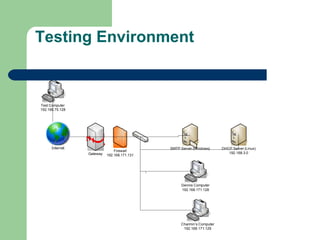
The document describes the design and implementation of a network firewall to prevent operating system fingerprinting. Key aspects include:
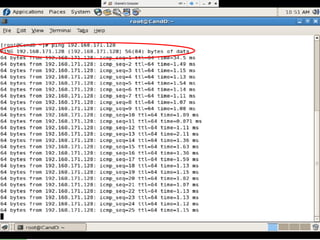
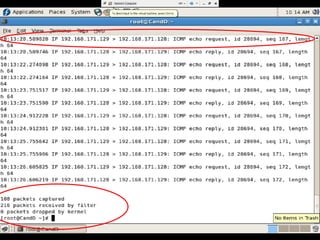
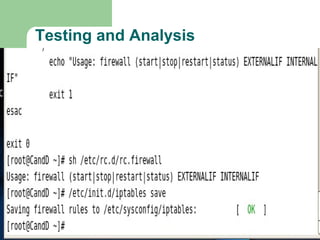
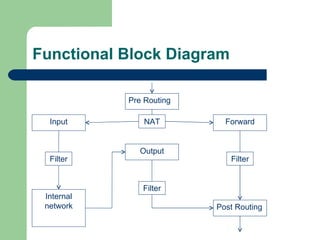
- The firewall uses iptables rules to drop packets attempting TCP or ICMP response analysis that could reveal the operating system.
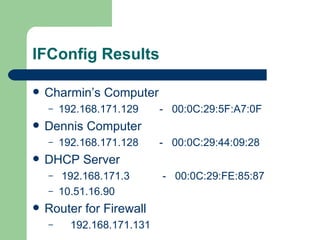
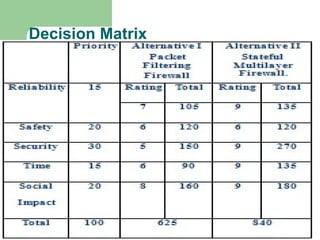
- It also implements MAC address filtering to block specific external computers deemed malicious.
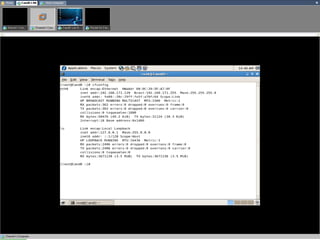
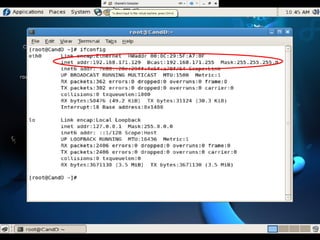
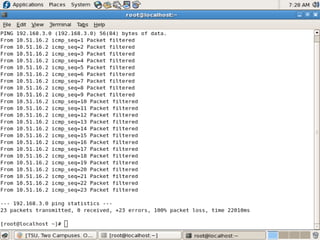
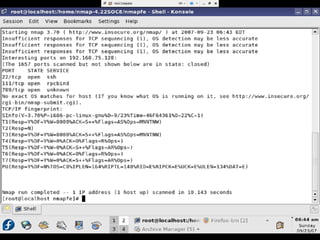
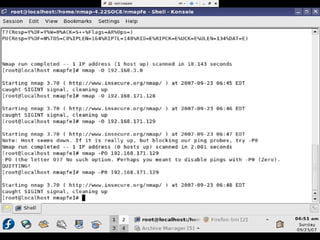
- Testing showed the firewall successfully prevented operating system fingerprinting via Nmap and restricted access based on MAC addresses as designed.






![Need Analysis There is a need to: Design a system to protect the identity of the OS implemented on the hosts and servers of a given network. Design a system to deny access to specific computers that have been deemed malicious. [10] Tony Bautts, Terry Dawson, Gregor N. Purdy. Linux Network Administration Guide 3rd Edition. Sebastopol, CA: O’Reilly Media, Inc., 2005.](https://image.slidesharecdn.com/OperatingSystemFingerprintingPrevention-122974092557-phpapp01/85/Operating-System-Fingerprinting-Prevention-7-320.jpg)

![Specifications The system must be capable of examining MAC addresses. The system must deny any responses to any testing sequence that involves sending standard and non standard tcp packets. The system must deny any responses to any testing sequence that involves icmp response analysis. The system must validate three way handshake process. [10] Tony Bautts, Terry Dawson, Gregor N. Purdy. Linux Network Administration Guide 3rd Edition. Sebastopol, CA: O’Reilly Media, Inc., 2005.](https://image.slidesharecdn.com/OperatingSystemFingerprintingPrevention-122974092557-phpapp01/85/Operating-System-Fingerprinting-Prevention-9-320.jpg)


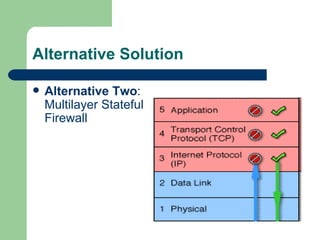



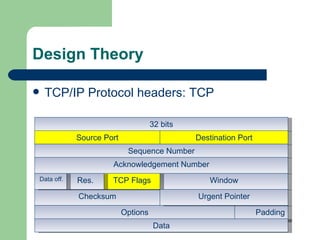
![Design Theory TCP/IP Protocol header: Ethernet Full Ethernet Packet (46-1500 bytes) Destination MAC Address Type Data CRC Source MAC Address [10] Tony Bautts, Terry Dawson, Gregor N. Purdy. Linux Network Administration Guide 3rd Edition. Sebastopol, CA: O’Reilly Media, Inc., 2005.](https://image.slidesharecdn.com/OperatingSystemFingerprintingPrevention-122974092557-phpapp01/85/Operating-System-Fingerprinting-Prevention-19-320.jpg)

![3 WAY HANDSHAKE PROCESS [10] Tony Bautts, Terry Dawson, Gregor N. Purdy. Linux Network Administration Guide 3rd Edition. Sebastopol, CA: O’Reilly Media, Inc., 2005. SYN SYN/ACK ACK Source Destination](https://image.slidesharecdn.com/OperatingSystemFingerprintingPrevention-122974092557-phpapp01/85/Operating-System-Fingerprinting-Prevention-22-320.jpg)
![Design Theory: [10] Tony Bautts, Terry Dawson, Gregor N. Purdy. Linux Network Administration Guide 3rd Edition. Sebastopol, CA: O’Reilly Media, Inc., 2005. IPTABLES NAT MANGLE FILTER INPUT OUTPUT FORWARD INPUT OUTPUT POST-ROUT PRE- ROUT OUTPUT POST- ROUT](https://image.slidesharecdn.com/OperatingSystemFingerprintingPrevention-122974092557-phpapp01/85/Operating-System-Fingerprinting-Prevention-25-320.jpg)




![Overall System Implementation Firewall Rules to prevent OS fingerprinting (inbound traffic): 1. IPFILE=$BLACKLIST if [ -f $BLACKLIST]; then for IP in 'cat $IPFILE' do $IPTABLES -A INPUT -i $EXTERNALIF -m mac --mac-source $IP -j DDROP done fi](https://image.slidesharecdn.com/OperatingSystemFingerprintingPrevention-122974092557-phpapp01/85/Operating-System-Fingerprinting-Prevention-30-320.jpg)