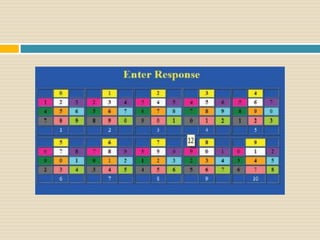
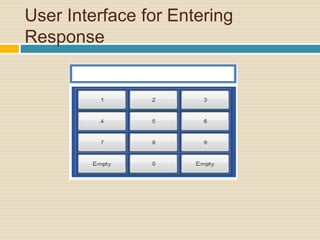
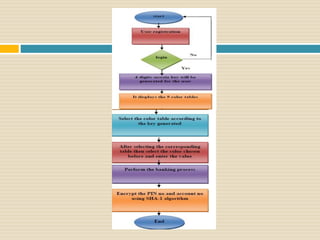
This document proposes a new authentication method called Color Lock that uses color-coded PINs to resist shoulder surfing attacks. It aims to allow users to securely enter their login credentials in public without revealing their actual PIN. The proposed method assigns unique colors to numeric values and uses a color-coded interface for PIN entry. It is intended to provide security against observation attacks while maintaining usability for users. The document outlines the background, working mechanism, objectives, applications and conclusions of the Color Lock method for more secure authentication.