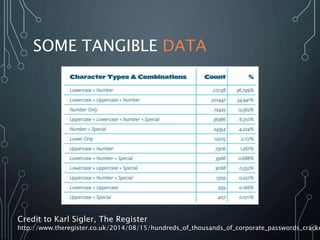
The document discusses authentication, emphasizing the significance of identity verification through passwords, security tokens, and biometrics, and outlines common issues with password usage. It highlights the vulnerabilities associated with password-based attacks and introduces the lava.password.factory tool designed for generating and managing passwords for secure authentication. The presentation is delivered by Christopher Grayson, a senior security analyst, who encourages feedback on the ongoing development of the tool.