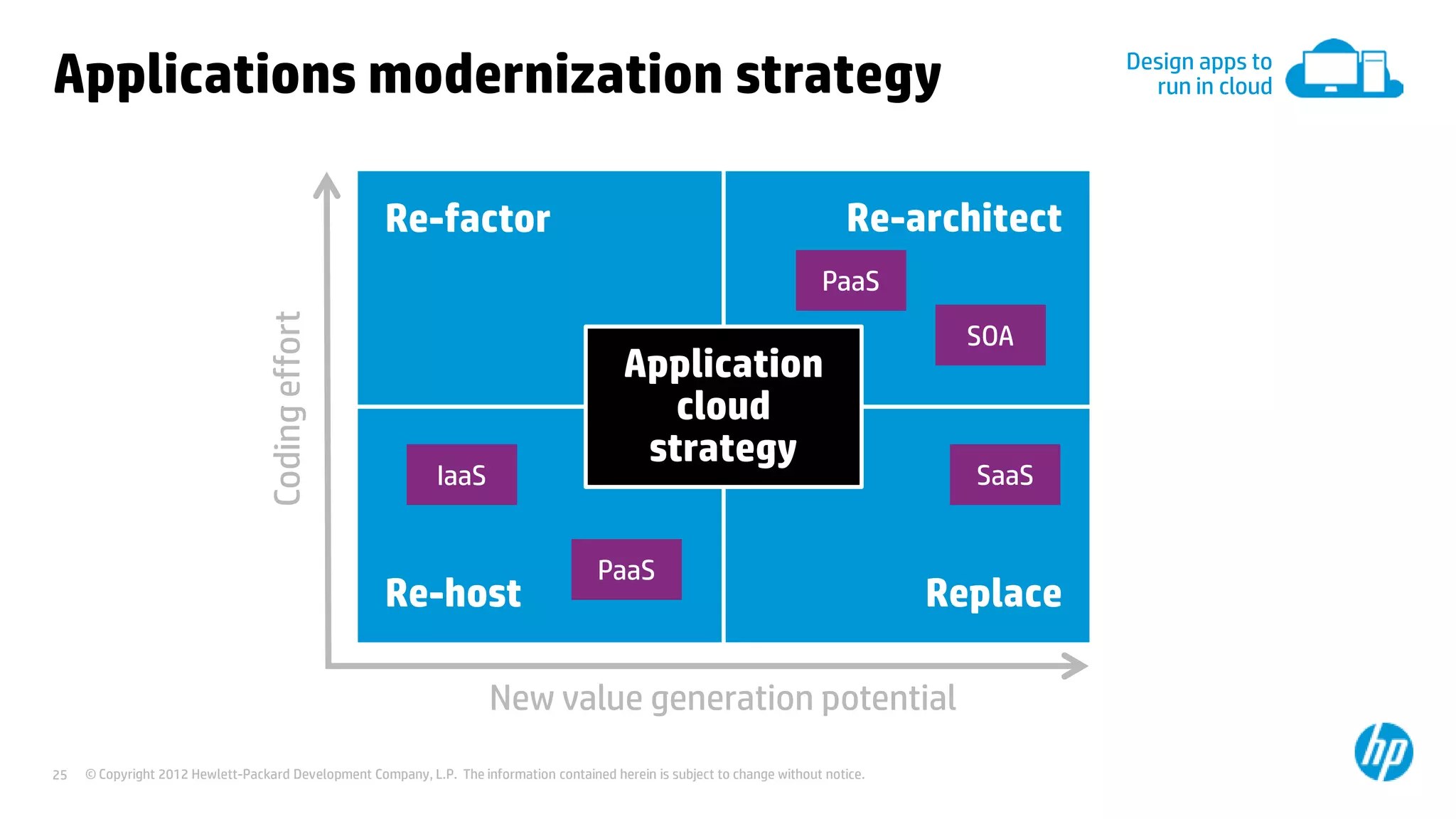
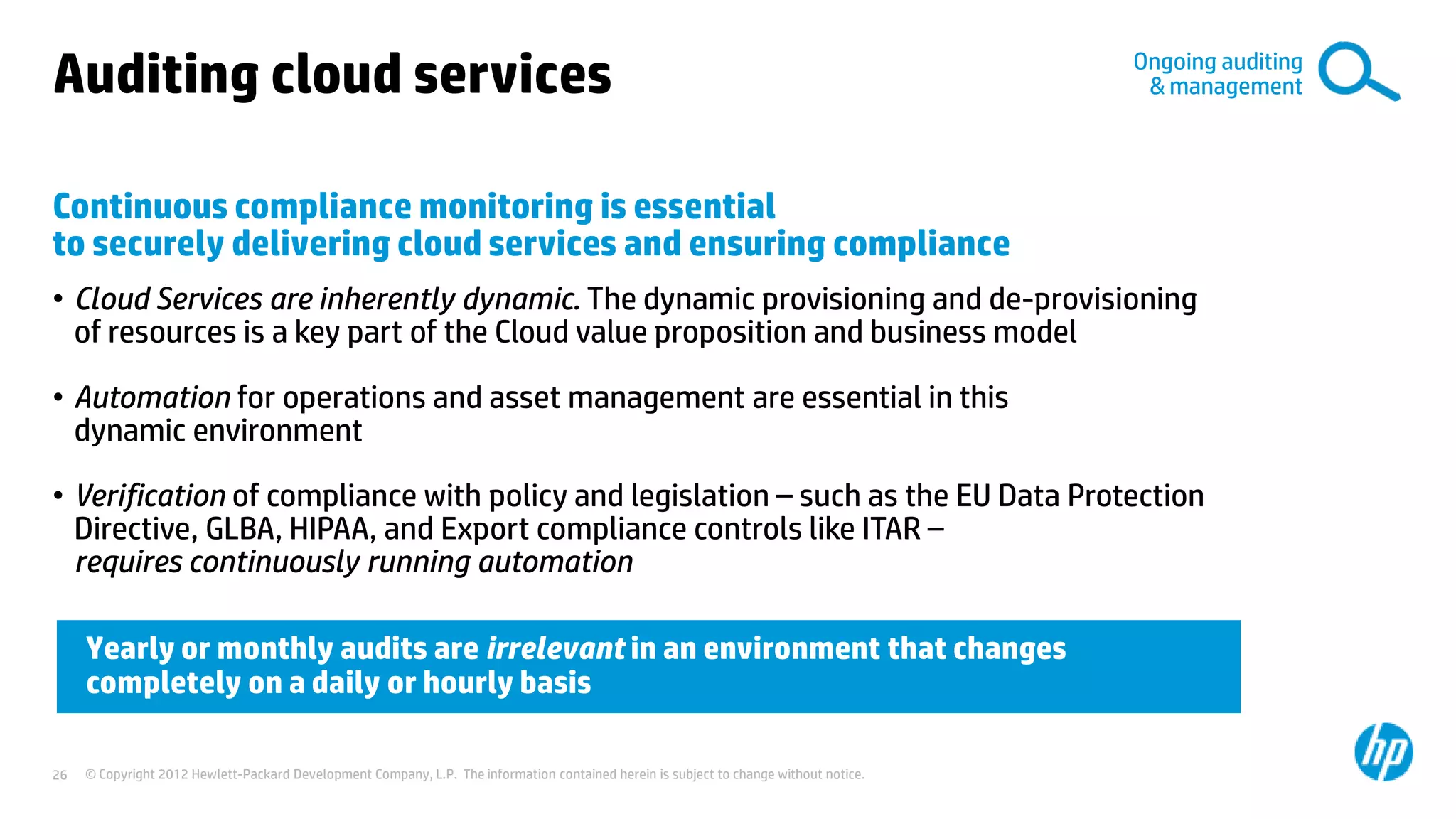
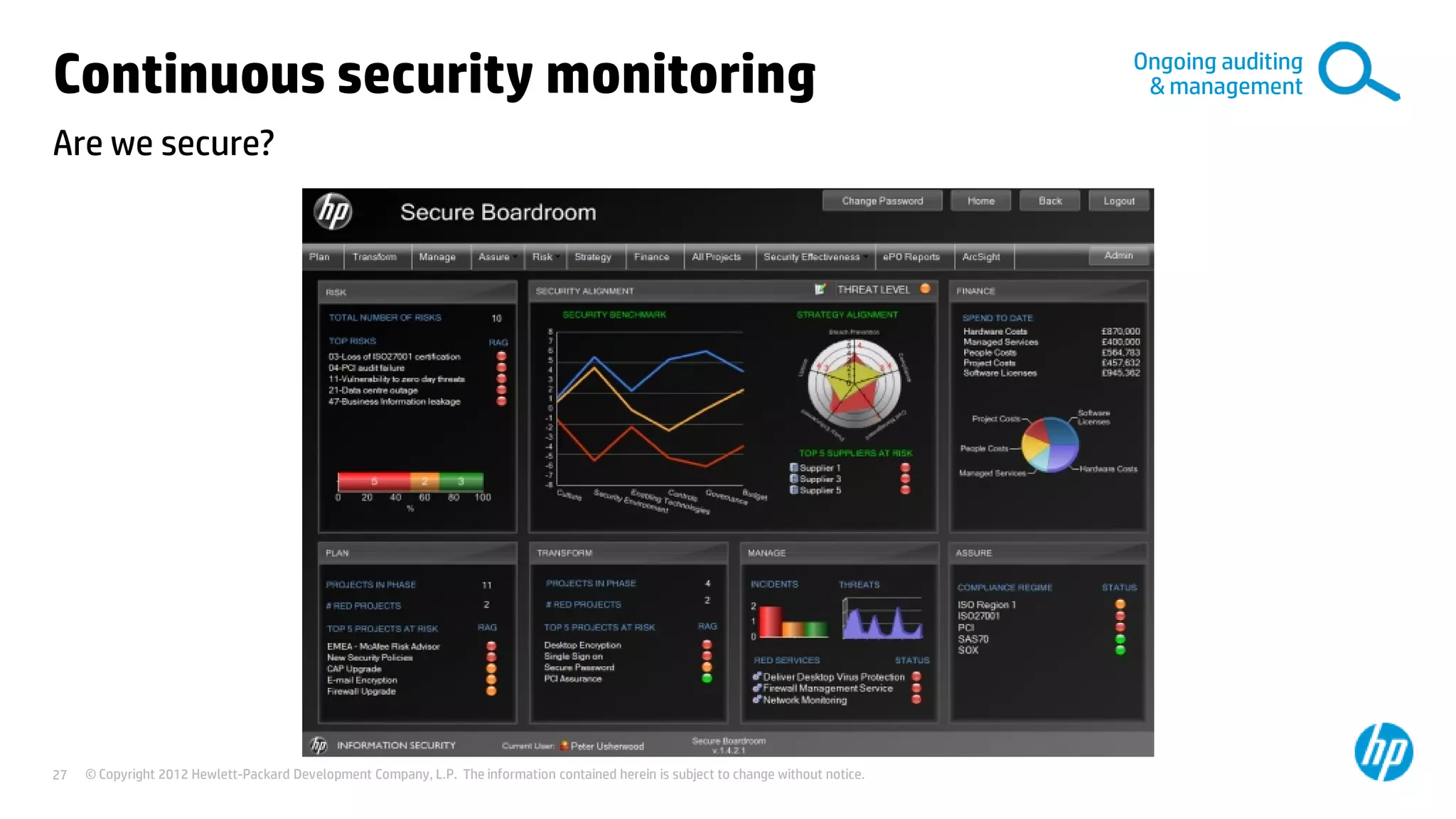
This document discusses cloud security from an enterprise perspective. It begins by outlining trends in security threats facing organizations and the challenges of managing risk. It then provides guidance on taking a risk-based approach to cloud security, designing applications securely for the cloud, and conducting ongoing auditing and management. The key recommendations are to understand your risk profile, architect for security in cloud environments, implement robust identity and access management, confirm compliance obligations, and define clear security responsibilities between customers and cloud service providers.