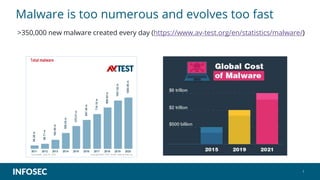
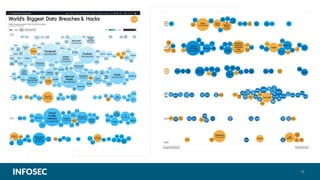
The document discusses machine learning (ML) and its application in cybersecurity, highlighting its ability to automate malware detection, adapt to evolving threats, and innovate in areas like deepfake technology. It includes live demonstrations and outlines the career opportunities in the field, particularly for cybersecurity data scientists. The emphasis is on the importance of ML in combating sophisticated cybercrime and the necessity for professionals to understand and implement these technologies.