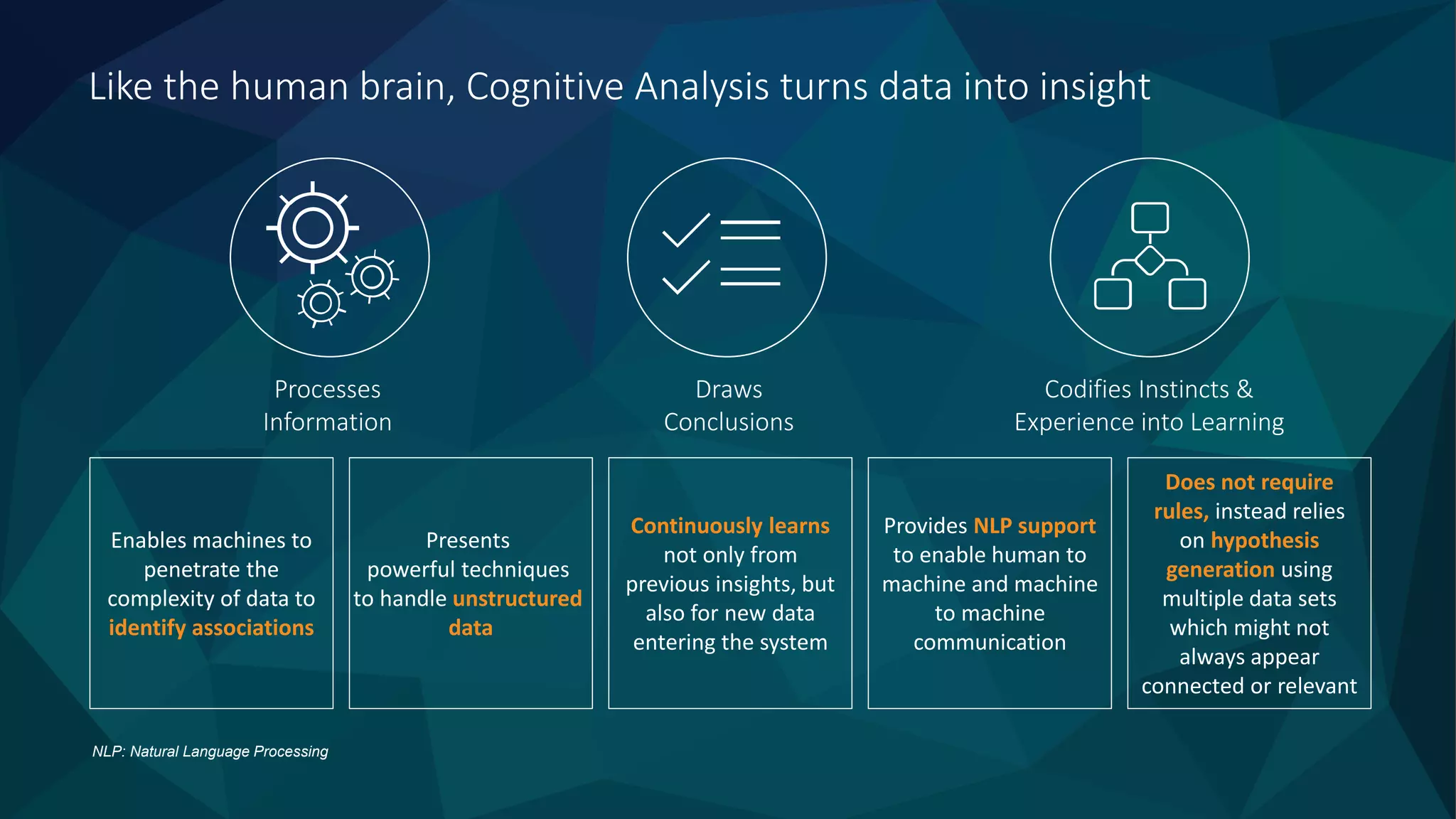
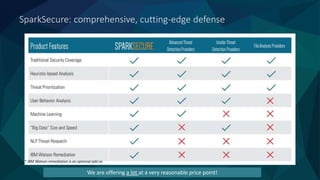
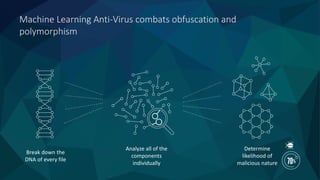
Cognitive analysis transforms data into insights and enables machines to efficiently handle unstructured data, continuously learning from both past and new information. It incorporates natural language processing (NLP) for enhanced communication and automated threat detection, prioritization, and remediation in security systems. SparkSecure, powered by IBM Watson, provides advanced threat research and analysis to improve the security teams' productivity and response times.